Application Security Assessment: Protect from Threats in the Google Workspace Marketplace
- The Risks of Third-Party Google Workspace Marketplace Applications
- Application Security Assessment Best Practices
- Application Security – Automation vs Manual Efforts
- Spinbackup – Virtual Security Expert
- SpinOne Third-Party Apps Security Common Use Cases
- Get Automated Intelligence and Security Expertise for Your Google Workspace Environment
Third-party applications can greatly extend the functionality and capabilities of your public cloud environments. However, they can also introduce potential security implications as well. This threat makes companies seek application security assessment tools that can eliminate risks while not turning down the advantages of using public SaaS completely.
Focusing on Google Workspace (G Suite) environment –what is application security? What does Google Workspace Security involve? How can your business effectively control third-party apps in the Google Workspace public cloud and effectively meet Google Workspace security goals?
The Risks of Third-Party Google Workspace Marketplace Applications
There are numerous productivity apps available in the Google Workspace Marketplace. These apps offer various options to improve your Google Workspace experience. Take a look at them to see the wide range of choices available. There are tools ranging from apps for accounting & finance, administration, ERP & logistics, HR & legal, creative tools, web development, office applications, etc.
If you need a specific application in Google Workspace, there’s probably one available to do that task for you.
You are responsible for your data when using third-party apps and ensuring Google Workspace security. This responsibility is similar to other parts of Google Workspace and public cloud platforms. In fact, Google makes this clear in their Google Workspace Marketplace Terms of Service. It clearly states:
“Google is not responsible for any Product on the Market that originates from a source other than Google, and you should ensure that you read and agree to any additional terms that apply to those Products before accessing or using them”
Third-party apps are a mix of value and risk (Image courtesy of Google)
Google recommends that all businesses using Google Workspace environments evaluate a Google Workspace Marketplace app and its security before installing and using the app. In regards to the security of Google Workspace Marketplace apps, Google makes this statement:
“You are solely responsible for any compromise or loss of data that may result from using a Marketplace app.”
You may wonder, why is there a risk from using third-party applications when they may be listed in the Google Workspace Marketplace? The risk factor from third-party applications comes from two different perspectives:
- The third-party application may directly try to leak your data or have some kind of malicious intent
- The third-party application may be legitimate in nature, but be poorly written. Poorly written applications may introduce Google Workspace security vulnerabilities that can lead to compromise.
Read more about risky, fake, and malicious apps.
Application Security Assessment Best Practices
While Google has a screening process for developers, as Google’s disclaimer mentions, “you are solely responsible for any compromise or loss of data”. Businesses must take hard and fast ownership of screening third-party apps for security best practices. What are the best practices that Google outlines for third-party application security?
- Properly evaluate the vendor or application
- Screen gadgets and contextual gadgets carefully
- Use the Security Assessment Program to help gauge whether a vendor or application should be trusted.
Evaluate vendors and/or applications
Google notes that you must evaluate a vendor or application and decide to use it for your Google Workspace environment. To analyze whether or not a vendor or application is acceptable to use from a Google Workspace security perspective before you install the application:
- Look at reviews left by customers who have downloaded and installed the third-party application. The reviews are listed for all Google Workspace Marketplace apps
- Look and analyze closely the third-party application vendor’s Terms of Service, privacy policy, and deletion policy agreements to ensure there are no unwanted, hidden clauses that may affect the security
- Contact the third-party application vendor directly with questions regarding any grey areas that may be questionable
Screen Gadgets and Contextual Gadgets Carefully
What about third-party gadgets? What are the gadgets? These are full web applications written in HMTL, CSS, and Javascript that can run in the context of the Google Workspace environment.
You can use Gadgets in Gmail, Calendar, Drive, and Sites. What are the security implications?
- A special class of gadget is known as the Gmail contextual gadget. These types of gadgets can extract data from a Gmail message and provide contextually relevant information to you in the message pane.
- Poorly written gadgets by third-party vendors may expose your business to potential risks in the form of phishing attacks and potential data loss or leakage.
Gadgets in general and specifically contextual gadgets should only be installed from vendors that you implicitly trust.
Use the Google Workspace Security Assessment Program
Google has a Google Workspace Marketplace Security Assessment Program that allows developers to submit their apps to a third-party security firm which then performs a full security and risk assessment of their application. Once an application has passed the security assessment, the application will be able to display a security badge in the Marketplace listing.
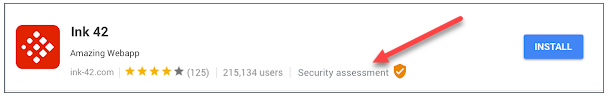
Review Google Workspace third-party apps for Security assessment badge (Image courtesy of Google)
By following these Google-defined best practices for Google Workspace security, businesses can much better gauge the security of applications that are integrated with the Google Workspace environment. It will help to conduct an application risk assessment.
Another danger when it comes to third-party applications is your end-users. How is this the case?
In general, your typical end-user is very trusting of any application that requests permission to access their data. Most of us are guilty of blindly clicking “Allow” to permissions requests on mobile devices when installing a new third-party application. Do most take the time to consider the security implications of allowing access? For most of your users, the answer is “No”.
Now, think of that same mindset when it comes to accessing sensitive corporate data. Do you want the same type of decision-making to happen when deciding whether or not to allow applications to access important business data? This is a very real and present danger in today’s corporate culture of freedom to access business data with mobile devices, including BYOD, from various untrusted networks, etc.
You must have the means in place to keep strict watch over and control of third-party applications. This is to ensure the applications that are granted access to your sensitive corporate data are those that meet the criteria listed above. And to have the characteristics of a trustworthy application that is not known for data leaks or all-out malicious activity.
How can you successfully meet the ever-increasing demands on IT professionals, not only in the area of operations but now with increasing security complexities?
Application Security – Automation vs Manual Efforts
With the sheer number of threats, variants, complexities, hybrid networks, BYOD, and many other factors, it is becoming increasingly difficult, if not impossible for you to rely on manual efforts for effective security. Humans are simply not as effective and efficient at parsing logs and manually correlating metrics and activities as “machines” or computers are.
Computers are much better at repetitive tasks that require monotonous activities such as crunching numbers and examining data than humans. Additionally, computers do not “get tired” and can work 24x7x365. Machine Learning is a new technology that businesses can use. It uses mathematical algorithms to learn about an environment, identify what is normal, and detect any deviations from this normal pattern.
When used with security, machine learning is able to create a baseline of what normal activity is in an environment and build a baseline of activity. If an activity is noticed outside of the normal behavior of both users and applications, this could be a red flag that there may be malicious intent with the new behavior.
Machine learning and intelligent design can protect Google Workspace from security threats in Google Workspace Marketplace. These threats may come from third-party apps that have the potential to harm your data.
Spinbackup – Virtual Security Expert
Imagine if you could have a full-time “expert” security person working to secure your Google Workspace public cloud SaaS environment. Would you feel more confident about your business-critical data from a security standpoint? Absolutely! You can have such an expert security assistant working to secure your Google Workspace environment – Spinbackup.
Using the latest in powerful machine learning algorithms, Spinbackup is a virtual security expert scanning the Google Workspace environment looking and watching for anything that could pose a danger to business-critical data.
Spinbackup’s API-driven CASB technology integrates with Google Workspace seamlessly to become a hardened security layer in between corporate data and anyone or any device accessing it. This includes third-party applications that are allowed access to corporate data. Its AI-based approach to analyzing third-party apps saves IT personnel and Google Workspace administrators tremendous amounts of time and energy protecting the Google Workspace environment.
The Spinbackup analytics engine provides unique expertise and fully automated scanning of over 20,000 apps and counting. With new improvements in algorithms and scanning technology implemented on a regular basis, Spinbackup is constantly improving the solution to provide the best possible security for businesses utilizing the Google Workspace environment. The bottom line is that Spinbackup allows automating the best practices recommended by Google when securing third-party applications.
AI-based Third-Party Apps Risk Assessment and Remediation
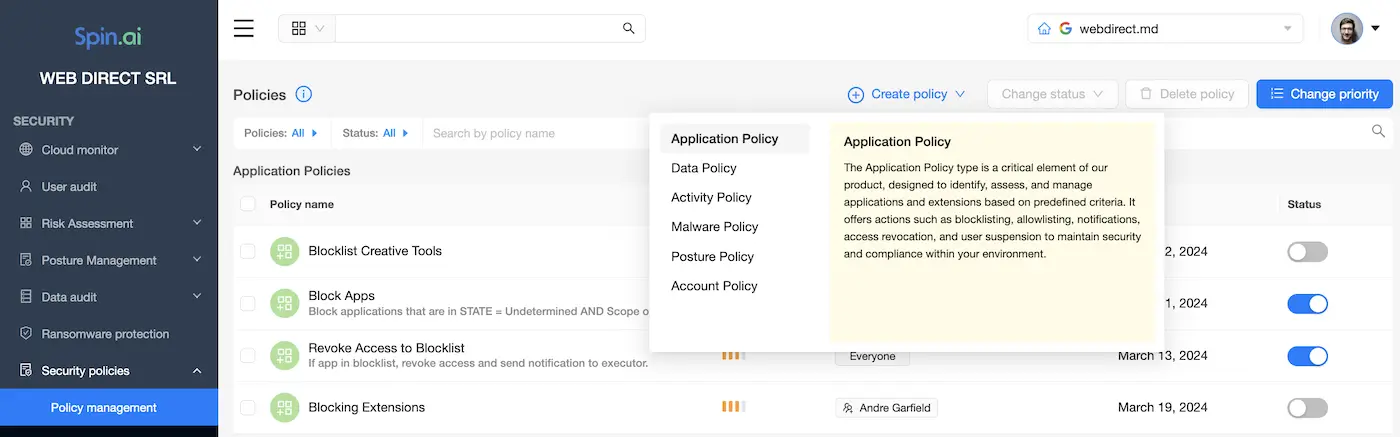
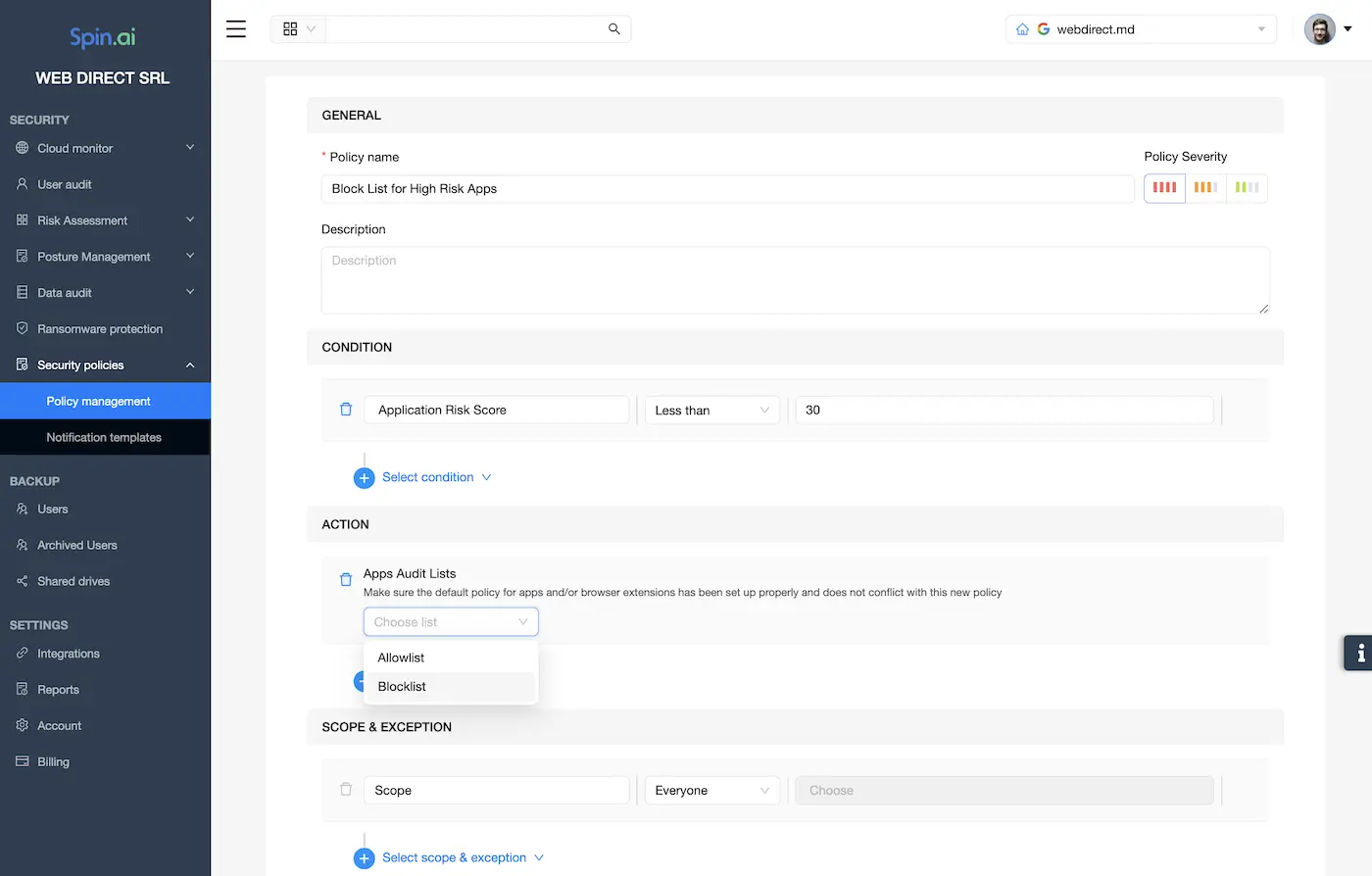
With the Third-Party Apps protection module and AI-enabled technology, the Apps Audit Policies allow creating effective rules that control how apps are allowed to be installed in the Google Workspace environment. Spinbackup conducts web application scanning and allows creating both a blacklist and whitelist of applications that are allowed or disallowed to access your Google Workspace environment.
This application risk assessment is a powerful approach that you can use to only allow certain applications to be installed or disallow a list of applications, or a combination of both. Notifications are proactively sent to administrators, notifying them of the event.
Here is how it looks like in action:
Under the Apps Audit Policies, the Blacklist & Whitelist allows configuring the following:
- Application Name – This field contains the application’s full name, or part of the name, as found in the Google Workspace Marketplace or in the Apps Audit section.
- Application Category – Detects all applications under the defined application category.
- Application Risk Rate – Detects all applications under the chosen risk rate.
- Use Apps Audit Blacklist Check – If this checkbox is enabled, it will compare detected applications with the blacklist in the Apps Audit section. This rule will be skipped if the blacklist doesn’t contain the detected application.
- Use Apps Audit Whitelist Check – If this checkbox is enabled, it will compare detected applications with the whitelist in the Apps Audit section.
- Remove Application – When selected, the application is removed.
- Send Notification – Sends notifications.
Below, you can configure the Conditions for the Audit Policy Rule applied to the Google Workspace environment for third-party applications.
SpinOne Third-Party Apps Security Common Use Cases
What are some of the common use cases Spinbackup’s AI-based third-party apps protection module solves for businesses utilizing Google Workspace SaaS environments?
- Unsanctioned data download – An employee installs an app that connects to the Google Workspace environment and starts migrating sensitive data from a corporate account to their personal private cloud storage account. This commonly happens when an employee decides to leave a company.
- Unsanctioned third-party apps download – An employee installs an app that is not sanctioned for use in the Google Workspace organization
- Employee Termination – When a company fires an employee, IT admins usually suspend the user account. When you suspend a Google Workspace account, all the apps still have access to sensitive data that was accessible by the user.
This can be a potential for a data breach. Spinbackup’s third-party app security solution is a must-have tool for HR Departments that have to take care of the most efficient way of OFF-boarding an employee by removing all the Apps that have access to sensitive data through a suspended user account. - Compromised third-party apps – An App can be hacked by cybercriminals. Developers may not be able to quickly identify the breach before it starts downloading or migrating an abnormal amount of data or changes the scope of permissions which constitutes abnormal behavior.
Get Automated Intelligence and Security Expertise for Your Google Workspace Environment
Third-party applications provide tremendous value to your business to extend the capabilities of your Google Workspace environment. With the capabilities of Google Workspace Marketplace apps, there are security risks involved.
Google makes it clear that if you decide to utilize third-party apps, you must take ownership of your data and by extension, any data loss that happens due to a risky third-party app. Implementing third-party apps best practices can be involved, and require a lot of manual processes to be effective. To keep pace with the complexity and sheer pace of hybrid environments today, you must make effective use of machine learning and AI to be effective.
Spinbackup is one of the best web application security assessment tools that provides the definitive solution for securing the Google Workspace environment. It makes intelligent decisions regarding third-party apps and installation in Google Workspace. By making use of intelligent AI-based technology, Spinbackup is the virtual security expert that constantly watches your Google Workspace environment and enforcing security 24x7x365.
With Apps Audit and other built-in technologies, Spinbackup allows creating blacklists and whitelists of applications for sanctioned use. If the AI-based engine detects that a once-approved third-party app begins demonstrating malicious behavior, Spinbackup provides notifications and remediation of the potential security event. Spinbackup provides automated intelligence and security expertise to your Google Workspace environment, seamlessly, and in a way that provides confidence in making use of third-party applications.
Sign up for a demo, and see how Spinackup works in action!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...