What is Shadow IT: A Comprehensive Guide for Businesses

77% of IT professionals predict that Shadow IT will become a major problem for organizations by 2025 if left unchecked. What is Shadow IT? Why do most IT professionals consider it a key problem? What are the 4 major strategies to battle Shadow IT? Here you will find the answers to all these questions.
This article contains key takeaways from our programmatic whitepaper “The Ultimate Shadow IT Playbook”
Download the full guide here.
What is Shadow IT?
Any IT technology that workers use without the approval of the IT security department is called Shadow IT.
The largest organizations today are using, on average, 976 SaaS applications. These are all apps that IT security is aware of and controls. Here’s another stat. 80% of employees admit to using SaaS applications at work without securing approval from the IT department.
What are the key drivers of Shadow IT growth?
Rapid cloud adoption
93% of enterprises are embracing hybrid cloud environments or migrating completely to the cloud within the next 5 years. Already nearly 40% of enterprises operate entirely on SaaS.
While organizations were hesitant to trust cloud platforms 8-10 years ago, that perception has largely changed. Most organizations have come to trust cloud environments and what they offer. Cloud service providers have matured, and the platforms have grown and expanded to include many robust applications.
In addition, business-critical applications on-premises might require purchasing a new server and network infrastructure, configuring the architecture, and deploying the applications in the data center, which might take weeks or months. With cloud SaaS applications, deploying new mission-critical applications for the entire organization takes only a few clicks.
This tremendous shift to cloud SaaS and the ease with which businesses can install third-party cloud SaaS applications has led to the explosion of cloud SaaS apps in the enterprise. However, despite the many advantages that come from this paradigm shift to cloud SaaS, it also opens organizations to a myriad of cybersecurity threats, one of which is Shadow IT
Lack of knowledge about security risks
There are two main reasons why employees do not understand the risks of Shadow IT. First and foremost, the company doesn’t conduct regular cybersecurity awareness trainings.
Second, 80% of global population have the optimism bias. This percentage is consistent across race, nationality, gender, and age. Optimism bias makes people believe that they are invincible. Bad things like ransomware attacks or sensitive data leak happen daily but not with them. Danger is far and they are beyond its reach. Until they aren’t.
Chase for comfort
58% of employees aren’t completely satisfied with their company’s technologies – and bend the rules to accommodate.
With the tremendous number of cloud Software-as-a-Service (SaaS) applications available to organizations today, businesses have access to an infinite number of capabilities in the cloud. In addition, if there is a feature or function in the cloud that does not exist natively, there is a third-party app that can add it to a company’s cloud SaaS environment.
Hybrid work models and BYOD
In the US, 87% of employees prefer the flexibility of the remote/hybrid setup. Though having many benefits, this model of work undermines corporate IT security. Employees no longer work in safe networks. As a result, the enterprise has little to no control over the applications they use.
The same is true for BYOD practice. Meanwhile, over 80% of enterprises encourage employees to use their personal devices for work.
What are the main risks of Shadow IT?
In this section, we’re discussing the main shadow IT risks and discuss how they impact your business.
Data breach
The key danger of allowing unmanaged apps to get installed in your cloud SaaS environment is that it opens your organization up to the possibility of malicious applications. Attackers realize that most businesses today are storing large quantities of their production data in cloud environments. Using phishing attacks coupled with OAuth abuse, an attacker can masquerade a malicious app as a legitimate application and entice an unsuspecting end-user into granting access (OAuth token) to a malicious application.
OAuth tokens granted to a third-party cloud application allow the application to access the cloud SaaS environment without a password. By its very nature, OAuth is a token-based authorization mechanism that, when used properly, is a secure, cloud-native authorization protocol. However, its weakest link is the end-user. Unless a user scrutinizes the permissions requested by an application, they may be granting high levels of access to an unknown application and third party.
Data loss and Leak
Shadow IT operations can lead to specific data getting leaked unintentionally or exposed to third parties that should not have access to the data. The fallout from leaked data can be tremendous, leading to fines, damaged business reputation, legal action, and financial repercussions that can last for years. Some businesses may never fully recover from a data leak incident.
Cloud SaaS applications may include storage services not sanctioned by IT that end-users may use to store work data. Essentially, this is data exfiltration from the sanctioned cloud environment and can lead to data leaks.
Additionally, certain cloud apps may not protect data in-flight and at rest with proper encryption, increasing the likelihood of an attacker being able to compromise business-critical data.
Lack of visibility and control
One of key problems of Shadow IT is that it’s invisible for IT security teams. This makes the control of risky applications impossible. Shadow IT creates substantial security gaps that hackers exploit to attack companies.
More than 40% of file-sharing traffic was routed to unsanctioned apps and services. And 34% of IT teams say the lack of visibility into SaaS security settings is one of the leading causes of SaaS misconfigurations.
Non-compliance
Even if a third-party application is not malicious in nature and is a legitimate tool or extension of the cloud SaaS environment, it may go against compliance requirements or other data access restrictions. Due to specific compliance regulations, organizations may need to expressly limit who or what applications have access to certain data types. When users begin installing third-party applications that have not had a proper risk analysis performed, it can lead to compliance violations.
IT overspending
Up to 50% of IT spending is estimated to go to Shadow IT in large organizations. In many cases, these applications duplicate the functionality of the available and approved solutions. As a result, companies can spend substantial budget on similar applications many of which pose serious danger to their data integrity.
Overcoming Shadow IT: 4 Strategies
1. Regular employee training
As mentioned earlier, many employees engage in Shadow IT operations without even knowing it. They may simply be trying to accomplish day-to-day tasks as efficiently as possible, and installing a third-party cloud SaaS app may seem like the best approach.
Employee cybersecurity training, including training around what constitutes shadow IT operations and how users can avoid using unsanctioned apps, can go a long way in helping to curb their use. Most users want to meet the expectations of the business and align with corporate policies regarding the use of technology and other resources.
Good communication with users from both the business and technology side can help users understand the impact of Shadow IT and how they can avoid becoming involved in using unsanctioned technologies that can compromise business-critical data. In addition, ensure employees have an opportunity to review this information periodically to have the most up-to-date information on corporate technology policies.
2. Providing sanctioned tools
If employees are restricted from using unsanctioned third-party cloud SaaS apps, make sure they have an approved app that allows them to be equally productive. The first step to providing what end-users need is understanding their cloud technology needs. Asking the right questions helps to understand the needs and the proper steps forward:
- What functionality and capabilities do they need to carry out business-critical tasks?
- Is the functionality already included natively in the cloud SaaS environment?
- Have the proper risk assessments been performed on the apps requested? What compliance requirements apply?
Users who feel the business is doing their best to understand their needs and facilitate those with sanctioned applications that align with compliance and governance requirements will be more likely to work in harmony with these requirements.
3. Inventory of cloud SaaS apps
Shadow IT is a tremendous problem in the enterprise because businesses often lack the visibility needed to know which apps are installed and used. Additionally, legacy monitoring and security tools cannot provide the visibility and insights needed in cloud SaaS environments as organizations move to the cloud.
Companies need modern cloud-native cybersecurity tools to understand cloud SaaS application usage, which employees are using them, and which data the apps are accessing. Without visibility and understanding of this aspect of technology usage in your cloud SaaS organization, it will undoubtedly lead to Shadow IT.
Apart from inventory, it’s also important to carry out continuous Shadow IT Monitoring. It will help you detect the applications that users add without the knowledge of IT security team.
4. Enforcing policies for cloud SaaS apps
In addition to employee training, providing sanctioned tools, and having visibility to cloud SaaS apps used in the cloud SaaS environment, businesses must have the technology tools to enforce governance of cloud SaaS apps and their usage. Without the right policies in place, there can still be users who inadvertently use unsanctioned third-party apps. It also helps enforce corporate boundaries for unscrupulous users who may knowingly attempt to use unsanctioned apps.
In addition, many compliance frameworks require appropriate policies and governance guardrails in place to have the correct cybersecurity posture dealing with in-scope or sensitive data. Technology policies help complete the various layers of compliance and security for cloud SaaS environments.
Learn more from our whitepaper “The Ultimate Shadow IT Playbook”
Download the full guide here.
How to Make Shadow IT applications visible
Many organizations may have small or limited IT teams wearing many “hats” of responsibility. Even larger organizations with a security operations center (SOC) can be taxed to perform risk analyses on the thousands of apps available in cloud SaaS marketplaces. In addition to performing risk analyses on cloud SaaS apps, knowing employee behaviors, what they are installing, and which apps they are granting access to would be next to impossible to control using only manual means.
By leveraging next-generation artificial intelligence (AI) and machine learning (ML), organizations can have the technology tools needed to help provide visibility and automated actions required in today’s cloud environments. In addition, AI/ML tools help monitor cloud SaaS environments, detecting anomalies and risks that may be undetected by using manual, human-driven processes.
SpinOne provides an AI/ML-driven solution that helps organizations level the playing field of today’s cloud SaaS apps risks and Shadow IT concerns. It also helps organizations effectively prevent data leaks.
- Continuous risk level analysis of applications – SpinOne provides visibility when users install or uninstall apps in the cloud SaaS environment. It offers automatic reviewing of applications and those that are blocked using SpinOne policies. When SpinOne blocks an app, the app’s access is revoked automatically.
- User behavior analysis – SpinOne provides security information about user behavior, including when they are accessing, applications used, which IP address they are connecting from, and geolocation.
- The shared items control feature helps understand how cloud data is accessed and shared – See which file resources are accessed and any shared files or folders and see if these are shared publicly. You can capture events in historical dashboards. Sensitive information, such as Credit Card Numbers (CCNs), is easily identified
- SaaS security policy orchestration – With SpinOne, you can use granular policies to customize SaaS apps, data audits, and domain audit-related policies to customize cloud SaaS security for your environment. Policies allow for specific rule scopes blocklisting and allow listing, exceptions, and notification settings per-rule basis
- SaaS Data Audit – Using SpinOne’s SaaS Data Audit dashboard, IT admins have quick and ultimate visibility into data shared organization-wide.
- Automated Risk Assessment – SpinOne’s SaaS Risk Assessment module allows businesses to have full visibility into applications integrated into the environment and either allow or block applications based on the continuous risk and scoring provided by SpinOne.
- Ransomware protection – The automated Cloud Ransomware Protection module helps stop any cloud ransomware attack using SpinOne’s automated processes, allowing organizations to eliminate data leaks due to ransomware
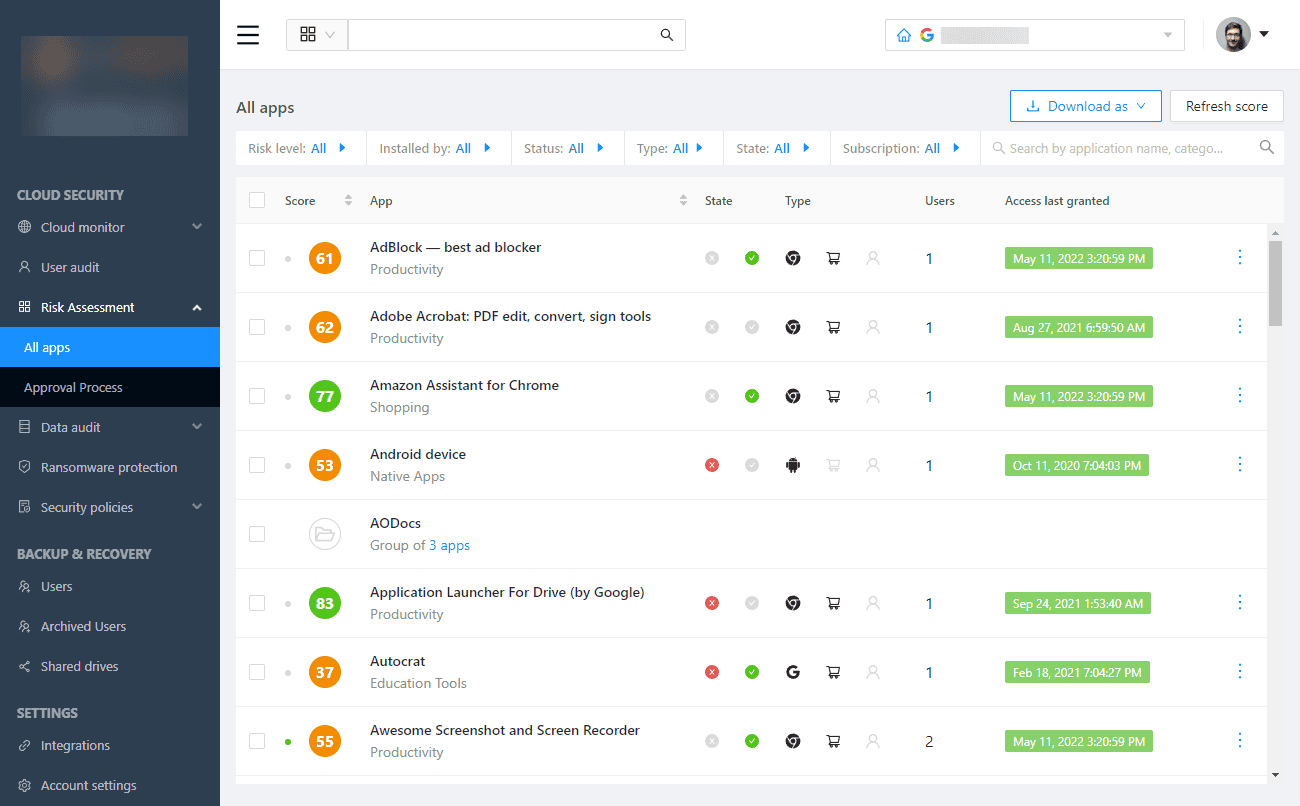
SpinOne provides automated risk assessments of cloud SaaS appsLearn more about how SpinOne can help your organization mitigate Shadow IT threats here: Shadow IT – Tackling SaaS Security Risks with SpinOne
FAQ
What are the potential risks associated with Shadow IT?
The potential risks associated with Shadow IT include zero-day attacks, ransomware attacks, and data leaks.
How does Shadow IT impact an organization’s security posture?
Shadow IT decreases an organization’s security posture significantly as it opens up the entry point for potential hacker attacks, and the IT security team is “blind” to the source of the attack.
What are the challenges in detecting and managing Shadow IT?
The main challenges are the abundance of unauthorized applications as well as the fact that users can launch them any day. Furthermore, the SaaS tools like Microsoft 365 or Google Workspace do not have the necessary functionality to control these apps efficiently.
How can organizations effectively address the issue of Shadow IT?
Organizations can efficiently address the issue of Shadow IT by acquiring tools to control them like SSPM.
What are the potential consequences of ignoring or neglecting Shadow IT?
The potential consequences include legal fines, lawsuits, revenue, and reputational losses due to a cyber attack caused by Shadow IT.
What are some best practices for managing and controlling Shadow IT?
The best practices for managing and controlling Shadow IT include regular Shadow IT monitoring and control, security policies, and using third-party apps.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Expert Insights: SaaS Application Data Protection Fundamentals
March 21, 2024SaaS applications appeal to organizations because they make running the application “somebody else’s problem.” However,... Read more


