SaaS Security: Best Practices to Keep User Data Safe
With many businesses relying on SaaS environments, SaaS security has become critical. Learn the best practices of SaaS security that will help you keep your data safe from multiple risks.
Understanding SaaS Security
SaaS environments like Google Workspace and Microsoft 365 have become widespread in companies across the globe. They have many advantages for businesses like computing power, decreased costs, scalability, and security.
However, these environments aren’t entirely secure as part of the responsibility for ensuring security lies on the organization. Let’s take a closer look at SaaS security risks.
SaaS security challenges
There are several challenges to maintaining SaaS security for a business. SaaS environments lack defined security perimeter, visibility, and thus control over what’s happening within the system.
Let’s start with the security perimeter. The SaaS environment is “porous.” Users can log in to it from virtually any spot on the planet provided there’s Internet access. Administrators and IT security specialists cannot be sure about the identity of the person who has just logged in. It might be your loyal employee of 5 years, a hacker who has just managed to steal their credentials, or both of them at the same time.
Not only the external perimeter is porous, but the system internally has very few boundaries. The file-sharing feature has become such a powerful productivity boost for most companies. However, it also undermined security and caused multiple data leaks.
Furthermore, the ability to use your credentials to access other SaaS applications provides an additional threat to your SaaS security. The access and in some cases the ability to edit your data that these apps have has high chances of data theft or data corruption.
The OAuth access also enables cloud ransomware to penetrate a well-defended cloud environment and infect it.
The IT security team has little visibility into all these cases and even less control, at least with the given functionality of Microsoft 365 and Google Workspace.
SaaS security risks
Many of the above-mentioned challenges open up opportunities for various cybersecurity incidents that result in data loss or data leaks. There are several risks associated with SaaS environments.
- Insider threats
- Cloud ransomware
- Shadow IT
- Misconfigurations
- Non-compliance
Best Practices for SaaS Security
In this chapter, we discuss how to battle SaaS security risks, overcome challenges, and improve your SaaS security posture.
Data access control
Google Workspace and Microsoft 365 have good tools to fend off the perimeter of the environment. And we strongly recommend using them. These tools include multifactor authentication, strong passwords, and regular password changes. They can prevent account hijacks.
However, when it comes to internal access, things aren’t as good. Some subscription plans have DLP policies that enable Admins to control file sharing. However, once again, they aren’t enough.
We suggest acquiring third-party tools that can enable Admins to get full visibility into the sharing settings of all the files in the system. Such tools also have the functionality to change sharing settings manually right on the spot or even take ownership. Furthermore, they offer more complex data protection policies to automate sharing control and reduce the IT team’s workload.
Data backup and disaster recovery strategies
Regular backup of your SaaS data can prevent data loss as a result of human error or malicious activities of your users. Neither Google Workspace nor Microsoft 365 have inbuilt data backup. Even though some companies use them to back up their on-prem data.
To avoid data loss, we suggest using third-party cloud-to-cloud backup tools and making snapshots of your data at least once a day.
Shadow IT control
Most SaaS applications with unauthorized access to your environment remain invisible to your SaaS security team. That’s why they’re called Shadow IT.
Both Microsoft 365 and Google Workspace have limited functionality that enables the Administrators to detect applications with OAuth access to these environments. The MSO 365 app control even has risk assessment.
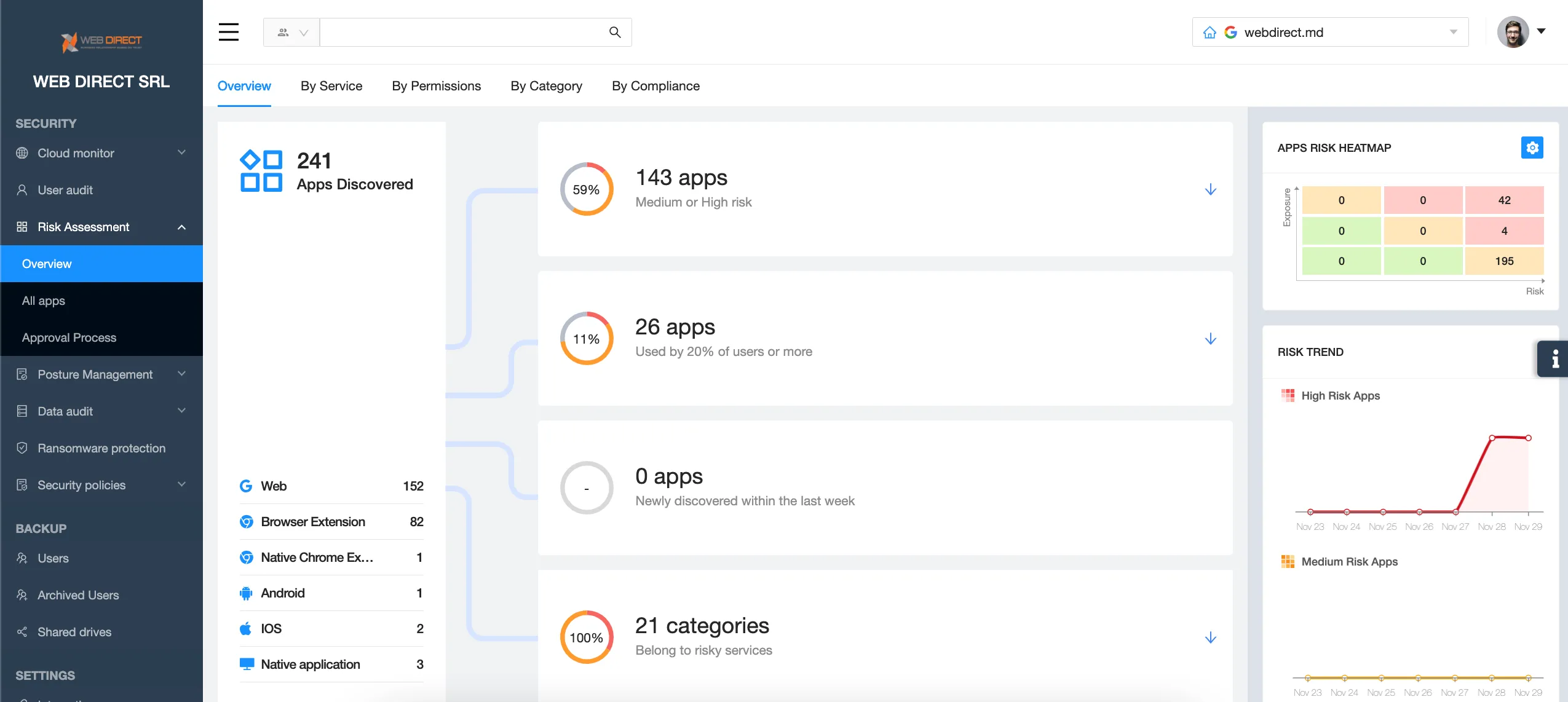
However, they lack several important features that enable Admins to take full control of the SaaS applications. These are the ability to revoke the app’s access to your environment and the ability to create black lists and white lists to control apps automatically.
These critical features can substantially reduce the workload of the SaaS security team and enable them to monitor and control Shadow IT more efficiently.
We suggest using third-party tools to ensure full control over your applications and browser extensions.
Protection against ransomware attacks
Ransomware attacks pose a real and serious threat to your SaaS environment. In fact, ransomware attack has been rampaging over the past several years. Every year we see some new strains and legacy tools using historical pattern recognition to detect ransomware and decrypt files prove to be inefficient.
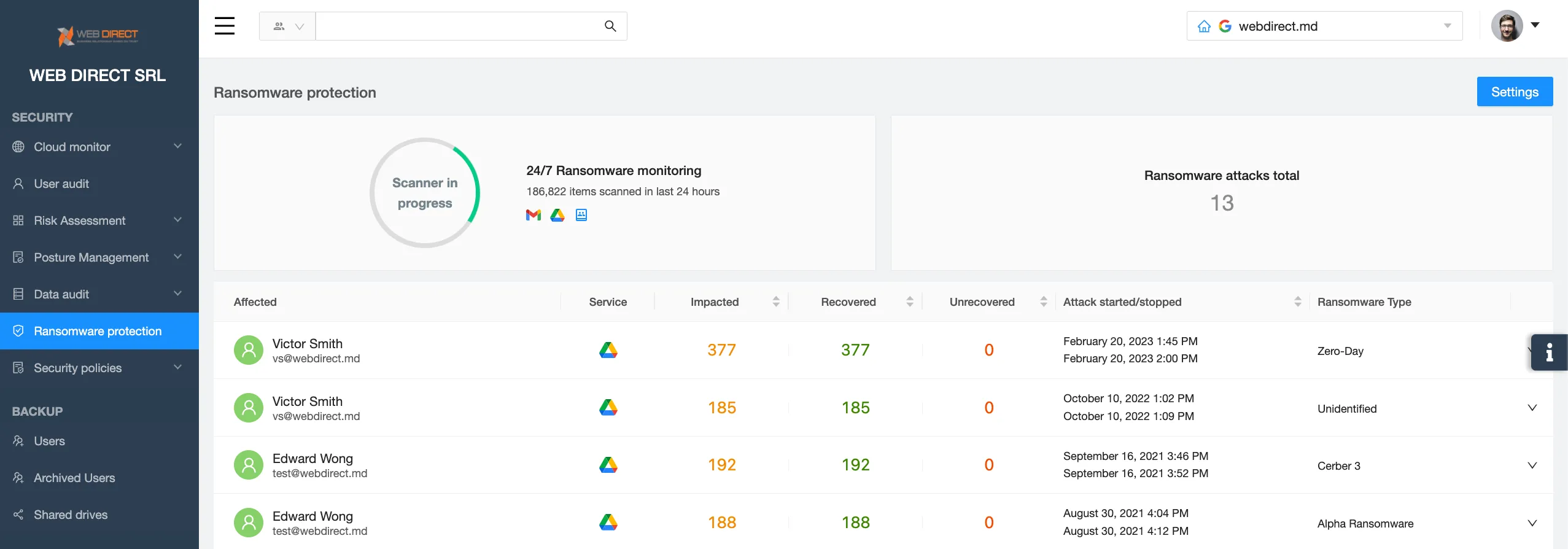
MSO 365 and GW have strong email filters to catch risky links and protect humans from social engineering attacks. However, they are not enough. In practice, the emails sent by hackers hit the inbox and infect the environments. Organizations are forced to pay the ransom. They experience significant downtime, reputational losses, financial losses, and legal implications.
The backup tools aren’t efficient as they recover data slowly and extend the downtime severely. The decryption keys provided by hackers often fail. And about half of the victims of attacks get successfully hit with ransomware for the second time.
To prevent ransomware attacks and data loss, we suggest using third-party ransomware protection tools that use AI to detect and stop this type of malware almost immediately.
User education and security awareness
Your user is a gate to your system and you can either enforce them with cyber awareness or leave them for hackers to freely exploit in a social engineering attack.
There are many companies that have ready-made courses for cybersecurity awareness that also include practical training. For example, they send fake phishing emails to check the ability of your employees to detect social engineering attacks and slap them on the hand in case they don’t.
Misconfiguration control
Misconfigurations are becoming the number one reason for cyber incidents and non-compliance in SaaS environments.
Any GW or MSO 365 Administrator knows that the Admin centers of these apps are pretty close to a rocket ship control room. With the overwhelming talent gap, skill gap, constant stress, and work overload, it’s hard to miss a configuration or two.
Both GW and MSO 365 do not have misconfiguration detection. That’s why getting a third-party application that will enable you to track them is key to successfully controlling the misconfigurations.
SaaS security with SpinOne
SpinOne is a SaaS security platform that is able to address all the above challenges and risks. Furthermore, it provides a single pane of glass to control applications, ransomware, access, and misconfigurations. It also backs up data up to three times a day.
FAQs
Why is data backup crucial for SaaS companies?
The SaaS-based data may be easily deleted either intentionally or unintentionally by insiders, encrypted by ransomware, or otherwise corrupted by malicious actors and cyberattacks. To ensure data availability and integrity in such scenarios, data backups are crucial. However, most SaaS providers do not offer data backup as they work based on the shared responsibility model when SaaS is responsible for their networks, OS, and applications. In contrast, data housed in the SaaS lies on customers’ shoulders. This means that ensuring data backups is beyond SaaS providers’ responsibility. Therefore, the users must take care of third-party backup services to ensure the integrity and availability of their SaaS-based data. Consider using Spinbackup to make the process easier for you.
How do strong passwords and authentication protocols protect data?
Strong passwords and authentication protocols enhance data protection by creating robust barriers against unauthorized access.
Strong passwords involve a long, hard-to-guess combination of alphanumeric characters and symbols – example: !H89mT85MB – resisting easy guessing or hacking attempts.
Strong authentication techniques usually combine two independent factors to confirm someone’s identity and access. For instance, multi-factor authentication (MFA) adds an extra layer of security by requiring users to verify their identity through either something you know (PIN, passwords), something you possess (smartphone), something you are (fingerprints, faceprints), etc. Compromising one element doesn’t affect the other, ensuring the overall security of systems. Each element is unique and never reused, making it extremely difficult for unauthorized parties to steal or compromise.
Together, strong passwords and authentication protocols fortify access controls, mitigating the potential impact of breaches and ensuring that only authorized users can access critical information.
What are SaaS governance best practices?
At its core, SaaS governance seeks to centralize control over SaaS usage while enabling businesses to make immediate knowledge-based decisions. The SaaS governance best practices encompass defining policies, processes, and guidelines to ensure that SaaS usage aligns with the organization’s objectives, improves operational effectiveness, and minimizes possible risks.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


