What is Data Security Posture Management (DSPM)?

In the past 20 years, the number of data compromises has been steadily growing in the US, reaching its peak in 2021. These incidents impacted both businesses and individuals whose data was exposed and prompted countries worldwide to consider more strict legislation governing data security. Correspondingly, the cybersecurity market introduced a variety of new methodologies and tools to provide businesses with better data control. Data security posture management was one such solution.
What is Data Security Posture Management (DSPM)?
The term Data Security Posture Management was first coined by Gartner in 2022 in relation to a software application. Gartner said that DSPM should provide visibility into the ways data has been used, its location, access, and security posture. Later cybersecurity experts broadened the scope of the term to include data security methodologies.
Data Security Posture Management (DSPM) is a system that focuses on the company’s capabilities to predict, prevent, and respond to cyber incidents related to data (breaches, leaks, and exposure), i.e., its security posture.
The key components of DSPM include
Experts define four main components of Data Security Posture Management:
Data Inventory
An organization needs an inventory that will encompass all its data and systemize it according to multiple criteria. Every new piece of data must be added to the catalog and categorized. It will enable organizations to answer the question: where is our data?
Data flow mapping
Once an organization has inventoried the data, it needs to identify and analyze potential compromise risks—for example, improper sharing settings or excessive permissions of a risky application.
This component answers two important questions: who has access to our data, and how do they use it?
Data Risk management
After outlining all possible risks, organizations should build a risk management system to prevent major data incidents. It includes tools, policies, and practices. For example, you can disable sharing files outside your organization.
Data incident detection and response
The final component of Data Security Posture Management requires a system of incident response. It includes the tools and practices for incident discovery, the response plan, and the recovery measures and capabilities.
How to build an efficient DSPM?
Learn how to create and implement an efficient DSPM in your company.
Analyze your data management
In a large company, a data management system has probably been implemented. You can leverage its resources to build your DSPM, e.g., for data discovery.
Discover and classify data
Corporate data is usually scattered around endpoints (computers and mobile devices), data centers (on-prem and cloud), and applications (coop tools, inboxes, etc.). You need to inventory all your data and all the places your data is stored. We suggest creating a process or purchasing a tool that will catalog your data automatically.
Next, categorize your data by its sensitivity and identify the security configurations for each data category. For example, there’s a drastic difference in the security requirements of a product backlog and a corporate logo.
Assess data risks
At this stage, you need to identify all the possible security risks that your data may be exposed to. For example, with the rise of work-at-home practices, your files may be on an employee’s personal laptop or private Google Drive.
Create new data policies
Outline the new policies for storing, accessing, and managing data based on your identified data risks. For example, create a rule that forbids storing data in a public cloud. Identify how you will impose these policies and ensure that everyone follows them. For example, you can use DLP policies in Microsoft Office 365.
Lay down the Incident Response Plan
No matter how good your defense is, it will always be breached. An Incident Response plan will help you act immediately and minimize the impact of a cyber event.
Identify and acquire resources
Organizations must understand what resources are necessary for implementing Data Security Posture Management. The resources include budget, employees in charge, and tools. Once you’ve analyzed your state-of-art in data security posture, you can outline both available and lacking assets and define ways to obtain them.
Empower your DSPM with SpinOne
SpinOne is an all-in-one SaaS security solution for Google Workspace and Microsoft 365.
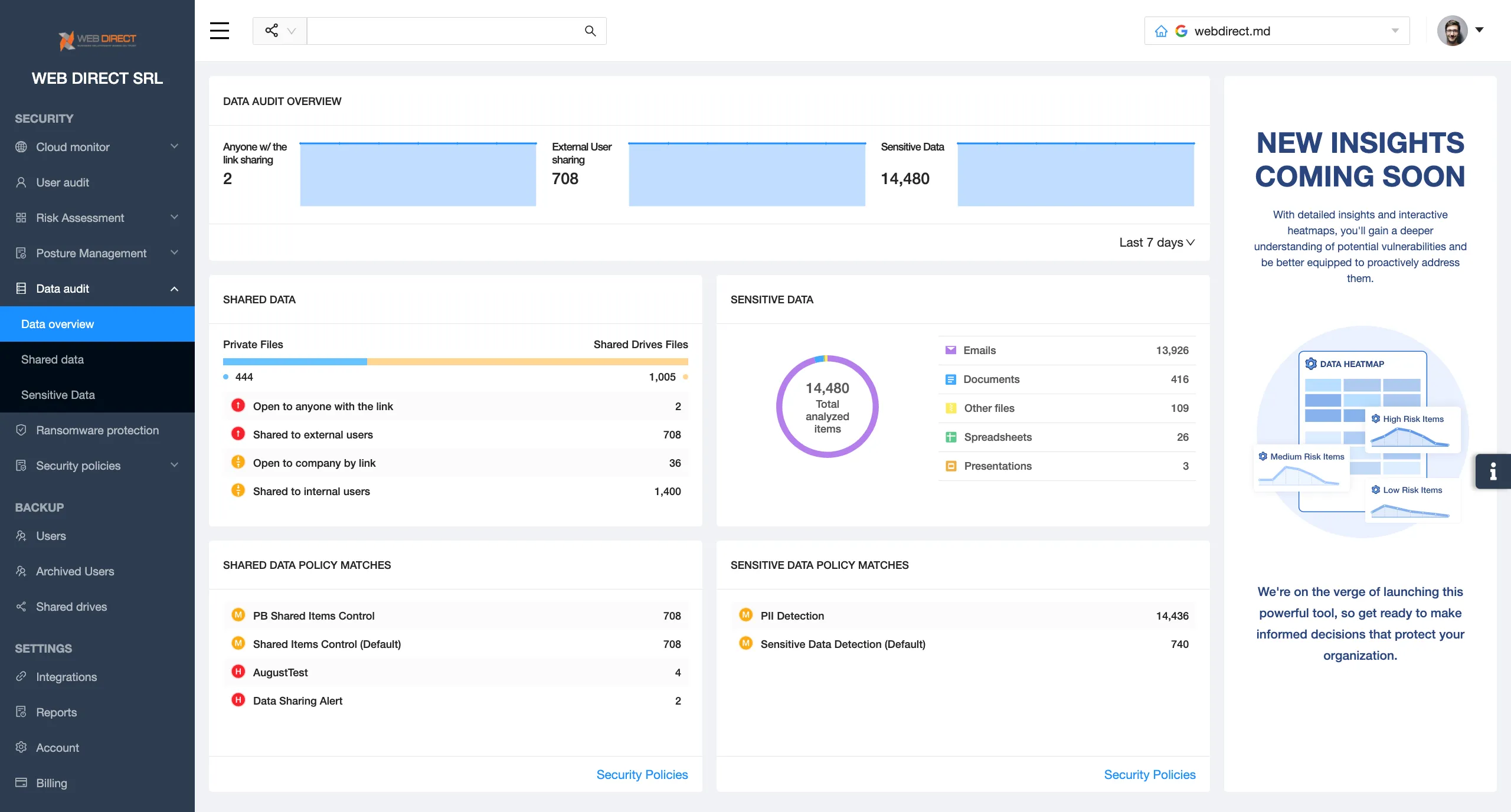
Its functionality can enhance your Data Security Posture Management.
- Data access monitoring and control
- Abnormal logins and data behavior
- Ransomware protection
- Application risk assessment and control
- DLP policies
FAQs
What are the benefits of implementing DSPM?
The benefits of implementing DSPM include better visibility, detection, and response to data-related cyber incidents.
Are there best practices for implementing DSPM?
The best practices for implementing DSPM include data mapping, risk assessment, data policies, and incident response plans.
How can I get started with DSPM?
We suggest beginning with mapping and cataloging your data.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Google Workspace Backup Solutions Comparison
April 26, 2024The number of Google Workspace (formerly GSuite) backup solutions is overwhelming, and choosing the right... Read more
What’s the Best Google Workspace Backup Solution?
April 26, 2024In today’s digital age, businesses rely heavily on cloud-based services like Google Workspace (G Suite)... Read more
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more


