Many are afraid of what “lurks in the shadows.” For a good reason, what we can’t see can hurt us the most. While this is undoubtedly true in the physical world, it is also true with the world of cybersecurity threats at the hands of “shadow IT.” What is shadow IT? What dangers does it pose to business-critical data? Is it a threat in cloud Software-as-a-Service (SaaS) environments? How to prevent shadow IT?
What is Shadow IT?
What is this elusive term, “shadow IT,” and why is it so dangerous? Shadow IT describes any unsanctioned activity, software, hardware, or service used by an end-user without the expressed approval from the business, specifically IT. Information Technology (IT) is generally responsible for configuring and securing solutions used in the organization.
What are the dangers of Shadow IT?
If end-users use products and solutions out of the purview of IT, there can be tremendous security consequences for the business. But, again, the dangers of Shadow IT go back to a lack of visibility. When businesses have no visibility into activities, software, solutions, behaviors, and so on, it can open the company up to the potential for malicious activity and data leak or compromise.
We can think of Shadow IT as someone having a key to your house without you knowing about it. It is unnerving and certainly sends a chill up the spine of CIOs and SecOps. Organizations must have visibility to user activities, the software they are using, and any solutions with access to business-critical data.
Is Shadow IT a threat in cloud Software-as-a-Service (SaaS) environments?
Everything is visible in the cloud. Right? It would seem that modern cloud SaaS environments, running on top of world-class data centers, would leave nothing lacking in visibility and controls over shadow IT activities in the cloud environment. However, this could not be further from the truth.
Cloud Saas environments such as Google Workspace and Microsoft 365 provide state-of-the-art tools and solutions to businesses worldwide. Both solutions make it very easy for users to collaborate, communicate, and use integrated cloud services through marketplace environments.
However, this is a double-edged sword. It means that users, by default, can integrate any cloud apps into a business-critical cloud SaaS environment with sensitive data. As mentioned previously, this opens the business up to data leaks, data compromise, and the potential for malicious activity.
Shadow IT is not always the result of an intentional or malicious end-user activity or decision. It can happen innocently. Users may inadvertently install browser plugins or cloud apps when prompted without considering the ramifications to overall business cybersecurity.
It helps to underscore the necessity of organizations to have both visibility and control over cloud applications installed in the cloud SaaS environment. Cloud apps may be installed and granted high-level permissions, assuming the user’s permissions via OAuth, without enforced controls.
OAuth and Shadow IT
OAuth is the “magic” behind easily installing and integrating cloud applications in cloud SaaS environments without giving the app your account password. Instead, the application is granted an authentication token which allows the app to operate with the same permissions as the user, without knowing the user password.
OAuth is a modern authorization technology powering today’s cloud SaaS environments. Users involved with Shadow IT activities grant OAuth tokens to the applications installed in the cloud SaaS environment. As a result, end-users may not scrutinize the permissions requested or the ramifications of permissions granted to a particular cloud application, resulting in very high-level and dangerous permissions assumed by cloud applications not sanctioned or secured by IT.
If an application is malicious, potentially even containing ransomware, the malicious cloud application has the permissions to encrypt all the user’s data and any data the user can access. OAuth tokens even bypass two-factor authentication in cloud SaaS environments and must be manually removed if compromised.
Prevent Shadow IT in cloud SaaS with SpinOne
Preventing Shadow IT in cloud SaaS environments is vital to the cybersecurity posture of modern organizations leveraging cloud SaaS solutions. However, organizations often struggle with native cloud cybersecurity tools and monitoring as these can be disjointed and disparate, even depending on the cloud SaaS subscription level.
SpinOne is a modern SaaS Security Posture Management (SSPM) solution that uses artificial intelligence (AI) and machine learning (ML) to monitor and automatically remediate cybersecurity events effectively. In addition, SpinOne provides the tools needed to prevent Shadow IT activities by end-users.
It includes both the monitoring and control features businesses need to defend against cybersecurity threats successfully, including Shadow IT activities.
Note the following features:
- Risk Assessment – The risk assessment features provided by SpinOne include the ability to monitor cloud applications integrated with the cloud SaaS environment. SpinOne’s security automation continuously provides a risk assessment of cloud applications and scores them based on their behavior. This reputation score can change if the application begins to behave maliciously.
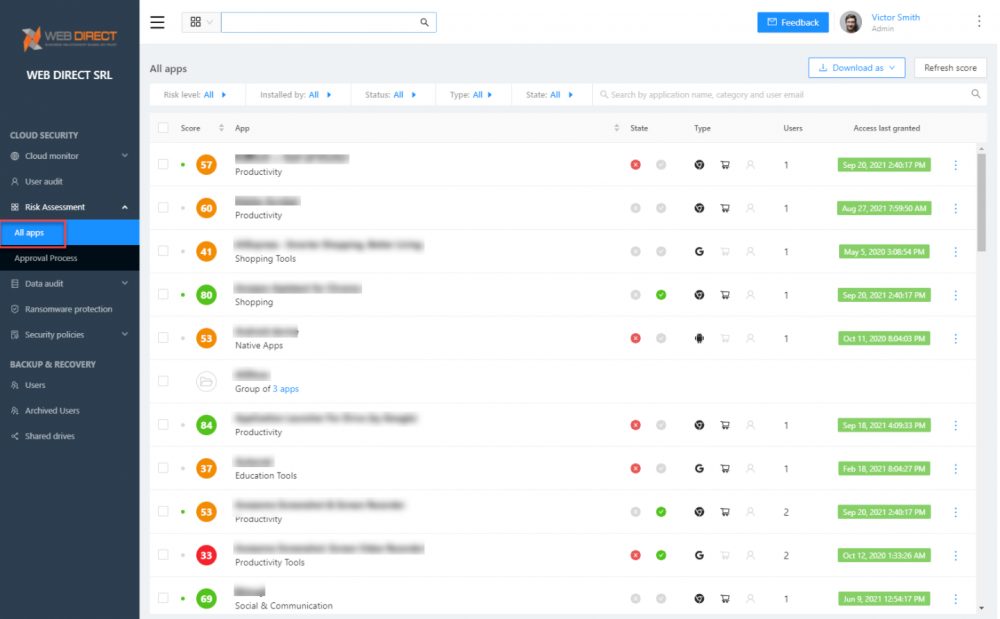
SpinOne provides real-time risk assessments of cloud applications
- Cloud Monitor – The Cloud monitor dashboard provides a single-pane-of-glass view of your cloud SaaS environment and gives visibility to both cloud environment events and SpinOne-specific events. It allows IT admins to have a single view of events taking place in the environment. This visibility strengthens the overall cybersecurity posture of the organization. Admins can quickly view the Incidents dashboard of the Cloud monitor to view cybersecurity events.
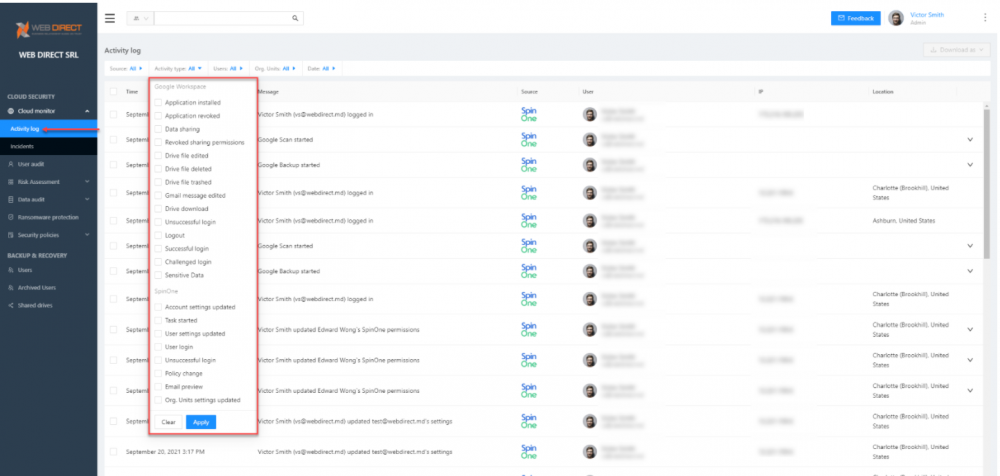
Easily view cloud activity with SpinOne
- Ransomware protection – Modern ransomware is increasingly targeting cloud SaaS environments. Attackers see the trend of moving business-critical data to cloud environments. As a result, ransomware is becoming “cloud-aware” to capitalize on this shift in data storage. It means that businesses must increasingly be aware of the risk of unsanctioned cloud applications integrated into the environment.
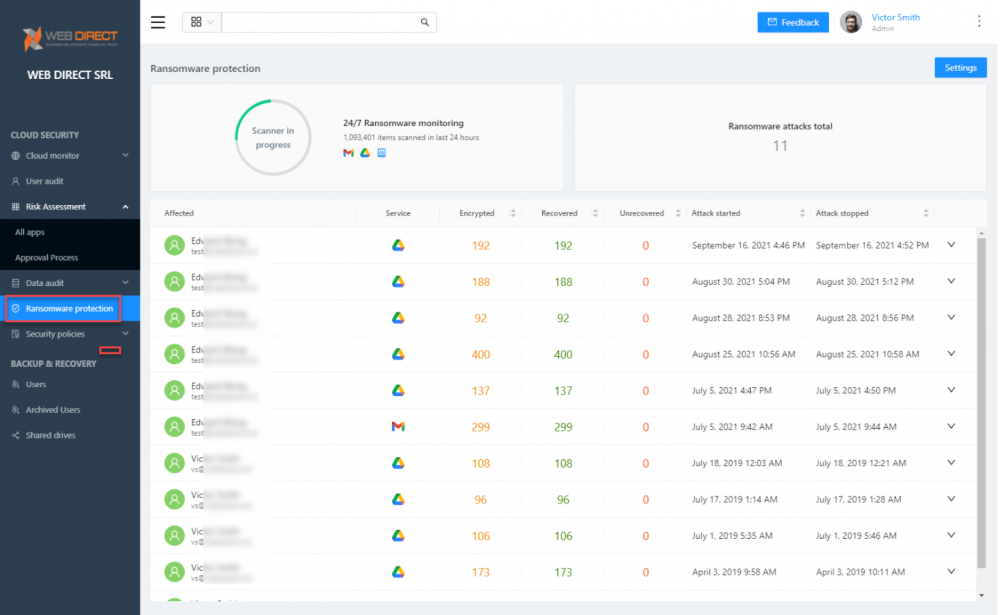
Remediate ransomware attacks with leading cybersecurity automation and AI
- Data Audit – In addition, SpinOne keeps up with your data and who it is shared with, providing tremendous visibility into data leak potential. Admins can take control of data that is shared and remediate data leaks.
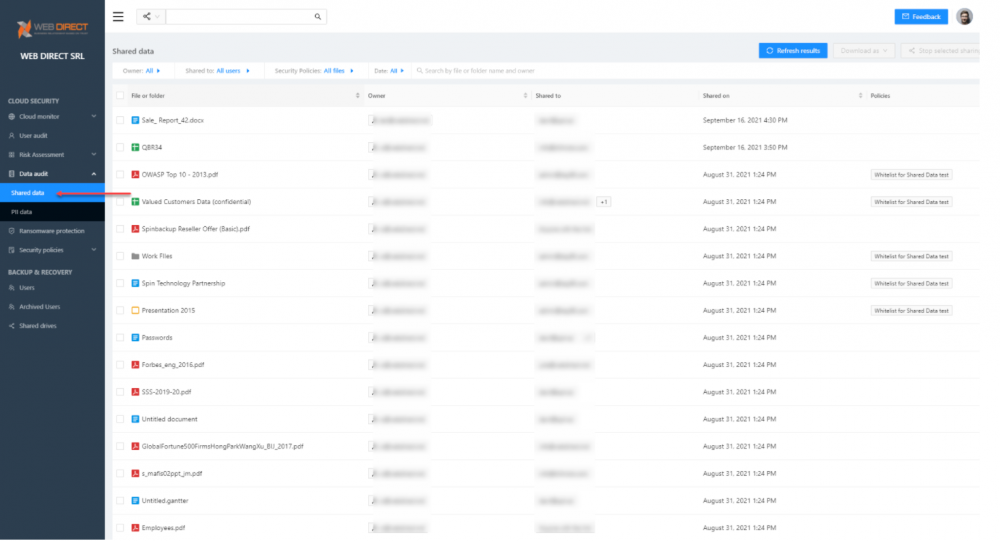
SpinOne provides visibility to data sharing
With these and many other protections provided by SpinOne, businesses can confidently transition to cloud SaaS environments with the cybersecurity posture needed to combat current and future data threats.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


