How to Prevent Ransomware Attacks in 2023: 7 Ransomware Prevention Tips
Ransomware is a significant threat to organizations worldwide. Hackers are using ransomware to infect a company’s digital environments, steal data, and encrypt critical data. Moreover, new techniques and dark web activities have made ransomware accessible to threat actors everywhere and even more sinister. With the proliferation of ransomware threats, businesses everywhere need to bolster their cybersecurity posture to protect their critical data. Let’s look at ransomware prevention tips that can help prevent ransomware attacks.
Why ransomware is such a huge problem for organizations
What kind of problem is ransomware today? Cybersecurity Ventures estimates that costs from cybercrime activities, including ransomware, increasing 15 percent per year over the next five years. By 2025, the costs will total $10.5 trillion. In 2020 alone, there were around 300 million ransomware attacks, and about 3/4 of these were successful.
It is worth noting why the risk of ransomware has exploded as it helps prioritize protecting critical cloud data and the need to do so. Why has the threat of ransomware escalated to the point we see today? It is mainly due to a couple of reasons. Please consider the below:
- Ransomware-as-a-Service (RaaS)
- Initial Access Brokers (IABs)
Ransomware-as-a-Service (RaaS)
If one development has proliferated ransomware attacks, it is the appearance of Ransomware-as-a-Services (RaaS). Ransomware groups looking to provide even more revenue streams for their activities have created the concept of Ransomware-as-a-Service.
RaaS provides attackers of all skill levels access to a readily available ransomware solution ready to attack an organization. Ransomware-as-a-Service delivers a solution akin to Software-as-a-Service solutions, such as Google Workspace and Microsoft 365. However, with Google Workspace and Microsoft 365, the underlying infrastructure is abstracted from the consumer. As a result, they don’t worry about which servers and network resources are required to run the SaaS services.
Similarly, RaaS abstracts the underlying complexities of the ransomware solution from the threat actor consuming them. Consider how RaaS has increased ransomware attacks. Even relatively novice attackers can now access robust and cutting-edge ransomware solutions with the latest features.
They no longer have to develop and provision the underlying infrastructure required for launching the attack, exfiltrating data, encrypting data, and collecting the ransom payment. Instead, all of this is taken care of for them. Unfortunately, it brings ransomware to the masses and is bad news for organizations already fatigued with the myriad of other cybersecurity and compliance challenges.
In return, the ransomware groups running the RaaS solution take a percentage of the ransom payment collected from a successful attack, further helping to fund other nefarious activities.
Initial Access Broker (IABs)
Another development on the dark web proliferating ransomware attacks is the Initial Access Broker (IAB). Part of the challenge facing cybercriminals is gaining initial access to an environment to carry out an attack. A sinister development on the dark web is the evolution of a service called Initial Access Brokers (IABs)
These are individuals or groups that steal, leak or harvest the credentials of an organization’s users and sell this access on the dark web. Generally, the higher the privileges of the stolen credentials and the larger the organization, the more the IAB stands to make from the sale. Ransomware-as-a-service and Initial Access Brokers provide a literal ala carte offering on the dark web, allowing attackers to have everything they need to easily and quickly launch an attack, including the required credentials for the initial compromise of the environment.
7 ransomware prevention tips to prevent potential ransomware attacks
What tips can organizations follow to help prevent potential ransomware attacks? Note the following ransomware prevention tips and how they can help to bolster your cybersecurity posture against attack.
- Back up your data
- Secure remote access solutions
- Use two-factor authentication
- Patch critical systems regularly
- Limit third-party cloud SaaS apps
- Conduct cybersecurity training
- Leverage proactive ransomware protection
1. Back up your data
Almost 50% of companies are unable to recover data after a ransomware attack. Paying ransom doesn’t guarantee the full recovery either. Every company needs data backup to be able to recover independently from a ransomware attack. There are many third-party backup tools that make data snapshots on a regular basis and store them in separate cloud storage.
2. Secure remote access solutions
One of the most common entry points for ransomware attacks is remote access solutions. For example, the significant ransomware attack on Colonial Pipeline involved compromised VPN credentials. Time and again, attacks compromise insecure or vulnerable remote access technologies.
Tip: Ensure remote access solutions are secured with two-factor authentication and strong passwords
- Two-factor authentication significantly improves the cybersecurity posture of remote access and other systems
- Ensure remote access solutions are deployed according to vendor best practices
- Keep these patched
3. Use two-factor authentication
Leaked credentials are often used in launching ransomware attacks. Initial Access Brokers (IABs) use compromised passwords to provide ransomware groups with the access needed to carry out an attack. The additional authentication factor tremendously increases security. In addition, even if an attacker has a compromised password, they still do not have all the elements needed to authenticate successfully.
Tip: Ensure all remote access solutions and Internet-facing applications are secured with two-factor authentication
- Generating one-time passwords with an authenticator app is more secure than receiving these through text
- Educate users about the dangers of “MFA fatigue,” where an attacker sends many push requests to an end-user in hopes a user will mistakenly grant access.
4. Patch critical systems regularly
Patching critical systems is a necessary part of a strong cybersecurity posture. Unfortunately, attackers are more commonly targeting known vulnerabilities and zero-day exploits. By regularly patching essential systems with the latest security and other updates, organizations help to close off as many of these holes as possible before an attacker can exploit them.
Tip: Have a regular patch schedule where updates are deployed to critical business systems, especially those that are Internet-facing
- Test and regularly implement the latest security patches
- Take advantage of cloud-based solutions that are “evergreen” and continuously updated to help alleviate the maintenance burden
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
5. Limit third-party cloud SaaS applications
Many may not consider their cloud SaaS environments when thinking about protecting themselves from the threat of ransomware. However, cloud-based ransomware is evolving and becoming more prevalent as attackers follow the trend of organizations shifting critical services and data to cloud SaaS environments.
Third-party cloud SaaS apps allow extending cloud SaaS functionality. However, without proper risk assessments and guardrails, users can quickly become involved in Shadow IT by installing unsanctioned apps or malicious or “leaky” third-party applications. Attackers use phishing attacks to coax users into installing malicious third-party apps that may contain ransomware.
Organizations need to control which apps can be installed and perform rigorous risk assessments of those third-party apps they choose to allow in their cloud SaaS environments.
Tip: Enforce controls over which third-party applications users can install in the cloud SaaS environment. Use automated risk assessment solutions to assess third-party app risk properly.
- Create allow lists and block lists of third-party cloud SaaS apps
- Use cybersecurity automation for handling risk assessments using artificial intelligence and machine learning
6. Conduct cybersecurity training
Social engineering is the most widespread attack vector for ransomware. Training your employees to spot phishing emails has proven to be an efficient way to prevent ransomware attacks. The training should comprise two parts:
- theoretical when you explain the basics
- practical when you send training phishing emails to your employees
There are many companies that provide cybersecurity training. Their main advantage is that you do not need to spend time and resources on compiling and conducting a training course or figuring out how to send fake phishing emails. The service provider will do it for you.
7. Leverage proactive ransomware protection
Look for cybersecurity solutions that provide proactive ransomware protection. Next-generation solutions can use artificial intelligence (AI) and machine learning (ML) to quickly and proactively stop a ransomware attack. With the sheer span and depth of cloud SaaS services and data, cloud SaaS environments need to leverage proactive solutions to help contain and stop ransomware attacks from infecting critical data.
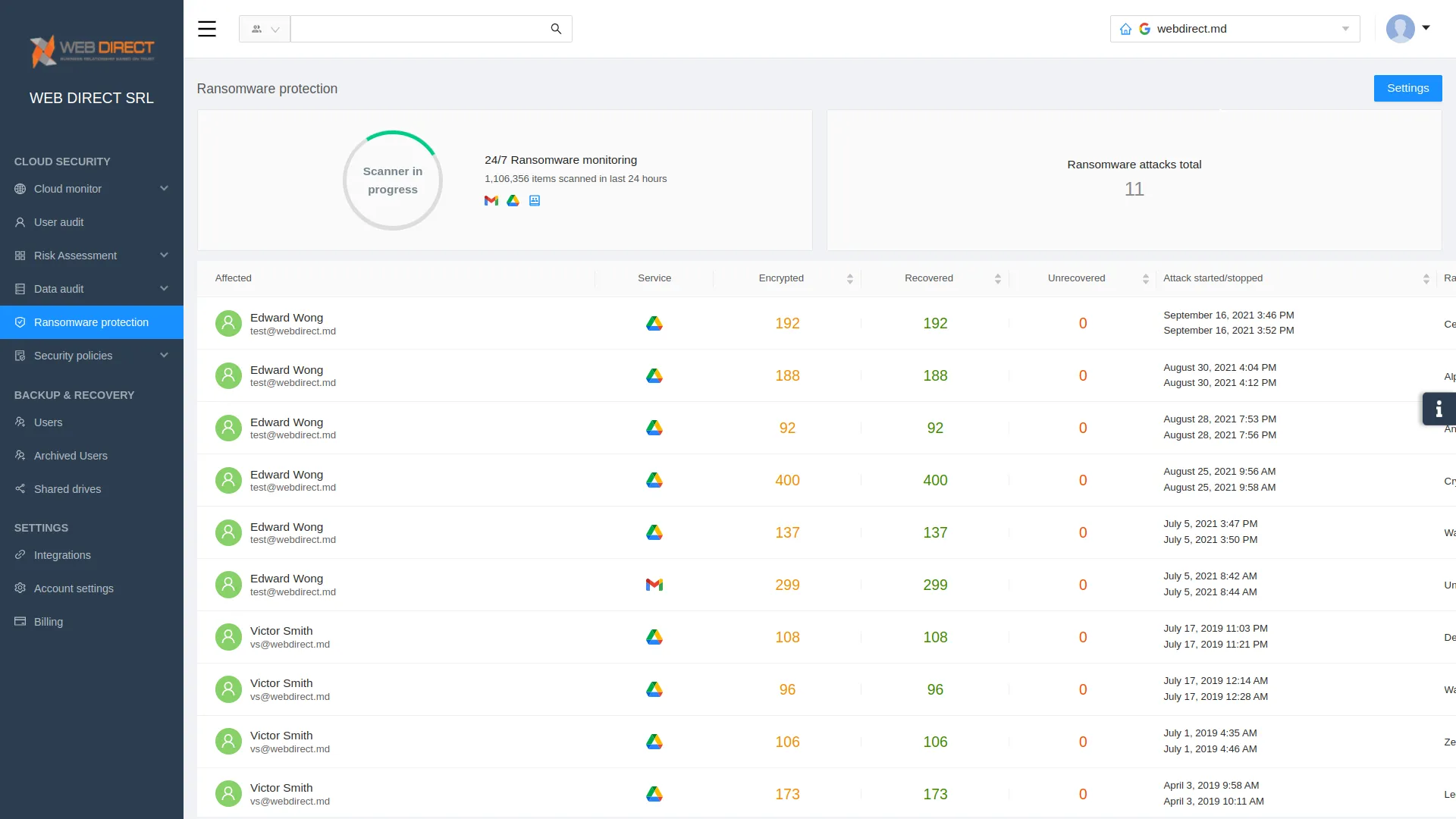
A proactive approach also helps curtail double extortion’s effects, where malicious processes first leak data from the environment before encrypting it.
Tip: Use proactive next-generation ransomware protection leveraging technologies like AI and ML to fight ransomware
- Backups are not enough to protect against double extortion
- Proactive protection is essential to help prevent the effects of ransomware
Proactive ransomware protection with SpinOne
SpinOne enables organizations to have the technical capabilities and features needed to protect and secure cloud SaaS data to meet the challenge of ransomware. With SpinOne, you get:
- Proactive ransomware protection
- Cybersecurity automation
- Cloud-to-cloud backups
- Third-party app control
- Automated cybersecurity risk assessments for cloud SaaS apps
- Visibility and monitoring of cloud SaaS activities, data, and security
If you would like to speak with a Spin Solution Engineer to discuss how SpinOne can help you meet your ransomware protection challenges, click here to book a demo: Request a Demo of SpinOne
FAQs
Can traditional antivirus solutions effectively prevent ransomware?
No. Traditional antivirus solutions detect ransomware based on historical data. Unfortunately, new ransomware strains appear regularly, and traditional antivirus tools can’t keep up with them.
How does two-factor authentication (2FA) mitigate the risk of ransomware?
Many hackers steal credentials to access the victim’s IT environment. Two-factor authentication provides an extra layer of security disabling the hackers from accessing the system if they do not have another device to access the environment.
How can businesses protect their cloud and SaaS environments from ransomware?
Businesses need proactive ransomware protection that is based on AI that analyzes the patterns of data behavior and detects abnormal elements.
How can SpinAI’s ransomware tool enhance an organization’s defense against ransomware?
SpinAI ransomware protection uses AI to analyze data behavior in the cloud and detect anomalies. It stops the attack upon detection and recovers the encrypted files. Because it can detect and stop the attack within minutes after its beginning, the ransomware doesn’t have enough time to decrypt large amounts of data. As a result, the recovery time with the SpinAI ransomware protection tool is decreased by 99%.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...



