Why Native Microsoft Security Features Aren’t Enough

Many businesses using cloud office solutions by Microsoft trust in native Microsoft Office 365 security features. By doing so, they leave significant cybersecurity gaps untreated. This guide will help you define such gaps and close them.
Most if not all organizations today are somewhere in their journey of using cloud technologies. The move to the cloud has accelerated since the onset of the global pandemic in early 2020. Cloud technologies and solutions provide cutting-edge technologies that most organizations would not otherwise have available with on-premises infrastructure. One of the leading cloud SaaS environments is Microsoft Office 365, now Microsoft 365.
Moving data and services to the cloud are not without concern. Security is a vital consideration for organizations using Microsoft cloud services or any other cloud environment for that matter. While Microsoft offers native cloud security capabilities, these may not be enough to meet modern cloud security needs. What native security limitations should you be aware of in Microsoft’s cloud environment? Where does Microsoft’s responsibility end and your responsibility as a customer begin?
Shared responsibility model
Many businesses migrate to cloud environments with misconceived ideas regarding the cloud provider’s responsibility. While cloud service providers are responsible to a certain point, ultimately, you as the customer are responsible for your data and the security of that data. This dual responsibility is known as the shared responsibility model as defined by today’s cloud providers. What is the shared responsibility model, and how does it affect the security and protection of your data?
Shared responsibility essentially defines where the cloud service provider’s responsibility ends and the customer’s responsibility begins. For example, in Microsoft’s “7 steps to a holistic security strategy” whitepaper, note the following graphic detailing the shared responsibility of Microsoft and customers.

Microsoft shared responsibility model
While the graphic seems to indicate Microsoft takes care of all the security concerns, note the following from the same whitepaper.
“Security is a shared responsibility. While the cloud provider needs to provide state-of-the-art security and encryption, you as their customer must ensure that the services you’re purchasing are in fact secure and you’re extending required security policies into your cloud resources.”
As mentioned, it is up to your business to define the appropriate security policies that protect your organization from security threats and take the responsibility to do so. The pressing burden of security falls to the customer.
Microsoft’s cloud offerings provide access to many native security solutions designed to help protect your business-critical data from attack or loss. However, are these enough?
Areas lacking with native Microsoft security features
While Microsoft offers a wide range of various security solutions across their portfolio of cloud service offerings, these are significantly lacking in a few areas. What are these?
- Weak ransomware protection
- No native backups and limited retention
- Limited data sharing visibility
- Multiple dashboards and disjointed security tools
- Multiple subscription levels and bolt-on security services
1. Weak ransomware protection
Ransomware is arguably the number one threat businesses need to be thinking about when protecting their business-critical data. Unfortunately, there is a good chance that if your company hasn’t already been affected by ransomware, it will be at some point in the future. According to recent projections from cybersecurity analysts, a business will be attacked by ransomware every 11 seconds in 2021.
Microsoft has a few solutions in place for protecting Microsoft 365 against ransomware. One of these is ransomware protection and recovering your files. Ransomware protection is a solution that notifies you when your company’s data housed on OneDrive has been attacked. When Microsoft detects a ransomware attack, you get a notification on your device and receive an email from Microsoft 365. What does the notification from Microsoft include? The notification in the email will contain details of what triggered the alert and steps to walk through the recovery process.
Once you log in to the Microsoft 365 portal, you will see the Signs of ransomware detected screen when navigating to OneDrive.
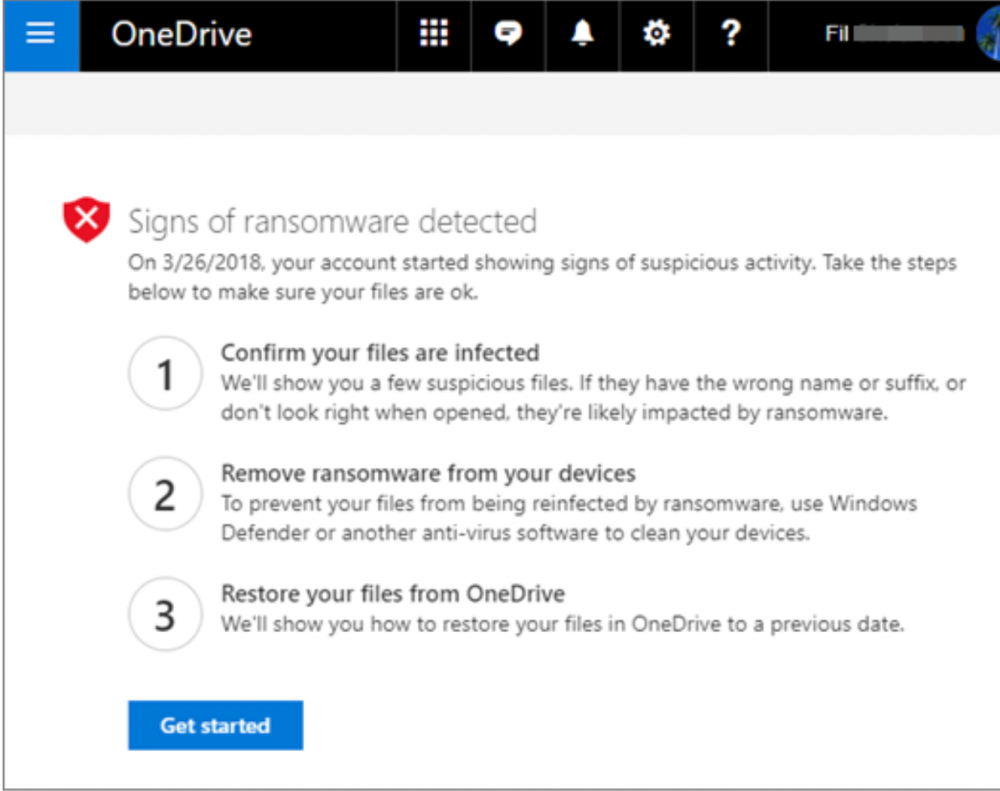
Signs of ransomware detected by Microsoft
You will need to confirm your files are encrypted and then begin the restore process. What does the recovery process include? You first need to verify your files are infected, clean all your devices, and then restore your OneDrive data.
Doesn’t file versioning help organizations who have been attacked by ransomware in the Microsoft cloud? Potentially. However, there are some cases where even Microsoft says file versioning in OneDrive, SharePoint, and other services is not the “end all be all” solution for a ransomware attack. Microsoft mentions in their Malware and ransomware protection in Microsoft 365 support document:
“Versioning helps to protect SharePoint Online lists and SharePoint Online and OneDrive for Business libraries from some, but not all, of these types of ransomware attacks.”
In today’s very technology-dependent environments where end-users need access to data constantly, detecting a ransomware attack and quickly stopping the attack is crucial to recovery. There are a couple of significant issues with the native protection afforded by Microsoft against ransomware.
As detailed above, the ransomware solution from Microsoft in Microsoft 365 is simple ransomware detection, not prevention or protection. The protection is reactive and not proactive. It means you and your business are in a reactive stance with the ransomware infection. Microsoft alerts you that your files have been/are getting encrypted. However, it does not actively do anything to stop the infection. Instead, with the native Microsoft ransomware detection service, you are only notified of the infection and then walked through the process of restoring your data.
As detailed, file versioning is not a bullet-proof solution when it comes to ransomware. It is also not a standalone backup of your data. Since Microsoft, like most other cloud service providers, does not provide a native backup solution built into Microsoft 365, you only have file versioning. So, what happens if your data is not recoverable from the standpoint of a file version?
2. No native backups and limited retention
With the Microsoft 365 cloud SaaS environment, there are no native solutions positioned as proper “backups” of your data. File versioning is a solution that can provide a safety net in some situations. However, file versioning is not a true standalone backup copy of your data stored safely outside the Microsoft cloud environment.
Additionally, there are certain limitations with the data Microsoft retains on your behalf, including retention for deleted items and also for the file versioning mechanism itself. OneDrive ransomware recovery allows you to recover previous file versions for up to 30 days before the date of the ransomware attack. While 30 days may not be limiting for many environments, there are certainly cases where businesses might need to go back further, creating a recipe for disaster for those who are simply relying on the built-in file versioning.
Note the following documented data retention, deletion, and destruction in Microsoft 365.
| Data Category | Data Classification | Description | Examples | Retention Period |
| Customer Data | Customer Content | Content directly provided/created by admins and users
Includes all text, sound, video, image files, and software created and stored in Microsoft data centers when using the services in Microsoft 365 |
Examples of the most commonly used Microsoft 365 applications that allow users to author data include Word, Excel, PowerPoint, Outlook, and OneNote
Customer content also includes customer-owned/provided secrets (passwords, certificates, encryption keys, storage keys) |
Active Deletion Scenario: at most 30 days
Passive Deletion Scenario: at most 180 days |
| Customer Data | End User Identifiable Information (EUII) | Data that identifies or could be used to identify the user of a Microsoft service. EUII does not contain Customer content | User name or display name (DOMAIN\UserName)
User principal name (name@domain) User-specific IP addresses |
Active Deletion Scenario: at most 180 days (only a tenant administrator action)
Passive Deletion Scenario: at most 180 days |
| Personal Data (data not included in Customer Data) |
End User Pseudonymous Identifiers (EUPI) | An identifier created by Microsoft tied to the user of a Microsoft service. When combined with other information, such as a mapping table, EUPI identifies the end user
EUPI does not contain information uploaded or created by the customer |
User GUIDs, PUIDs, or SIDs
Session IDs |
Active Deletion Scenario: at most 30 days
Passive Deletion Scenario: at most 180 days |
Microsoft’s retention policy forces businesses to conform to Microsoft’s retention policy for their data and not the data retention policy that aligns best with their company. There is no question. If organizations want to effectively align their data backups and retention policy to their business needs and protect their data according to industry best practices, a third-party backup solution is required.
3. Limited data sharing visibility
It is essential for IT admins and SecOps alike to have visibility and control over data sharing in the Microsoft 365 environment. Due to the ease of data sharing in the Microsoft 365 organization, sensitive data can easily leak from the environment. Therefore, your business must maintain both visibility and control over data sharing for compliance and security purposes.
Microsoft provides native tools to control data sharing. Native controls allow defining the types of guests to which content is shared and defining users in specific groups to share data externally.
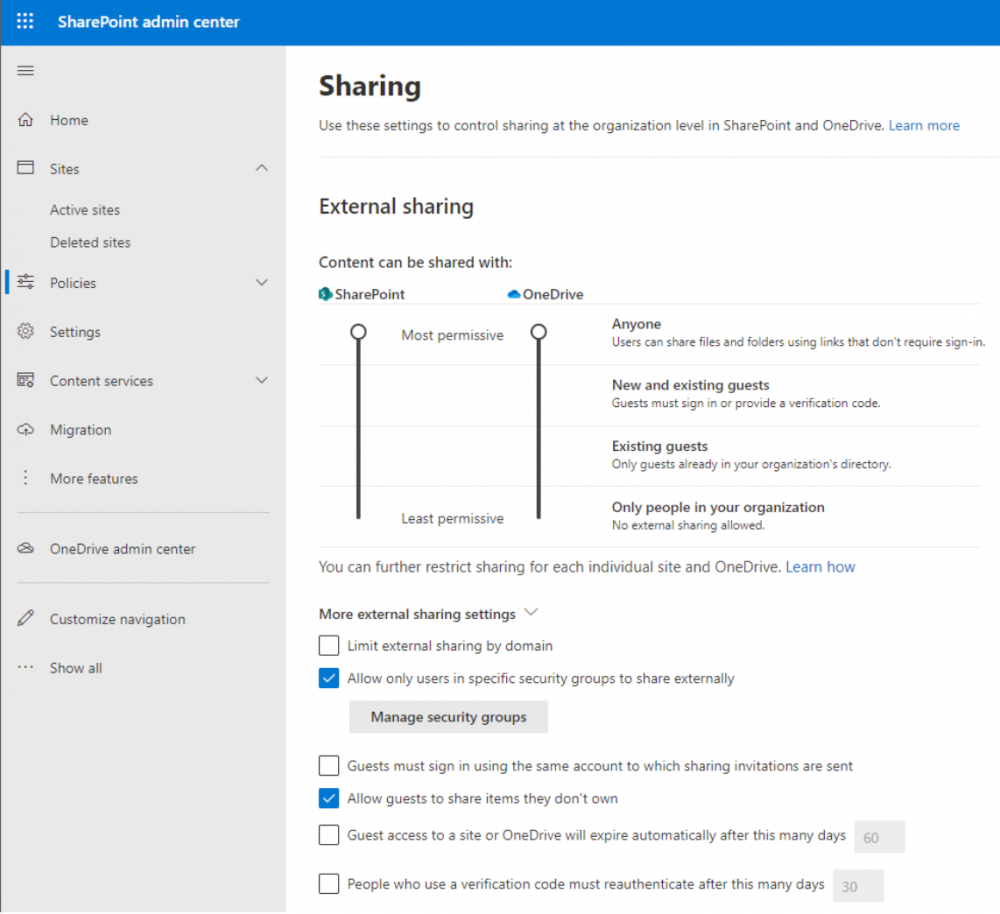
Configuring advanced sharing settings in Microsoft 365 for SharePoint and OneDrive
While controls exist to set boundaries on sharing for the Microsoft 365 organization, easy visibility to which data is shared can be cumbersome. Admins can enable the auditing of data sharing in Microsoft 365. However, easy access to viewing the sharing data collected tedious. It involves paying attention to the sharing workflow as outlined by Microsoft, which includes:
- Searching the Audit log
- Export results to CSV
- Use PowerQuery Editor to format the exported audit log
- Filter the CSV file for resources shared with external users.
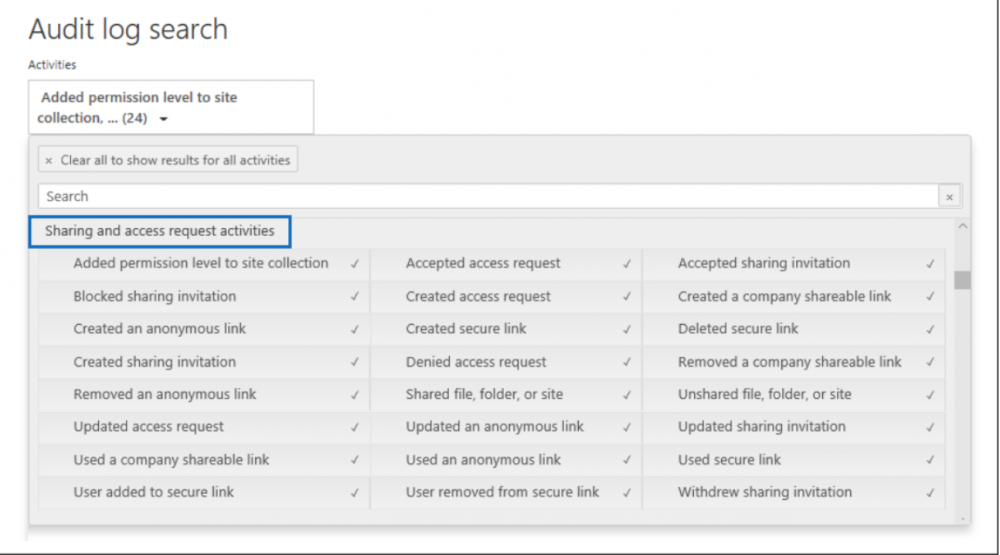
Searching the audit log for data sharing events
When processes are tedious and cumbersome when related to data sharing visibility, there is a high likelihood that data may be shared inside or outside the organization to undesired recipients and security teams missing these security events.
4. Multiple dashboards and disjointed security tools
One of the barriers to implementing seamless security in Microsoft 365 is the multiple tools and dashboards customers have to view for querying information and gaining visibility. There is no single-pane-of-glass tool that provides all the security information in one place. As shown above, the simple act of performing data sharing audits requires using multiple tools and processes to view this information.
Public cloud service providers such as Microsoft and others have an issue of tools and dashboards bloat that can get in the way of effective security processes, visibility, and controls.
5. Multiple subscription levels and bolt-on security services
Customers housing data and services in the Microsoft 365 cloud must also give attention to the multiple subscription levels. Choosing a specific M365 subscription level changes which built-in security services and tools are available to secure the environment. For example, the higher-level enterprise subscriptions contain the Advanced Threat Protection offerings by default. However, lower-level subscriptions may require additional security services to be added at extra cost for similar functionality.
SpinSecurity – Resolving Microsoft native cloud security gaps
When we perform an overall look at gaps in the security features provided in the Microsoft cloud, it is apparent that organizations need a third-party solution to bolster their Microsoft cloud security. SpinSecurity provides a comprehensive, next-generation solution, leveraging artificial intelligence (AI) and machine learning (ML) to both protect and secure your business-critical data.
SpinSecurity provides key features that help organizations have automated security intelligence protecting their environment. These features include:
- Artificial Intelligence-powered ransomware detection
- 24x7x365 automated monitoring
- AI-based ransomware recognition
- Alerts and Analytics
- Stop the ransomware attack
- Automated ransomware restore
The automated ransomware response provided by SpinSecurity provides world-class ransomware protection. It transcends beyond the simple “reactive” stance cloud service providers take and allows your business to go after ransomware attacking your data proactively. Note the four-step automated ransomware protection approach:
- Detect a ransomware attack
- Stop the encryption process
- Identify encrypted files
- Recover files automatically
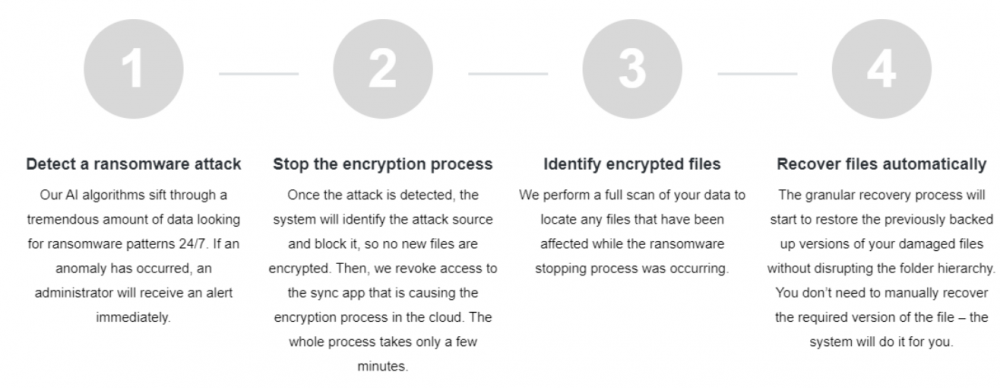
Overview of the SpinSecurity automated ransomware protection
With SpinSecurity, your business is not simply notified of a ransomware attack. Instead, the automated processes start to work immediately – automatically stopping the ransomware and recovering any affected data. The automated recovery of business-critical data is made possible by automated backups of your SaaS data that align with your retention policies, not Microsoft’s. In addition, Spin allows unlimited data retention to provide the restore points needed for your business.
Learn more about how Spin can bolster your Microsoft 365 security here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more
Expert Insights: SaaS Application Data Protection Fundamentals
March 21, 2024SaaS applications appeal to organizations because they make running the application “somebody else’s problem.” However,... Read more


