Effective Steps to Take During a Cloud Ransomware Attack
In 2023 alone, 72% of companies were affected by ransomware, a significant increase compared to 55% in 2018. Unless your business has a reliable ransomware protection solution, the risk of getting infected remains high. In this article, we discuss what companies should do in the event of a cloud ransomware attack.
The number of ransomware attacks has been steadily increasing for the past decade. This type of malware attacks both cloud and on-prem environments and makes its way to the IT systems of businesses regardless of their size. The most recent trend of stealing data prior to data encryption forced many companies to pay ransom.
Recognizing a Cloud Ransomware Attack
Since ransomware encryption takes time, it’s critical to detect it early on. Let’s take a look at the signs and symptoms of a ransomware infection.
If you do not have special tools that can track abnormal logins or downloads, you will most likely miss the early signs of a ransomware infection. It usually starts with the hacker infiltrating your cloud environment and in some cases scanning for the opportunity to steal data. The alert of an abnormal login (outside the regular region or time frame) can be the first sign.
The second symptom of a ransomware infection is the mass editing of the data in your environment. This is a detectable event as the content of the files will be encrypted (and in some cases their names too). However, this event is easy to miss if you do not have specific monitoring tools as it often happens outside your regular business hours.
Check out how encrypted files look in OneDrive:
Unfortunately, the tactics of early detection forced many ransomware gangs to apply intermittent encryption tactics. In short, the infection doesn’t encrypt all the data, instead, it focuses either on the files of a specific size or with specific keywords. This tactic guarantees faster encryption while making sure that files of the greatest importance are lost in the attack.
Other possible signs of a ransomware attack are new users or Admins. Some hackers get into your system by stealing the credentials. Once in the system, they will try to find ways to increase their privilege, i.e., get more access and more control. Logging in your system as an Admin will give them greater control over it. They can then create new users and assign them as Admins. In this case, they’ll be able to return to your system through the backdoor and infect it again.
Immediate Actions to Take
There are several immediate actions you need to take to minimize the impact of ransomware on your company. You need to inform all the people on the incident response team immediately and begin carrying out your incident response plan. If you do not have any, below we discuss in detail your company’s next steps.
First, you need to inform the management, the legal department, and the IT security team about the ransomware attack. While management and legal departments inform law enforcement and the clients, the IT security team needs to find the source of a ransomware attack.
Cloud ransomware works as any SaaS application. It has OAuth access to your data with editing permissions – that is how it encrypts your data. Your team needs to find this application and revoke its access to your cloud environment.
It is also important to keep a record of every step your team has taken for further analysis of the incident response efficiency and the investigation of the incident.
Assessing the Scope of the Attack
Once you have stopped the ransomware attack, it’s time to assess its scope and impact on your data and environment. First of all, you need to understand, how much data has been encrypted and how much data has been left intact.
Second, you need to look for a decryption key. There are several organizations that can help you identify the ransomware strain and provide a decryption key for free. Keep in mind though, that ransomware is a type of malware that is easy to develop. That’s why we see several new strains each year. You might be lucky enough to get infected with the old variant and find a decryption key. However, the probability isn’t high.
Third, you might want to change all the passwords of your accounts. Ransomware gangs often get access to your cloud environment by stealing the credentials of one of your users. If you do not change passwords, you risk leaving the back door for the criminals to your system.
At this stage, you would also want to look at any new accounts that have been created over the past week. You need to make sure that they belong to the real employees and haven’t been created by hackers as a backdoor.
If the decryption key is available, you can now recover your data. However, if you do not have it a deeper evaluation of your situation is required.
The IT security team needs to provide management with a realistic time frame for data recovery provided you have a backup. Remember, that cloud environments have API limitations that make data recovery from backups extremely slow.
You also need to communicate the percentage of companies that managed to recover their data with the decryption key they got from the ransomware gang is around 50%. Finally, you need to investigate if cybercriminals stole any of your data.
Upon receiving all this information from the IT department and getting legal advice from the lawyers, management needs to make a decision on whether to pay ransom or not.
Recovery and Restoration
At this stage, the IT department needs to come up with and implement a recovery strategy. If your management decides against paying the ransom, the data restoration from the backup can take weeks or months.
You need to have a clear-cut strategy on which files to recover first. You also might want to transfer some of the operations to the backup IT systems, e.g., drafting and storing documents in another IT system, or temporarily introduce the BYOD practice.
While data is being recovered from backup or with the help of the acquired decryption key, your IT system department needs to continue investigating the source of the attack. Was it social engineering, vulnerability exploit, account hijack, or malicious intent of one of your employees?
Simultaneously, your legal department needs to assess the legal implications of this attack. Despite the fact that you are the victim in this situation, your government, partners, or clients can still press charges. The reasons for non-compliance can range from insufficient data protection to data leakage to third parties.
At the same time, management has to deal with the consequences of the attack for your business and its reputation.
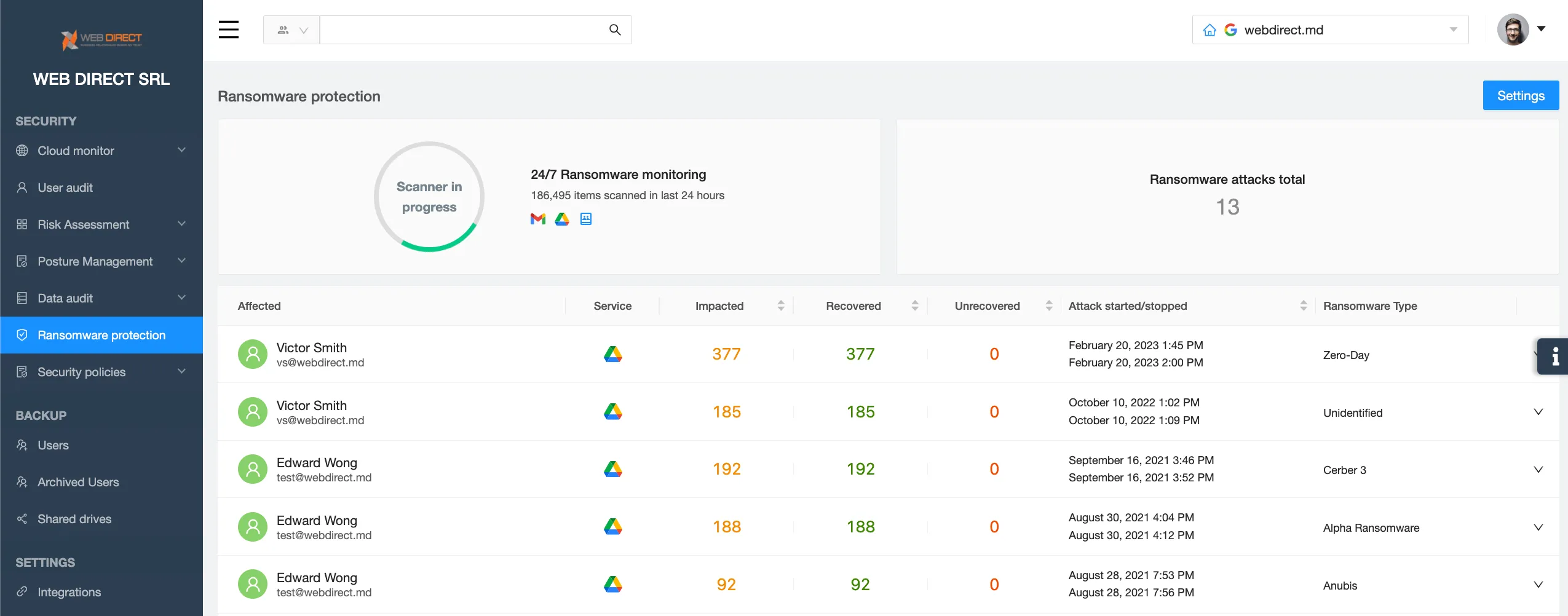
Learning from the Ransomware Attack
At the final stage, the IT security department finalizes the investigation and identifies the security gaps in cloud security. Next, the prevention steps should be taken to avoid the next ransomware attack. Statistics show that about 50% of ransomware victims get hit by ransomware for the second time, and about 30% for the third time.
You will want to study the ransomware protection solutions to avoid another ransomware attack on your business. Learn about cloud ransomware protection.
Ransomware Prevention
Below we summarized Ransomware prevention steps every business should take:
1. Get automated backup for your data
Tools like Spinbackup can help you prevent the loss of your data in case of a ransomware attack. They will also come in handy in other cases of data loss. Keep in mind that backup only helps you to prevent data loss.
2. Increase your access control
Impose strong passwords in your organization. Strong passwords contain capital letters (e.g., “I”), numbers (e.g., 17), and special characters (e.g., $). Make sure your users change passwords regularly.
3. Start cyber awareness training
It can help your employees recognize social engineering techniques and potentially prevent a ransomware attack. If you have no time or resources to do it in-house, find an outsourcing firm. The most important thing about such training is its regularity. Another important aspect of the training is the ability to train on simulated attacks (e.g., fake phishing emails).
4. Begin controlling your applications
First, many successful ransomware attacks begin with vulnerability exploits in SaaS applications. Second, cloud ransomware is a SaaS application, only a malicious one. Cloud office suites have functionality that helps you detect the applications. However, they often lack risk assessment, revoke access features, and automation. Having a tool that can notify you about and ban risky applications automatically, can help you cut the attackers before they can get to your system.
5. Get a ransomware protection tool
Ransomware protection tools can become your last layers of defense when all other defenses have proven inefficient. However, not all solutions are equally good. There are three main types of such tools: historical, traffic-based, and based on data behavior.
Historical detection is based on the ransomware data that is available in their database. They compare the program to the samples they already have and make a decision whether it’s ransomware or not. Unfortunately, with so many strains emerging every day, historical detection cannot keep up with the hackers.
Traffic-based detection analyzes the traffic in the system. It detects ransomware by the unusual spikes of the traffic. Unfortunately, such a method can create many false positives, as spikes in traffic can occur naturally, e.g., during project deadlines.
The last class of tools analyzes how data is behaving in the system. They use AI that is capable of detecting trends that humans cannot detect. This method doesn’t rely on historical data about ransomware or traffic spikes.
SpinOne ransomware protection is an example of a tool that analyzes data behavior. It successfully detects cloud ransomware. Next, it finds its source application and revokes its access to your system. Then it recovers files from the inbuilt backup, all within a couple of hours after the attack.
Try SpinOne Ransomware Protection
FAQs
Why is it important to be prepared for a ransomware attack?
Being prepared for a ransomware attack is crucial for several reasons. First, it allows for early detection of ransomware, enabling containment and mitigation of potential damage before it spreads throughout the network. Second, prepared organizations regularly back up their data to be able to quickly restore it in case of a ransomware attack or other data incident. Third, preparation minimizes downtime, ensuring that critical business operations can resume quickly, reducing financial and reputational losses. Finally, being prepared for a ransomware attack demonstrates a commitment to security and data protection, so it helps maintain the trust of customers and stakeholders.
What are the common signs of a ransomware infection?
There are several common signs that may indicate a ransomware attack. These include (but are not limited to):
Uncommon file extensions. Files on your system may have unexpected extensions, such as .locky, .crypt, or .xyz, indicating that something went wrong and you might have been encrypted by ransomware.
Changed File Names. Files may have their names changed to a random set of characters.
Inability to access files: You may suddenly being denied to access your files because they are corrupted, encrypted, or otherwise inaccessible.
Ransom notes. Ransomware typically leaves messages notifying you of the attack and offering instructions on how to make the ransom payment to recover access to your files.
Unusual network traffic: Ransomware frequently interacts with its command servers to receive instructions and send encryption keys. If you notice a notable surge in network activity, especially outbound traffic it may suggest a potential ransomware infection.
Spike in disk activity and system responsiveness. Encrypting data by ransomware is a resource-intensive process, so it would negatively affect your system performance.
Unauthorized creation of new accounts as attackers try to create a backdoor in your network, which allows them to penetrate the systems and encrypt files.
What should I do immediately if I suspect a ransomware attack?
When suspecting a ransomware attack, do the following immediately:
Cut off your incoming and outgoing connections (disconnect from your Wi-Fi, turn off your device, unplug your ethernet cord, etc.). This helps isolate the affected devices from the network and prevent the ransomware from spreading to other systems.
Disconnect external storage devices. Ransomware often tries to corrupt your hard drives, thumb drives and other external storage devices where essential backups and data are stored. Thus, quickly remove your external devices to ensure they remain clean.
Alert relevant parties. Inform your IT department immediately to obtain guidance and initiate incident response procedures. If the attack is severe or involves sensitive information, consider reporting the incident to law enforcement agencies.
Where can I find additional resources and tools for ransomware prevention and response?
Along with backups, MFA, zero trust approach, and other ransomware prevention mechanisms, consider using adaptive technologies that ensure 24/7 threat detection, investigation, and response like SpinOne Ransomware Protection. SpinOne incorporates AI-based cybersecurity measures that back up and recover files that might have been exposed to ransomware. Combined with robust automated backup and recovery functionalities, SpinOne integrates AI-driven cybersecurity measures that independently restore any files that may have undergone encryption by ransomware.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


