Choosing the Right SaaS Security Posture Management (SSPM) Solution for Your Organization
SaaS Security Posture Management solutions are plenty on the market. The abundance can create analysis paralysis even in the most experienced buying teams. This guide essentially explains how to choose the tool that meets your business needs.
What is the SaaS Security Posture?
SaaS security posture identifies the overall condition of the security of a company’s SaaS applications.
This includes inter alia:
- the state of cloud data security
- the authentication methods
- the authorization process
- access to data
- the use of data.
A company’s SaaS security posture is a constantly evolving and complex issue, as new threats and vulnerabilities are discovered on a regular basis.
A proper SaaS security posture begins with researching the specific security risks associated with the SaaS apps in use. Organizations need to be aware of the potential threats that can put their data at risk, and take steps to mitigate those risks.
The use of apps implies storing corporate data in the cloud beyond the organization’s control. Many cybersecurity experts consider it to be the one of key dangers related to apps. Correspondingly, apps become a popular target for cybercriminals seeking to steal and take advantage of the data. Hence, we see constant searches (successful on way too many occasions) for the app’s vulnerabilities.
Experts recommend that organizations take the following steps in order to secure their data in third-party apps:
- Confirm that apps use up-to-date security technologies, including authentication, authorization, and data encryption.
- Reassure that the cloud provider is reputable and has a good security track record.
- Routinely monitor the security of the applications and the data.
- Set up alerts of any security incidents.
- Systematically audit the security of the applications and the data.
- Reduce the pressure on IT team and tackle the skill or talent gap.
All these tasks can be carried out either by a team of humans or software. The software that performs these tasks is usually called SSPM.
What Is SaaS Security Posture Management (SSPM)?
SaaS tools like Office 365 or Google Workspace have created complex environments with thousands of ‘satellite’ applications. These apps are created to improve the productivity of the main tool that controls the given environment.
Unfortunately, the scope of GW or MSO 365 control over app security isn’t as large, as many IT teams think or wish for. Every year, hundreds of apps are published on Google and Microsoft Marketplaces. Most of them have barely passed the minimum requirements for security and thus might have hidden vulnerabilities.
Nevertheless, the enterprise employees begin using them unbeknownst to the Administrators. As a result, they create significant threats to their companies. The latter often bear the full responsibility for app security (unlike the app owners or publishers).
Detection, risk assessment, and control of these applications is the goal of any large organization. This process is tedious and time-consuming. That’s why it has been automated and presented in a single tool we know as SaaS Security Posture Management.
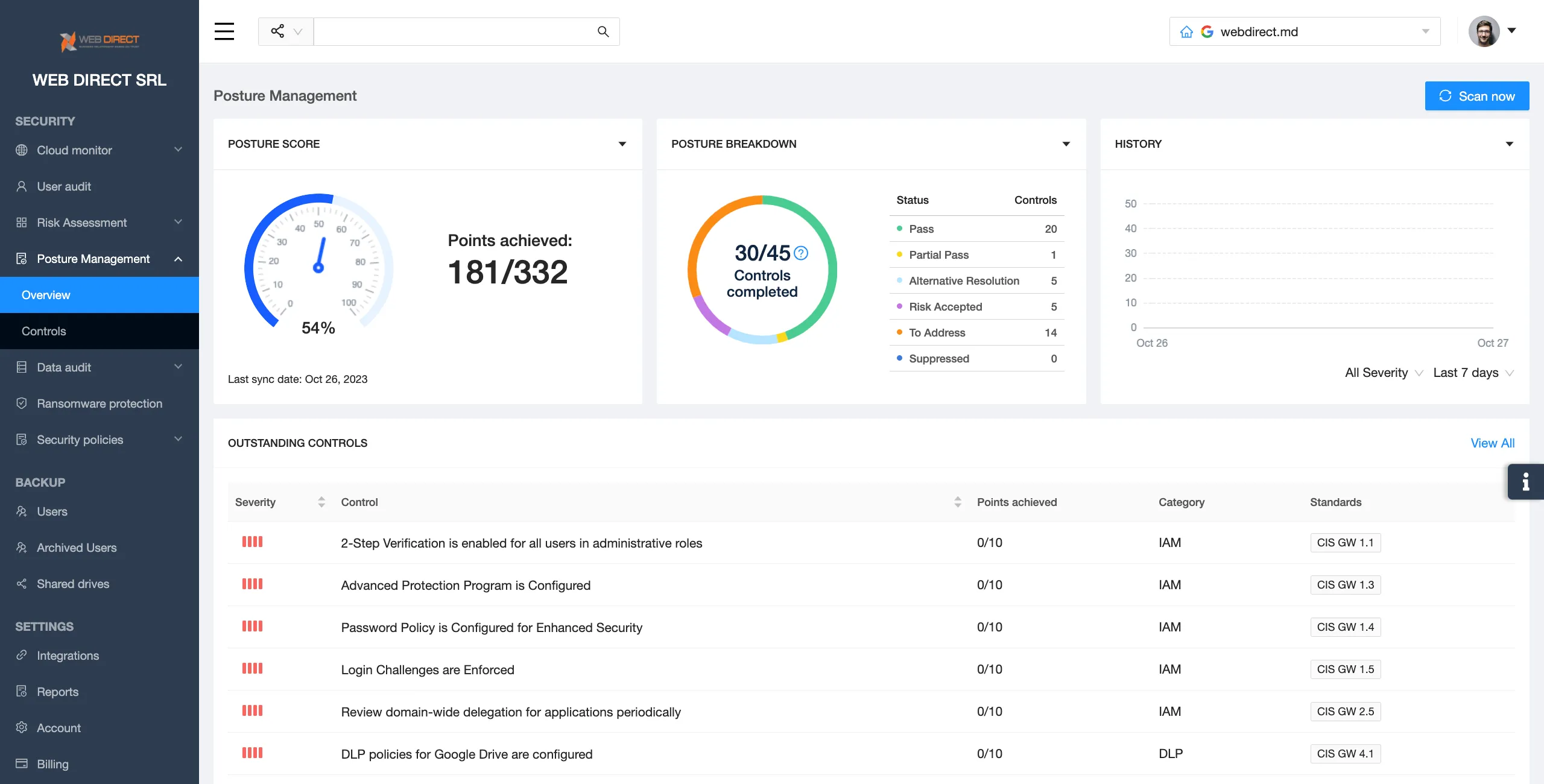
How Does SSPM Work?
SSPM focuses on three main areas:
Permissions
When installed, SaaS applications require a certain scope of permissions to do their job (from as simple as access to certain folders to data editing rights). SSPM detects apps, analyzes the scope, and alerts the IT team about it.
Compliance
Organizations must comply with various laws and regulations. These depend on the country of their registration and business operation, industry, company size, type of business, etc. Certain regulations govern the use of applications. SSPM helps to identify compliance-related features of applications in order to block their use.
Configuration
Improper configurations of apps can happen as a result of a human mistake or a deliberate attack by one of your employees. They can lead to multiple hazards, including ransomware attacks, or unauthorized access to data. SSPM helps teams detect such misconfigurations and change them.
The Importance Of Saas Security Posture Management For Enterprises
SSPM helps enterprises achieve several goals:
- Identify and control excessive permissions that can become hazardous to your cybersecurity.
- Detect threats (both existing and potential) to the organization’s compliance and set policies that prevent non-compliance.
- Expose and mitigate risks pertaining to app misconfigurations.
- Eliminate the use of applications that can lead to non-compliance or data breaches.
- Build a system of non-stop monitoring and seize the opportunities for immediate remediation.
Factors To Consider While Choosing SaaS Security Posture Management (SSPM) Solution
Find here a buying checklist for SSPM. It will help you to vet the solutions represented on the market.
Centralized platform
Define the functionality that meets the needs of your business. Search for solutions that provide all the necessary features rather than buying several siloed tools.
The Breadth of Integrations
Outline the tools that your business uses. Search for an SSPM that integrates with as many of them as possible.
Monitoring & Incident Reporting
Find out if there’s 24/7 monitoring available and how the tool reports the new risky applications, e.g., via email.
The Number of Applications
Ask the sellers how many applications their SSPM detects. Another good question would be about the frequency of their app database updates.
Application Assessment Criteria and Scoring
Often overlooked by the buying teams, this functionality is one of the most critical. Some SSPMs use only 2 or 3 criteria to evaluate risks and use a simple scoring system (e.g., High-Medium-Low).
Access Revoke Functionality
The ability to immediately revoke access of an application with a high-risk score can not only save much time for your admins but also possibly prevent a cyber incident.
Blocklisting & Allowlisting
Creating lists of ‘desired’ and ‘unwelcomed’ applications can save you much time in the long run. It also enables you to implement an initial zero-trust approach when all apps are blocked. In this case, you have no Shadow IT and get a significant leverage when it comes to cooperation with departments on app acquisition.
Security Policies
Confirm that an SSPM enables you to configure a security policy that doesn’t allow users to set up applications based on certain criteria (e.g., risk score or scope of permissions).
Employee Requests System
This functionality streamlines the request process when employees want to acquire a new application and want to send an official request to the IT department.
Company-based Customization Opportunities
SaaS Security Posture varies from company to company based on a number of factors. The possibility to customize the platform functionality will allow you to build the system that will defend your data most effectively.
Support
Check if the company provides round-the-clock support. It’s essential to be able to talk to the specialist if you have any questions pertaining to the app.
Pricing
This is an important factor. At some point of the buying process, the IT team will have to ‘sell’ the solution they chose to their management. They’ll need to present the tool of choice in terms of money it can save for the company from the standpoint of automation and incident prevention rather than how it fits the overall IT budget.
Best Saas Security Posture Management (SSPM) Tool
SpinOne is a SaaS Security Posture Management tool developed by Spin Technology. Enterprises can choose between two products:
- SpinSPM: only SSPM functionality.
- SpinOne: data protection platform that includes backup, ransomware protection, DLP, and SSPM.
In terms of SSPM features, these products are the same. That’s why we won’t review their functionality separately.
Integrations
The SSPM is designed for Microsoft Office 365 and Google Workspace. The data is stored in AWS, GCP, Azure, or any other designated storage of a client’s choice.
Monitoring & Incident Reporting
SpinOne uses APIs to monitor events in GW and Microsoft Office 365, including the setup of new applications by users. It stores all events in the Activity log. The dangerous events are additionally stored in the Incidents log. Both logs have filters that enable Admins to find necessary events easily. In addition to this, it sends alerts to notify admins on new threats and risks.
Additionally, SpinOne keeps a list of all the applications in its Risk Assessment section. It shows the app name, its risk score, the allow/blocklist status, and the number of users who have access to this application. By clicking on each app, administrators can get more information about it, such as the scope of permissions, location, category, business operation risks, etc.
The Number of Applications
SpinOne detects over 100,000 applications and browser extensions.
Application Assessment Criteria and Scoring
The SSPM uses 15 various criteria, divided into four categories: Security Scope, Business operation risks, Security Risk, and Compliance Risk.
It uses a complex scoring algorithm developed by the company’s cybersecurity experts. Apps can score from 0 to 100. The higher the score the safer the app.
Access Revoke Functionality
Admins can revoke application access directly in SpinOne. The SSPM enables you to carry out this procedure to one, several or all users.
Blocklisting & Allowlisting
SpinOne enables enterprises to create allowlists and blocklists and add applications there. Admins configure this functionality for one or several users, for the entire company or an organizational unit.
Security Policies
Using SpinOne, Administrators can set up several policies to govern applications. In particular, you can automate blocking/allowing apps based on their name or ID, category, developer, scope of permissions, or risk score.
Employee Requests
SpinOne enables users to send requests to the IT team for application approval. The functionality is embedded in the browser for users and in SpinOne platform for Admins. The list of requests is stored in a separate section, and administrators can easily approve or decline the requests in just few clicks.
Support
Spin Technology has 24/7 support via chat or email.
Pricing
Request Pricing here.
FAQ
Why is SSPM important for my organization?
SSPM is important for your organization as it can provide necessary visibility into your cloud and its vulnerabilities. In addition, it will help you close security gaps.
How does SSPM differ from traditional security measures?
SSPM differs from traditional security measures in the following way. Instead of creating perimeter security, it focuses on detecting and remediating the inherent SaaS risks, like sharing sensitive data.
Are all SSPM solutions the same?
SSPM solutions are built similarly, but they are not the same.
Can SSPM solutions guarantee 100% security?
No solution can guarantee complete security. However, a robust SSPM can significantly enhance your SaaS applications’ security posture and minimize risks.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


