Insider Threat
Protect your critical SaaS data against insider threat with SpinDLP

Insider Threat Use Case
Unfortunately, sometimes the biggest threat to your SaaS security is inside your own organization. Insider threat refers to employees, former employees, contractors, or business associates that (often maliciously) share files and data outside the organization, grant access to unauthorized users, or intentionally delete or download sensitive SaaS data or IP.
Impact of Insider Threat

Reduce the Risk of Insider Threat
Visibility and Control over Data Sharing

Combating insider threats means understanding when data is shared, where it is shared, and by whom. You need a solution that provides policy-based, automated controls over data sharing, aligning your business with compliance regulations.
Automated Alerts and Incident Response
With automated, policy-based controls over data sharing and third-party SaaS apps and extensions, you can quickly gain control over data access and align with compliance objectives. Set thresholds and get customizable notifications on abnormal login, data downloads, or transfers by your users to take timely action.

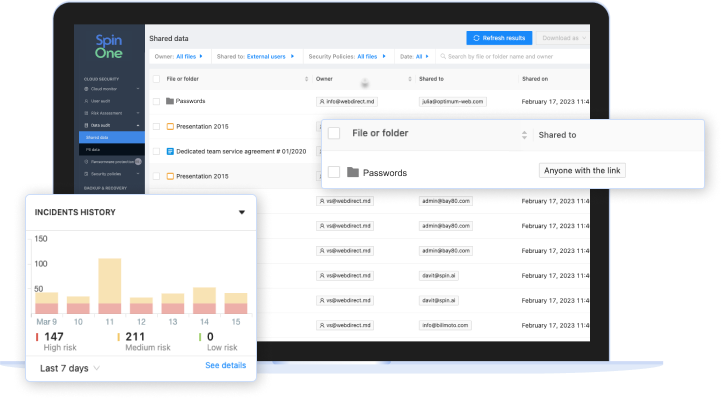
SpinOne Data Leak Prevention and Data Loss Protection (SpinDLP)
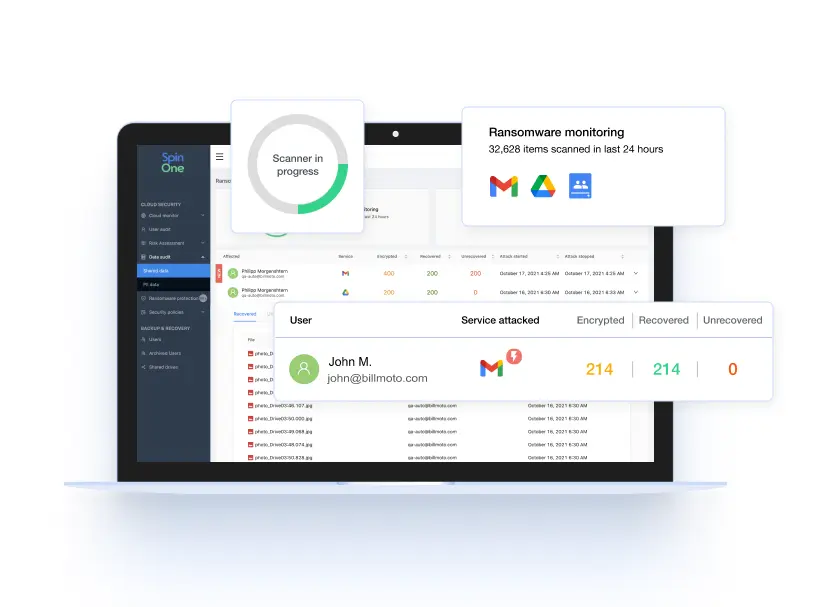
Protect your sensitive SaaS data against insider threat with complete visibility and swift, fully automated incident response from SpinDLP, a solution within the SpinOne platform.
Improve compliance with automated protection and reduce security issues by 95%.
Why Businesses Choose SpinDLP
Related Resources
Your SaaS Security starts with SpinDLP
Frequently Asked Questions
What is the definition of insider threat?
Insider threat refers to any threat that comes from business workers – meaning a current or former employee, a contractor, an associate, or any other worker who intentionally or unintentionally exposes the company’s SaaS environment to cyber risk. Especially with hybrid or remote work, the risk of insider threats can devastate an organization quickly.According to the Cost of Insider Threats by IBM Security, “Negligent employees or contractors were the root cause of 2,962 of the 4,716 incidents reported.”
Why is insider threat a risk to my business?
Insider data breaches could cost your business billions and cause significant damage to your brand and bottom line. Insider threat can also cost you:
- Theft or loss of mission-critical data or intellectual property
- Unauthorized access to sensitive data
- Costly downtime on organizational productivity
- Legal and regulatory impacts, including litigation defense cost and fines
- Loss of confidence and trust among key stakeholders
- Deterioration of marketplace brand and reputation
According to IBM’s Cost of Insider Threats: Global Report 2020, companies spend an average of USD 644,852 on each incident caused by insider threat because of the following:
- Negligent or inadvertent employee or contractor
- Criminal insider including employee or contractor malice,
- Employee/user credential theft (a.k.a. imposter risk)
How can I prevent the risk of insider threat?
Regular SaaS data audits are a strong strategy to prevent the risk of insider threat with an overall view of your SaaS environment.
Solutions like SpinDLP help SecOps and IT teams with inside threat detection. They provide monitoring of SaaS environments and help identify unauthorized access, sensitive information sharing, and data theft. SpinDLP also helps set security policies to enhance insider threat prevention.
What are the key features of SpinDLP that prevent insider threat?
SpinDLP is a cybersecurity solution that detects anomalous activities, SaaS data misuse activities, and other cybersecurity risks across your cloud data environment. SpinDLP helps protect against insider threats and data misuse by continuously monitoring your enterprise’s cloud data, and allowing you to:
- View all data shared in the cloud SaaS environment
- View ownership of files
- Audit users with whom data has been shared
- Apply rules to files based on SpinOne security policies
- Quickly see files that are shared externally to the public
- Discover sensitive information such as credit card numbers (CCNs) shared using email
- View and sort data by an individual
- Generate data audit reports and export the audit reports as needed
What specific solutions does Spin.AI utilize to monitor and detect insider threats?
Spin Data Leak Prevention and Data Loss Protection (SpinDLP) provides complete visibility over who can access, share, or modify sensitive data and offers swift, fully automated incident response.
Can Spin.AI secure my systems from insider threats while employees work remotely?
Yes, SpinDLP can significantly improve your remote work security posture and mitigate insider threats by helping you define and enforce policies that restrict access to sensitive data, monitor employee activity related to sensitive data, trigger alerts for security personnel, and even block attempted data transfer in real-time.
Can SpinDLP monitor administrators?
As long as the accounts are licensed under SpinDLP, it monitors the accounts regardless of whether they are users or administrators.
How does SpinDLP mitigate insider threats in real time?
SpinDLP mitigates insider threats in real time by monitoring user behavior, analyzing activity logs, and enforcing data loss prevention policies. Leveraging machine learning and behavioral analytics, it detects anomalies and triggers automated responses such as access restriction and alert escalation.


