Misconfiguration Management
Quickly detect and proactively manage security misconfigurations with SpinSPM

Misconfiguration Management
Security misconfigurations are widely regarded as the top cloud threat – stemming most commonly from simple human error, default settings left unchanged, erroneous configuration changes, or even new applications added without proper risk assessment.
Just one misconfiguration can open the door to unauthorized access – leaving your SaaS data in environments like Google Workspace, Microsoft 365, and Slack vulnerable to potential security and compliance risks.
Impact of Misconfigurations
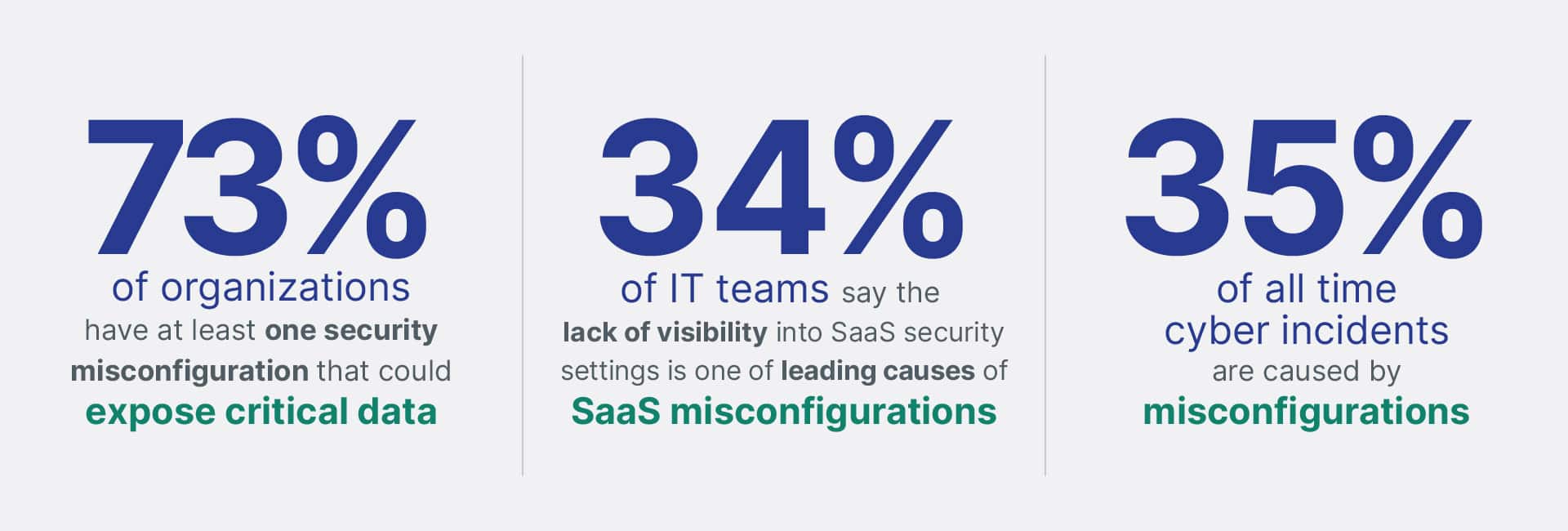
Reduce the Risk of Misconfigurations
Automated Misconfiguration Management & Alerts
To keep up with the constantly evolving risk of misconfigurations, security drifts, and compliance breaches within your SaaS applications, you need automated detection and fast incident response on your side. Get immediate, customizable alerts for detected misconfigurations from a single, integrated dashboard using SaaS Security Posture Management (SSPM) solutions.
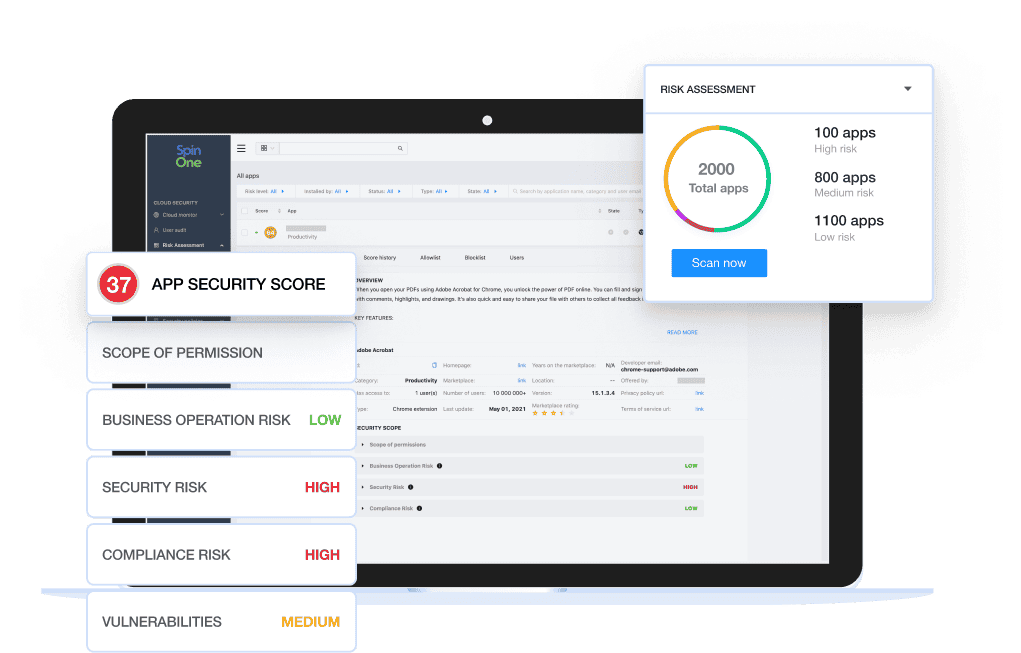
Continuous Risk Assessment
New, unknown third-party apps and extensions are constantly being introduced to your SaaS environment. To avoid potential misconfigurations, you need to be able to detect when these third-party apps or extensions are installed, uninstalled, or even updated – then automatically review or block any potential risks with continuous reassessment.

Spin SaaS Security Posture Management (SpinSPM)
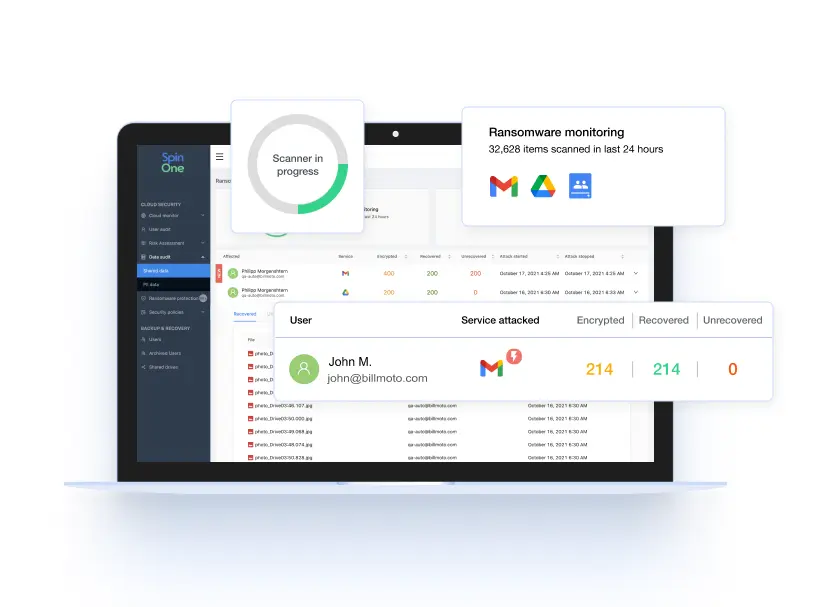
Mitigate and eliminate misconfigurations in your SaaS environment with full visibility and fast, automated incident response from SpinSPM, a solution within the SpinOne platform. Slash your risk assessment time from weeks manually to seconds automatically.
Why Businesses Choose SpinSPM
Related Resources
Your SaaS Security starts with SpinSPM
Frequently Asked Questions
What is a security misconfiguration?
A security misconfiguration occurs when system or application configuration settings are missing or are erroneously implemented, allowing unauthorized access. Common security misconfigurations can occur as a result of leaving default settings unchanged, erroneous configuration changes or other technical issues.
Why is managing misconfigurations important?
SSPM helps correct SaaS misconfigurations
One of the risks associated with using cloud SaaS applications is not always due to an inherent security vulnerability in the cloud SaaS application itself, but rather the organizations’ misconfiguration of the cloud SaaS application. Most cloud applications have best practice recommendations and settings for keeping business-critical data secure. Manually configuring proper security settings on potentially hundreds of different SaaS applications is a losing battle for enterprise organizations with IT operations and security teams stretched thin. SSPM solutions use effective automation powered by technologies such as artificial intelligence (AI) and machine learning (ML) to effectively and intelligently carry out routine and important security configuration tasks.
What steps can I take to reduce the chances of security misconfigurations?
To effectively mitigate extension and SaaS app risks like misconfigurations, businesses must adopt a comprehensive approach to manage the entire risk lifecycle. It involves effectively discovering all extensions and SaaS applications connected to the environment and which can access which data. It also involves proactive, continuous risk assessments of all connected extensions and SaaS apps. Finally, as risk may change over time, organizations must leverage automated risk assessments and modern cybersecurity tools to eliminate the threat.
We use Microsoft Configuration Manager within our Microsoft 365 deployment. Should we consider third-party misconfiguration management solutions such as SpinSPM? Why?
Third-party solutions like SpinSPM can provide additional layers of security and automation, offering features such as real-time misconfiguration detection, remediation workflows, and compliance monitoring. This dual approach enhances the organization’s ability to proactively identify and address misconfigurations across the Microsoft 365 deployment, reducing security risks, ensuring compliance, and optimizing system performance.
Can SpinSPM integrate with existing management and monitoring systems used for Microsoft 365 and Google Workspace?
Yes, SpinSPM offers integrations with existing management and monitoring systems used for Microsoft 365 and Google Workspace. These integrations allow organizations to seamlessly leverage SpinSPM’s misconfiguration management features within their IT infrastructure.
Does SpinSPM create and manage backups of critical data to mitigate risks associated with misconfigurations?
SpinSPM focuses on identifying, remediating, and preventing misconfigurations within cloud environments like Microsoft 365 and Google Workspace. Try SpinBackup to create and manage regular backups of your critical data.
How does SpinSPM integrate with other Spin.AI solutions?
SpinSPM is part of the SpinOne platform, which unites SpinBackup, SpinDLP, SpinSMP, and SpinRDR under one umbrella. Using all these solutions together gives maximum protection to your SaaS environment.
We are looking for an automated solution to enhance our HIPAA compliance. Would SpinSPM be helpful in this regard?
Yes. SpinSPM can help enhance HIPAA compliance through its automated misconfiguration management features. SpinSPM continuously monitors configurations within Microsoft 365, Google Workspace, Salesforce and Slack environments, automatically identifies misconfigurations that could lead to compliance violations, and even can automatically trigger remediation actions to correct the issues and bring the SaaS environment back into compliance.



