Top SaaS Data Protection Challenges – Why Protect SaaS Data
As we enter cybersecurity awareness month, businesses worldwide need to consider how they are protecting and securing their data. As most organizations are adopting cloud environments, specifically cloud Software-as-a-Service (SaaS), protecting cloud SaaS data is critical. However, there are many challenges to providing adequate data protection and security for your business-critical SaaS data. What are these? Let’s consider the top SaaS data protection challenges and tips to overcome them with enterprise data protection software and introducing security practices.
Why protect SaaS data?
First of all, why should we care about protecting cloud SaaS data? After all, aren’t today’s premiere SaaS offerings built on top of world-class hyperscale data centers with multitudes of redundancy?
The data centers run by hyperscale cloud service providers, such as Amazon, Google, and Microsoft, have extremely robust redundancy and availability built into the solution. However, it is essential to understand that cloud SaaS data loss can happen because of the same reasons it occurs in the on-premises enterprise data center. What are these?
- Human error and intentional actions – End users in SaaS environments can delete data by mistake. Disgruntled employees may even delete critical data on purpose. Even though the data centers themselves and the underlying physical hardware are resilient, it does not eliminate the possibility of data loss due to this reason.
- Malicious software and ransomware – Threat actors are more commonly compromising cloud environments. They realize that businesses increasingly place more of their data in the cloud. As a result, future attacks will undoubtedly put increased focus on compromising cloud data. In addition, ransomware in the cloud can happen using phishing attacks, stealing OAuth authorization permissions, file synchronization, and other means.
- Hardware failure – Even with the multitude of redundancy layers in place by cloud service providers, hardware failures can and do lead to data loss in the cloud. All of the major cloud service providers have outages from time to time, affecting access to production environments
Top SaaS data protection challenges and tips to overcome them
Let’s look at the following SaaS data protection challenges and tips to overcome them effectively:
- Lack of backups
- Third-party apps
- Shadow IT
- Lack of proper risk assessments
- Poor visibility and monitoring
1. Lack of backups
As we have already described, data loss can happen in cloud SaaS environments for several reasons. Today’s cloud service providers also operate in what is described as a shared responsibility model, leaving customers responsible for protecting their data.
The shared responsibility model is essential to understand. It means at the end of the day, your business is responsible for protecting and securing the data. The cloud service provider is responsible for the underlying server and network infrastructure. It places the burden of responsibility square on your organization’s shoulders to ensure data is protected.
Tip: Use a third-party cloud-to-cloud backup solution for cloud SaaS environments
- Using a third-party cloud-to-cloud backup solution protects your data from the common causes of data loss. It also gives you control over your data. Even if you end the subscription to your cloud service provider, you have a copy of your data.
- While cloud service providers often provide capabilities such as file versioning, it does not protect you from data loss in all scenarios. In addition, it can be cumbersome to use to recover your files after a ransomware attack or other data disaster.
Protect your SaaS Data from multiple threats
2. Third-party apps
Another high-priority item for organizations to protect their critical SaaS data is controlling third-party cloud SaaS applications. Most cloud SaaS environments provide thousands of SaaS apps that users can easily integrate into the environment. However, without a proper risk assessment, third-party apps can present security risks such as data leaks, malicious behavior, and poor security hygiene.
Attackers can also use malicious applications to launch ransomware attacks in cloud SaaS environments, steal data, and further compromise the environment. As a result, businesses need to limit access to only those cloud SaaS applications that have been rigorously tested and sanctioned by the business.
Tip: Control which third-party cloud SaaS apps are used in the environment
- Limit the default permissions allowing users to install any third-party application. Instead, organizations allow only the installation of only those cloud SaaS apps approved for use.
3. Shadow IT
Shadow IT is becoming a significant problem for organizations today. One poll found that 83 percent of corporate employees engage in informal Shadow IT practices. In addition, cloud SaaS environments have accelerated Shadow IT practices across the board due to the ease with which users can install cloud Saas apps by default.
As we have already mentioned with the default behavior, users can install any third-party apps in cloud SaaS environments, such as Google Workspace and Microsoft 365. Furthermore, they can do this without the approval of IT or other business stakeholders. It is a breeding ground for Shadow IT operations in critical cloud SaaS environments.
Tip: Limit the installation of cloud SaaS applications and perform proper risk assessments of third-party SaaS applications
- Monitor which apps users are installing
- Have an allow list and block list of third-party apps which can or can’t be installed
4. Lack of proper risk assessments
Carrying out proper risk assessments with third-party cloud SaaS applications is vital. However, due to the sheer multitude of cloud SaaS apps available, many businesses struggle with performing risk assessments for cloud SaaS apps using manual risk assessment activities. However, this can lead to significant security risks if cloud SaaS apps are not adequately screened for security and are integrated into the environment.
Tip: Use automated risk assessments and cybersecurity automation to control third-party SaaS apps
- With the thousands of third-party Saas applications in cloud SaaS marketplaces, manual risk assessments of each application would be tedious and highly challenging
- Using automated risk assessments helps to alleviate the burden of manually assessing risk, automating this with artificial intelligence (AI) and machine learning (ML).
5. Poor visibility and monitoring
Poor visibility and monitoring is a challenging problem for businesses looking to protect and secure their critical data, especially in cloud SaaS environments. Poor visibility of what is happening in cloud SaaS environments can lead to sensitive data shared outside the organization, nefarious user activities, stolen credentials, Shadow IT, and many other serious problems.
Tip: Provision monitoring of cloud SaaS environments, including user activities, data sharing, third-party applications, and other cloud SaaS environments metrics
- Proper monitoring increases the visibility of potentially malicious activities and helps organizations to secure their critical data from inappropriate or unsanctioned data sharing
- Monitoring is also a requirement of many compliance regulations
Solve SaaS data protection challenges with Spin
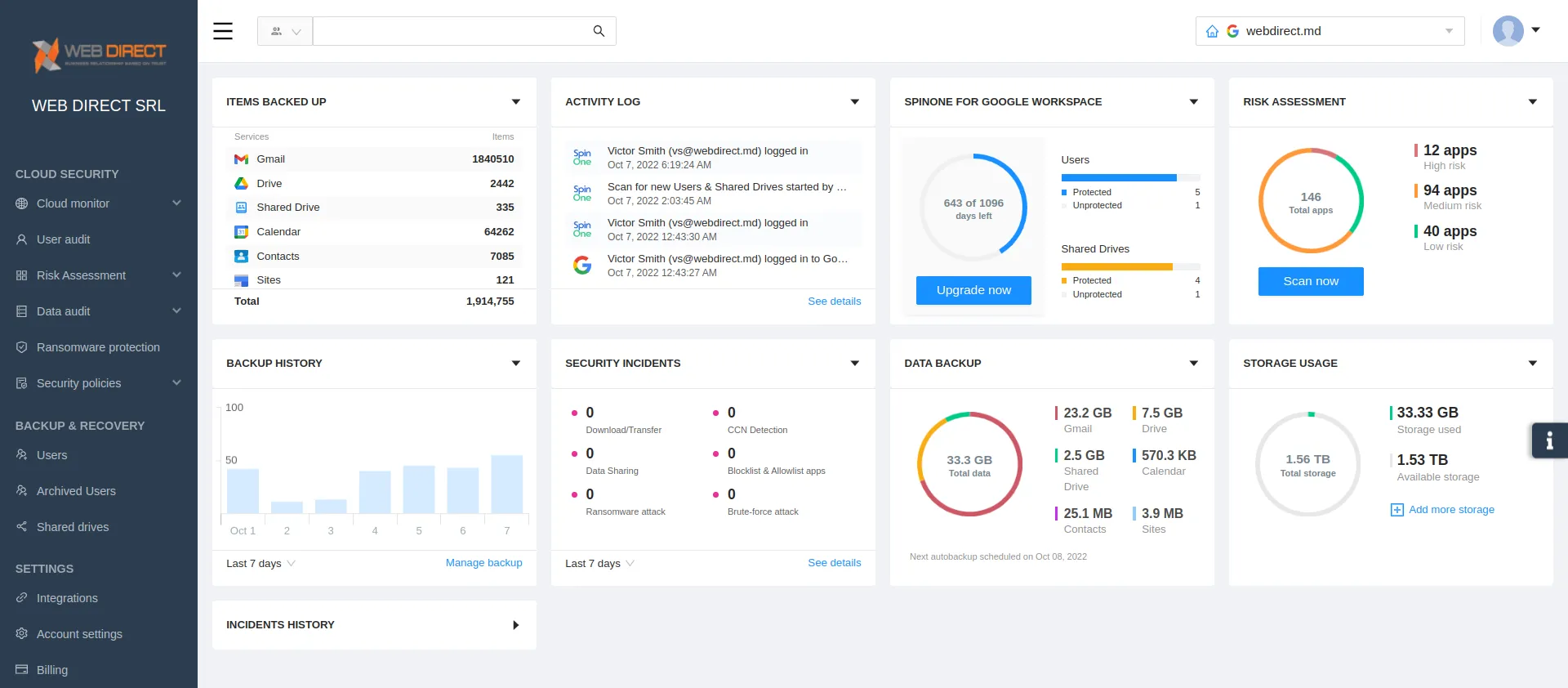
SpinOne enables organizations to have the capabilities and features needed to protect and secure cloud SaaS data to meet the complex challenges facing organizations utilizing cloud SaaS environments. With SpinOne, you get:
- Cloud-to-cloud backups
- Third-party app control
- Cybersecurity automation to prevent Shadow IT
- Automated cybersecurity risk assessments for cloud SaaS apps
- Visibility and monitoring of cloud SaaS activities, data, and security
If you would like to speak with a Spin Solution Engineer to discuss how SpinOne can help you meet your ransomware protection challenges, click here to book a demo: Request a Demo of SpinOne
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


