SSPM for Google Workspace
Protect Google Workspace Data with Spin SaaS Security Posture Management (SpinSPM)
SSPM Advantages for Enterprise
Get full visibility and fast incident response for misconfigurations and unsanctioned 3rd party apps and browser extensions with SpinSPM, a solution within the SpinOne platform. Reduce security, compliance, and data loss risks while reducing manual workloads.
What Makes SpinSPM for Google Different?
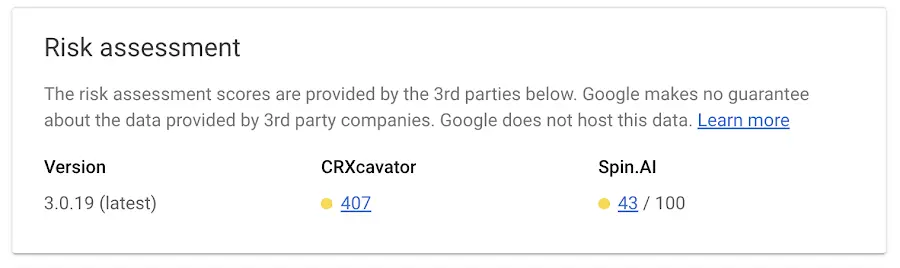
Integration with Google

SpinOne was selected by Google to be integrated into the Google Workspace Console to assess the risk of sanctioned and unsanctioned Chrome browser extensions.
Shadow IT Discovery
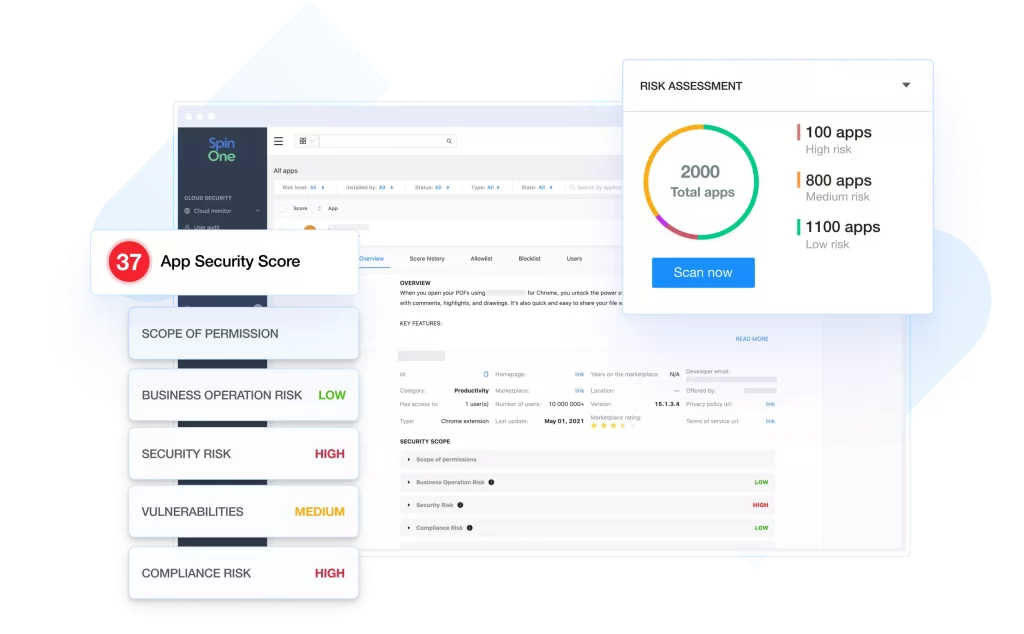
SpinOne has discovered and assessed over 300,000+ OAuth applications and browser extensions using its AI-algorithms, helping organizations reduce risk assessment time from months manually to seconds automatically.

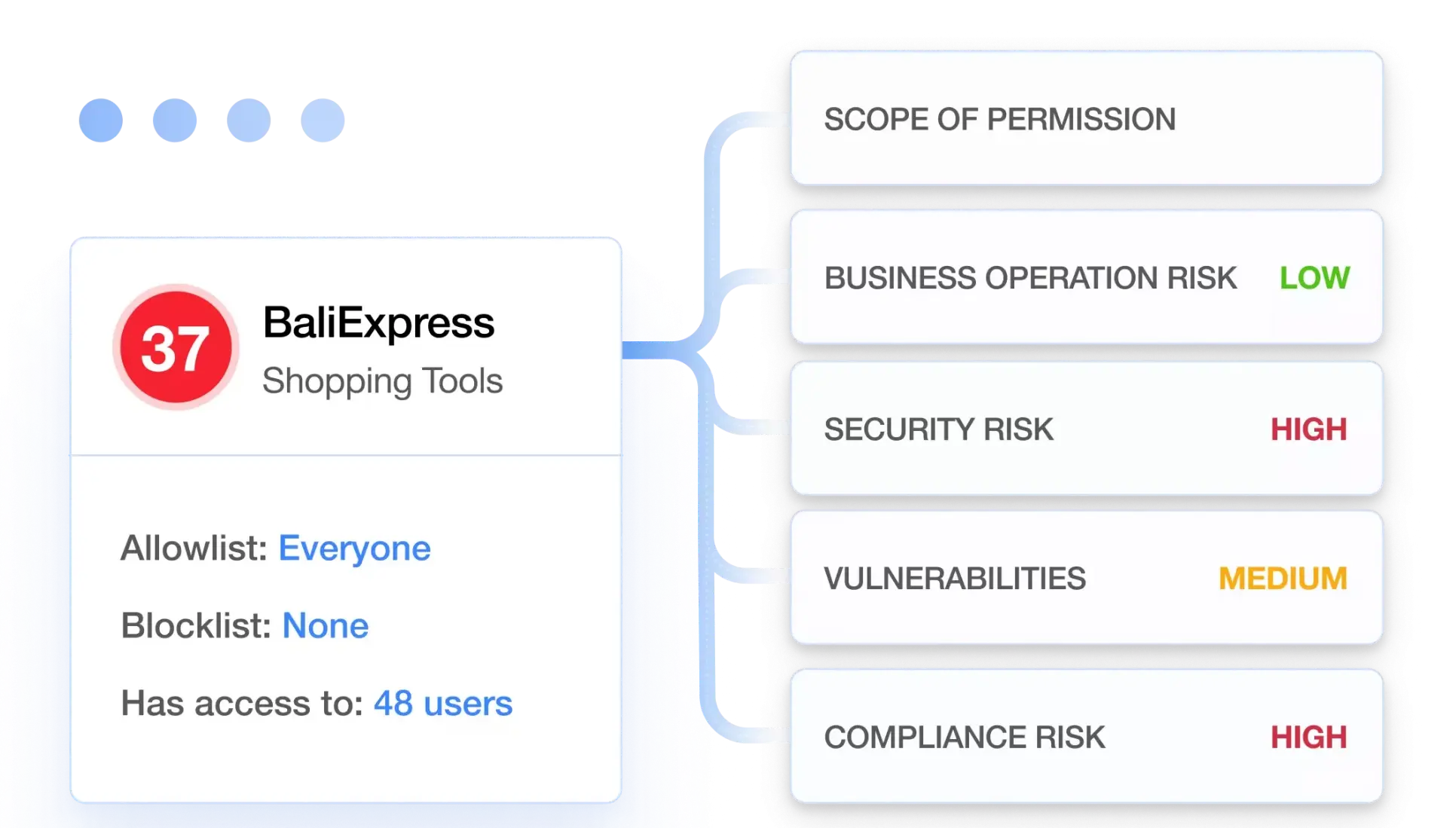
Granular Risk Assessment

SpinOne uses over 15 factors to assess the application and extension risk, and breaks the assessment down into the following sections: scope of permissions, business operation risk, security risk, and compliance risk. Based on this data each app receives a security score from 0 to 100 to zero in on the riskiest applications and extensions and facilitate your decision-making process.
Here’s Why Businesses Choose SpinOne
Frequently Asked Questions
Does Google Workspace have any protection against Shadow IT?
No. Businesses, SMBs, and enterprises alike need solutions like SpinOne. Our platform detects and assesses OAuth applications and extensions. It also alerts about any apps with high risk. To help organizations deal with the increased risk of extensions, Google integrated SpinSPM with the Google Workspace Admin Console.
Why are third-party Google applications and Chrome extensions risky?
Each application and extensions has some sort of access to user data. They can have vulnerabilities that cybercriminals exploit or a hidden malicious code that can be triggered at any moment and infect your Google Workspace or steal your SaaS data.
Is SpinOne safe?
Yes. SpinOne applies functionality to encrypt data in transit, at rest, and in use. It stores backups on cloud storage (AWS, GCP, or Azure).
How does SpinSPM protect Google Workspace data?
SpinSPM provides full visibility and fast incident response for misconfigurations and unsanctioned third party apps and extensions helping organizations harden their security posture and minimize risky access to mission-critical SaaS data.
Streamlined Enterprise Security for SaaS Data
SaaS data security is our top priority. We’ve introduced several processes and regulations to protect your enterprise SaaS data and enhance compliance.






Roland Chan
Chief Information Security OfficerJake Kilian
Technology Support ManagerTed Do
IT ManagerLouis Burdulis
Executive Vice PresidentVal Pashchenko
Information Technology ManagerGeorg Israel
General ManagerMichael Svedeman
Senior Manager, Project DevelopmentGeet Jacobs
Director, Digital OpsJoshua Goss
Senior Director of ITStephan Matter
Technical Operations Manager