Browser Extension Risk Assessment Plugin
Reduce Risk with SpinMonitor – Free Extension Security Checker

Assess the Risk of Browser Extensions Installed in Your Browser
SpinMonitor – Free Extension Security Checker detects and assesses the risk of all browser extensions, including those pushed directly to the browser, providing full visibility into the potential business, security, and compliance risks of each extension. SpinMonitor is quick and easy to install, giving IT and SecOps teams a proactive, automated solution for reducing browser extension risk.
Dealing with thousands of Apps and Browser Extensions?
Looking for Automation and Fast Incident Response?
Discover all the benefits of the Professional version below
Unique Value
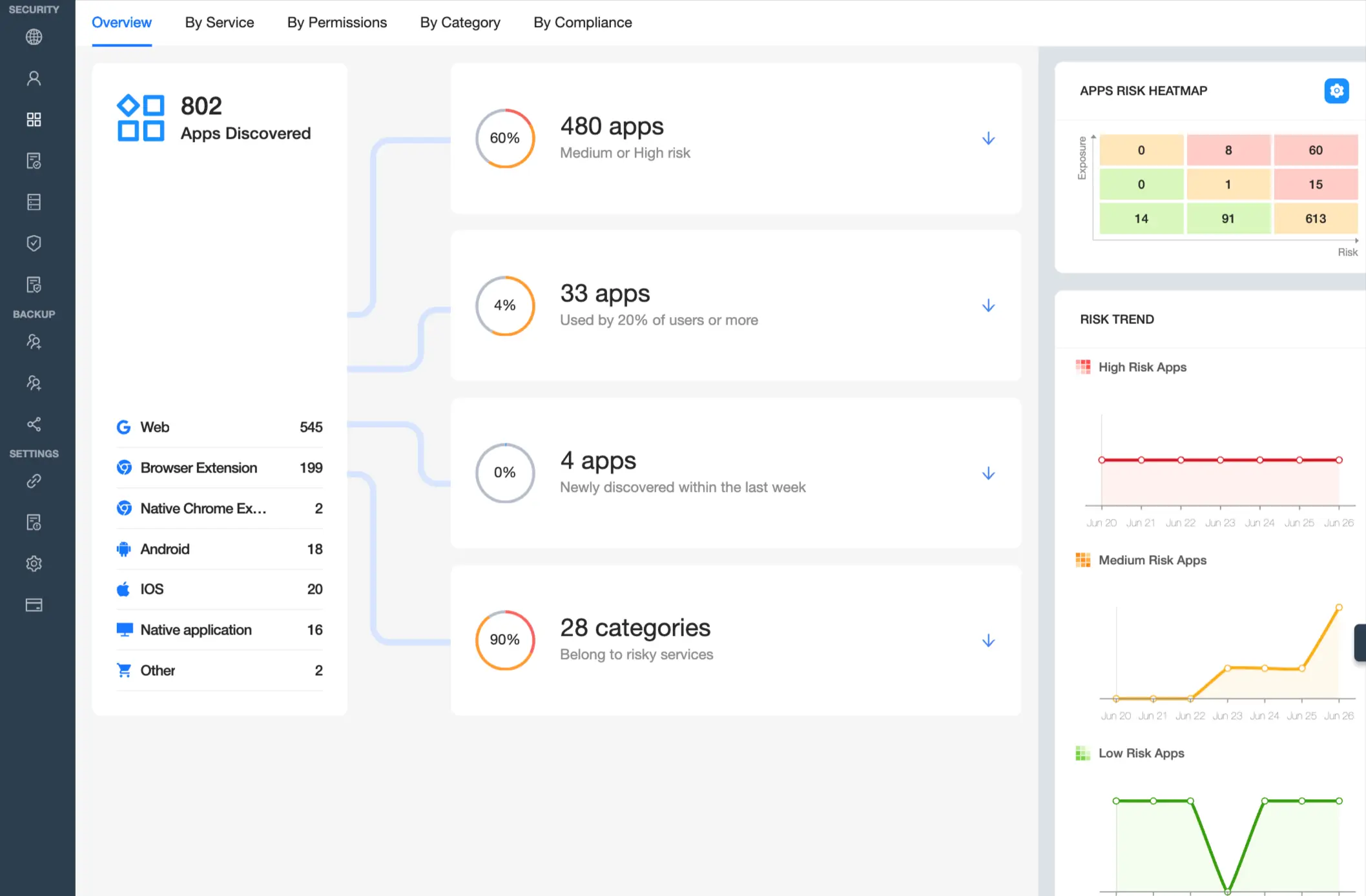
- Simplified Security Operations: Streamline your security management processes.
- Reduced Shadow IT risk: Mitigate the threats posed by unsanctioned apps or browser extensions.
- Automated Risk Assessment: Continuous 24/7 scanning and evaluation using AI to ensure high accuracy.
- Rapid Risk Identification: Identify risky, medium-risk, or low-risk apps in a matter of seconds.
- Automated Access Management: Implement blocklist/allowlist policies effortlessly.
- Vulnerability Scanning: Detect apps or browser extension vulnerabilities.
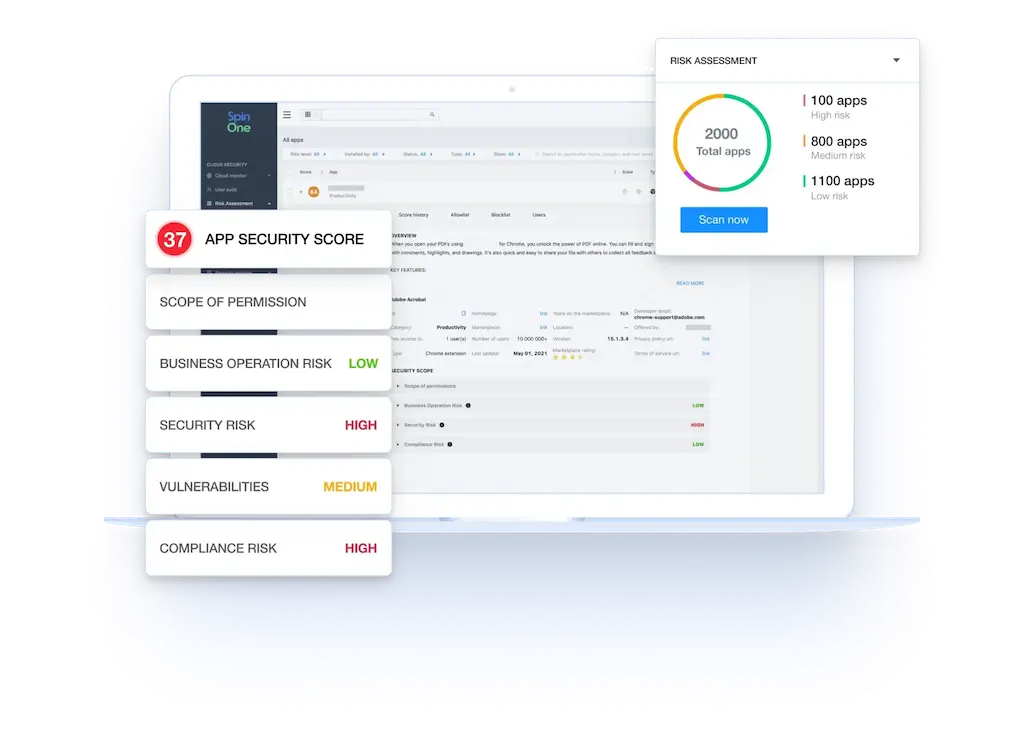
Features

- Comprehensive Inventory: Full inventory of SaaS apps, cloud apps, mobile apps, and browser extensions with access to your data.
- Risk Scoring & History: Evaluate and track the risk levels of each app over time.
- Audits: Conduct permissions, user, and compliance audits.
- Security Policies: Implement and manage robust security policies.
- Advanced Reporting: Generate detailed insights with advanced reporting tools.
- AI-driven Assessment: Over 400,000 apps and browser extensions assessed.
- Broad Compatibility: Available for M365, Google Workspace, Salesforce, and Slack.
- Seamless Integrations: Integrate with Splunk, Email, ServiceNow, Jira, Slack, and Teams.
Trusted by over 1,500 organizations across 100+ countries

Enterprise security for SaaS data






Related Solutions
Application & Browser Extension Risk Assessment Tools
Get Visibility and Control Over Your SaaS Environment
Frequently Asked Questions
What is a browser extension?
A Browser Extension is a small piece of software that adds functionality or features to a web browser to enhance browser experience. Extensions can be used in browsers like Google Chrome, Firefox, Edge, or Safari. They are powerful tools that can be used for good or for bad.
What are the main risks of browser extensions?
Browser extensions can:
- Spy on you
- Steal your data
- Perform account hijacking
- Collect & sell your data
- Delete, encrypt, or damage your data
- Lead to non-compliance
What are the best practices for managing browser extension risk?
- Visibility: Maintain an up-to-date catalog of all browser extensions across the organization. This inventory serves as a critical foundation for systematically assessing and prioritizing the organization’s threats and vulnerabilities.
- Risk Assessment and Reassessment: Perform a comprehensive risk assessment of every browser extension, including an evaluation of its business operations, security, privacy, and compliance risks. This assessment must be continuously performed to account for any changes in the browser extension.
- Automation and Incident Response: Leverage automation to immediately respond to incidents. By automating this process, organizations can effectively contain the risks, minimize the potential impact, and maintain continuous protection.
Are browser extensions safe to use?
The browser extension ecosystem offers tremendous value by enhancing user experience, adding useful features, and improving productivity. Extensions can be great tools for personalizing workflows, streamlining tasks, and accessing additional services directly through the browser. However, some extensions can introduce significant risks, such as data leaks or privacy concerns, if not properly managed. To ensure the security, compliance, and privacy of both your data and your customers’ data, it’s essential to have the right monitoring and risk assessment tools in place. With the right safeguards, you can fully leverage the benefits of extensions while minimizing potential threats.
To learn more, read the guide Understanding Browser Extension Risk.
What methodology did Spin.AI use to build the Risk Assessment?
Spin.AI Risk Assessment methodology is built based on the following frameworks:
- OWASP (Open Web Application Security Project) – Provides extensive documentation on secure coding practices, including those applicable to browser extensions.
- Mozilla Developer Network (MDN) – Offers detailed documentation on how browser extensions should manage permissions and data securely.
- Google Chrome Web Store Policies – Google’s policies provide insight into best practices for developing secure and compliant browser extensions.
- Electronic Frontier Foundation (EFF) – The EFF discusses privacy risks and considerations for browser extensions.
- Center for Internet Security (CIS) – CIS benchmarks and guidelines provide insights into secure configurations that apply to browser environments.