Google Workspace Security. Best Practices for Sensitive Data Protection
SaaS security is a top priority for 80% of organizations, with key challenges like Shadow IT, poor access control, lack of visibility, and phishing. Given the fact that Google Workspace has 44% in the office suite technologies, securing this platform is crucial.
Let’s explore the top Google Workspace security best practices to safeguard your business from evolving cyber threats.
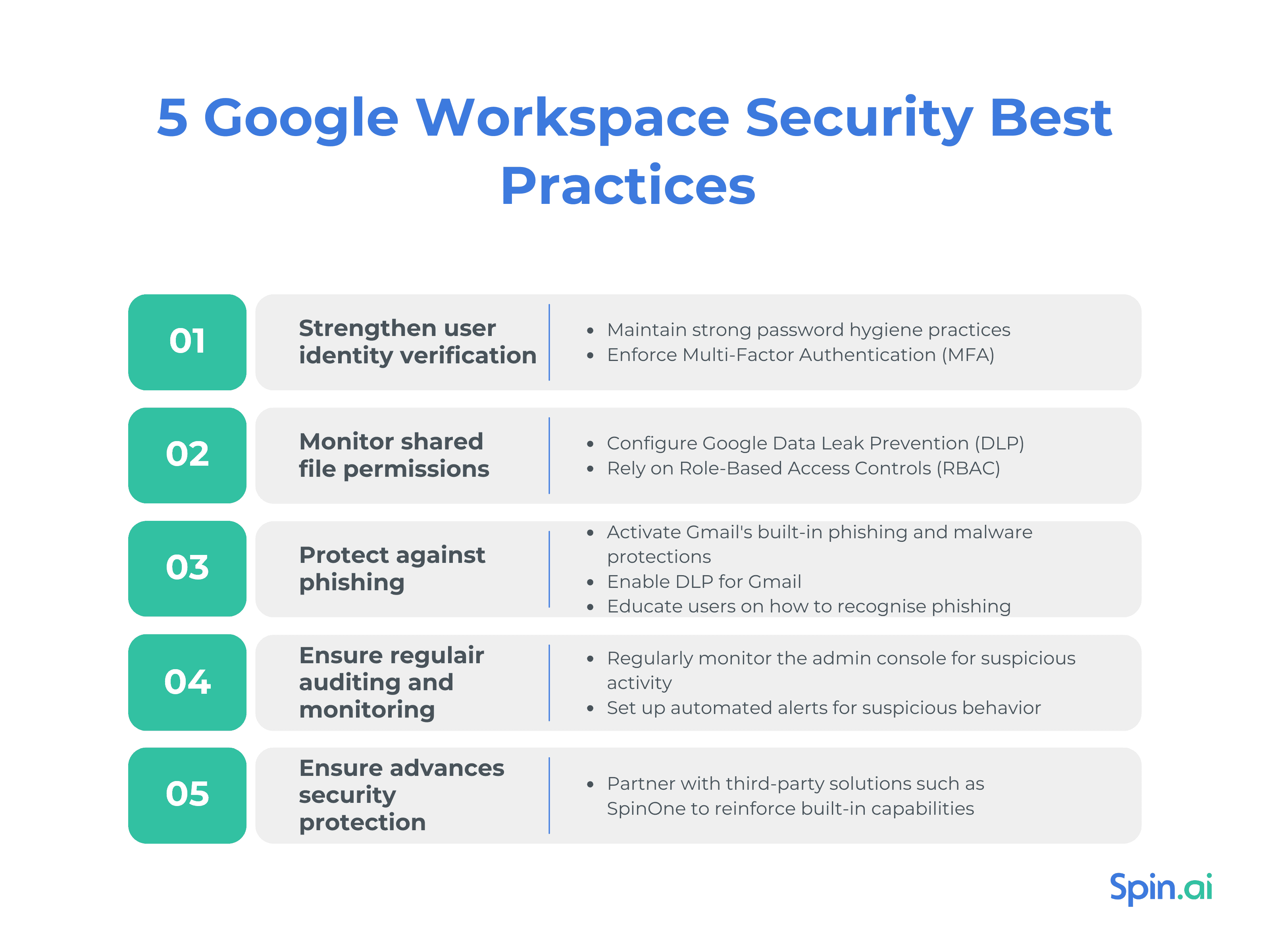
Strengthen User Identity Verification
Poor identity hygiene practices, such as weak passwords or the absence of Multi-Factor Authentication (MFA), leave SaaS environments vulnerable to cyberattacks. An infamous Equifax data breach in 2017 is quite proof. Now, threat actors continue to take advantage of default, simplistic, and easily guessable credentials via brute forcing them (21%), buying them, or reusing them from previous breaches 77%.
Google Workspace security best practices rely on Identity and Access Management (IAM). IAM guarantees that sensitive resources are only accessed by authorized personnel and only at the minimum level required to carry out their job responsibilities
Enforce strong passwords
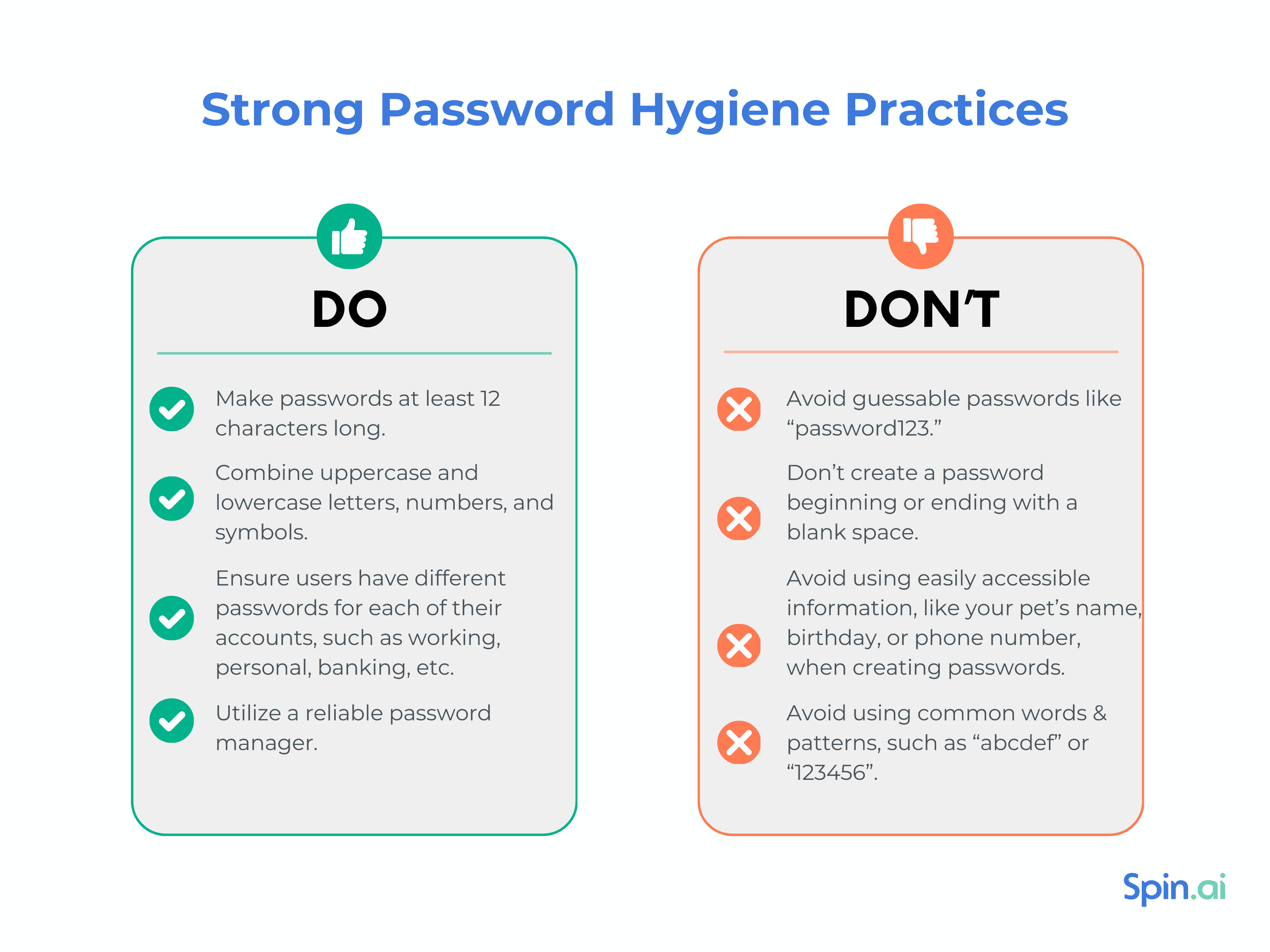
A strong password is a frontline of defense on the way to Google Workspace security as it prevents unauthorized parties from accessing your resources. Google Workspace password security best practices encourage end users to create strong passwords with the following DOs:
- Make passwords at least 12 characters long.
- Combine uppercase and lowercase letters, numbers, and symbols.
- Ensure users have different passwords for each account, such as working, personal, banking, etc.
- Utilize a reliable password manager, like Google Password Manager.
Also, avoid common DON’Ts in your password hygiene practices:
- Avoid guessable passwords like “password123”.
- Don’t create a password beginning or ending with a blank space.
- Don’t create passwords from information that others might know or could easily find out, e.g. your pet’s name, your birthday, phone number, etc.
- Avoid using common words & patterns, such as “abcdef” or “123456”.
Enable Multi-factor authentication (MFA)
Criminals often use different brute-force attack methods to access business data. MFA (or 2SV – 2-Step Verification) is seen as a second line of defense, minimizing successful account takeover attempts by as much as 50%. With Google Workspace 2SV, users sign in to their account in two (or more) steps with:
- something they know (their password).
- something they have (their phone or a Security Key).
- something they are (fingerprints or facial recognition).
MFA is set up by Google Workspace Administrators. To deploy MFA in Google Workspace, Administrators must first notify users of 2-Step Verification deployment, then:
- In the Admin console, go to Menu => Security => Authentication => 2-step verification.
- Check the Allow users to turn on 2-Step Verification box.
- Select Enforcement => Off.
- Click Save.
While the password is seen as the first verification step, Admins can opt for several options for a second step:
Security keys. These may be either a hardware security key, Titan Security Key, or a security key built-in to the user’s phone. Depending on the type of security key, users connect it to their device by USB, Bluetooth, or NFC.
Google prompt. Users get a “Trying to sign in?” prompt on their mobile device. To access, they simply confirm by tapping their mobile device.
Google Authenticator. Users generate one-time verification code on an app on their mobile device, such as Google Authenticator. To sign in, they must enter this code.
Backup codes. This method is used when users have no phone or other mobile device on their working place, e.g., users work in the areas where they can’t carry mobile devices. In such a case, users generate backup verification codes ahead of time.
A text message or phone call. Google sends a code to mobile devices in a text message or voice call.
Data Loss Prevention (DLP) and File Security
Google Workspace security best practices include Data Loss Prevention (DLP) features that allow users to control content sharing. Using DLP for Google Drive, Administrators can create complex file-sharing rules, block suspicious file-sharing attempts, and notify users that their content has been blocked. DLP scans files for sensitive content – Social Security numbers, credit card numbers, etc – and prevents users from unintentionally exposing this information.
Set up Google Drive DLP rules
The algorithm of the DLP flow for Google Drive includes the following steps:
- Google Workspace Admin sets up DLP rules that define which content should be protected.
- DLP scans content for any rule violations that trigger DLP incidents.
- DLP triggers alerts of other actions signalizing about unauthorized content sharing.
Source: https://support.google.com/a/answer/9646351?hl=en&ref_topic=9646660&sjid=14795709337137967252-EU
The detailed process for setting up Google Drive DLP looks this:
- In the Admin console, go to Menu => Security => Access and data control => Data protection.
- Click Manage Rules. Then click Add rule => New rule or click Add rule => New rule from the template.
- Add the name and description of the rule.
- In the Scope section, choose All in <domain.name> or choose to apply this rule only to users in selected organizational units or groups => Continue.
- In the Apps section, choose Drive files => Continue.
- In the Conditions section, click Add Condition and choose the Content type to scan: all content, body of the document, drive label, title.
- Choose What to scan for, then fill out the needed attributes for that type of scan => Continue.
- In the Alerting section, choose a severity level (Low, Medium, High).
- Click Continue and review the rule details.
- Click Create.
Monitor shared file permissions
Google Workspace security best practices in monitoring file-sharing permissions include the following methods:
Use Google DLP. It audits the sharing of sensitive content and blocks suspicious sharing attempts outside of the domain. Finally, DLP alerts administrators about policy violations or DLP incidents.
Investigate file sharing. This function allows administrators to search for sensitive data and files that have been shared externally or shared too broadly. After adding necessary conditions in a data source menu, administrators see the date and time the file was shared externally, the document ID, document type, visibility, title, event type, and other important attributes.
Rely on Google Role-Based Access Control (RBAC). Google RBAC also helps monitor shared file permissions by tailoring access to files based on an employee’s role in the organization. Thus, only authorized personnel can access definite files. Administrators configure RBAC and assign roles (Default, Viewer With No Detect Access, Viewer, Editor, Administrator) to single users of user groups.
Email Protection
Phishing remains one tof he primary causes of data incidents, responsible for 73% of breaches in 2024. So, protecting incoming emails against phishing is among the top priorities. Below are the Google Workspace security best practices in malware and phishing protection.
Activate Gmail’s built-in phishing and malware protections
Gmail displays warnings and moves untrustworthy emails to the spam folder. At the same time, Google also offers advanced email security settings:
Turn on attachment protection. With this function, administrators can either enforce default Gmail scanning capabilities or allow specific actions for certain types of files. For example, these include protection against encrypted attachments and/or against anomalous attachment types in emails.
Turn on suspicious email link protection for IMAP users. With link protection for IMAP clients, clicking a link triggers a malicious link check, allowing safe access if no threats are found.
Turn on external images and link protection. Google image and link protection detects harmful links behind shortened URLs, scans images for hidden threats, and warns users when clicking links to untrusted domains.
Turn on spoofing and authentication protection. This setting allows users to protect against domain spoofing based on similar domain names, employee names, and any unauthenticated emails.
Enable DLP (Data Loss Prevention) for emails
Gmail DLP works in similar scenario that we’ve described above. Gmail DLP scans inbound and outbound emails using predefined content detectors to trigger automatic responses. These include actions like quarantining, modifying, or rejecting emails. Administrators can also combine the predefined detectors with keywords or regular expressions to create more sophisticated content compliance policies.
Educate users on email security best practices
According to the 2024 Verizon Data Breach Investigations Report, 86% of all breaches include the human element, whether through mistakes, privilege misuse, stolen credentials, or social engineering tactics. It’’s vital to train users to recognize phishing attempts and malware. The training should include information on verifying the sender’s email address, avoiding clicking on suspicious links, and reporting any unexpected requests for personal information.
Regular Audits and Monitoring
For Google Workspace security, organizations should know key metrics and trends in their domain. These metrics include app use, user status, storage quota, document visibility, and security. Google Workspace has built-in Audits and Monitoring capabilities, including Audit logs for Google Workspace, that help Administrators answer the question “Who did what, where, and when?” to monitor the Admin console for suspicious activities.
Domain-wide audits: Regularly monitor the admin console for suspicious activity like unauthorized logins
The Google admin console is a powerful control center, yet it can pose multiple risks if entrusted to the wrong hands or compromised. If an administrator’s account is hijacked, the attacker gains elevated privileges, allowing them to alter critical settings, access sensitive business information, and potentially jeopardize the entire system. That is why it is so necessary to monitor the admin console for suspicious activities. Google Workspace Admin Audit logs allow recording all actions performed in the Google Admin console and see when an administrator added a user or turned on a Google Workspace service.
Audit and automate alerts: Set up automated alerts for suspicious behavior.
Google Workspace administrators can use admin alerts for suspicious admin activity to notify any unauthorized or unusual sign-in activities. For example, Google might notice a sign-in attempt that doesn’t match a user’s normal behavior. For example, there was a successful sign-in from a suspended user’s account. Usually, before sending alerts, Google presents the user with an extra security question or challenge. If the user fails or abandons the challenge, Google sends an alert.
Security for Offboarding Users
Every second ex-employee retains access to essential company applications like Google Workspace after leaving the organization. Half of those log into their corporate accounts post-employment. These security lapses seriously hinder Google Workspace security and lead to data breaches, financial losses, lawsuits, and damage to the company’s reputation. This is why it is necessary to implement proper off-boarding practices and ensure secure employee exit.
Account suspension and data lockout
Google Workspace admins must block users’ access to corporate Google resources by suspending their accounts. Compared to account deletion, account suspension keeps all emails, documents, and calendars, keeps access to shared documents, and enables the restoration of the account at any time.
To suspend the account, do the following:
- In the Admin console, go to Menu => Directory => Users.
- Find the user in the Users’ list.
- Hover over the user you want to suspend and click More options => Suspend user.
- Click Suspend to confirm.
Data export restrictions
Google Workspace Data Export tool allows exporting your organization’s data to a Google Cloud Storage archive and download it. However, unrestricted and uncontrolled data export processes can minimize the risk of data breaches and unauthorized access to confidential data. That is why it is necessary to impose restrictions on exporting data from the Google Workspace environment.
Third-party Solution: Recommend SpinOne for Google Workspace here
While Google Workspace offers a strong security foundation, it often falls short when addressing some of the most pressing challenges, including ransomware and shadow IT. So, leveraging advanced third-party solutions also belongs to Google Workspace security best practices.
SpinOne for Google Workspace can take your organization’s Google Workspace security to the next level by reinforcing and expanding on Google’s native security tools. SpinOne offers improved visibility and control over user activities, helping to prevent malicious incidents and unauthorized data disclosure. SpinOne’s security solutions for Google Workspace include but are not limited to:
- Spin SaaS Security Posture Management (SpinSPM) – detects and responds to misconfigurations while also providing inventory and assessment of OAuth apps and extensions.
- Spin DLP protects Google Workspace against human error, malicious intent, malware, and other areas when its native DLP falls short.
- Spin Ransomware Detection and Response (SpinRDR) provides AI-driven ransomware detection and incident response capabilities to stop an in-progress ransomware attack on your Google Workspace data.
- SpinBackup offers a 3x-a-day automated backup on in multiple locations across the globe to comply with local regulations.
By proactively defending against advanced threats and reinforcing your native Google security tools, SpinOne helps ensure your data is safe, compliant, and recoverable, empowering your business to operate with confidence.
Get a free demo to learn more about SpinOne’s capabilities in protecting Google Workspace.
FAQs
How do I make my Google Workspace more secure?
To make your Google Workspace more secure, manage your access properly with Google RBAC, enable IAM for authentication and authorization, activate email and phishing protection, and enable DLP and audit logs for access and file sharing monitoring. Finally, partner with third-party solutions such as SpinOne to reinforce built-in capabilities.
Does Google Workspace have security?
Sure, Google Workspace offers basic built-in security capabilities such as phishing and malware protection, DLP, RBAC, etc. However, these capabilities often fall short when it comes to advanced threats such as ransomware, social engineering, or AI-powered cyber attacks.
Is Google Workspace more secure than Gmail?
Partially yes. Google Workspace is generally more secure than Gmail because it is designed for business use and offers additional security features and administrative controls over user accounts that are not available with standard Gmail accounts.
Is Google Workspace more secure than Microsoft 365?
Google Workspace and Microsoft 365 both offer robust security, but their security depends on specific organizational needs. For example, Workspace is more secure for organizations looking for secure real-time collaboration, phishing protection, and ease of use. Microsoft 365 offers deeper integration with legacy systems, advanced encryption, and better compliance tools.