Data Leak Prevention
Prevent unauthorized exposure of sensitive information and protect your sensitive SaaS data with SpinDLP

Data Leak Prevention
When it comes to data leaks in cloud environments like Google Workspace™ and Microsoft 365, without the proper controls, it’s not a question of possibility, it’s a matter of certainty. 82% of data breaches involve data stored in cloud environments — these breaches can lead to costly downtime and severe reputational damage that can linger for years.
In a constantly shifting security landscape, you need proactive data leak prevention measures to minimize unauthorized exposure and avoid the devastating impacts on customer trust and regulatory compliance.
Impact of Data Leak

Reduce the Risk of Data Leak
Visibility and Control over Data Sharing
You need a solution that provides full visibility into when data is shared, where it is shared, and by whom.
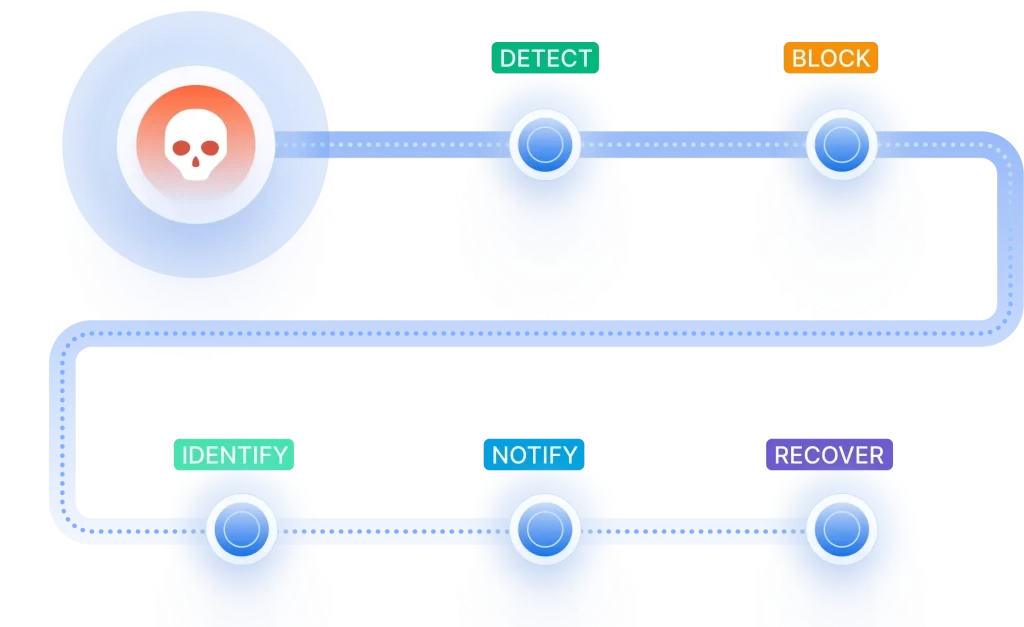
Automated Alerts and Incident Response
With automated, policy-based controls over data sharing and third-party SaaS apps use, you can quickly gain control over data access and align with compliance objectives. Set thresholds and get customizable notifications on abnormal login, data downloads, or transfers by your users to take timely action.

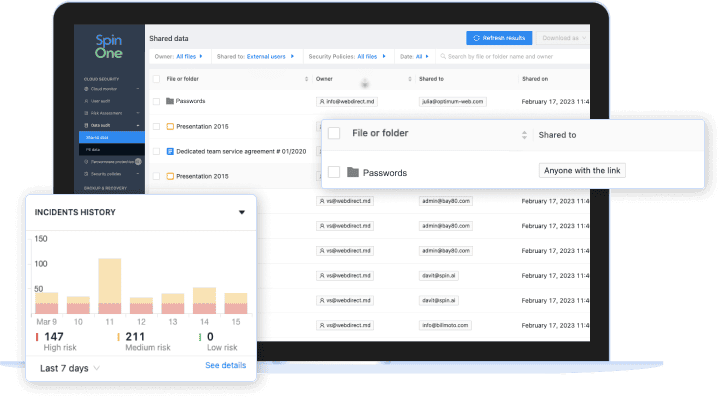
Spin Data Leak Prevention and Data Loss Protection (Spin DLP)

Guard against unauthorized data exposure in your SaaS environment with complete visibility and swift, fully automated incident response from SpinDLP, a solution within the SpinOne platform. Improve compliance with automated protection and reduce security issues by 95%.
Why Businesses Choose SpinDLP
Related Resources



Book a Demo with Spin.AI
Schedule a 30-minute personalized demo with one of our security engineers.
Frequently Asked Questions
What is Data Leak Prevention (DLP), and why is it crucial for organizations?
Data Leak Prevention (DLP) enables enterprises to detect and monitor unauthorized access or transfer of sensitive information, ranging from credit card numbers to social security numbers and other personally identifiable information (PII). Businesses must keep this SaaS data safe and secure to avoid the risks of insider threats and cyberattacks.
Common vectors for DLP include:
- SaaS data sharing by users: SaaS environments make data sharing easy. With a few clicks, end-users can share sensitive data internally or worse – externally.
- High-risk third-party applications: Applications found in cloud marketplaces, such as Google Marketplace or Microsoft Azure Marketplace, provide robust features, but often have OAuth permissions to sensitive SaaS data that make them high-risk.
- Cloud ransomware: Ransomware attacks can result in downtime, data leaks, data loss, data breaches, and potential theft of intellectual property. This can cause huge losses for businesses – in reputation, customers, revenue, and penalties.
According to Gartner, “Through 2025, 90% of the organizations that fail to control public cloud use will inappropriately share sensitive data. Cloud strategies usually lag behind cloud use. This leaves most organizations with many unsanctioned and unrecognized public cloud use, creating unnecessary risk exposure. CIOs must develop a comprehensive enterprise strategy before the cloud is implemented or risk the aftermath of an uncontrolled public cloud.”
What types of data can be protected using DLP solutions, and how are they categorized?
DLP solutions can protect the following types of SaaS data in apps like Google Workspace™ and Microsoft 365:
- Identity information – name, address, phone number, email address, username, password
- Activity information – order and payment history, browsing habits, usage details
- Credit card information – card numbers, CVV codes, expiration dates, billing zip codes
Private, sensitive information is vulnerable and valuable to attackers. Attackers seek to compromise sensitive personal information found in internal databases, user lists, customer records, payment information, and many other data sources. These are often the first types of SaaS assets that attackers seek to compromise for the treasure trove of sensitive information. Information may be compromised due to weak encryption, no encryption, software flaws, or poorly monitored and controlled SaaS environments.
How do DLP solutions comply with various regulatory standards related to data privacy?
DLP solutions help discover and prevent violations of compliance regulations and cybersecurity frameworks, such as PCI-DSS, GDPR, CCPA, or HIPAA.
What are the key features of SpinDLP that enable rapid response to potential leaks, and how does it reduce associated costs?
SpinDLP capabilities include:
- Data Leak Prevention
- 24/7 Cloud Monitoring
- Alerting & Reporting
- Security Automation and Integrations
- Low False Positives
- Compliance-Friendly SaaS Backup
It reduces the costs associated with improving compliance and reducing security issues.
Does SpinDLP work with zip files and encrypted zip files?
Yes, SpinDLP works with zip files and encrypted zip files. It can scan the contents of zip archives, including encrypted ones, to detect sensitive data and enforce data loss prevention policies.
What is the difference between Data Leak Prevention and Data Loss Prevention?
Data Leak Prevention and Data Loss Prevention (DLP) are often used interchangeably, but they can refer to slightly different concepts:
- Data Leak Prevention focuses on preventing sensitive or confidential information from being leaked or exposed outside of authorized channels. It involves monitoring data flow within an organization’s network, endpoints, and cloud services to detect and block unauthorized attempts to transmit or share sensitive data externally.
- Data Loss Prevention, on the other hand, is broader in scope and encompasses measures to prevent the loss or exposure of sensitive data through various means, including accidental deletion, theft, or unauthorized access. While DLP often includes elements of data leak prevention, it also addresses internal risks and vulnerabilities within an organization, such as employee errors, malicious insiders, or inadequate security controls.
What mechanisms does SpinDLP utilize to identify or monitor sensitive data to prevent leaks?
SpinDLP looks at three main things when monitoring sensitive SaaS data:
- What data does an organization consider sensitive?
- Who has access to it?
- What are users doing with the data?
What type of information does SpinDLP monitor?
SpinDlP can monitor many sensitive data types, including credit card numbers, domain names, IP addresses, social security numbers, and more.
We have a BYOD policy. Will all mobile devices, including employees’ cell phones and tablets, also be monitored?
SpinDLP allows you to gain visibility over all your Google Workspace™ or Microsoft 365 data, independent of what device you and your employees use.
How will we know there is a risk of data loss?
SpinDLP continuously scans all data in your SaaS environment. Once a data policy is broken, it can stop sharing it immediately or take any other action defined by your admin. SpinDLP also sends real-time alerts to your Splunk, ServiceNow, Jira, or Slack.