Mastering SSPM (SaaS Security Posture Management) for Insider Threat Prevention: A Comprehensive Guide

- Understanding Insider Threats
- The Role of SSPM in Insider Threat Prevention
- SSPM and Cloud misconfigurations
- Shadow IT detection with SaaS Security Posture management
- Correcting sharing settings with SSPM
- Detecting abnormal behavior of data and Users
- Connecting SSPM to SIEM
- Preventing Insider Threats with SpinSPM
- FAQ
Most of the cybersecurity incidents are caused by human errors or other types of insider threats. In this article, we will discuss how IT security teams can prevent insider threats using SaaS Security Posture Management (SSPM).
Understanding Insider Threats
The common perception of a cyber incident is a hacker’s attack on the organization’s IT system. However, the majority of security events are caused by employees, former employees, or contractors.
Insider threats are cybersecurity risks that come from within the organization and are usually associated with human activities.
The types of insider threats:
Human errors
Human error is the most common type of insider threat. Humans make errors all the time. However, some of these errors can have ripple effects on the organization. One example of human error is cloud misconfigurations that create an entry point for hacker attacks on the cloud.
Malicious intent
Some employees and former employees can attack their companies on purpose. Their goal is to gain profit or take revenge on the organization. They can participate in espionage, carry out an attack, or become a middle person.
Compromised credentials
Hackers are constantly looking for ways to obtain the credentials of other people and gain access to corporate IT systems. For example, they use password spraying. In this technique, a program tries one or several popular passwords (like “12345”) against many accounts and see if there’s a match.
Insider threats can cause data loss, data leaks, or cyber-attacks.
The Role of SSPM in Insider Threat Prevention
SaaS Security Posture Management is a type of solution that helps IT teams detect and neutralize insider threats. SSPM works with SaaS environments, for example, Google Workspace, or Microsoft 365.
Corporate cloud office suites can have hundreds and even thousands of users each having hundreds of documents. On top of that, they have shared drives for better team cooperation. Keeping track of such large data sets is impossible for many IT security teams that can suffer from skill or talent gaps.
Configuring such environments to comply with existing laws and regulations and meet the unique security needs of an organization is yet another challenge that IT security teams face.
SSPMs provide a bird’s eye view of the whole system finding and highlighting the possible insider threats to the organizations. SSPM can identify and help you control the following threats to your organization:
- Cloud misconfigurations
- Shadow IT
- Incorrect sharing
- Abnormal data behavior
- Abnormal user behavior
SSPM and Cloud misconfigurations
Cloud misconfigurations are types of human errors with the most rippling effects on organizations. It is an Admin’s mistake and it can influence the whole cloud office environment. Misconfigurations can enlarge the attack surface for hackers. They can also lead to violations of laws and regulations.
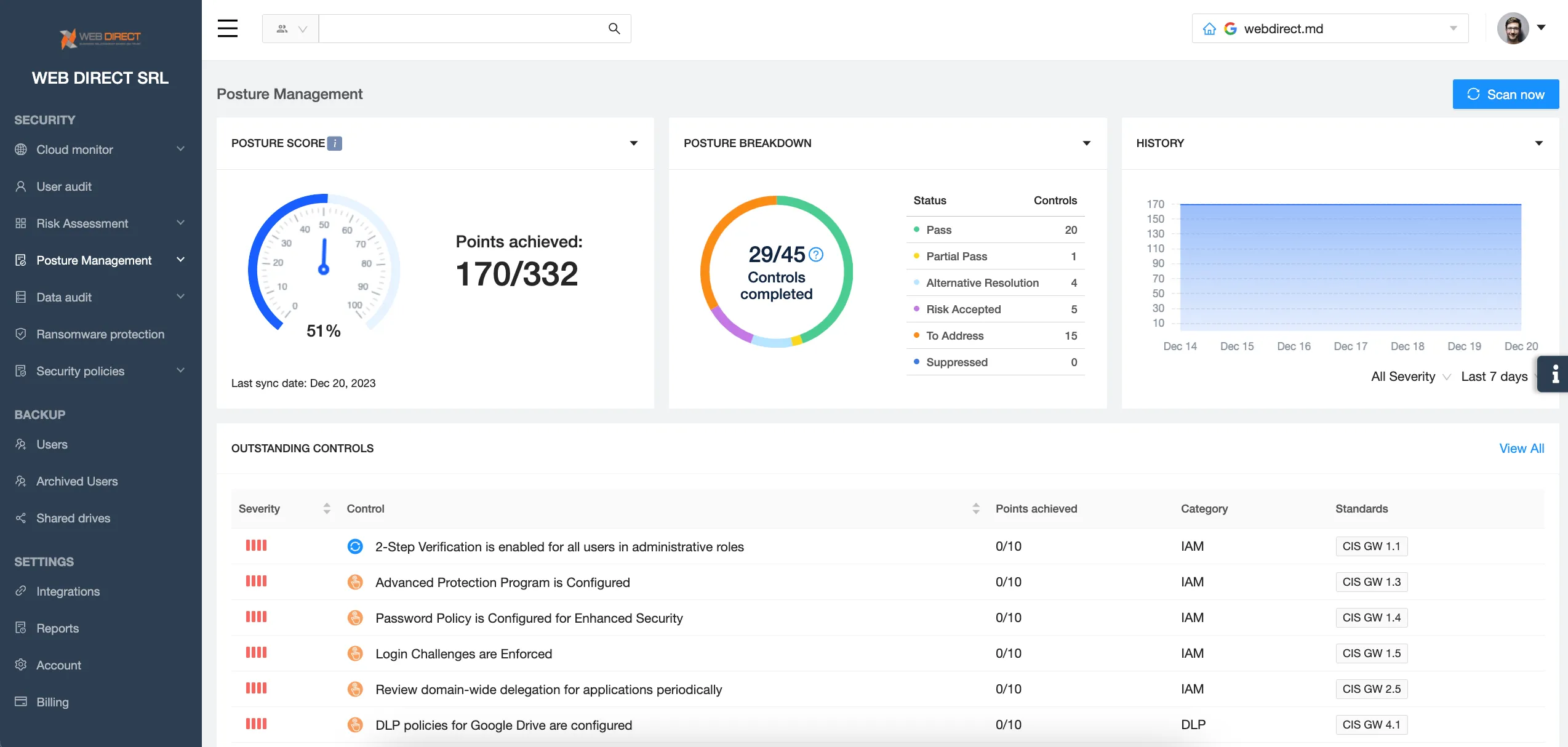
SSPMs detect the misconfigurations in the cloud. They can also identify the urgency and severity of a misconfiguration and arrange them respectively. This enables IT security specialists to make decisions based on priority and need.
You can set up SSPM to meet certain compliance requirements. For example, businesses wanting to work in the European Union would want to know if their IT environment is GDPR compliant.
Shadow IT detection with SaaS Security Posture management
Shadow IT can be attributed to insider threats because Shadow IT emerges due to human error or disregard for rules. In most cases, employees use Shadow IT due to the lack of knowledge. Less often, they know about the corporate security rules and choose to break them. Furthermore, some IT security professionals use unauthorized applications even though they know the risks of these apps.
Shadow IT in the cloud includes an application or browser extension that has OAuth access to your corporate cloud environment. Employees use their working accounts to sign up for these applications. Meanwhile, the IT security department does not know anything about such use.
SaaS Security Posture Management tools detect applications and browser extensions that have access to your IT environment. It can show how many users are currently using a certain application. Another important SSPM feature is a risk assessment of applications. Companies that have dozens of departments and hundreds of employees can have thousands of applications. Investigating and evaluating each app can take months. Instead, SSPM can do it within seconds.
Apart from detection and risk assessment, SSPMs provide control functions to Admins who use them to ban certain applications. Some tools can even enable Admins to create allow and block lists using one or several criteria (e.g., region, app score, etc). This can automate the app control.
Correcting sharing settings with SSPM
Users share files and folders all the time. The key goal is to collaborate on the data with their coworkers. However, incorrect sharing can cause data leaks if unauthorized people within or outside the organization gain access to such a file or folder.
With thousands of files across the organization, it’s very difficult to detect and fix the incorrect sharing settings, especially because they are located on the users’ drives. SaaS Security Posture Management tools provide a bird’s eye view of all the shared files.
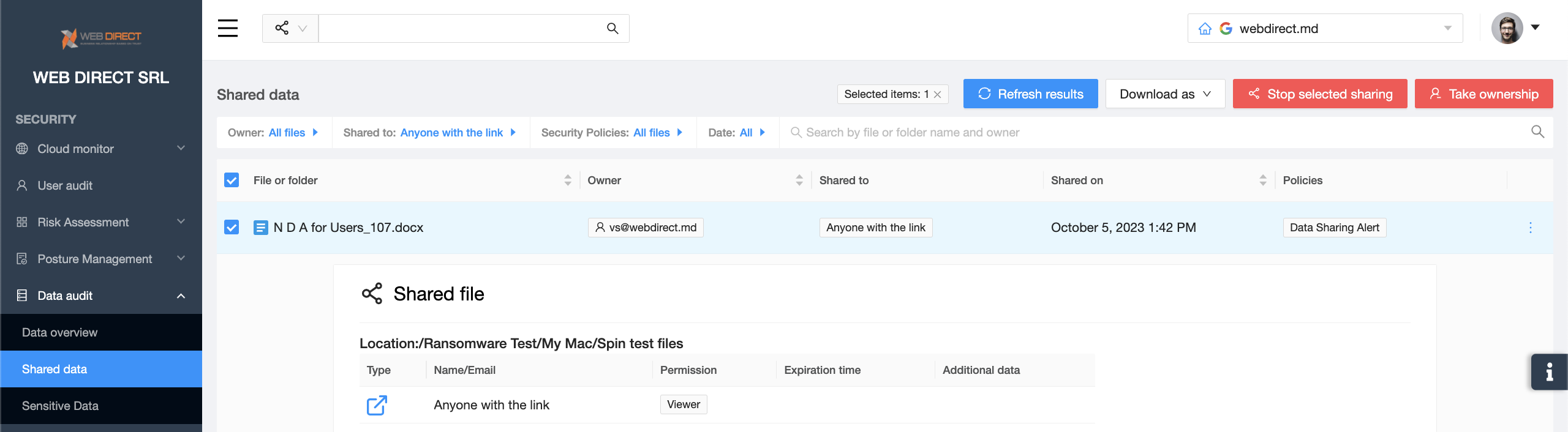
Admins can filter them by sharing settings (e.g., public, shared outside the organization, etc.) and then revoke access in the SSPM. The tool also enables them to take ownership of the document if it’s deemed particularly critical for the organization.
Finally, SSPM has security policies that enable Admins to control sharing. For example, it can automatically notify Admins or correct sharing.
Detecting abnormal behavior of data and Users
Abnormal data or user behavior might be a sign of insider threats. For example, a local download of Google Drive can signify that the account has been compromised and a hacker has taken over it. Hackers would often make a mass data download to sell it on the Dark Web. Similarly, an employee with malicious intentions can do the same.
Mass edits or mass deletions can also be a sign of an insider threat. For example, a user can “revenge on the organization” by deleting the business-critical data.
Abnormal user behavior usually occurs when the account is hijacked. For example, a user logs in outside business hours or outside the expected region.
Needless to say, IT departments do not have enough human resources to follow all these incidents online. Unfortunately, they often remain unspotted until a major cyber incident occurs.
SSPMs on the other hand can warn the Admins about suspicious behaviour of a user or data so that they can make a timely intervention.
Connecting SSPM to SIEM
SIEMs are large environments that use AI and machine learning to analyze enormous datasets from different sources. Connecting your SSPM and other security tools to SIEM can help you detect the insider threats that a human eye would otherwise miss.
AI is capable of analyzing user behavior across multiple applications, identifying new patterns, and predicting insider threats. However, even without SIEM, SSPM remains a powerful tool to automate monitoring and response to insider threats in your organization.
Preventing Insider Threats with SpinSPM
SpinSPM is a modern SaaS Security Posture Management tool for Google Workspace and Microsoft 365. In The Forrester Wave(™): SaaS Security Posture Management, Q4 2023, it was named a Strong Performer, only a year after its release.
SpinSPM has all the necessary functionality to battle insider threats:
- Detection and evaluation of cloud misconfigurations
- Detection and risk assessment of SaaS applications and browser extensions
- Access revoke, blocklisting, and allow listing for SaaS apps and browser extensions
- Control over incorrect sharing settings with access revoke and file takeover
- Data and User behavior analysis and detection of abnormal patterns
- Connection to SIEM and data feeding
FAQ
What steps are involved in implementing SSPM for insider threat prevention?
Implementing effective SSPM for insider threat prevention requires integrating a multifaceted approach. The main steps on this way involve but are not limited to:
- Establishing a Policy that outlines acceptable use, monitoring guidelines, and employee reporting procedures and ensures a common understanding of the root causes and consequences of insider risks.
- Identification and detection of potential insider threats through behavior analysis and anomaly detection
- Ensuring the security of sensitive data through encryption, access controls, and data loss prevention technologies.
- Applying Data Loss Prevention (DLP) tools to monitor, detect, and prevent unauthorized access to sensitive data.
- Educating employees about the significance of insider risks, security best practices, and the importance of promptly reporting unusual activities.
- Developing and implementing access policies to monitor employee access to critical data and systems.
- Establishing an incident response plan to respond to insider threats and mitigate potential damage.
What should organizations consider when choosing the right SSPM solution for their needs?
When choosing the right SSPM solution pay attention to the following:
Functionality. Define the functionality that best fits the needs of your business and focus on a solution that provides all the necessary features rather than buying several siloed tools.
Integrations. Outline your existing tools and solutions and search for an SSPM that integrates with as many of them as possible.
Monitoring & Incident Reporting. Focus on solutions that offer 24/7 monitoring and reporting the risky applications. Ask the sellers how many applications their SSPM detects.
Application Assessment Criteria and Scoring. Focus on SSPM that use several criteria and a complicated scoring system to evaluate risk assessment and a complicated scoring system, e.g.
Blocklisting & Allowlisting. Allowlist/blocklist risky applications or browser extensions to prevent unauthorized access to your most critical data.
Security Policies. Confirm that an SSPM enables you to configure a security policy that doesn’t allow users to set up applications based on certain criteria (e.g., risk score or scope of permissions).
How can SSPM tools proactively prevent insider threats?
Software-as-a-service (SaaS) security posture management (SSPM) is a category of automated security solutions designed to monitor and address security risks within SaaS applications. SSPM tools like SpinOne implement various measures to detect, monitor, and mitigate potential insider threats and allow to:
- gain visibility of all SaaS apps and extensions and understand who has access to these apps.
- set thresholds and get customizable notifications on abnormal login, data downloads, or transfers by your users to take timely action;
- allowlist/blocklist risky applications or browser extensions for everyone or specific organizational units to prevent unauthorized access to your most critical data;
- Generate data audit reports and export the audit reports as needed
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
What You Need to Know About AT&T’s Data Breach and How t...
Arguably, it is one of the worst breaches that has happened recently. AT&T disclosed in...
Lessons from the Twilio Breach: Securing SaaS Applications Against ...
Another recent security breach has made organizations think yet again about SaaS apps they may...
Unpacking the CrowdStrike Outage: Causes, Impacts, and Protecting Y...
A major global IT outage occurred on Friday, July 19, 2024, causing widespread disruptions across...


