Common Mistakes That Lead to Data Breaches

Data breaches are costly to your business, reputation, customer base, and future business prospects. As organizations experience more breaches across the board, costs continue to rise for companies and customers. However, costs typically get passed on to the consumer.
Surprisingly, many data breaches could be avoided by protecting infrastructure, processes, and technologies from common mistakes. So let’s dive into common mistakes that lead to data breaches and see how these can be avoided.
How costly are data breaches?
There are many types of cyberattacks that lead to tremendous costs for businesses. However, a data breach event can be one of the most costly. Recently IBM released the Cost of a Data Breach report 2022 with many eye-opening statistics for organizations to consider.
- 83% of organizations studied in the report have more than one data breach
- 60% of breaches led to increases in prices passed on to customers
- 79% of organizations operating critical infrastructure services didn’t have a zero trust architecture
- 19% of breaches resulted due to a breach of a third-party organization or business partner
- 45% of breaches were cloud-based
- The average total cost of a data breach reached USD 4.35 million
- The average total cost of a critical infrastructure data breach was USD 4.82 million
- When AI and security automation are deployed, organizations save an average of USD 3.05 million
- The average cost of a ransomware attack, without the cost of the ransom, totaled USD 4.54 million
- Stolen credentials caused 19% of breaches
- 59% of organizations don’t deploy or rely on zero trust architecture
- When remote work is a factor, it leads to an increase of USD 1 million
- Average cost savings associated with an incident response team (IR) and a plan that is thoroughly tested are USD 2.66 million
- Companies running extended detection and response XDR technologies experienced a savings of 29 days in response time
- Healthcare experienced the highest average cost of a breach for 12 straight years in a row
- USD 9.44 million – the average cost of a breach in the United States which is higher than any other country in the world
The above figures should get the attention of organizations today as they are certainly not insignificant. In addition, the untold or intangible costs of lost customer confidence tarnished brand reputation, and other variables can result in additional financial consequences for businesses struggling to recover.
Common mistakes that lead to data breaches
With the high cost of data breaches for organizations, avoiding them at all costs must be a top priority. Unfortunately, data breaches often start with common mistakes that lead to data being accidentally exposed or making it an easy target for attackers looking to steal critical or sensitive data. Let’s consider the following common mistakes that lead to data breaches:
- Weak passwords and password policies
- Leaky cloud applications and Shadow IT
- Cloud misconfigurations
- Unpatched vulnerabilities
- No proactive Ransomware protection
- Attackers capitalize on common security mistakes made in the enterprise
1. Weak passwords and password policies
The most common initial attack vector in 2022 was stolen or compromised credentials. As mentioned, it accounted for 19% of breaches, with an average cost of USD 4.50 million. Even more alarming, stolen or compromised credentials were the initial attack vector with the longest time for businesses to identify and contain the breach at 327 days. One of the reasons for this is compromised credentials activity often looks like legitimate user activity, so it goes unnoticed.
Organizations often miss the “low-hanging fruit” of adding multi-factor authentication to their on-premises and cloud environments. Even if user accounts contain weak passwords, multi-factor authentication drastically improves the organization’s security posture by adding the additional “factor” required for user authentication. The most common form of multi-factor authentication adds a one-time passcode or push notification to a mobile device, allowing a user to confirm or deny a malicious login.
Failing to bolster the organization’s login security often leads to epic data breaches. The ransomware attack on Colonial Pipeline is a great example of how serious compromised credentials can be. The Colonial pipeline ransomware attack started with breached VPN credentials that were used without multi-factor authentication.
2. Leaky cloud applications and Shadow IT
Another tremendous mistake many organizations make using cloud SaaS applications is failing to prevent users from installing leaky or insecure third-party cloud applications. Users with wide-open access to install any third-party cloud SaaS application lead to Shadow IT operations when they install unsanctioned cloud applications and grant access to business-critical and sensitive data.
When users can install any cloud application in the business-critical cloud SaaS environment, the application has not likely undergone a proper risk assessment. It may be unknown how the application handles the data if it stores it outside the environment or what security standards and protocols they follow.
Some users may intentionally resort to Shadow IT operations using unsanctioned applications to get around corporate policies or to store data in a way that allows access without any restrictions. Unfortunately, shadow IT can quickly lead to a data breach as data can be easily accessed in a risky or leaky way, exposing sensitive data. Allowing this kind of carte blanche access to third-party cloud SaaS applications is a common mistake many businesses make as they start to leverage cloud SaaS environments.
3. Cloud misconfigurations
Another common mistake that often leads to data breaches is cloud misconfigurations. We often hear about organizations mistakenly leaving an S3 bucket exposed to the outside world, allowing attackers or others to view or compromise massive amounts of business-critical data. What are examples of common cloud misconfigurations? These can include:
- Mistakenly exposed dangerous inbound ports – inadvertently exposing dangerous inbound ports, such as SSH, RDP, and others, can lead to attackers easily compromising internal resources with compromised passwords or brute force attacks
- Unrestricted outbound ports – Failure to restrict outbound ports can lead to data exfiltration dangers as users can connect to external resources and potentially copy sensitive data outside of the sanctioned
- Poor secrets management for development code – Code checked in that mistakenly includes API keys or even hardcoded, plaintext passwords can lead to compromised access
- Permissive privileged access – Privileged access is commonly given when it shouldn’t be granted as it makes it easier to give more than enough permissions without having to worry about exactly which permissions are needed
- Failure to implement role-based access – Tying into the above mention about privileged access, a common mistake with cloud misconfiguration involves failing to implement role-based access, leading to inappropriately permissive access
4. Unpatched vulnerabilities
Unpatched vulnerabilities in third-party software led to 13% of breaches in 2022 and cost an average of USD 4.55 million. In addition, hackers often look for unpatched vulnerabilities to launch ransomware attacks and other types of cyber attacks. A recent report found that unpatched vulnerabilities remain the most prominent attack vector exploited in ransomware attacks.
Often, vulnerabilities used to target organizations to launch ransomware attacks are vulnerabilities that have already been patched. But unfortunately, it means that businesses are failing to apply critical security patches to close the door on these types of exposures. It is a dangerous yet common mistake in the enterprise to let severe security vulnerabilities go unpatched or take too long to get them patched before exploits are in the wild and targeting critical resources.
In a Department of Homeland Security warning regarding the potential for Russian cyberattacks on critical infrastructure, DHS notes vulnerability exploitation as one of the common ways hackers can compromise critical networks.
CISA has observed Russian state-sponsored advanced persistent threat (APT) actors using common tactics in the past to successfully deploy cyberattacks, including spear phishing, brute force, and vulnerability exploitation.
No proactive Ransomware protection
Businesses often have a very reactive stance when it comes to ransomware attack. Usually, once a ransomware attack is discovered, it is already too late, with business-critical data having been encrypted once the ransom note is discovered. However, failure to employ next-generation cybersecurity solutions that use artificial intelligence (AI) and machine learning (ML) to help identify and stop anomalous activity leads to long recovery times, data loss, and even intentional data leaks.
Ransomware groups are now using a tactic known as double extortion to inflict maximum damage to victim organizations. What is double extortion? With double extortion, ransomware groups not only charge a ransom for recovering encrypted data but also ask for payment to prevent the data from being intentionally leaked on the dark web.
The double extortion scenario is becoming more common for businesses impacted by a ransomware attack. Simply having effective data backups does not protect you from the threat of data leaks. More is needed. Proactive ransomware protection solutions look for the common indicators of attack and prevent the attack from progressing using cybersecurity automation.
It would be a mistake for organizations today not to have proactive ransomware protection, both for on-premises environments and cloud SaaS environments.
SpinOne helps eliminate data breach mistakes automatically
More companies are migrating their critical data to cloud Software-as-a-Service (SaaS) environments. However, common mistakes can be made, even in the cloud, without the right processes, procedures, workflows, and technologies in place, leading to data breaches.
SpinOne is a modern cybersecurity solution that leverages artificial intelligence (AI) and machine learning (ML) to provide robust cybersecurity automation in cloud Software-as-a-Service (SaaS) environments. Using SpinOne, businesses can prevent many common mistakes that lead to data breaches.
Note the following key capabilities of the SpinOne platform:
- Automated risk assessments of third-party cloud SaaS apps – Manual risk assessments of cloud SaaS apps in the cloud marketplace can be time-consuming, labor-intensive, and ineffective. SpinOne takes the heavy lifting out of this process so businesses can have a proactive, automated risk assessment that can be used with cloud SaaS policies to enforce the use of only sanctioned cloud SaaS applications
- Policy-based cloud SaaS app control – SpinOne leverages policy-based automation to enforce governance and cybersecurity controls across the cloud SaaS environment
- Visibility to cloud data shared outside the sanctioned environment – Quickly see which data is shared externally, which users are sharing the data, and to whom it is shared. SpinOne allows admins to disable data sharing outside the organization quickly.
- Prevents data leak due to accidental or intentional sharing of data with external users – With policy-based controls and enforcement and automated cloud SaaS risk assessments, organizations can effectively limit data sharing, third-party applications, and other risks in the environment
- Provides automated backups of your cloud SaaS environment – With SpinOne, you get true enterprise backups of your critical data. You can also choose where your cloud SaaS data is stored in your cloud-to-cloud backups, in line with the 3-2-1 backup best practice model.
- Protects against insider threats – Gain visibility to unscrupulous activities of malicious users or quickly identify the possibility of compromised credentials
- Provides proactive Ransomware Protection with automated remediation – A unique offering from SpinOne is automated ransomware protection, automatically remediating ransomware threats in your cloud SaaS environment
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
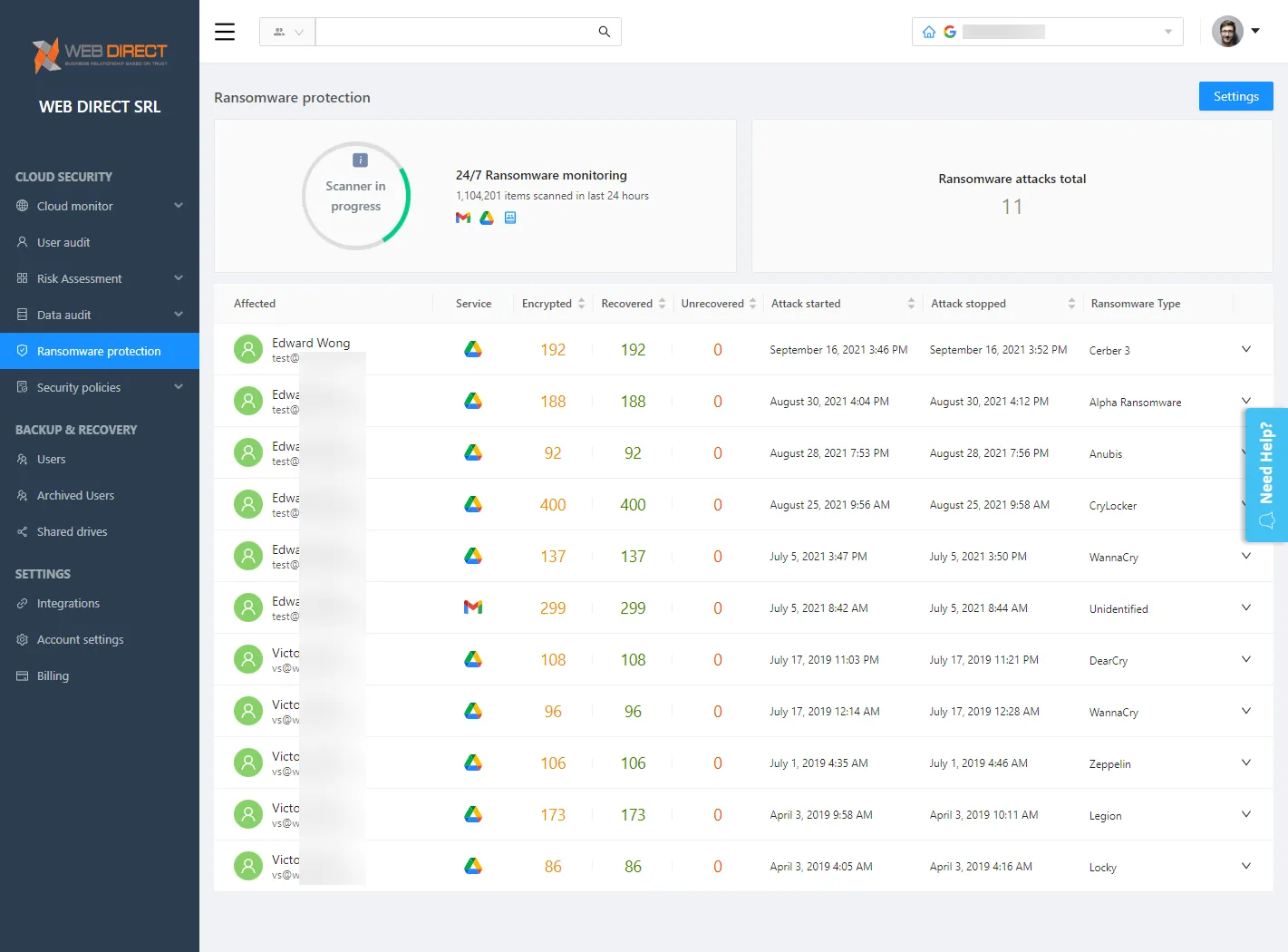
SpinOne Proactive Ransomware Protection
One of the powerful features, as mentioned with SpinOne, is the proactive Ransomware Protection module. It provides cybersecurity automation to handle a ransomware attack in your cloud SaaS environment. Note the automated response to a cloud SaaS ransomware attack:
- An automatic cybersecurity scanner, empowered with artificial intelligence, scans your cloud SaaS environment for ransomware 24x7x365
- If ransomware is discovered, it automatically blocks the ransomware process
- SpinOne identifies all files that may have been initially affected by the ransomware
- The files are then automatically recovered, leveraging Spin’s automated cloud SaaS backups
- SpinOne notifies the cloud SaaS administrator about the ransomware attack
Wrapping up
Businesses can avoid many data breach events by avoiding the common mistakes that lead up to compromise or accidental exposure of business-critical and sensitive data. Unfortunately, attackers look for these common mistakes organizations make to find a short path to infiltrating networks, launching ransomware attacks, and stealing sensitive data. Therefore, organizations must stick to best practice methodologies regarding passwords, role-based access, least privilege access, cloud configurations, and ransomware protection.
SpinOne provides a robust, automated cybersecurity solution allowing businesses to take control of the protection and security of critical data in cloud SaaS environments. Learn more about SpinOne and the capabilities and features it provides here: Enterprise ransomware protection and apps security solutions (spin.ai)
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
What You Need to Know About AT&T’s Data Breach and How t...
Arguably, it is one of the worst breaches that has happened recently. AT&T disclosed in...
Lessons from the Twilio Breach: Securing SaaS Applications Against ...
Another recent security breach has made organizations think yet again about SaaS apps they may...
Unpacking the CrowdStrike Outage: Causes, Impacts, and Protecting Y...
A major global IT outage occurred on Friday, July 19, 2024, causing widespread disruptions across...



