Risk Assessment for OAuth Apps & Browser Extensions
Risk Assessment and Access Management allows administrators to take full control of their environment and mitigate Shadow IT.
SpinOne detects and assesses all OAuth applications and Browser Extensions that have access to user data, taking into consideration over 20 different categories per app!
Let’s dig deeper into the module and uncover more of its functionality!
By heading into the Risk Assessment section from the left panel of your dashboard, you will immediately see a list of all OAuth apps and Browser Extensions connected to your organization. Let’s understand what the sections highlighted in the below screenshot mean.
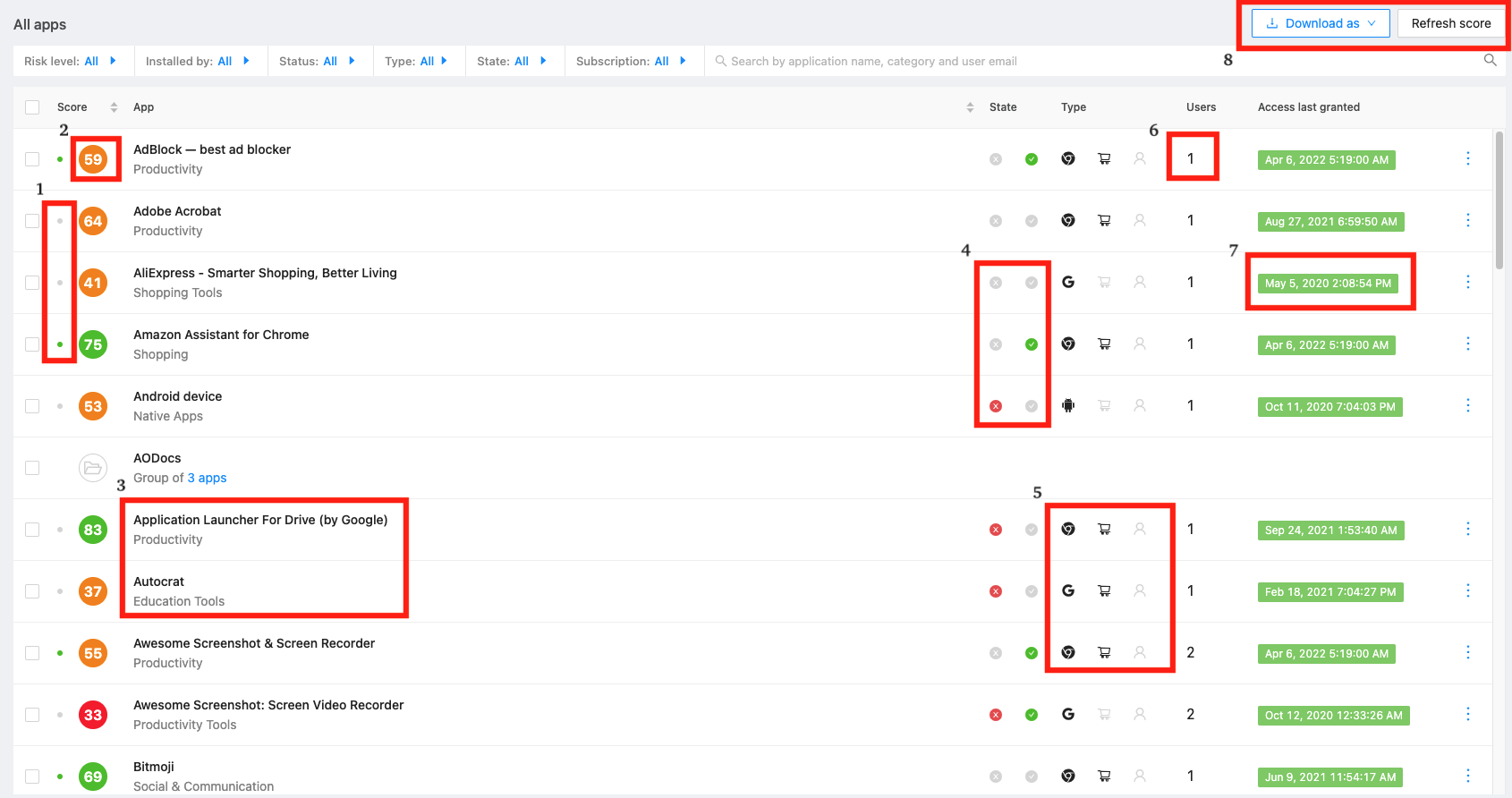
1. Status – The presence of a green circle will indicate that the application is currently active and has access to data, whereas a gray circle indicates inactive apps.
2. Score – This is the score associated with the application as a result of the assessment. The higher the score, the less risks it can impose.
3. Name & Category – The name of the application as provided along with the category if detected.
4. State – Will display whether the application has been sent to the Allowlist/Blocklist classifications.
5. Type – The type section is broken down into 3 sections. First, it will show whether the app is a Web app, iOS, Android, etc. The other two sections will display whether the app is installed from an official marketplace (such as Google Workspace™ Marketplace https://workspace.google.com/marketplace/) and will show if the application has been installed by an administrator for everyone in the organization.
6. Users – Provides insights as to how many users have access to the application.
7. Access last granted – Insight as to when the OAuth token between users and the app was last refreshed.
8. Settings – Ability to extract the list of all apps to a local device, or launch a Refresh of all apps in your organization.
Now, click on any app to uncover a more in depth assessment and to understand why an app has received the score it has.
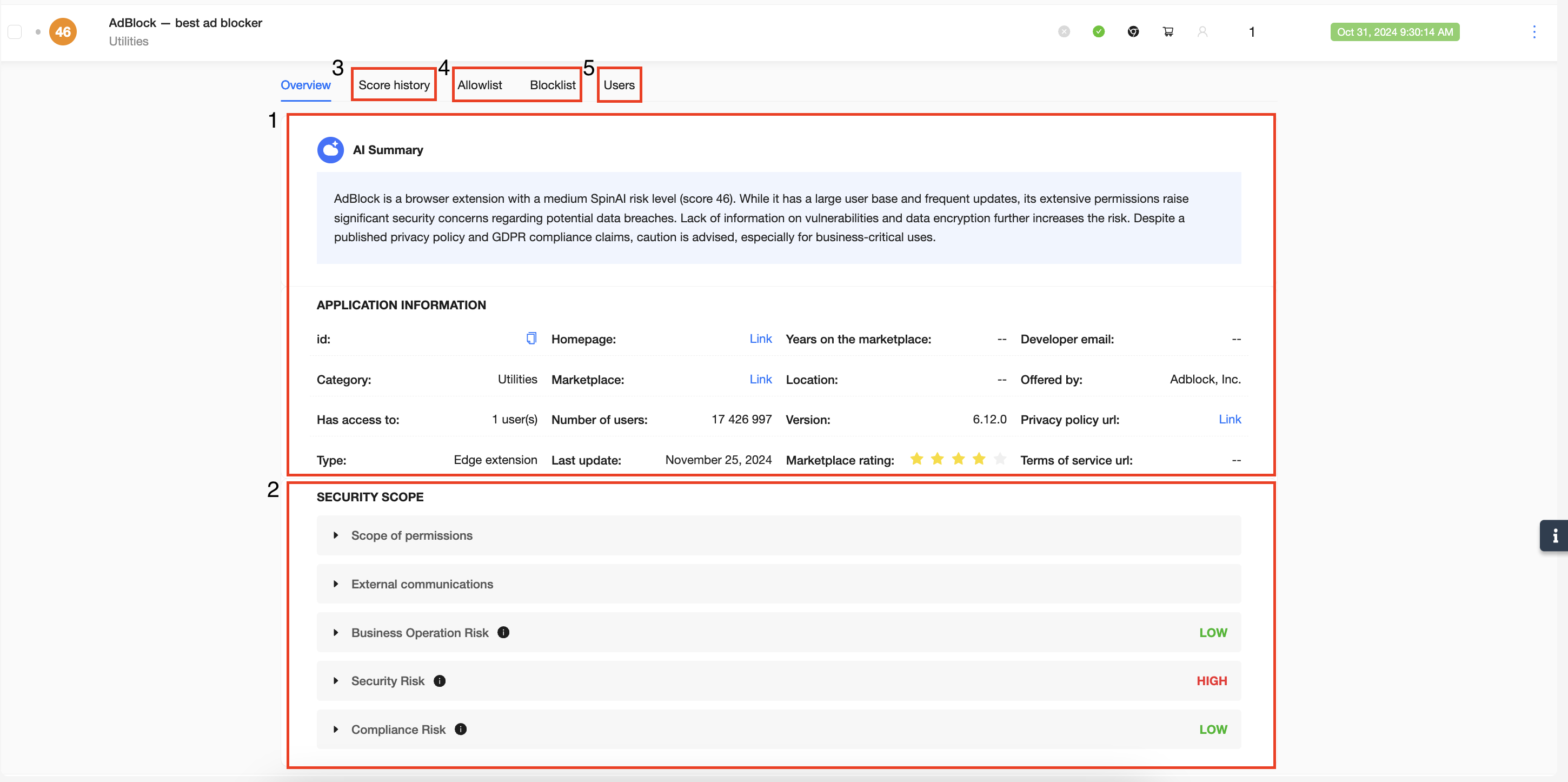
1. AI Summary & Application Information – A quick AI generated summary of the entire application assessment report, including information about the application from the marketplace.
2. Security Scope – This is the section where the assessment of the application is done. It outlines the full Scope of permissions the application requests upon installation, any external communication an app or extension may make, and then displays the Business, Security and Compliance assessment performed by SpinOne. The combined assessment of these 3 sections determines the score of the application. If there have been any vulnerabilities detected, they will be listed on the bottom.
3. Score History – You can find previous assessments of the application here if there has been changes. The Score History section will also be able to generate an AI summary on exactly what changed between any two assessments.
4. Allowlist/Blocklist – In these sections, admins can send the application to the Blocklist or Allowlist for everyone in the organization, or for certain Users/Security Groups.
5. Users – A list of all users along with their email addresses that have access to the application.
If you don’t agree with the score provided to an application, feel free to Suggest an improvement by clicking the three dots on the right hand side of each app. Include as much information and detail as possible, and you will be connected with our Security department.
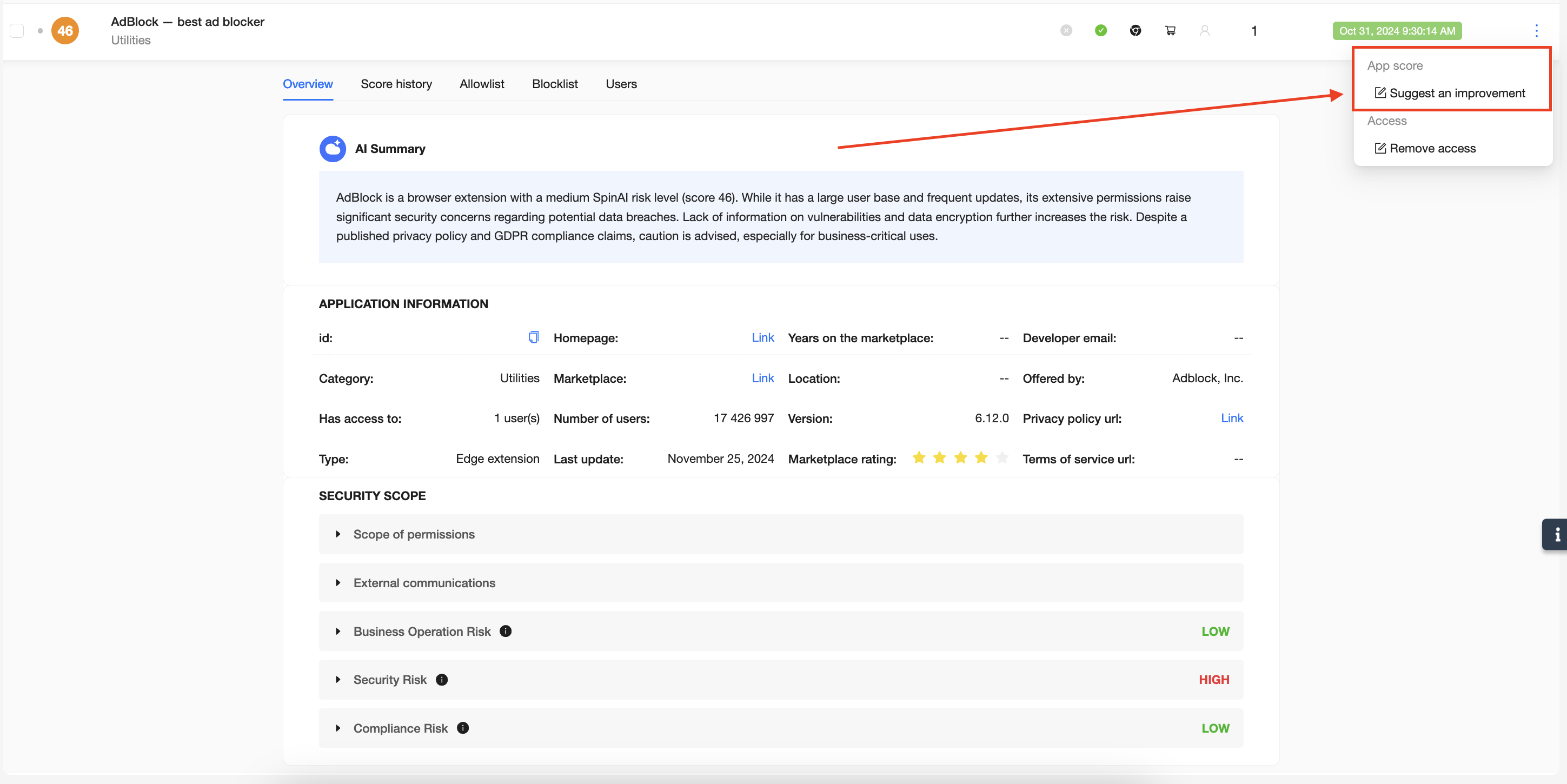
Now, you can take a look at all applications that have access your data and can understand why they have received their corresponding Risk score. Following this, you can make decisions around which applications to Blocklist/Allowlist.
To help you automate these processes, SpinOne allows you to create Security Policies. Be sure to check out the available Default Policies, and also learn how to create your own policies here.
Get more information on Google Workspace™ Backup Solutions