Shadow IT Risk Mitigation
Protect your critical SaaS data from the risk of Shadow IT with SpinSPM
Shadow IT Use Case
In our remote-friendly world, employees are understandably comfortable downloading and utilizing apps that help them do their jobs. The problem? These third-party applications and browser extensions can have dangerous access to your sensitive, mission-critical SaaS data – posing severe threats of data leaks, breaches, and ransomware attacks.
Shadow IT refers to the fact that these cracks in your armor are not easily detected by your organization’s SecOps teams – and they can’t control what they can’t see. How do you detect and mitigate this looming risk?
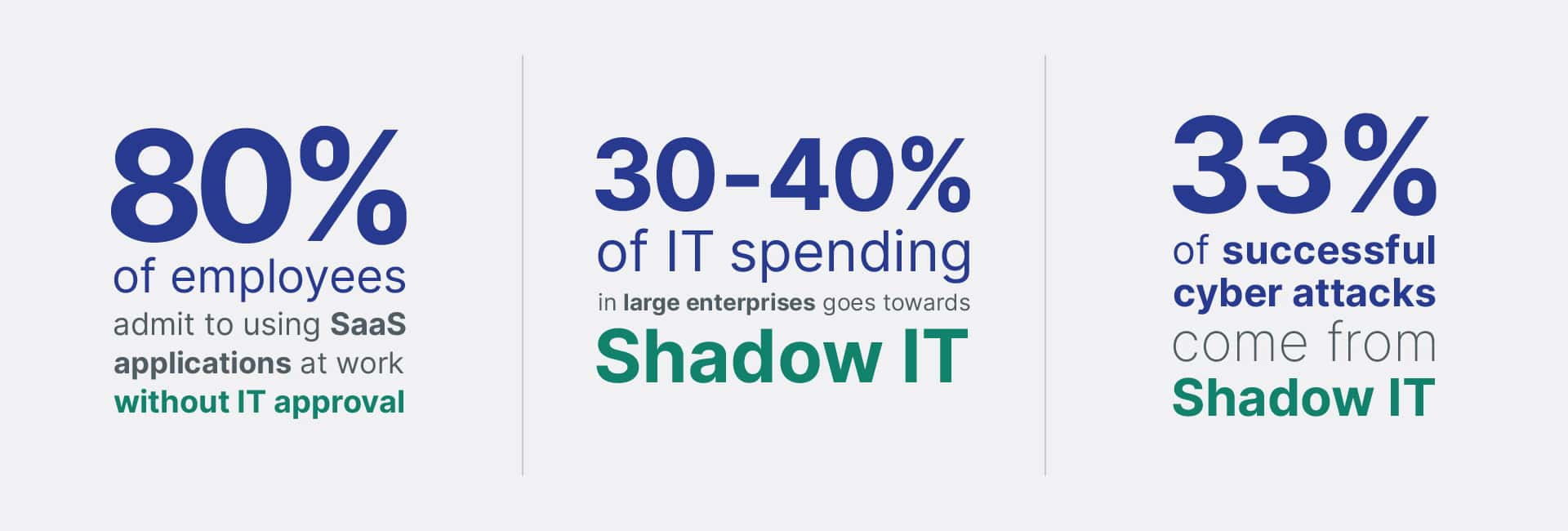
Impact of Shadow IT
Reduce the Risk of Shadow IT
Visibility and Control Over Your SaaS Environment
To tackle Shadow IT, you need to be able to see and inventory all cloud services, mobile apps, SaaS apps, and browser extensions that have access to your SaaS environment — and understand who has access to your critical SaaS data. You require an industry-leading SaaS Security Posture Management (SSPM) solution.
See why we are integrated with Google for Chrome extension risk assessment.

Automated, Continuous Risk Assessment
Eliminate time-wasting busywork for your SecOps team with automated risk assessment (taking your risk assessment time from months manually to seconds automatically.) Detect when new third-party apps or extensions are installed, uninstalled, or even updated – then automatically review or block potential risks with continuous reassessment.

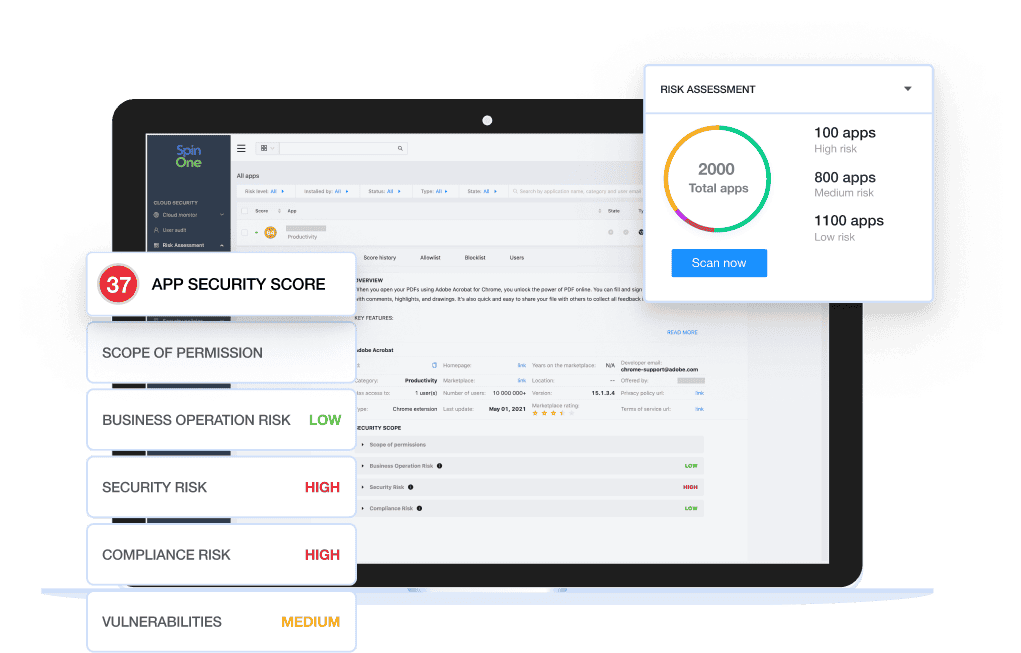
SpinOne SaaS Security Posture Management (SpinSPM)
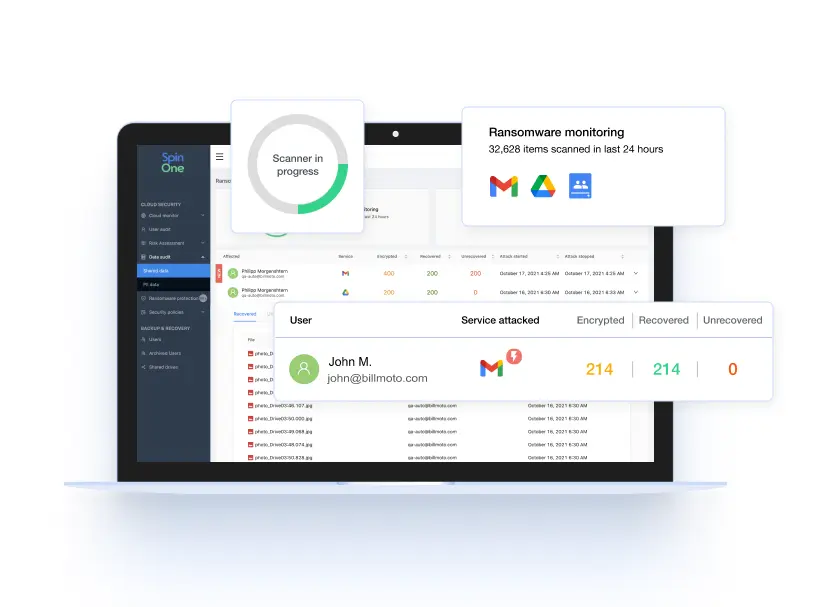
Combat Shadow IT with full visibility and fast, automated incident response for unsanctioned apps and browser extensions from SpinSPM, a solution within the SpinOne platform. Slash your risk assessment time from weeks manually to seconds automatically.
Related Solutions
Application & Browser Extension Risk Assessment Tools
Why Businesses Choose SpinSPM
Related Resources
Your SaaS Security starts with SpinOne
Frequently Asked Questions
Why is Shadow IT a concern in a remote-friendly work environment?
Shadow IT is the phenomenon where employees use third-party apps, extensions and devices to complete work-related tasks without corporate IT approval. While this scenario might seem like a quick way to increase productivity especially in remote work environments, it’s a serious cybersecurity challenge that can lead to many security, compliance, productivity, and cost concerns.
How can organizations detect and mitigate the risks associated with Shadow IT?
Start by implementing:
- Automated Shadow IT discovery to analyze every single application or browser extension that has access to your business-sensitive data.
- Automated AI-driven risk assessment to save your SecOps teams significant amounts of time, avoiding human mistakes and increasing the accuracy of risk detection.
- Ongoing AI-based risk assessment performed every time an app changes access permissions or updates to a new version to make sure no new vulnerabilities have occurred.
What are the main causes of security breaches related to Shadow IT?
One of the main causes of security breaches related to shadow IT involves OAuth abuse. OAuth is a modern authorization technology that powers today’s cloud SaaS environments. The OAuth (Open-Authorization) protocol was created by a team at Google to secure user authentication. OAuth lets users grant third-party applications access to their accounts without sharing sensitive data, like logins and passwords.
Many third-party apps that business users in your organization may install request permission to access user information and data, and sign-in on the user’s behalf in other cloud apps. When users install these apps, they frequently click accept without carefully reviewing the details in the prompt, including granting the app permissions. Accepting permissions from third-party apps poses a security risk to your business.OAuth can make it easy for users to share information with cloud SaaS applications to access data stored in other online services. But OAuth does have its risks — if a malicious application gets its hands on an OAuth token, it can use that token to pretend to be the user and gain access to their account or steal their data.
If an application is malicious, potentially even containing ransomware, the malicious application has permission to encrypt all the user’s data and any data the user can access. OAuth tokens even bypass two-factor authentication in cloud SaaS environments and must be manually removed if compromised.
How does SpinSPM help organizations manage Shadow IT risks?
Misconfiguration management Visibility and inventory of all third-party apps and browser extensions connected to the SaaS environment Automated assessment of the risk of all apps and extensions connected to the SaaS environment and continuous re-assessment Access management to allowlist or blocklist risky applications and extensions Configurable, granular security policies based on set criteria
We have a BYOD policy. Will all mobile devices, including employees’ cell phones and tablets, be monitored to detect Shadow IT?
By monitoring user interactions, data flows, and application usage patterns within your SaaS environments, SpinSPM can detect instances of Shadow IT regardless of the devices used.
What specific capabilities does SpinSPM offer?
SpinSPM enhances your overall security posture, reduces security costs, and improves compliance by reducing the risk of misconfigurations and shadow IT, providing automated, in-depth risk assessments, ensuring complete visibility over your SaaS environment, and providing automated incident responses.
We don’t have remote workers. Are we still at risk of Shadow IT?
Yes, even if your organization does not have remote workers, you may still be at risk of Shadow IT. Shadow IT refers to using unauthorized or unapproved applications, services, or devices within an organization’s IT environment. This can occur regardless of whether employees work remotely or in a traditional office setting.
What is the pricing for SpinSPM?
Please see the pricing page for details on all our packages.



