Beyond Add-Ons: Elevating Browser Governance Against Malicious and Risky Extensions
Browser extensions, plugins, add-ons – these tools may have many names but they have even more purposes, from enhancing productivity to personalizing the user’s browsing experience or adding useful features to a standard web browser. But with great utility come some unprecedented risks, ones that manifest not just through malicious activities like data theft and unauthorized surveillance but also via seemingly benign permissions that can turn risky. In this blog we unpack the challenges introduced by browser extensions and discuss Perception Point’s latest innovation to solve them.
Risky & Prevalent: Some Number on Browser Extensions
Spin.AI’s risk assessment research on a substantial dataset of 300,000 browser extensions revealed an alarming number: 51% of extensions have been identified as having overly permissive access, creating potential gateways for executing malicious behaviors.

The research has shed light on other worrying phenomena:
- Anonymity: 42,938 extensions from the dataset had anonymous authors, meaning the app cannot be attributed to its developer/marketplace publisher.
- Popularity: the average number of browser extensions installed in an enterprise with over 2,000 employees is a staggering 1,454 (!) – It’s highly unlikely that the majority of them were sanctioned by the IT or the security teams.
These findings amplify the risk posed by third-party browser extensions, ranging from untrusted sources to greedy permission requests and “Shadow IT”. Next we’ll review the different types of risky extensions and what challenges they introduce to workspace security.
Types of Harmful Browser Extensions
Harmful browser extensions come in various forms and sizes. To put things simply, we can categorize these extensions into three main subtypes.
Risky/Permission-Heavy
Legitimate browser extensions that request more permissions than necessary. Permissions determine the actions an extension can perform and the data it can access within the browser. They are requested and granted during installation, varying depending on the functionality of the extension. Such permissions may grant the extension access to more information and control than required for its intended function, creating vulnerabilities that can be exploited for malicious purposes or result in unintended data exposure, thereby complicating compliance and security posture.
Day-1 Malicious
Created and spread by threat actors, often disguised as legitimate tools, these extensions can capture sensitive information, track online activities, inject unwanted advertisement (Adware) and harmful code, compromising both personal and organizational security. Day-1 Malicious extensions can come in the form of trojanized variants of real browser extensions (e.g ChatGPT and other GenAI malicious plugins) or totally original “ad-hoc” extensions being spread through social engineering and malvertising. It is important to note that even Day-1 malicious extensions can provide the users with the promised functionalities in order to avoid suspicion.
Compromised
A once trustworthy extension that falls into malicious hands, either through direct purchase by the threat actor or by compromising the developer’s account on the add-ons store, altering its intent and function and releasing malicious versions. Back in 2017, an incident involving the compromise of seven Chrome extensions highlighted the rising popularity of compromised extensions as a threat vector.
All three subtypes of harmful extensions can unfortunately be found and downloaded from the official browser add-on stores. This presence in trusted marketplaces adds to the complexity of detecting and mitigating the threats they pose to users and organizations.
Browser “Plaugue-Ins”: A Critical Blindspot
Even if a malicious browser plugin is detected and subsequently removed from the Google Chrome or Microsoft Edge store, this does not mean it will be immediately removed from browsers where it has already been installed, leaving organizations potentially compromised until the next browser update cycle. Moreover, the existing security solutions focusing on endpoint security, such as Endpoint Detection and Response (EDR), and network security measures like Secure Web Gateways (SWG), lack the capability to detect and block the malicious activities carried out through browser extensions.
On the other hand, while endpoint management tools like Unified Endpoint Management (UEM) and Mobile Device Management (MDM) systems offer a means to deploy and configure browser extensions across enterprise environments, they often fall short in providing sufficient visibility, control, and risk analysis capabilities to effectively mitigate the threats posed by malicious extensions.
This raises a critical need for better browser governance within IT and security teams to effectively manage, regulate and control the usage of browser extensions within the organization (employees and 3rd-party users alike). The gap underscores the need for a robust solution that can address and mitigate the unique challenges posed by browser-native threats.
Reducing Browser Extension Risk with Extension Analysis and Enhanced Governance
Perception Point’s latest addition to its Advanced Browser Security product aims to eliminate the risks associated with browser extensions. The integration with Spin.AI’s Browser Extension Risk Assessment technology provides organizations with unprecedented insight and control over browser extensions within the organization web environment.
Complete 3rd Party Extensions Inventory
Uniquely positioned within enterprise browsers such as Chrome and Edge, the Advanced Browser Security extension scans and offers an overview of all browser extensions installed on the user browsers. From one dashboard, security admins can view and assess extensions installed on users’ devices, discover the number of installations per extension, category, browser type, permissions and the Spin.AI Risk Score.
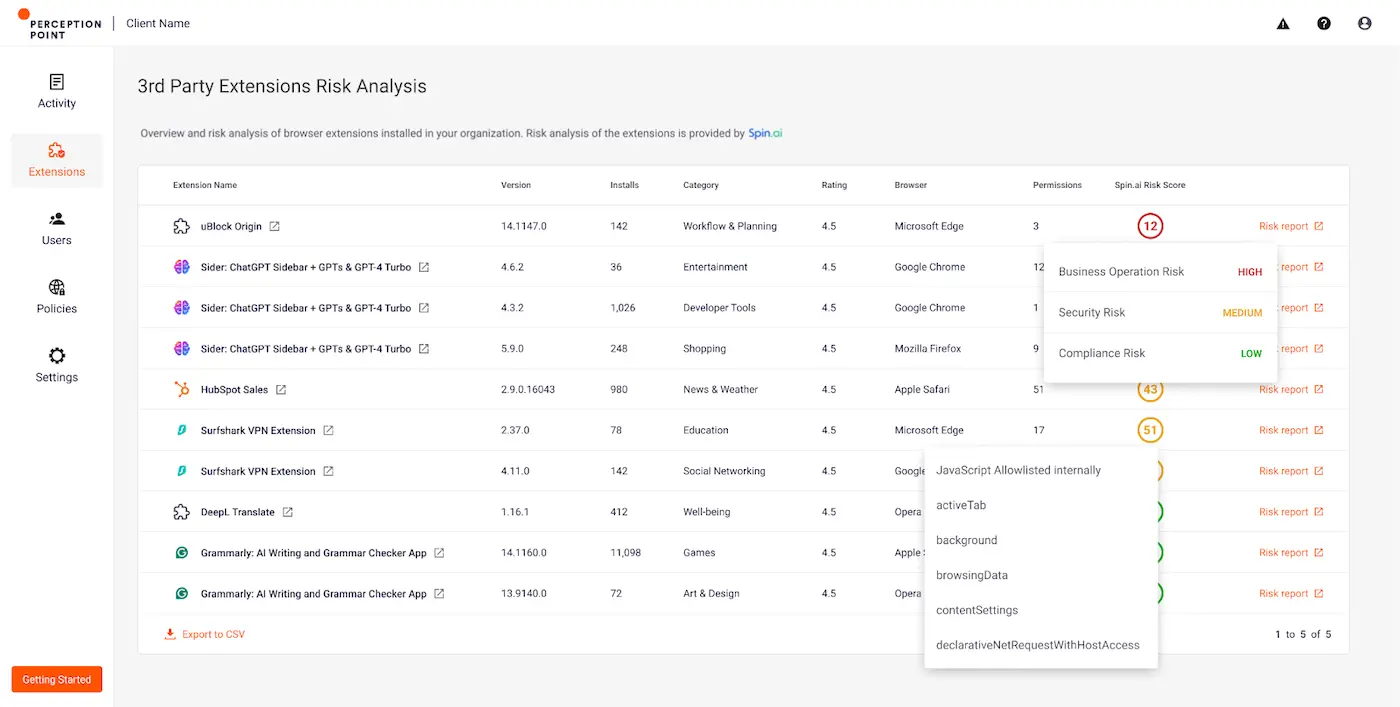
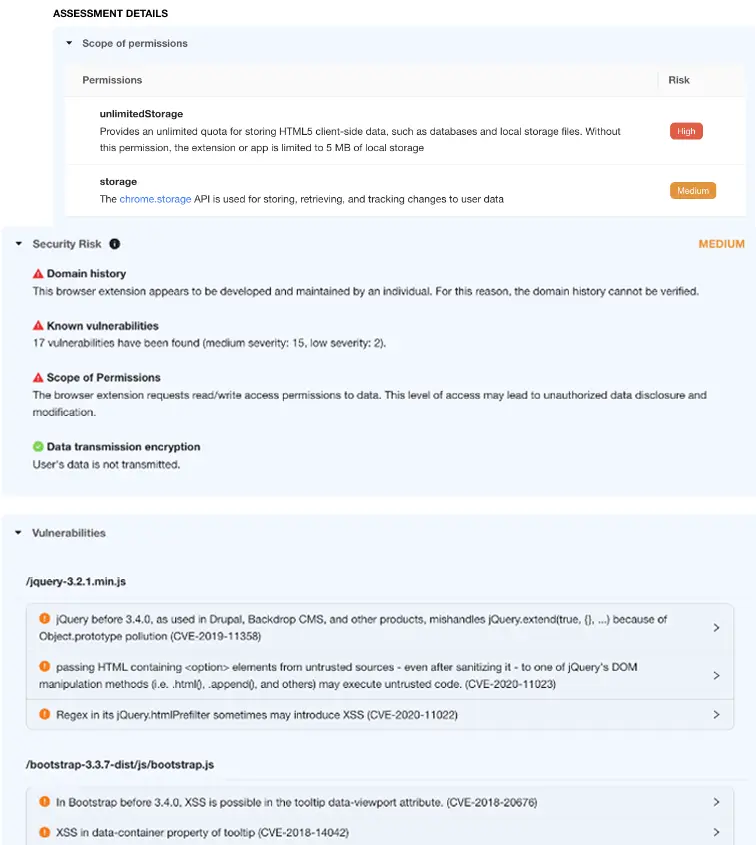
Spin.AI Browser Extension Risk Assessment
Perception Point customers can now access a full risk evaluation report by Spin.AI. Spin.AI utilizes advanced machine learning to analyze various attributes of each browser extension, including permissions, vulnerabilities, and compliance risks, to generate a comprehensive risk score. This enables organizations to better understand and manage the security implications of the extensions their users are using.
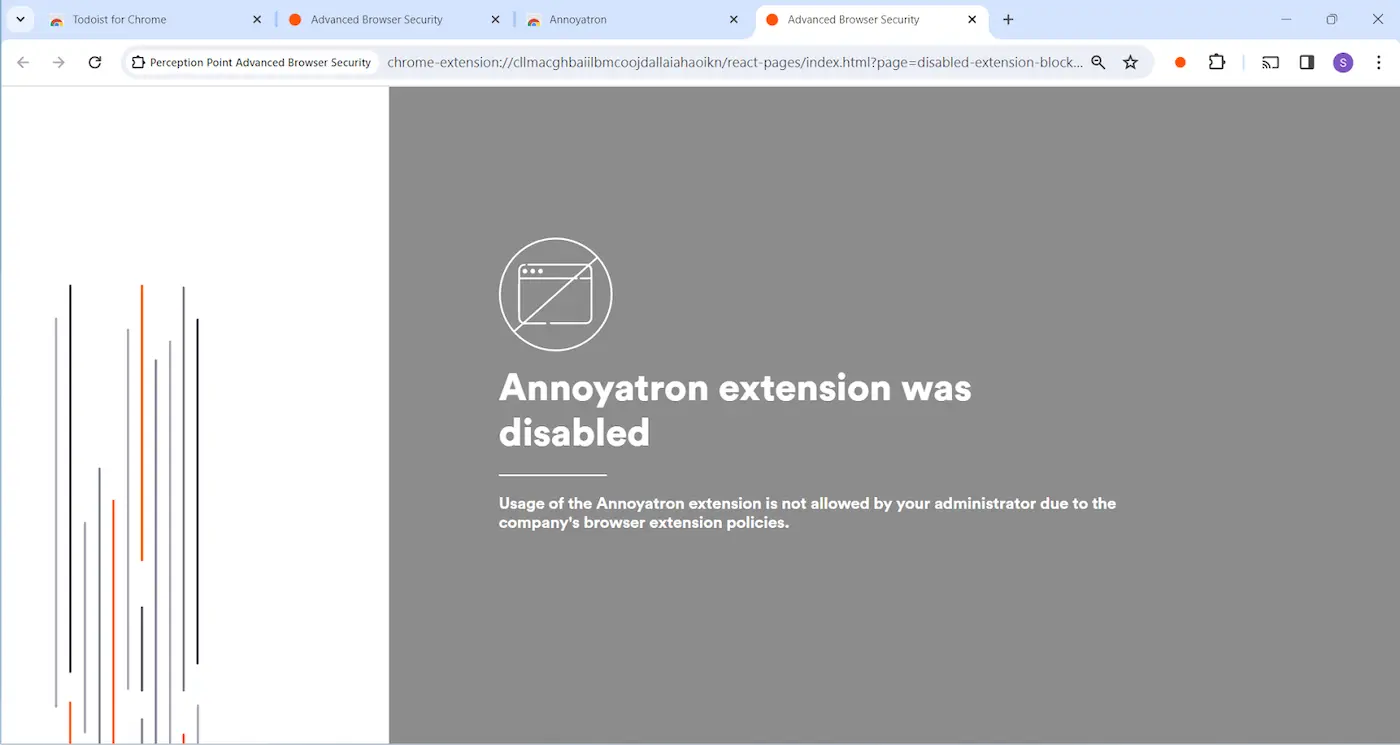
Browser Extension Governance
Advanced Browser Security allows administrators to disable risky (and benign) browser extensions using granular policies across the organization. It can record and alert on user behaviors performed with extensions – installation and uninstallation, enabling, updating, etc. Admins now have the ability to block and disable extensions automatically based on their risk scores.
Your Enterprise Browser Security is One Extension Away
Perception Point’s Advanced Browser Security deployed via a lightweight extension, integrates AI-powered phishing and malware detection, data loss prevention measures, and browser governance and visibility. The solution combines patented multi-layered detection technology to detect and prevent the most sophisticated web and browser-based threats with an all-included managed 24X7 incident response service to reduce IT/SOC team resources.See Perception Point’s Advanced Browser Security in action, request a demo today.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


