Cost of Data Breach: ROI of Backup and Disaster Recovery Software

Why is the cost of data breach so enormous? Why are backups critically important to your business continuity? Let’s look at the cost of a data breach and calculate the ROI of backup and disaster recovery software solutions.
Your data has become more valuable than ever before! With the rising cost and value of your data, there are also numerous threats to that data across the board. This can include the ever-growing threat of malware such as ransomware and other cybersecurity threats, or it could be the threat posed every day by end-users who may mistakenly delete business-critical data.
Attackers may infiltrate the perimeter defenses of your infrastructure and gain unauthorized access to your data. A data breach is a very real concern that you must take seriously. The cost of a data breach is rising exponentially, especially since your data is at grave risk of exposure, corruption, and even deletion from any number of sources. This is due to any number of threats from hackers, internal employees, and accidental data deletion to name a few.
As these threats to your data are on the increase, the cost of the data breach and data loss is enormous as we will see. For example, the average cost of a cyber attack on a small business exceeds $25,000. Even with a single data breach or data loss event, the ROI of backup and cloud disaster recovery software proves to be well worth the cost.
Common Misconceptions About Cybersecurity and Data Breaches
Today, data has often been described as the most valuable asset your business holds. This is because data is at the heart of most business activities. With online sales and e-commerce driving most industries, data is central to business success or failure.
When you think about the complex technologies, infrastructure, and cloud solutions that we invest in, their purpose is to support, transmit, and store your business-critical data.
The value of your data cannot be emphasized enough. All too often, you hear of companies that were so focused on growing their business and reaping the rewards of success, they failed to properly think about protecting their data.
Data protection is just as important to think about in cloud environments as it is on-premises. You may have migrated at least part of your data to the cloud.
Do you have cloud-based backup services to protect your data there?
Many businesses may fail to back up their business-critical cloud infrastructure as they may mistakenly view data protection as an unnecessary expenditure on a solution that is not needed. Many may be under the impression that cloud environments are immune to data loss. This is simply not the case. Consider the recent Amazon data loss event where a large chunk of customer data was lost.
Another misconception, especially among small to mid-sized businesses, is they may not be a target of a cyber attack due to their small size in comparison with other targets of attackers.
However, this type of mindset is extremely unwise as attackers are targeting a wide range of business sizes and industries. In 2019, there has been an uptick in coordinated ransomware attacks that have targeted hospitals, schools, media outlets, and public offices.
So far, we have spoken in general about the value of your data and the threat from a data breach. What are the underlying causes of a data breach?
Causes of data breach that effect the cost of data breach
Data Breach can be the result of many different kinds of events. However, the three most common causes of a data breach are:
- Malicious cybersecurity or criminal attack
- System glitch
- Human error
Ransomware
Ransomware can render your data useless.
Any of these events can lead to grave consequences for your business’s financials and customer confidence. What are those costs?
How Much Does a Data Breach Cost a Company?
Let’s take a look at the question – how much does a data breach cost a company? While this can be answered in general terms, let’s look at real data breach numbers and what it could wind up costing you and your business. Each year, IBM Security releases a study called the Cost of a Data Breach Report. This year’s report contains some alarming numbers when it comes to what data breach can actually cost your business.
The average cost of a data breach includes the following global averages:
- $4.45 million average total costs of a data breach
- The cost per lost record is $165
- Time to identify and contain the breach is 277 days
- The top 3 industries with the biggest data breach cost are Healthcare ($10.93 million), Financial ($5.90 million), and Pharmaceuticals ($4.82 million).
- The top 3 types of compromised data: customer PII (52% of all breaches), employee PII (40%), and intellectual property (34%).
More specifically, the United States saw the highest cost of a data breach in 2019, with the following:
- $9.48 million average total costs of a data breach
Compare this data to the 2019 Cost of Data Breach report:
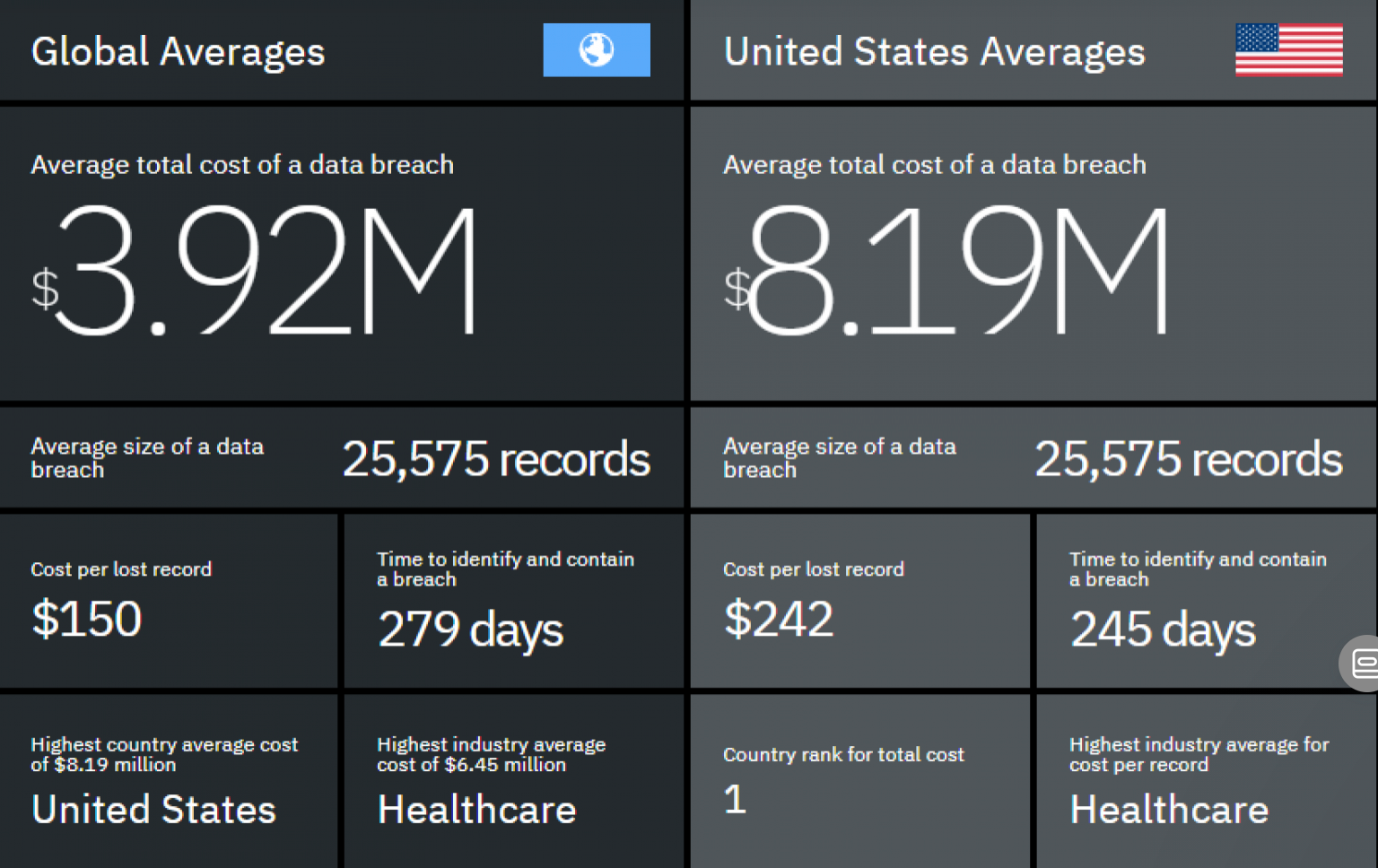
IBM Security Cost of Data Breach in 2019 (Image courtesy of IBM)
Where Data Breach Costs Come From
When you examine where the costs come from in the case of a data breach where data is lost or stolen, there are many different areas where your business can be affected by a data breach, including long-term effects that need to be considered.
Disaster recovery cost
Disaster recovery costs encompass all costs that a company spends on recovering its data and systems. Keep in mind, that some records might be permanently lost. Some recovery requires hiring a third-party specialists to tackle the problem.
Lost Customers
One of the major factors that cost your business in the event of a data breach event is lost, customers. When the news of a breach makes headlines, regardless of whether or not the breach is your fault, this can leave consumers who may have been future customers wary of doing business with you. Current customers whose data may have been lost or stolen will most likely no longer have confidence in your business handling their data.
Long-Term Effects
Keep in mind these types of costs can remain long-term, lasting even years down the road. Some 22 percent of data breach costs can happen in year two, after the breach. And an 11 percent cost of a breach can happen more than two years afterward! The effects are long-lasting!
Legal and Other Fees
Additional costs of a data breach can result from legal fees, third-party security firms, and internal time and administrative effort spent “cleaning up” after a data breach event.
Fines
Let’s also not forget very recent GDPR fines and penalties that can cost businesses more than the actual data breach event. GDPR fines and penalties can cost a business significantly. GDPR fines consist of up to 10 million euros or 2% of its entire global turnover of the preceding fiscal year, whichever is higher.
How are GDPR fines determined? If there is a punishable situation in a company, that is revealed through proactive inspection activities. Was the company negligent in protecting the data of its customers? Was there gross mismanagement or a lack of proactive protection of the data?
So, keep in mind that on top of the cost of the actual breach itself, your business can potentially be at risk of GDPR fines if subject to the purview of the EU. Considering the potential cost of a data breach, your business must think about how data is protected.
One eye-opening aspect when looking at the cost of a data breach is that cloud migration and housing your data in the cloud can actually increase data breach costs. This is due to the additional complexity that housing data in the cloud brings to your infrastructure.
In addition, misconceptions concerning the protection of your cloud data as mentioned above as well as a lack of processes and solutions in the cloud to protect your data can lead to greater data breach costs.
Cloud-Based Backup and Recovery ROI
Let’s focus on data loss as a result of the data breach. After looking at actual numbers making up the cost of a data breach resulting in lost or stolen data in 2019, your business would see an immense ROI for a backup and recovery software solution protecting your data.
If your business has migrated business-critical data and services to Software-as-a-Service environments such as Google Workspace (formerly G Suite) and Microsoft Office 365, you need to have an effective cloud-based backup service in place to protect this data in the cloud. The fine print included in most public cloud vendor SLAs points to the fact that your data is your responsibility, not theirs.
Cloud-based backup solutions
Cloud-based backup solutions allow you to make use of a DR-as-a-Service configuration for protecting your business-critical data. Cloud-based backups allow you to have an effective way to protect your SaaS data such as Google Workspace and Office 365 by copying your data to a protected cloud environment for backup.
This helps to ensure that your backup data is protected from accidental deletion or encryption by malware. The only access to your backup data is for recovery in times of disaster, including ransomware attacks that render your business data useless.
When choosing a cloud-based backup solution, you want to make sure your data is stored outside of the cloud environment you are protecting. This helps to make sure that in the event your production cloud vendor is having issues, your backup data is still accessible. This is in harmony with the 3-2-1 backup best practice methodology. Its core principle is based on the fact that you never want to have your backups housed in the same environment as your production data.
3-2-1 backup best practice methodology
To follow this principle, if you are using Office 365, you would want to have your backups housed in a different public cloud outside of Microsoft’s public cloud infrastructure is perhaps Google or Amazon. This helps to diversify where your data is housed.
As an example of a cloud-to-cloud backup solution that allows you to diversify where your data is stored, Spinbackup provides great options to store your backups in different cloud environments than where your data is stored. You can choose from Amazon AWS, Google GCP, or Microsoft Azure as the target for your backups.
Along with offering options on where to store your data, you get all the options needed to protect critical data in the cloud including automated backups, unlimited retention, encrypted backups, granular restores, data migration, and data downloads.
Google Workspace Backup by Spin.AI
Spinbackup provides backups and cybersecurity for Software-as-a-Service environments like Google Workspace and Office 365
Aside from backing up your data, Spinbackup offers a full cybersecurity suite of functionality to protect your SaaS environments from the cybersecurity threats that lead to a data breach in the first place.
Whatever solution you choose to backup and protect your data, backups are essential to being able to successfully recover from data breach events leading to data loss. Having cybersecurity protection to go along with effective backups can literally save your business millions along with the untold losses in customer confidence that can lead to years of losses as a result.
Securing Cloud SaaS with SpinOne SaaS Security Posture Management
Organizations today are heavily using cloud SaaS solutions that include Google Workspace and Microsoft Office 365. On top of the core services provided by each of these very capable cloud SaaS solutions, businesses have access to thousands of third-party applications that can extend the functionality of the platforms. How can organizations increase their security posture with cloud SaaS environments, including third-party applications, and protect against modern threats such as ransomware?
SaaS Security Posture Management Capabilities
SpinOne is a next-generation cloud SaaS Security Posture Management (SSPM) solution that leverages the capabilities of artificial intelligence (AI) and machine learning (ML) to provide an automated security solution. It offers organizations the following capabilities:
File-sharing Control
It provides the ability to fix shared mailboxes and files that are easy targets for hackers (Microsoft even recommends blocking sign-ins for shared mailbox accounts)
Cloud Data Access Control
For internal and external users – know who is accessing business-critical data, both from within and outside the organization
Easy employee offboarding
Including taking ownership of user account data by an admin, blocking access, migrating data to another cloud SaaS user account
Saas Application Risk Assessment
Maximize control and visibility in cloud SaaS applications where security gaps exist or may arise. Spin allows taking control of the applications users can access and integrate with cloud SaaS environments
Enhanced visibility into cloud applications
Used within the organization it allows acting immediately to fix any gaps to prevent data breaches and to put in place measures that ensure you maintain complete control over your data. This capability ensures no data subsets are anonymously accessible.
Automated Ransomware Protection
SpinOne provides automated ransomware protection that detects ransomware attacking your cloud SaaS data, blocks access to the malicious process, identifies affected files, and automatically restores data affected by the attack.
Today the threats against business-critical data are ominous. As organizations struggle with the current challenges of the hybrid workforce, they cannot neglect their security posture. SaaS Security Posture Management (SSPM) solutions provide today’s businesses with the automated tools needed to combat modern threats. The responsibility of configuring cloud SaaS applications for top-level security lies with the business, not the cloud service provider. To reduce the security cost and security management effort, utilizing SSPM solutions reduces the overall risk from a security perspective and bolsters its effectiveness. SpinOne’s automated security features help reduce the cost, time, and effort for in-house security teams struggling to keep up with escalating risks and multiple cloud SaaS applications.
Concluding Thoughts
The cost of a data breach is real. Your business could stand to lose millions initially and even more than that over time. Fines levied by GDPR and other compliance regulations can add to the cost of data breaches significantly. Worst of all, customer confidence can be lost forever.
The ROI of your investment in effective data protection can be achieved very quickly, especially if you suffer a data breach. By using both good backups of your environments, including the cloud, along with cybersecurity protection, you can offset many of the costs that otherwise could be detrimental to your business.
Want to find the service that does all that? Request a demo of full SpinOne’s protection and see it in action!
Was this helpful?
- Common Misconceptions About Cybersecurity and Data Breaches
- Causes of data breach that effect the cost of data breach
- Where Data Breach Costs Come From
- Cloud-Based Backup and Recovery ROI
- Google Workspace Backup by Spin.AI
- Securing Cloud SaaS with SpinOne SaaS Security Posture Management
- SaaS Security Posture Management Capabilities
- Concluding Thoughts
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Expert Insights: SaaS Application Data Protection Fundamentals
March 21, 2024SaaS applications appeal to organizations because they make running the application “somebody else’s problem.” However,... Read more


