The Missing Piece to your Cybersecurity Strategy
Going into the new year, have you checked the “blind spots” in your organization’s cybersecurity posture? Potential security issues can be lurking anywhere, and your weakest link can be your biggest vulnerability when it comes to a security breach. Considering the security threats associated with users and user accounts is common. However, your cybersecurity strategy may be missing a key piece: SaaS app security. Here’s why it needs your immediate attention.
Apps, Apps, and more apps!
Unquestionably, one of the biggest benefits of using cloud SaaS environments is the enormous number of cloud SaaS apps available. In addition, SaaS apps are at the heart of how businesses empower employees in the new hybrid work model – allowing employees to work from anywhere.
In our highly connected world, using SaaS applications has become second nature to most users. Effective cloud SaaS apps allow organizations to tap into talent worldwide and give employees the tools to feel connected with teammates, regardless of location.
Cloud SaaS has become the norm for most communication, collaboration, and business-productivity services. Most businesses no longer house email, file storage, or other solutions like SharePoint on-premises. Instead, they are leveraging cloud SaaS for those services.
Note the following statistics:
- The SaaS market will reach $172 billion in 2022
- Experts are expecting the industry to be worth up to $947.3 billion by 2026
- 45% of SMBs have most or all of their business applications in the cloud
- One-fourth of IT teams are spending the majority of their time managing third-party vendors and business solutions
In addition to the native cloud SaaS applications found in Google Workspace and Microsoft 365, they both include third-party SaaS app marketplaces – allowing users to integrate thousands of third-party apps into their cloud SaaS environment.
SaaS application security – the missing link
Attackers are looking to compromise business-critical data in any way possible. They may target data using phishing attacks, compromised credentials, zero-day vulnerabilities, cloud misconfigurations, and other means. However, third-party SaaS app security is a growing concern with organizations relying on cloud Saas environments.
It is also flying under the security radar for many businesses heavily using cloud SaaS to empower remote employees. As a result, many organizations concentrate their security efforts on the users themselves, their activities, and other aspects. However, third-party applications are becoming “blind spots” for SecOps and business leaders looking to increase the security of cloud SaaS environments.
Shadow IT and malicious SaaS apps
Without visibility or control over which cloud SaaS applications are installed, businesses open themselves up to shadow IT concerns and OAuth abuse by hackers looking for a foothold in the cloud SaaS environment. Additionally, users who can install any SaaS application in the marketplace may look for their own cloud solutions if they find internal tools lacking.
Hackers also understand that if businesses don’t have control over SaaS applications, they can easily target users using malicious applications. How does this type of attack happen? An attacker can use a malicious phishing email to entice users to install an official-looking application.
The email will be worded to make the user think the installation of a cloud SaaS app is needed or even required. For example, attackers may use phrases such as “required security update” or “upgrade your cloud security” to persuade users to install the “update.”
Users who click the link receive an OAuth authorization prompt for granting authorization to the SaaS app. Once given, the malicious cloud SaaS application can now act with all the same permissions as the user. With the OAuth authorization, an attacker can now do the following:
- Bypass two-factor authentication
- Encrypt or delete critical data the user has access to
- Share, leak, copy, or otherwise transmit data
- Disrupt other users who have access to the same data
Cloud SaaS Risk assessments should be mandatory
As businesses navigate the tricky waters of cloud SaaS, they must thoroughly analyze and perform risk assessments on any cloud SaaS application integrated into the environment. A proper risk assessment helps ensure the SaaS applications allowed for installation in the cloud SaaS environment have been deemed safe from a security and compliance perspective and align with the business and other policies defined for the company.
A proper risk assessment helps to define the following:
- The behavior reputation for the software
- Data security – how securely the software transmits and stores data
- Compliance standards – Is the software compliant with the required frameworks?
- Is the cloud SaaS app subject to frequent independent audits of security controls?
- What disaster recovery, availability, and resiliency controls are in place for the application data?
Without a proper risk assessment of SaaS apps, organizations are “flying blind” concerning the application’s security and compliance. However, performing a single cloud SaaS application risk assessment might take a trained SecOps professional hours to complete. Therefore, organizations must use cybersecurity automation and automated risk assessments to protect their livelihoods – their data.
Complete the cybersecurity puzzle of cloud SaaS with SpinOne
Cloud SaaS environments are simply too vast and complex to secure these using manual efforts and tedious tasks. Instead, businesses must take advantage of security automation. SpinOne is a cybersecurity and compliance solution that gives enterprises the visibility and controls needed for securing their cloud SaaS environments.
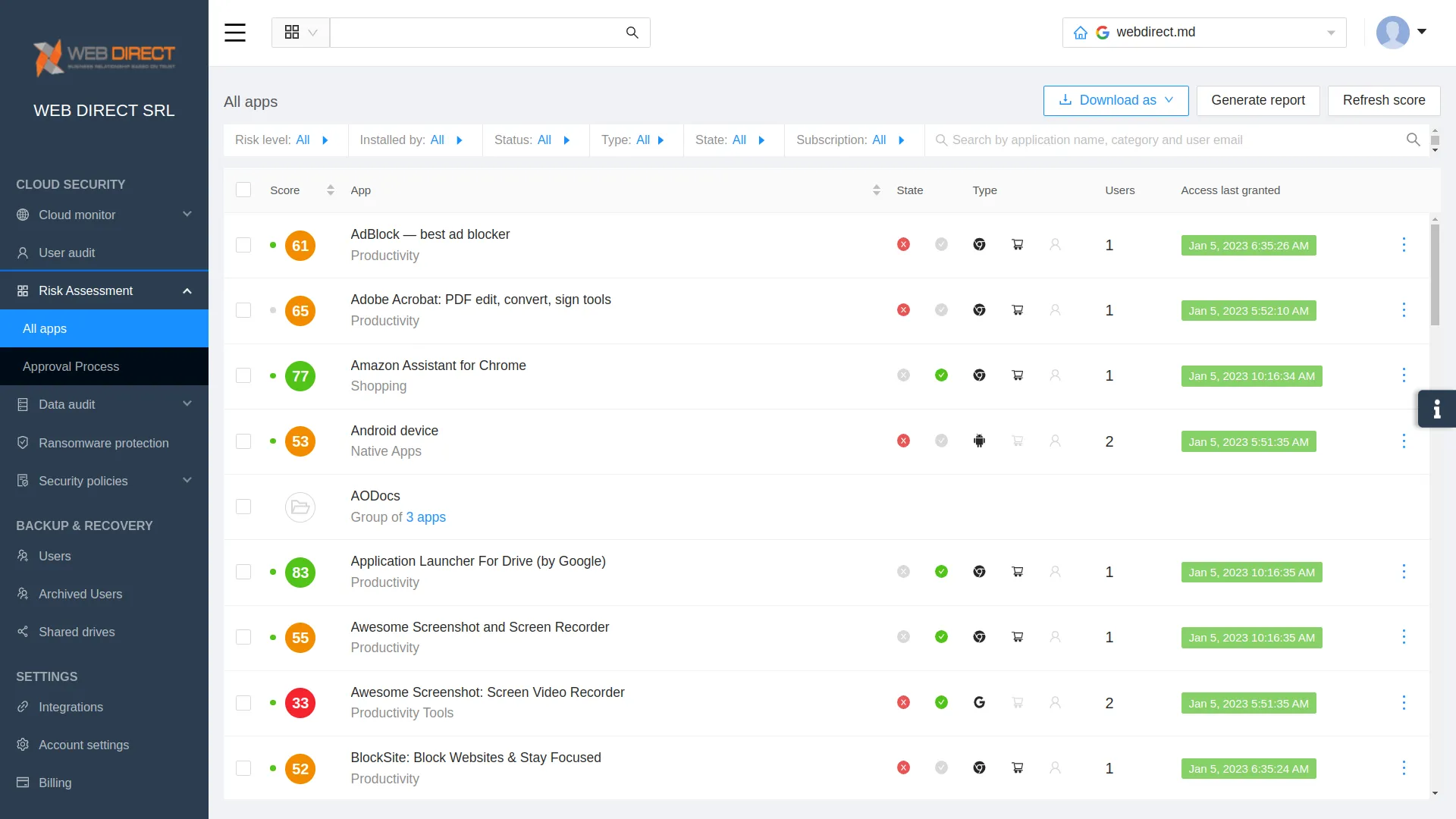
SpinOne uses artificial intelligence (AI) and machine learning (ML) to automate tedious, low-level tasks effectively, allowing SecOps professionals to use their time more efficiently. For example, one of the key capabilities provided by SpinOne is automated risk assessments.
Note the capabilities provided by SpinOne risk assessments:
- Cloud SaaS apps are automatically scored based on security metrics and behaviors
- Using SpinOne automated risk assessment scoring, admins can use SpinOne policies to block or allow apps based on their security score
- It continuously monitors app behaviors and reevaluates the score over time
- It provides the tools businesses need to block risky applications or malicious apps presented to end-users in phishing emails
With the automated scoring, global policies, and third-party app protection provided, SpinOne allows customers to use cloud SaaS applications confidently, knowing the apps have been properly evaluated and assessed for security and compliance risks.
If you would like to speak with a Spin Solution Engineer to discuss how Spin.AI helps protect your environment from malicious cloud SaaS apps, click here to book a demo: Request a Demo.
Was this helpful?
Latest blog posts
How to Create an Effective Cybersecurity Risk Assessment Matrix
Article Summary: This article explores how to create a cybersecurity risk assessment matrix to identify,...
Securing the Gateway: How Browser Extension Risk Assessment Protect...
Browser extensions are a normal component of today’s modern web browsers. They serve the purpose...
The Escalating Threat of Malicious Browser Extensions: How to Prote...
Browser extensions are part of modern tooling that organizations and users make use of to...