Beginners Guide to OAuth Authentication
Cloud Software-as-a-Service (SaaS) environments are a marvel of innovation and technology resources allowing businesses to achieve remarkable collaboration, communication, and business productivity. Modern cloud environments use an authentication protocol called OAuth authentication, allowing users to grant access to third-party applications on their behalf. Let’s dive deeper into what OAuth is and better understand this cloud-native protocol.
What is OAuth?
OAuth was developed by cloud service providers, such as Google, Twitter, and others, and released as an open standard in 2010. Since its release, most cloud service providers have been using OAuth in some way, including Amazon, Apple, Facebook, Instagram, LinkedIn, Microsoft, Netflix, and others. Now, the standard is in version 2.0 and provides even more capabilities in terms of security.
OAuth provides a framework allowing users to grant third-party applications access to cloud resources without disclosing their username and password to the application.
OAuth Authentication or Authorization?
Although OAuth is commonly referred to as an authentication protocol, it is actually an authorization protocol. The RFC documentation notes the OAuth 2.0 standard this way:
The OAuth 2.0 authorization framework enables a third-party
application to obtain limited access to an HTTP service, either on
behalf of a resource owner by orchestrating an approval interaction
between the resource owner and the HTTP service or by allowing the
third-party application to obtain access on its own behalf. This
specification replaces and obsoletes the OAuth 1.0 protocol described
in RFC 5849.
The simple difference between authentication and authorization is authentication verifies one’s identity, while authorization deals with “who granted permissions and to whom do they grant them.”
How does OAuth Authentication work?
Most of us have been to an amusement park where you buy tokens to ride the rides, participate in other activities, and take in all the park offers. These tokens grant you access to resources in the park. The tokens say nothing about your identity (authentication) but define what you are authorized to access. With this analogy in mind, OAuth authorization is a token-based protocol.
What is an access token? Like the token you receive at the park, the OAuth access tokens grant you access to resources. The token is made up of many technical components. However, in its basic sense, the token is another way to represent a username and password without one knowing the username and password.
This idea is essential in cloud environments where users want to authorize third-party cloud applications to access resources on their behalf. OAuth authorization allows issuing a token to a third-party application, so it does not have visibility to the user’s password but has access to operate on behalf of the user. Third-party applications in the cloud service provider marketplaces, including Google Workspace and Microsoft 365, work using OAuth.
OAuth abuse
While OAuth has measures included to help secure the authorization framework of the standard, attackers may still be able to compromise OAuth in various ways.
These include:
- Malicious third-party applications – Malicious third-party apps can masquerade as legitimate apps to steal date, launch ransomware attacks, and other malicious activities
- Access token leakage – Unscrupulous services, known as collusion networks, collect OAuth tokens for applications using OAuth. These tokens can be used on behalf of applications and colluding accounts.
- OAuth vulnerabilities and security weaknesses – Like any technology, OAuth is subject to vulnerabilities and zero-day attacks.
Let’s consider how attackers can use malicious third-party applications to compromise OAuth tokens in cloud Software-as-a-Service environments.
Malicious third-party applications
Malicious third-party applications can effectively steal OAuth tokens from users and carry out malicious activities without the user knowing. Unfortunately, even though OAuth itself is relatively secure, if a user unknowingly grants an OAuth token to a malicious app, the application can act on behalf of the user with all the permissions granted to that user. How does this happen?
Using a phishing email, attackers prompt a user to install or upgrade a cloud application that looks safe or even official. Then, thinking they are safe to do so, the user clicks the link to grant permission to the app, which, unfortunately, can carry out malicious behavior. So what does an OAuth prompt look like?
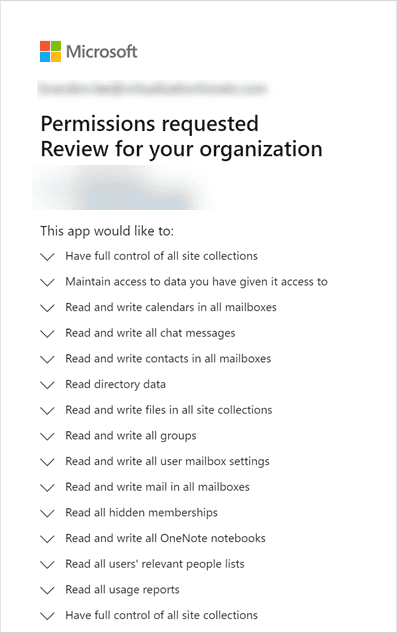
An OAuth token granted to a third-party cloud application has two additional security disadvantages. These are:
- OAuth tokens bypass two-factor authentication
- They have to be explicitly revoked and do not time-out automatically
Blocking risky third-party SaaS applications
As businesses continue migrating critical data and services to cloud SaaS applications, they must block risky third-party SaaS applications and conduct proper risk assessments of any SaaS app they decide to use. While third-party applications in Google Workspace and Microsoft 365 can significantly extend the capabilities of cloud SaaS environments, they also introduce risk. Unfortunately, modern cloud SaaS environments make it extremely easy for users to install and use third-party applications without the visibility and consent of IT. As a result, users can easily become involved in Shadow IT operations and potentially expose the business to security and compliance risks.
SpinOne is a cloud security posture management (CSPM) solution that allows businesses to take control of cloud SaaS applications and conduct proper risk assessments of all SaaS apps integrated into the environment. It helps to meet security and compliance challenges with ease.
With SpinOne, you can:
- Perform automated risk assessments of cloud SaaS applications and browser extensions
- Block risky third-party applications and browser extensions
- Use an automated scoring system from SpinOne to quickly assess SaaS apps
- Only allow access to applications that meet your requirements
If you would like to speak with a Spin Solution Engineer to discuss how SpinOne helps protect your environment from malicious cloud SaaS apps, click here to book a demo: Request a Demo.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


