How to Find & Disable Risky Apps in Your Google Workspace
Do you know how many apps and extensions actually have access to your Google Workspace data? On average, an SMB uses about 1,000 applications. And only 10% of them are known to the IT department. The rest remain in shadow, creating one of the greatest gaps in your cybersecurity.
Unlike Office 365, Google Workspace (formerly G Suite) has very limited functionality to monitor or control unauthorized apps and extensions. That’s why SecOps teams spend tremendous amounts of time and money mitigating the associated risks.
That’s when our G Suite CASB solution SpinOne comes in handy. It enables you to:
- identify all the apps and extensions with access to your Google Workspace
- automate their risk assessment
- grant or revoke app access to your data
- hit your compliance goals
- protect the cloud from malware attacks
- increase the efficiency of your SecOps while decreasing their costs.
Learn what problems CASBs solve in detail or find out more about how you can secure your Google Workspace with SpinOne below.
How SpinOne Finds Apps and Defines Which Ones Are Risky
Google Workspace (formerly G Suite) logs every event that takes place within the cloud. This includes granting access to an application or extension. G Suite Admin can view these events in the Audit Log Section of Admin Console.
However, identifying a cyber incident in the daily flow of events, even in a small organization, is problematic. You need a tool that will cherry-pick the app-related logs and turn them into comprehendible data.
That’s exactly what SpinOne does. It accesses the Google Workspace logs via API to compile and analyze them. Then, it represents the results of the analysis in the form of a report. Since our tool works 24/7 all year round, SecOps always get their hands on the fresh data.
The AI at the core of SpinOne uses:
- information from multiple sources, e.g., the database of 100,000+ apps;
- the complex score calculation algorithm;
- the risk criteria.
Here are the app risk assessment criteria that SpinOne applies:
- Business operation risks:
- App rating;
- Category (business, entertainment, productivity);
- Update frequencies;
- Developer reputation;
- The number of users.
- Security Risks:
- Scope of permissions;
- SSL certificate status;
- Domain history;
- Known vulnerabilities;
- Data Transmission Encryption
- Compliance Risks:
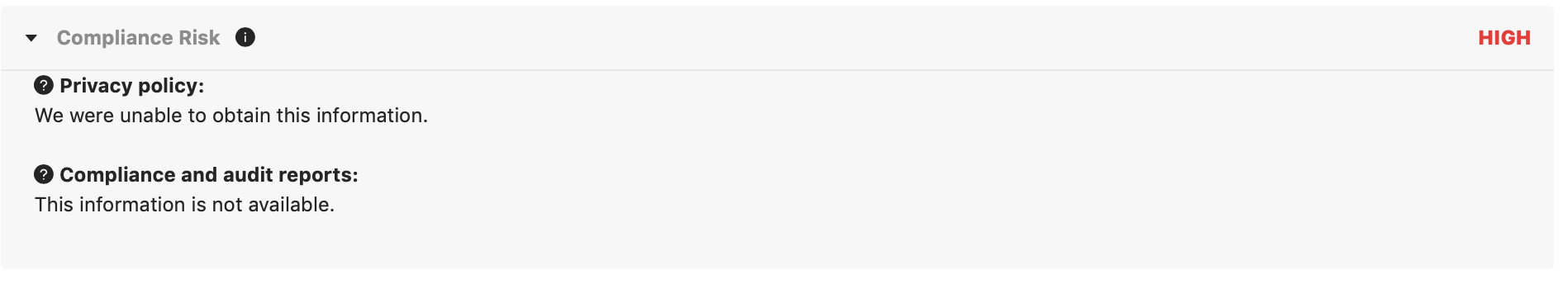
- Privacy policy
- Compliance and audit reports
- Developer Jurisdiction
Each criterion has a certain number of scores assigned to it; the higher – the more secure. The maximum score an app or extension can get is 100.
Apart from scores, SpinOne provides extensive risk assessment reports on each application. Google Workspace Admins can see the assessment criteria there to make a final decision on revoking or keeping the access.
Let’s take a closer look at SpinOne risk assessment reports in our next section.
How To Monitor And Control Risky Apps And Extensions In Your Google Workspace With SpinOne
You can check which apps have access to your G Suite in 2 sections of the SpinOne Admin Panel: Risk Assessment and User Audit. Each of them contains extensive app reports and black/whitelisting functionality.
Risk Assessment
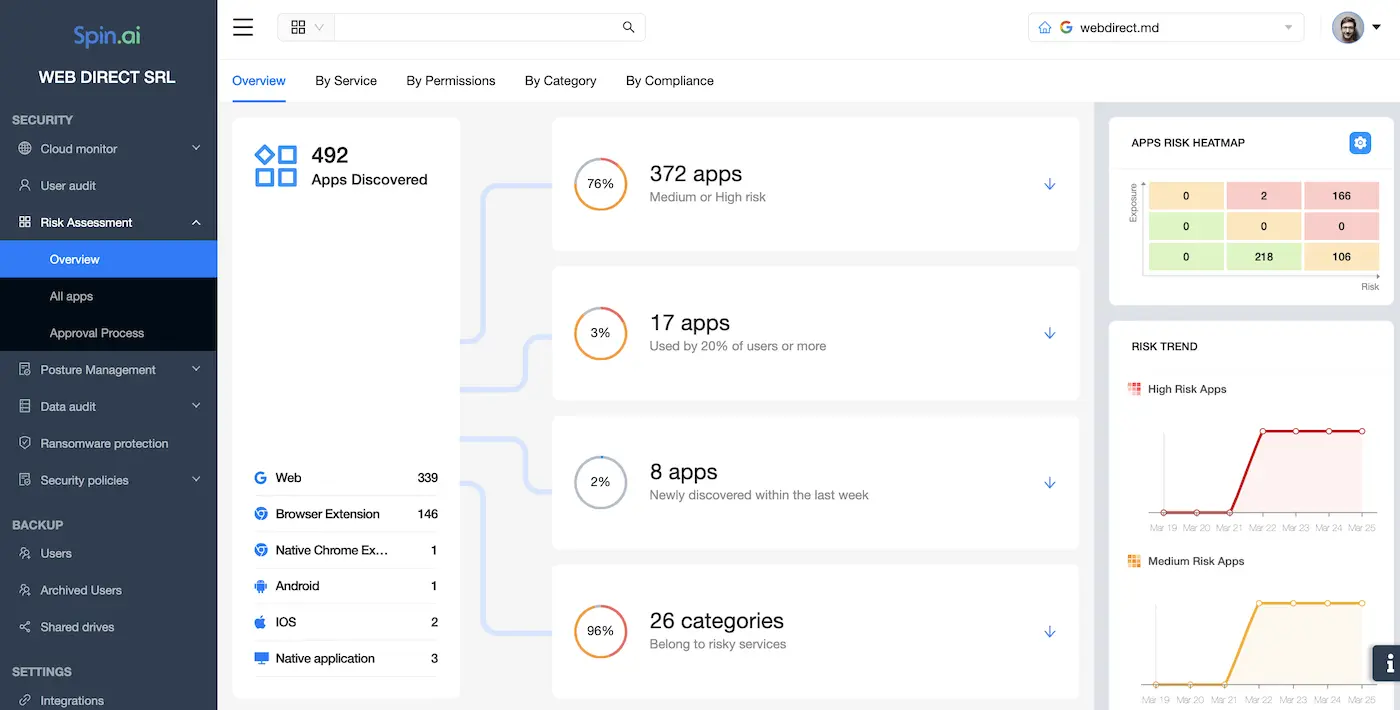
This section gives you a birds-eye view of all the apps and extensions that have access to your Google Workspace via OAuth:
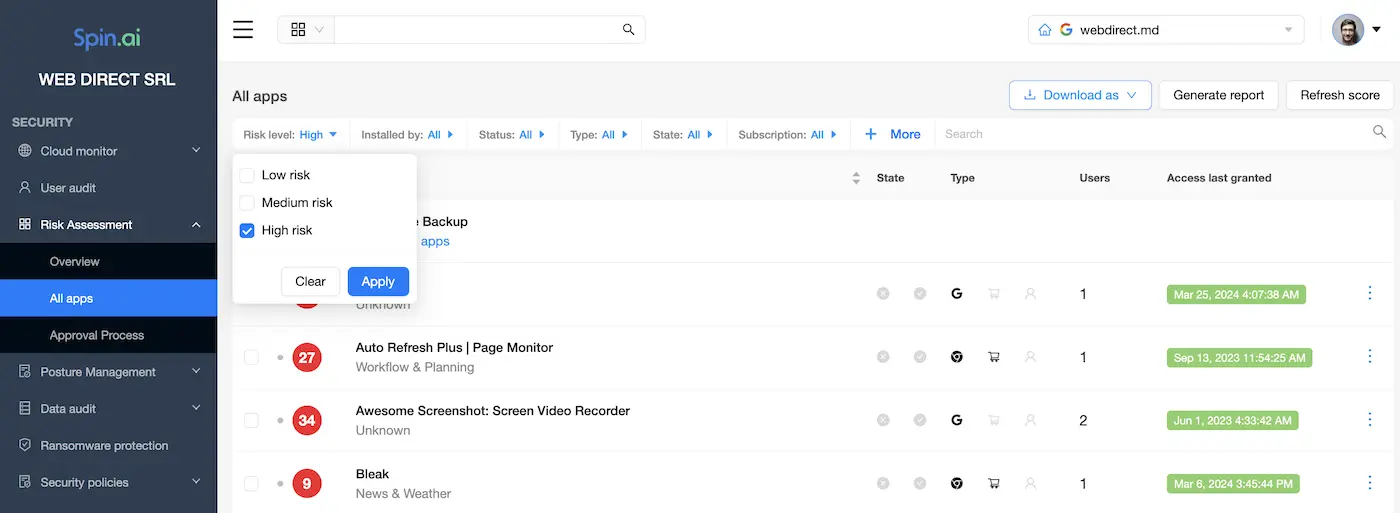
You can see here the list of apps with their scores, type, block state, number of users, and date of access. In addition to that, SpinOne provides filters for easier management and enables you to download the list.
By clicking on an App, you can get an in-depth report that begins with the general overview:
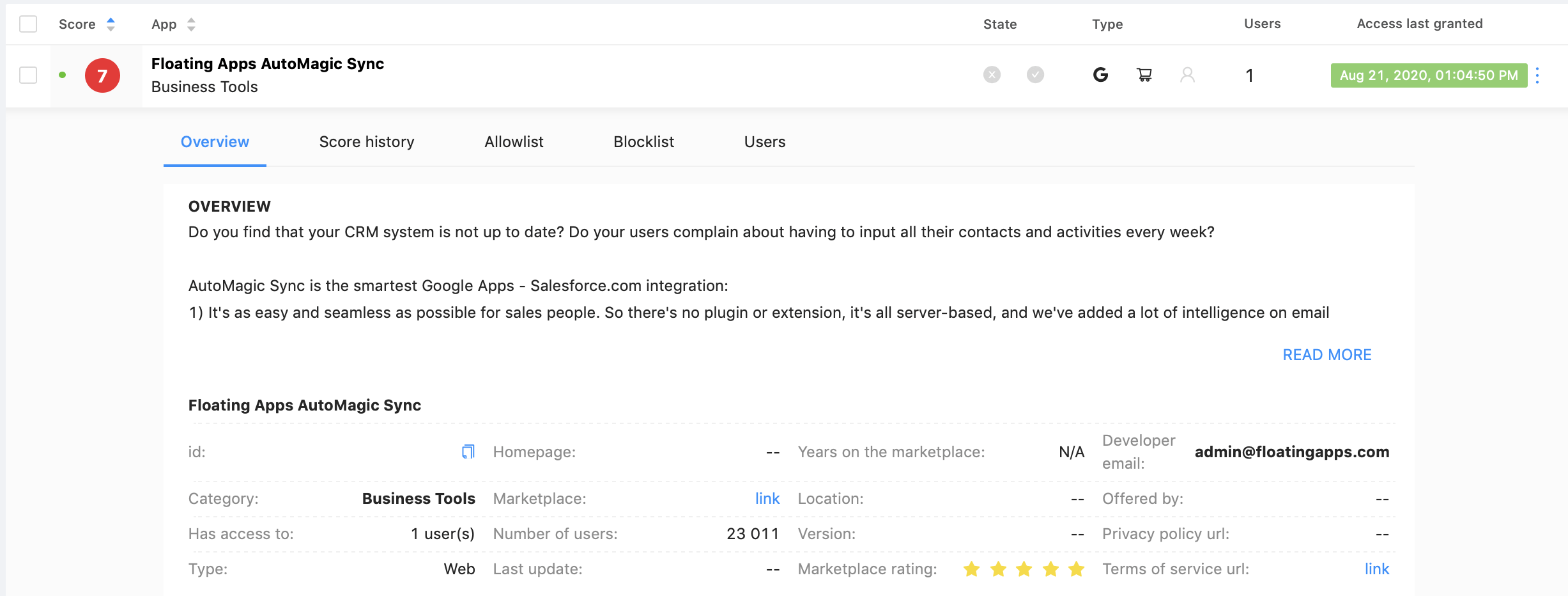
If you scroll down, you can see more details on each category (Business operation, Security, and Compliance).
Check out the application’s scope of permissions in the screenshot below. It is enormous. Not only does it have access to your data, but it also can alter it. SpinOne considers such scope risky for the cybersecurity of a company. That’s why the app will get a low score in the respective category.
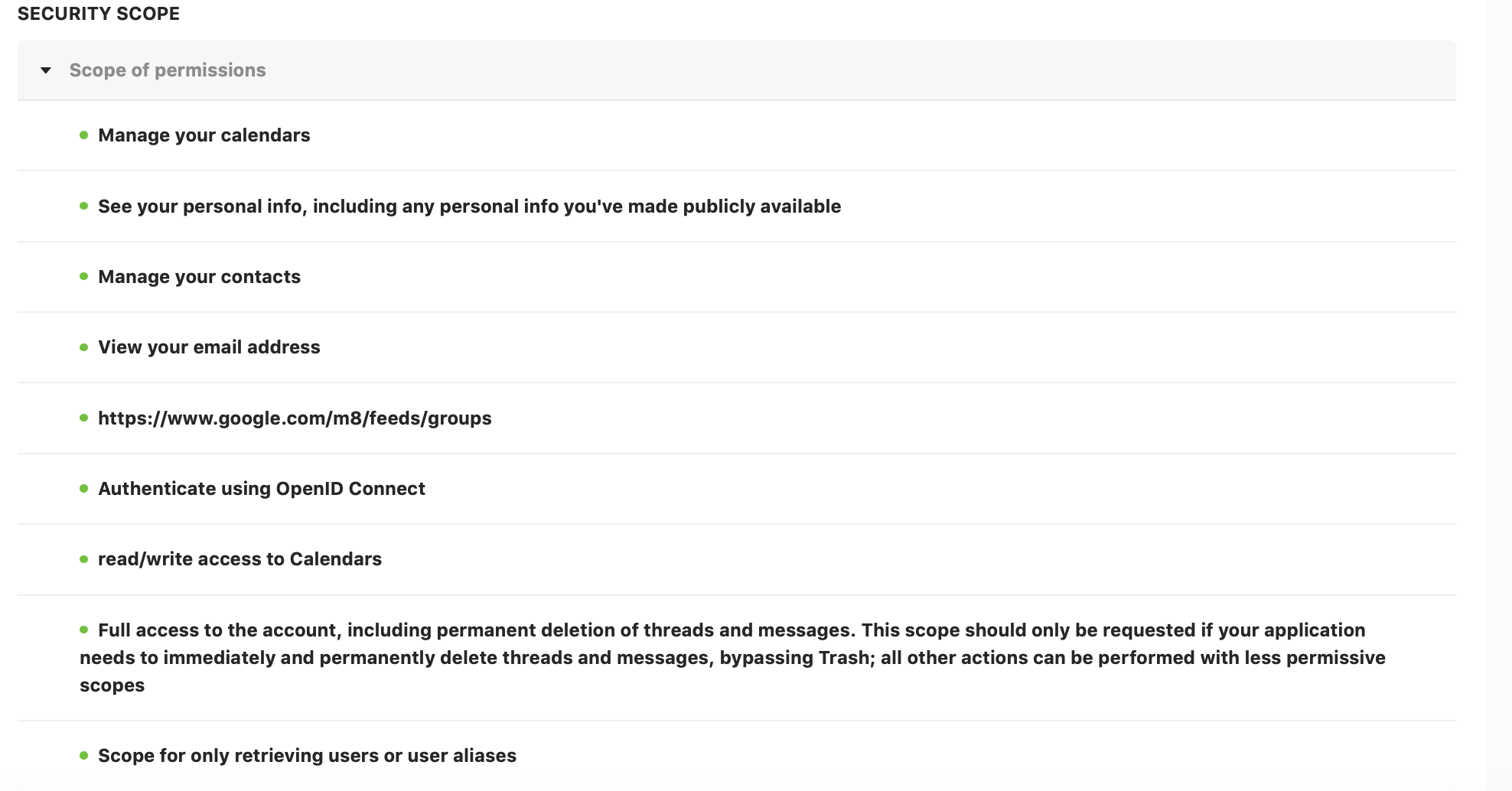
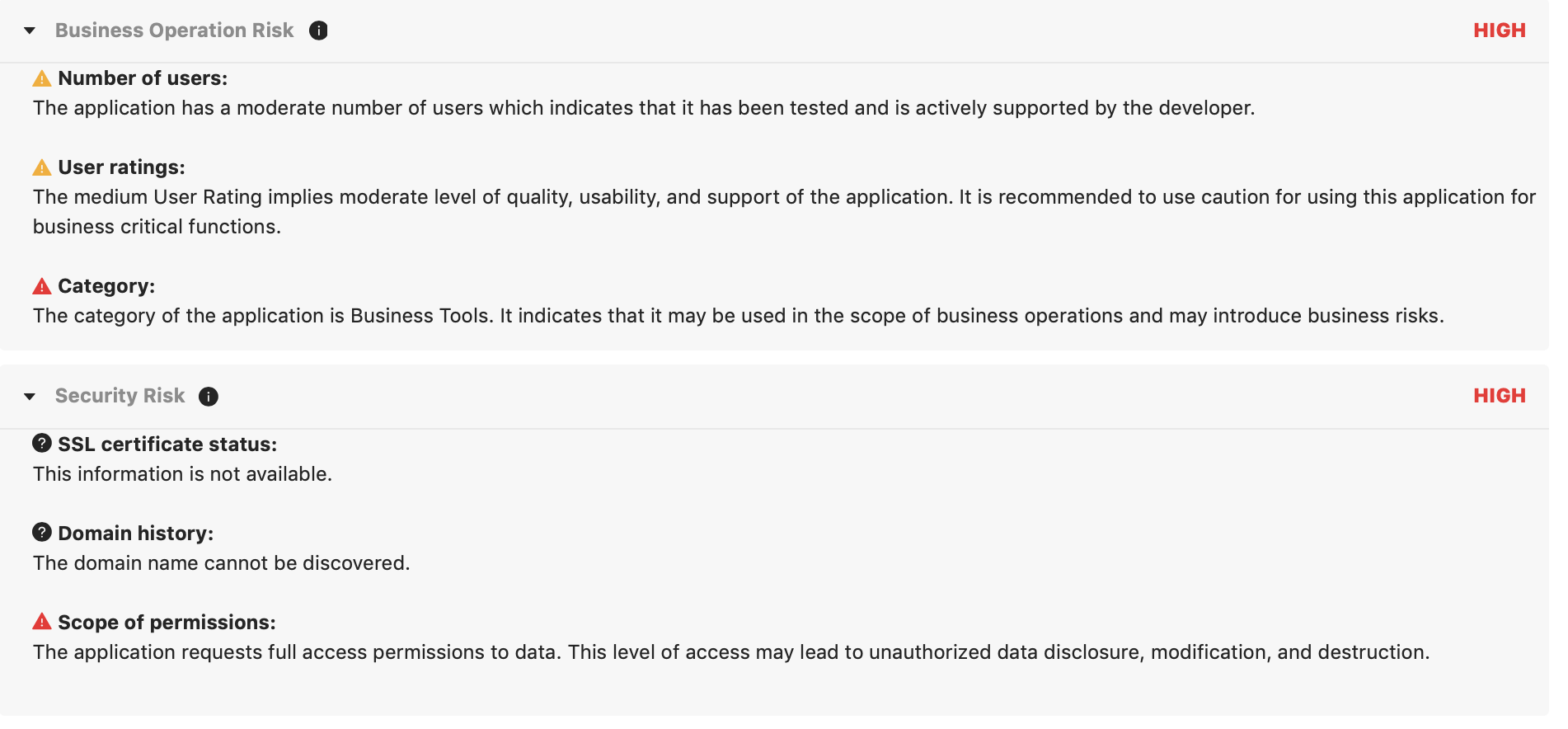
Finally, there are the compliance risks as the app never provided a privacy policy or compliance audit reports.
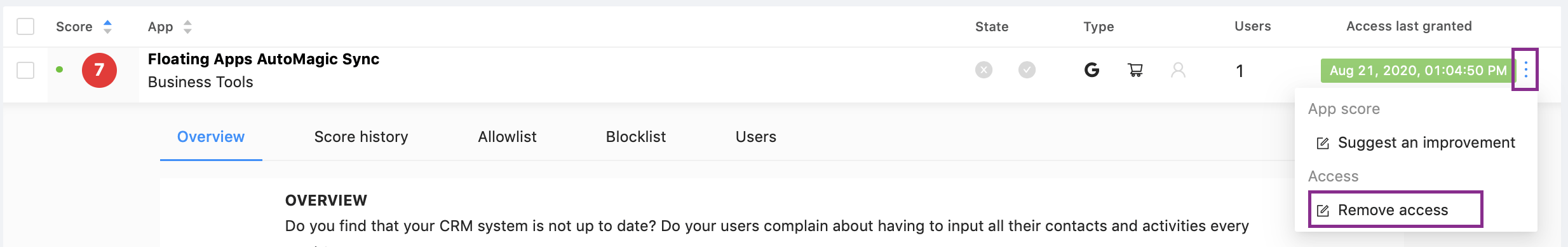
If you consider this app dangerous, you can easily revoke its access to your Google Workspace right on the spot:
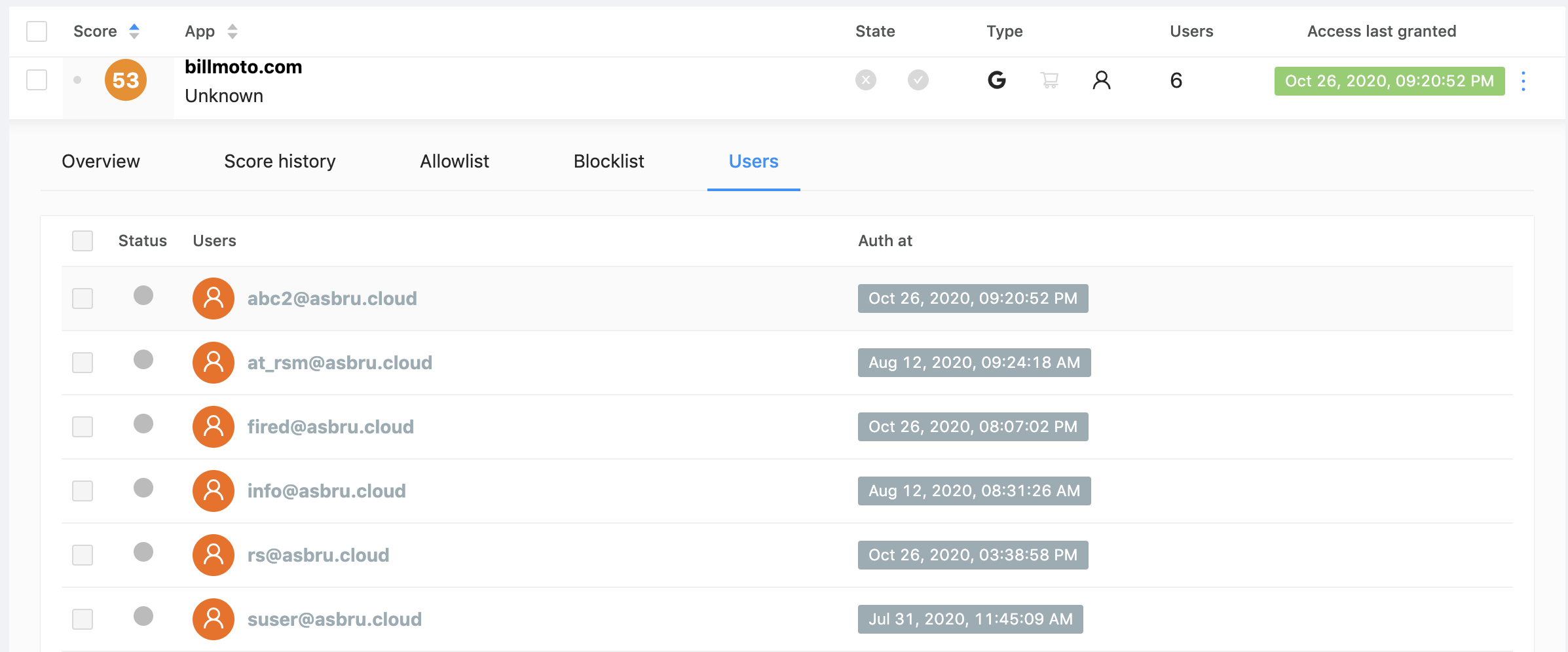
However, before revoking access, we suggest you look at who is using it in the User section of the report:
Sometimes, you will need to restrict access for some users. It can be easily achieved by making a block or allow lists:
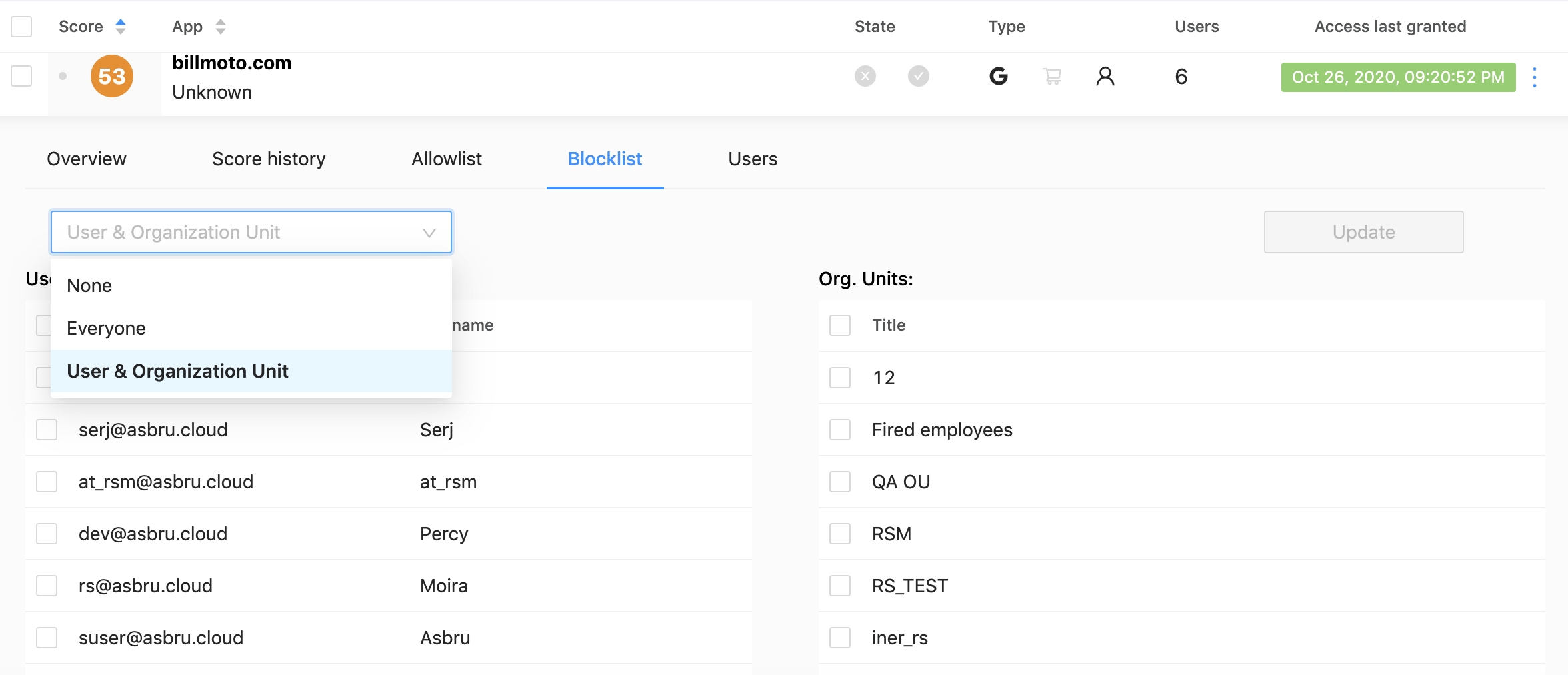
Just tick some users or organization units in the Blocklist section, and they’ll permanently lose their access to the application.
Users Audit
This section enables you to see what apps and extensions a certain User of your Google Workspace can access via OAuth.
All you need to do is click on the user name. You’ll be redirected to their page. Click on the Risk Assessment tab and check out all the apps of this user:
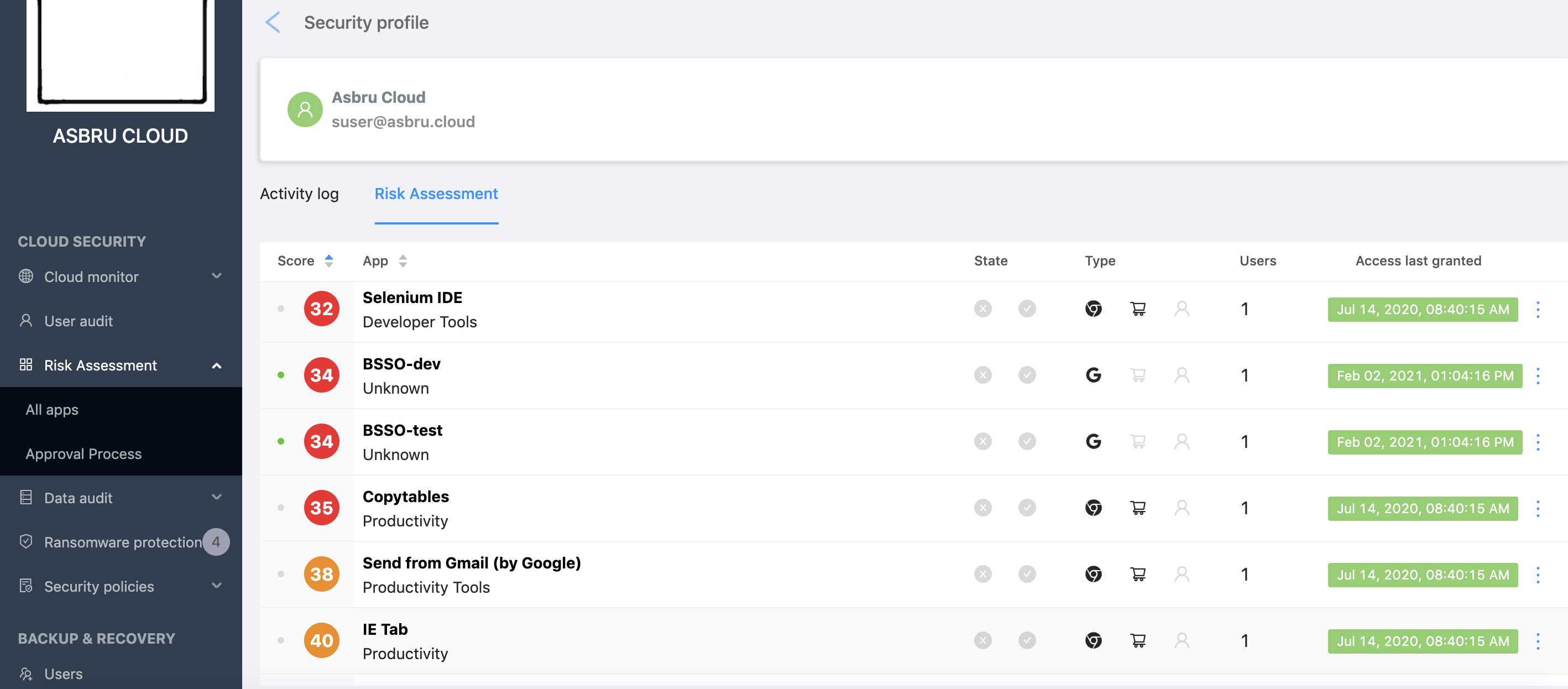
You can click on the app and get a detailed report similar to the one we described above.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


