How to Improve Visibility into Cloud Applications Data

Today, businesses face dangerous waters as they sail the ocean of cloud Software-as-a-Service environments and secure their business-critical data. One of the challenges facing organizations as they migrate their data and services to cloud SaaS is a lack of visibility into cloud applications data and cloud cybersecurity events. Without the proper visibility into cloud SaaS application cybersecurity threats, it leads to gaps in SaaS app risk assessment, policies and procedures, and an overall weaker cybersecurity posture.
Using native cloud SaaS environment dashboards, tools, and auditing can be challenging. What challenges do businesses face with native cloud visibility to their data and cybersecurity events? How does SpinOne help enterprises to solve the challenges of cloud SaaS applications visibility?
Challenges of Cloud Applications Data Visibility
There are many visibility challenges businesses face as they migrate their data to cloud SaaS environments. These include many aspects of the environment, including:
- Data sharing
- Application security and reputation
- Cloud cybersecurity events
1. Data sharing
Easy sharing and collaboration on various business-critical data is a tremendous strength of cloud SaaS environments. No matter where they are located or what device they are using, end-users can access data found in the environment. Enterprise users can also share data outside the cloud SaaS organization. However, this is the Achilles heel of cloud SaaS cybersecurity.
The effortless ability to share data between users and even ones outside the sanctioned cloud SaaS environment provides an easy opportunity for unintentional or even intentional data leakage on the part of an end-user. Using the native cloud SaaS tools found in either Google Workspace or Microsoft 365 can be challenging to have visibility to data sharing, both inside and outside the organization.
Google has a File Exposure Report as part of the security dashboard to help gain visibility to data sharing. However, it is not available in the Enterprise Standard edition of Google Workspace. So, subscription-level comes into play. With Microsoft, the ability to gain access to shared data is even more cumbersome. To understand data sharing in SharePoint Online, you have to create a CSV file to parse for shared data.
Organizations need a cybersecurity solution for visibility to file-sharing in either Google Workspace or Microsoft that doesn’t rely on the subscription level and certainly doesn’t require looking into low-level CSV files.
2. Application security and reputation
One of the immensely challenging aspects of cloud SaaS security is maintaining visibility and control over cloud applications and browser extensions that can access business-critical data. Cloud applications work off of OAuth permissions granted by users. When a user grants a cloud SaaS application or browser plugin access to cloud data, the OAuth permissions allow the application to act with the same permissions granted to the end-user.
The cloud SaaS application then has access to all the user’s resources without knowing the account password. OAuth permissions provide the flexibility and ease of integrating apps and granting access to data. However, this can easily lead to cybersecurity issues, especially if a user grants access to a malicious app.
Hackers are undoubtedly going to use malicious cloud applications to compromise enterprise cloud SaaS environments. Therefore, organizations must have visibility control over cloud SaaS applications and browser plugins users integrate into the environment.
Additionally, the behavior of a once benign application may change in the future. Therefore, auditing the application’s intentions and behaviors is critical for maintaining visibility and control over cloud SaaS data.
3. Cloud cybersecurity events
Another challenge for businesses is gaining visibility to cybersecurity events across all services they use in the cloud SaaS environment. Often each cloud SaaS service has its own management dashboard and logging. As a result, admins have to visit each cloud service and view logs for the service in question.
Many security solutions that provide aggregate views of events in the cloud SaaS environment are often additional add-ons or require a specific subscription level. As a result, it can leave organizations without visibility into cybersecurity events that may indicate data breaches or compromise.
SpinOne – Eliminating Cloud SaaS blindspots
A lack of visibility gives attackers the advantage and can lead to extended data breach lifecycles. So what is the data breach lifecycle?
IBM’s Cost of a Data Breach Report 2021 report defines the data breach lifecycle (an average of over 200 days in 2021) as:
“The time elapsed between the first detection of the breach and its containment is referred to as the data breach lifecycle. The average time to identify describes the time it takes to detect that an incident has occurred. The time to contain refers to the time it takes for an organization to resolve a situation once it has been detected and ultimately restore service.”
The data breach lifecycle is directly related to the visibility organizations have to cybersecurity events. SpinOne helps organizations eliminate the cybersecurity “blind spots” that often exist with cloud SaaS environments by providing the visibility needed in a single-pane-of-glass dashboard.
SpinOne’s Cloud Monitor allows organizations to view all monitoring activity captured by Spin, including cybersecurity incident alerting, giving visibility to remediated events such as Ransomware Protection, Shared Items Control, and Sensitive Data Detection.
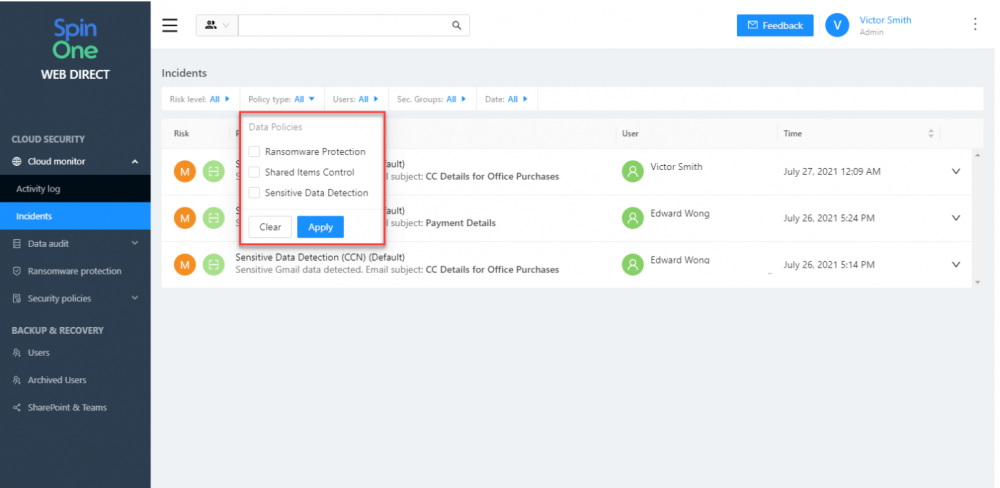
SpinOne Cloud Monitor Incidents dashboard
Easily see who has shared data, what was shared, and who the data was shared with SpinOne’s Shared data dashboard.
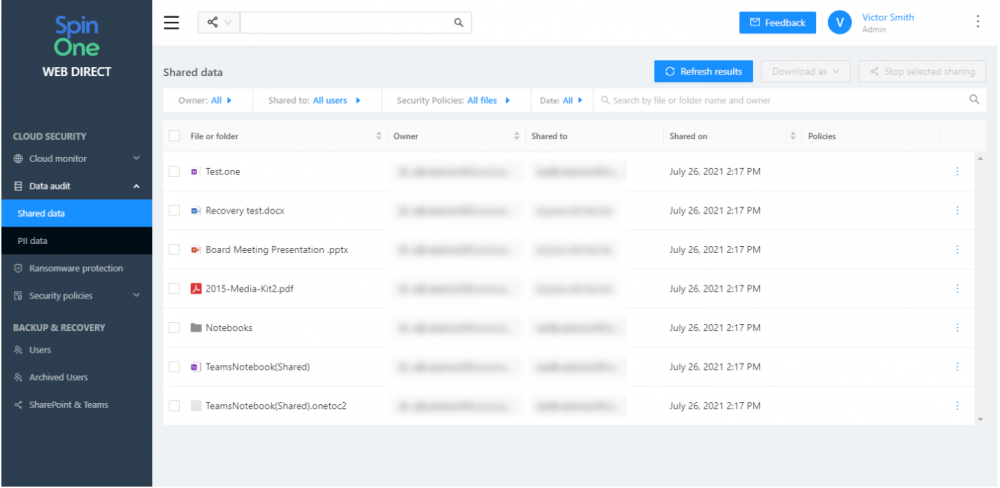
Viewing SpinOne’s shared data dashboard for visibility into data sharing in and outside the organization
Gain visibility to the risk of cloud SaaS applications with the SpinOne Risk Assessment module. It allows auditing cloud applications, creating an approval process, and monitoring the behavior of cloud SaaS applications with artificial intelligence (AI) processes.
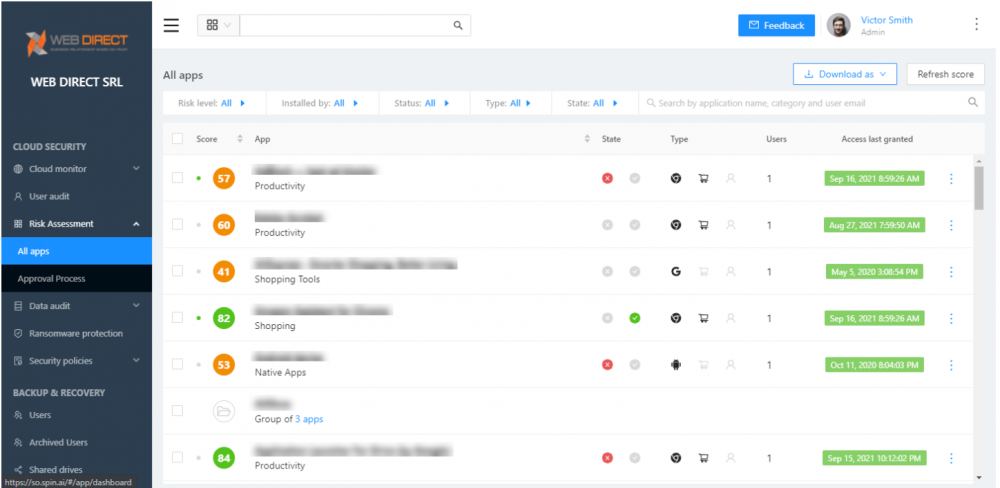
SpinOne Risk Assessment dashboard allows monitoring cloud SaaS applications
Organizations using SpinOne in their environment have the proper tools to provide visibility into current and future cybersecurity threats. As a result, it levels the playing defending against evolving attacks and new cybersecurity threats.
Protecting SaaS data in cloud services like Google Workspace, Microsoft 365, and Salesforce is your responsibility. Stay safe and schedule a demo here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


