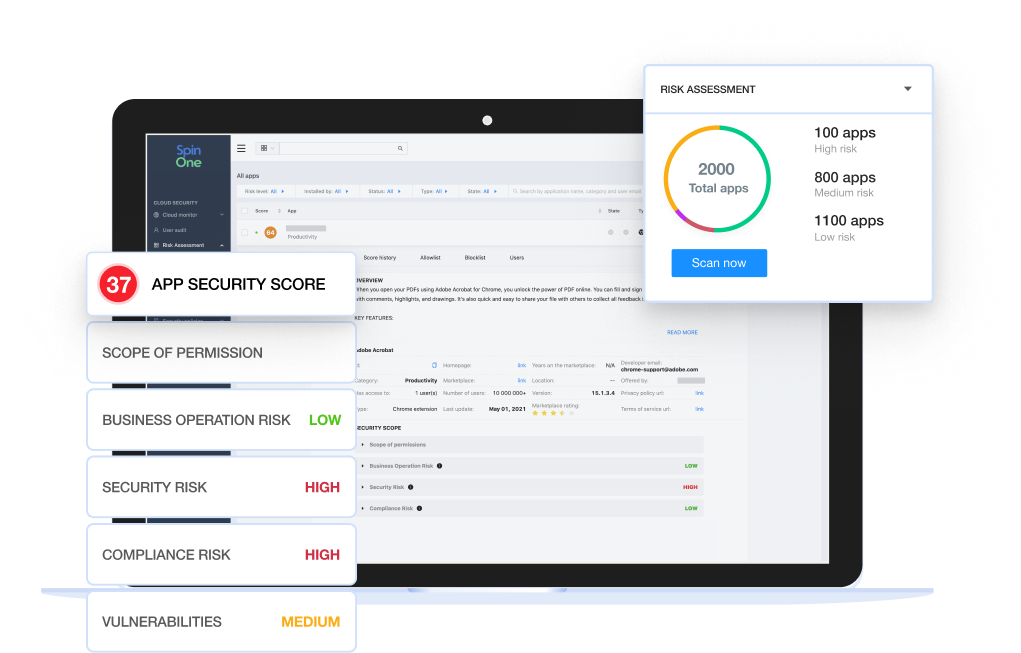
Compliance Risks
Steer clear of common compliance risks with SpinOne

Compliance Risks Use Case
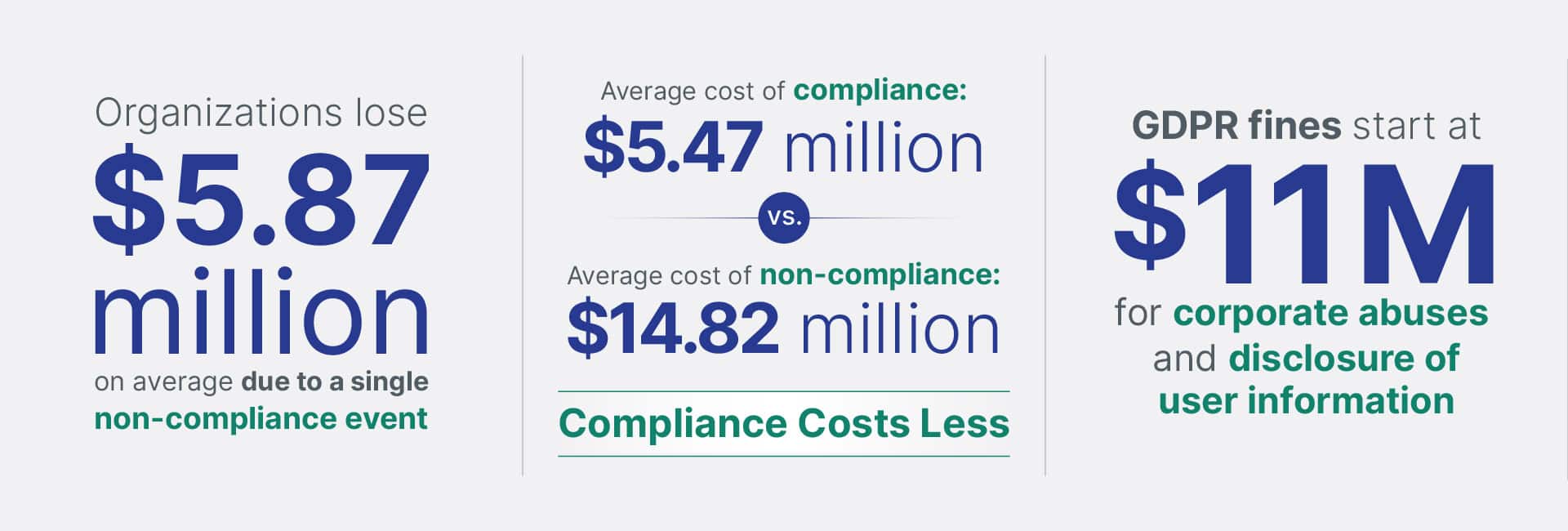
Did you know that the cost of non-compliance is nearly three times higher than the cost of implementing proper compliance solutions?
GDPR, ISO, NIST, NIS2, and other regulations require secure sensitive data backups. But you also need a SaaS security solution that goes beyond backup to help you meet your governance, risk, and compliance requirements.
Impact of Non-Compliance
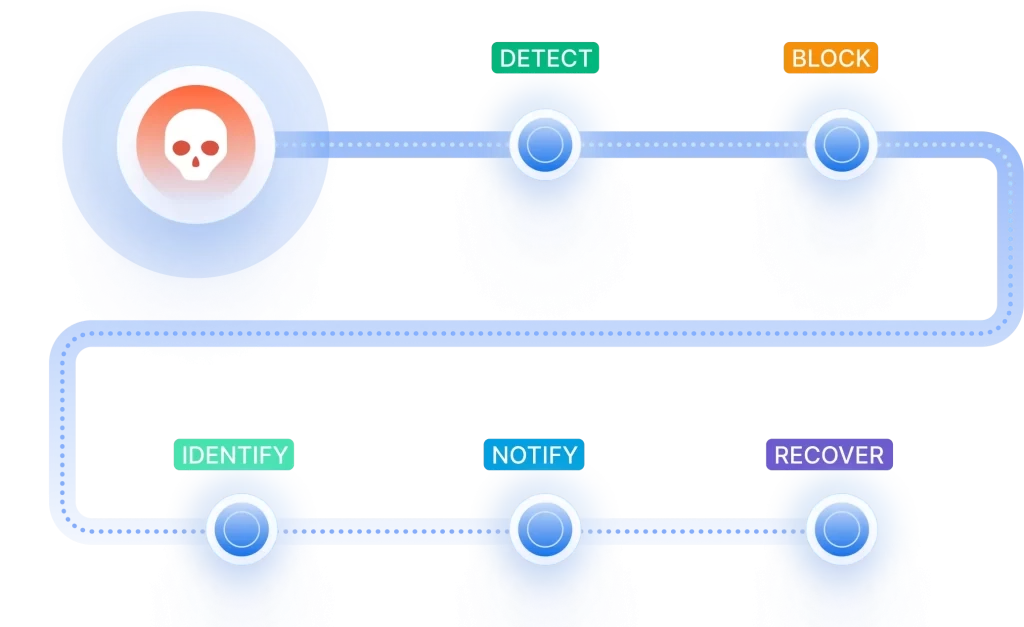
Reduce the Risk of Non-Compliance

Secure 1x or 3x Daily Backups

Secure backups help you meet compliance and local regulations. To do this, you need to backup your critical SaaS data with 1x/3x a day cloud-to-cloud backups to secure cloud storage at locations around the world.
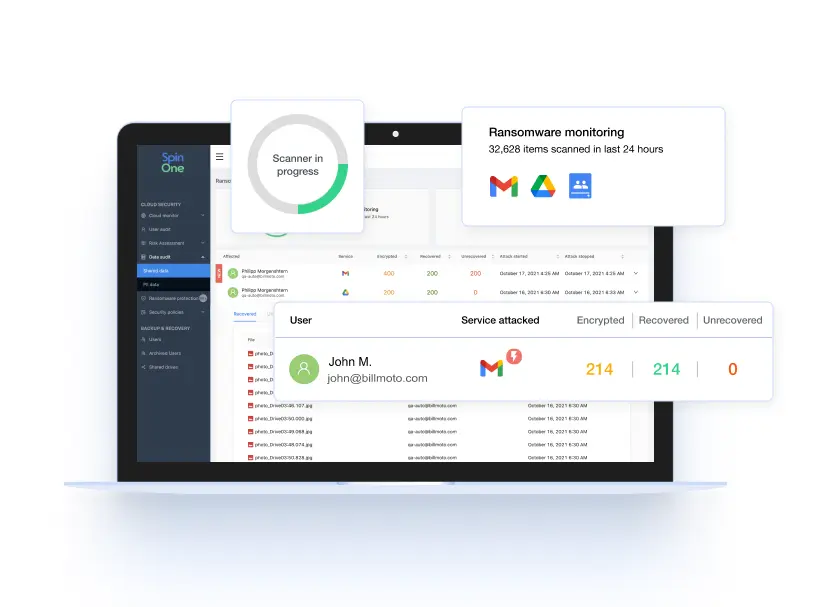
Granular, Automated Policies
With automated policy-based controls over data sharing and third-party SaaS apps, you can quickly gain control over your SaaS data and align with compliance objectives. Set thresholds and get immediate, customizable notifications on abnormal login, data downloads, or transfers by your users to take timely action.

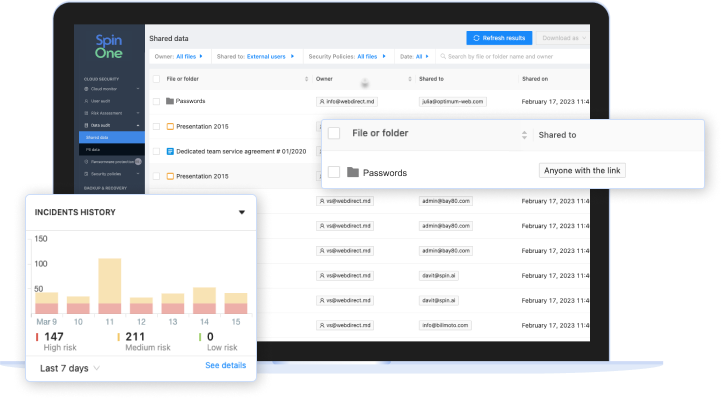
Sensitive Data Protection
Sending, storing, or sharing sensitive information is a breach of compliance regulations. You need proactive data leak prevention and data loss protection measures to deter unwanted removal of sensitive information and avoid devastating impacts on customer trust and regulatory compliance.

Misconfiguration Management
To protect your SaaS data, you need to ensure that configurations and 3rd party apps and extensions meet compliance standards. Just one misconfiguration can open the door to unauthorized access – leaving your SaaS data in environments like Google Workspace, Microsoft 365, and Slack vulnerable to potential security and compliance risks. SaaS security posture management (SSPM) solutions can reduce the risk of non-compliance.
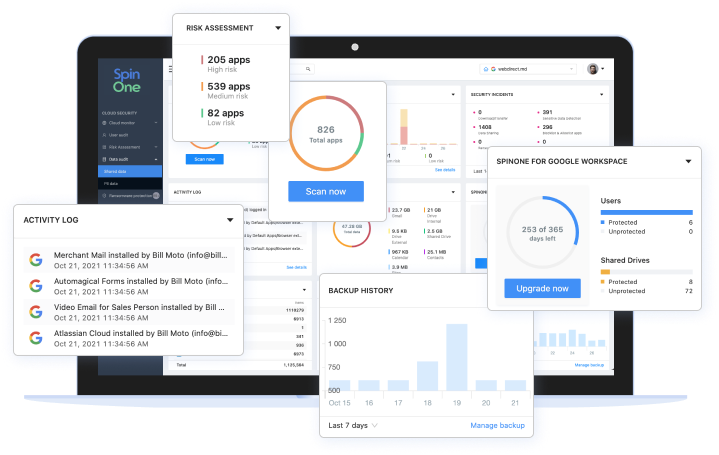
SpinOne
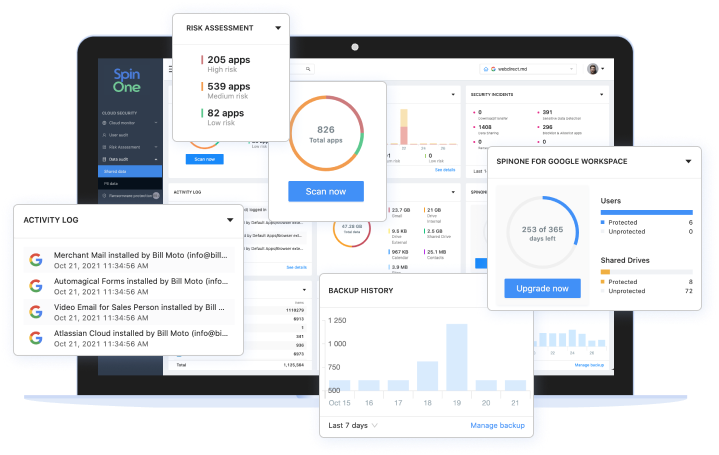
Reduce the risk of non-compliance with the SpinOne platform. Protect your SaaS data in Google Workspace, Microsoft 365, Salesforce, and Slack: mitigating risk, preventing data loss and leak, reducing downtime, saving time for Security Operation teams, and improving compliance.
Why Businesses Choose SpinOne
Related Resources
Your SaaS Security starts with SpinOne
Frequently Asked Questions
Why is compliance important?
Cloud-based SaaS solutions are becoming the leading technology for all businesses. The three most important reasons business leaders opt for this technology are scalability, on-demand functionality, and lower costs. Integrating a third-party application with your cloud SaaS environment allows bridging any gap between your products or services, giving you the ability to find solutions for your business needs instantly.
When integrating a third-party application with your cloud SaaS environment, security teams have to consider the risks of granting external applications access to your business-critical data and your cloud environment. Users can easily integrate third-party applications into cloud SaaS environments when no controls are in place.
Businesses of all sizes must be prepared to keep their SaaS data safe, track who accesses it, and know where it’s located at all times. With visibility into security settings across an entire cloud environment, you can monitor and audit access to sensitive data sets, including where data assets are stored and which applications may be sharing information with personal devices or external services.
“The increasing ubiquity of cloud and mobile adoption can reduce the visibility and control that IT security teams have over organizational risk exposure.”
— Craig Lawson, research vice president at Gartner
What are examples of common SaaS compliance concerns?
- User activities — For effective compliance and security visibility, companies must have visibility into end-user activities and understand what users are doing, what data they are accessing and sharing, and where and on what devices they are accessing it.
- SaaS Applications – Cloud applications have revolutionized the work of organizations. But, as with any technological advancement, there are associated risks. Security challenges pose the biggest threat to cloud-based applications and services, as users are prone to attacks from both internal and external sources.
- SaaS Data Protection – Data is the new oil, and businesses need to protect it. As a result, companies must protect their business-critical SaaS data from many different risks, including human error and malicious threats such as ransomware.
- Shadow IT – A growing concern for IT and security teams, shadow IT poses the risk that the security team will not be aware of the SaaS applications being used by employees, reducing the ability to monitor for malicious activity or data exfiltration.
What are the key features of SpinDLP that enable compliance?
With SpinDLP, you can create custom policies to automate the security processes for SaaS apps, data, and domain-related activities.
- 24/7 monitoring
- SaaS Security policy orchestration
- Security scoring for SaaS apps and browser extensions
- Automated allowlisting, blocklisting, or customized responses
- Immediate security alerts via email and Slack
- Account data archiving
- Audit logs and activity history
SpinDLP also lets you apply granular Security Policies to SaaS applications that meet multiple criteria, including:
- Application category
- Application ID
- Developer
- Scope of permissions
- Application Risk Score
- OAuth permissions delegation
- Chrome Extensions
What specific compliance standards and regulations does SpinOne address?
SpinOne helps businesses maintain compliance with HIPAA, PCI DSS, GDPR, CCPA, ISO, NIST and many other regulatory laws, regulations, and standards.
Can SpinOne substitute for an official information security risk assessment process required by most data security regulations and standards?
SpinOne offers a continuous risk assessment of your SaaS-based applications. While the solution provides valuable insights into the users’ SaaS environment, it still cannot substitute a long-term documented process required by HIPAA, PCI DSS, and other regulatory requirements. The security risk assessment process mandated by most regulations and standards requires a comprehensive evaluation of an organization’s entire infrastructure, including hardware, software, networks, personnel, and processes.
Can SpinOne provide insights and recommendations for improving overall compliance posture?
Yes. SpinOne includes backup and recovery, ransomware detection and response, data leak prevention, and security posture management functionalities. All these functionalities can work towards improving your overall compliance posture.
We are on the way to our HIPAA compliance. Can SpinOne assist in conducting compliance audits and evaluations?
While SpinOne doesn’t perform compliance audits and evaluations, it offers features tailored to healthcare organizations, including data protection, access controls, and activity monitoring within cloud applications like Google Workspace, Microsoft 365, Slack, and Salesforce. SpinOne can generate reports, analyze security configurations, and provide insights to help organizations assess their compliance status and identify areas for improvement in alignment with HIPAA requirements.
Does Spin.AI assist organizations in maintaining compliance documentation and records?
No. It is the organization’s responsibility to maintain compliance documentation. SpinOne can provide insights to help organizations assess their compliance status and identify areas for improvement in alignment with regulatory requirements.


