Sodinokibi Ransomware: Analysis and Protection

Sodinokibi ransomware has been known for some time, yet the attack on currency exchange Travelex brought this virus into the spotlight once again. Let’s find out more about Sodinokibi, how it works, and how to protect yourself from it.
Sodinokibi Ransomware Analysis
Sodinokibi, also referred to as Sodin or REvil, is a ransomware strain that appeared in April of 2019 and became the 4th most distributed ransomware in the world since then. GandCrab ransomware authors are likely to have taken part in the development of Sodinokibi.
Sodinokibi is a notable example of Ransomware-as-a-Service. It means that there are two groups working on ransomware: code authors develop it, and affiliates spread it to infect systems and collect a ransom. Sodinokibi spreaders are known for a special social engineering move—they threaten to double the required payment if the ransom is not paid within several days.
Highly evasive and constantly upgraded, this ransomware is a serious threat for organizations of all sizes. Primarily, Sodinokibi targets American and European companies, though attacks were reported all around the globe.
How Sodinokibi Works
Sodinokibi exploits a vulnerability in Oracle WebLogic (CVE-2019-2725), trying to get access to user data and encrypt it. Sodinokibi is often spread by brute-force attacks and exploits in servers, though using phishing or spreading infected links through ads is common as well.
Sodinokibi often successfully bypasses antivirus software. It downloads a .zip file with ransom code, written in JavaScript. Sodinokibi can move through an infected network, spreading further and looking for system-critical data. This ransomware strain encrypts files and appends a random extension to encrypted files. As long as the core ransom code is not deleted, Sodin may reinstall itself.
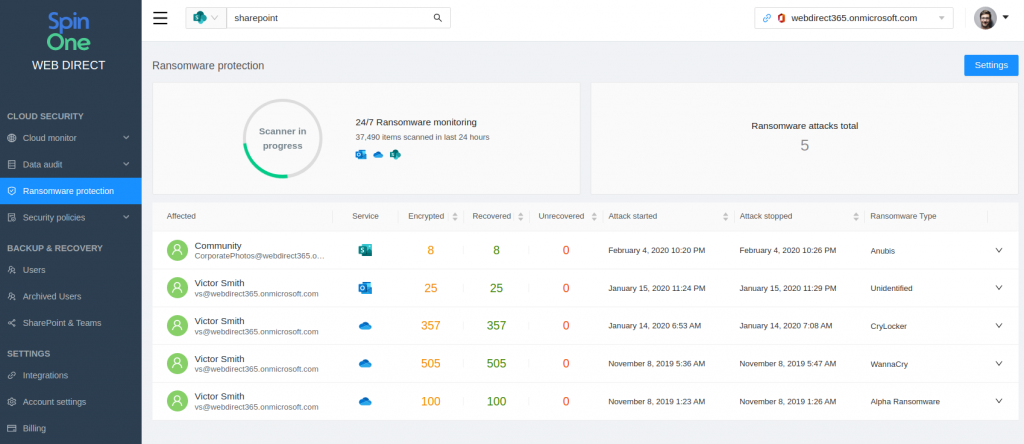
Making things worse, Sodin may infect on-site backups as well. To prevent this, we recommend implementing a ransomware backup strategy and using off-site backup tools for your Google Workspace (G Suite) or Microsoft 365 data.
At first, the Sodinokibi ransom demand was near $2500-5000 in Bitcoin, which is comparatively low. Yet, recent attacks have proved that Sodinokibi is becoming high-rolling ransomware with millions demanded for decryption.
Sodinokibi Ransomware Attacks
Sodinokibi is ransomware less than a year old, yet it has already been used in several notable cyberattacks.
PerCSoft attack, August 2019. This Wisconsin-based company, providing data backup service for dental offices across the USA, was attacked using Sodinokibi ransomware. More than 400 dental offices were impacted. This attack was a bright example, that backups can be damaged, thus advanced ransomware prevention tools are required.
Travelex Ransomware attack, January 2020. Travelex, a well-known currency exchange, had faced an enormous ransom demand of more than $6 million in Bitcoin. Hackers seized sensitive data of the company, threatening to sell it unless getting paid.
Sodinokibi disrupted the workflow of the company. The unavailability of online currency exchange services was one of the consequences. Moreover, several U.K. banks, relying on Travelex, were impacted. First Direct and Barclays were among them.
Gedia Automotive attack, January 2020. Sodinokibi damaged the German automotive parts manufacturer. As a result, 50GB of data was obtained by hackers. Similar to the previous incident, hackers threatened to sell the data if the ransomware was not paid.
See our extensive list of ransomware attacks in our Ransomware tracker.
Sodinokibi Protection Strategies
There is no reliable Sodinokibi decrypt tool available, so the best way to protect your data from this ransomware is to prevent it. What should you consider while setting up your ransomware prevention?
First of all, have your data backed up. Backing up your data allows you to restore it in case of a ransomware attack. As we’ve mentioned in Ransomware Backup Strategy, even a backup can be infected by ransomware. However, there are several advanced practices that greatly reduce the chance of infection: 3-2-1 backup strategy, backup versioning, and others.
Looking for an advanced backup solution? Try SpinOne for G Suite and Microsoft Office 365—a cloud backup software that combines anti-ransomware practices mentioned above.
Secondly, boost the security of your backup with additional ransomware protection software. The best way to prevent your backups from being corrupted is to stop ransomware attacks as soon as possible. That’s why advanced ransomware detection tools may come in handy.
To combine advanced backup functionality with ransomware protection in a single software, we recommend using SpinOne. SpinOne is an automated security platform that combines advanced backup functionality with ransomware prevention. This solution follows the 3-2-1 strategy, offers multiple backup versions, and automatically backs up data three times a day plus it utilizes advanced ransomware detection methods. SpinOne implements an innovative ransomware detection method – behavioral analytics. This method is based on understanding ransomware patterns via abnormal file behavior. Powered by machine-learning algorithms, it allows the achievement of 99% accuracy in detecting ransomware.
Have more questions about SpinOne? Schedule a demo and get them answered!
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
What You Need to Know About AT&T’s Data Breach and How t...
Arguably, it is one of the worst breaches that has happened recently. AT&T disclosed in...
Lessons from the Twilio Breach: Securing SaaS Applications Against ...
Another recent security breach has made organizations think yet again about SaaS apps they may...
Unpacking the CrowdStrike Outage: Causes, Impacts, and Protecting Y...
A major global IT outage occurred on Friday, July 19, 2024, causing widespread disruptions across...