CISO Guide for Closing Cybersecurity Skills Gap
Many challenges are facing CISOs today. These challenges include the cybersecurity threats themselves, hiring the right talent, and effectively implementing the tools and solutions needed to combat current and future threats. How can CISOs narrow the cybersecurity skills shortage? How can AI and having the right tooling help to combat current cybersecurity threats? Let’s consider a CISO guide for closing the cybersecurity skills gap and see how this can be accomplished.
There couldn’t be a more important topic for organizations today than cybersecurity. Businesses that fail to consider cybersecurity as part of their modern strategy are setting themselves up for disaster and most likely will be the subject of news headlines – not in a good way. The Chief Information Security Officer plays a pivotal role in the overall cybersecurity strategy for the business.
Closing the cybersecurity skills gap
As businesses with CISOs at the helm develop their cybersecurity strategies, there is a lot to consider on the horizon and with the current threat landscape. With the cybersecurity skills gap and shortage facing businesses today, what strategies are necessary for companies to build their cybersecurity strategy successfully? Let’s consider the following in our guide for closing the cybersecurity skills gap:
- Evangelize cybersecurity
- Simplify products and services
- Introduce security automation
- Don’t neglect the basics
- Protect cloud environments
Evangelize cybersecurity
There is no question there is a cybersecurity skills shortage across the board. According to Cybersecurity Ventures:
Over the eight-year period tracked, the number of unfilled cybersecurity jobs is expected to grow by 350 percent, from one million positions in 2013 to 3.5 million in 2021. And of the candidates who are applying for these positions, fewer than one in four are even qualified, according to the MIT Technology Review.
How can CISOs and organizations deal with this extreme shortage of cybersecurity talent for combatting current and future cybersecurity threats? CISOs, businesses, and various organizations can encourage interest in cybersecurity by using the following channels:
- Partner with K-12 local school districts to give visibility to the field of cybersecurity
- At the Collegiate level, internships can allow college students interested in computer science or cybersecurity to gain real-world exposure and experience.
- Outreach programs in communities allow students to see what they can do in the cybersecurity career field.
- Changing onboarding, education, and reeducation – Again, investment in education channels, outreach programs, and further reeducation of graduates and others looking to enter into the cybersecurity career field can help offset the cybersecurity talent shortage.
Simplify cybersecurity products and solutions
To effectively deal with the exploding cybersecurity risks on the horizon, organizations must continue incorporating new technologies, automation, and artificial intelligence (AI) solutions to accomplish lower-level job tasks.
More efficiently leveraging technology in place of “humans” to accomplish these lower-level tasks requires fewer cybersecurity professionals may be needed to carry out effective SecOps operations. It helps in the area of cybersecurity talent shortages. However, in addition to leveraging new technologies, simplification is vitally important to ensuring cybersecurity operations run efficiently and do not lead to solutions “bloat” or an unnecessary need for niche skills.
Why should CISOs be investing in security automation?
- It is a game-changer, malware detection, admin workload benefits, and greater accuracy of detection.
- Properly configured automation solutions allow reporting, which can provide effective auditing.
- Squelch false positives seen with legacy alerting
Introduce security automation
In organizations without security automation in place, humans have to carry out low-level tasks such as parsing through logs, processing network traffic looking for anomalies, and other tasks. Without automated processes, humans cannot carry these out efficiently. It is especially true with the sheer number of data points, and telemetry data organizations are capturing today.
On top of the lack of security automation, many organizations may use multiple solutions and toolsets to accomplish the full range of cybersecurity operations. There may also be overlap and various systems needed to provide visibility across the board. By simplifying and consolidating software and technology tools, the need for multiple skillsets related to a particular product or solution is reduced. In addition, it makes the workflow of defensive cybersecurity measures more manageable and more efficient.
Again this is where automation provides the answer for many organizations. It allows lower-level tasks to be handled by automated computer processes so cybersecurity professionals can carry out high-level functions, strategic planning, and higher-level analysis. How effective is security automation when it comes to handling these lower-level tasks?
According to Ann Johnson, Corporate Vice President Cybersecurity Solutions Group at Microsoft, they use security automation for many different use cases.
- Detecting malware (so defenders don’t have to deal with it). AI is being used to model the threat, and this modeling, driven by AI, happens in milliseconds, not minutes. Thus, low-level task automation is highly valuable. High-level tasks then are left for cybersecurity professionals.
- Microsoft sees 6.5 trillion signals a day of threat and telemetry data at MSFT. Without security automation, there is no way human beings can process, parse through, and make use of that many data points. However, it is possible with AI.
- AI can help build security into software solutions.
- AI can make it easier to go through the volumes of data and telemetry that come into the enterprise.
The cybersecurity skills gap also plays into the lack of automation in many environments. Understanding the toolsets and having the skillset to introduce, maintain, and administer security automation requires specific skills and expertise. Unfortunately, these skills can be challenging to find due to the high demand and lack of personnel to fill these types of roles.
In a recent study by IDG Research Services, 55% of senior IT and IT security leaders cite a lack of security automation as the top obstacle to security operations and management, followed by outdated technology and skills gaps. The immediate need to automate and the lack of cybersecurity professionals with the expertise and skills in these disciplines and technologies is helping exacerbate the immediate challenges of many organizations.
Don’t neglect the basics
Ann Johnson, quoted earlier, mentioned that from cyber hygiene or cyber resilience standpoint, it is still found that 70-80% of breaches are due to a lack of essential cybersecurity best practices. What are those?
- Sharing domain passwords
- Weak domain passwords
- Too much privilege at the endpoint
- No multi-factor authentication
No matter how sophisticated the cybersecurity solutions and technologies an organization uses, the likelihood of a breach is high without basic cybersecurity hygiene in place. In addition to using new cybersecurity solutions, tooling, and security automation, they must ensure security best practices.
Protect cloud environments
The number of services and amount of business-critical data moving to the cloud is staggering. Accelerated by the global pandemic, businesses have switched their cloud migrations into high gear to provide resiliency, accessibility, and access to services that would otherwise not be possible on-premises.
All too often, businesses migrate data and services to cloud environments without proper security controls in place. There is a misconceived notion that data in the cloud is inherently safer than data on-premises and is automatically backed up for you by the cloud service provider.
However, while cloud service providers operate world-class data centers with resiliency and uptime ratings that are not achievable in the private data center, it does not guarantee your data is safe. Threats can still reach cloud data in the form of security threats, data leaks, ransomware, and other concerns.
Leading cloud Software-as-a-Service giants such as Google and Microsoft have native solutions to protect your data to an extent. However, most organizations find these built-in solutions lack features, coverage or are even non-existent in specific plans or subscription levels. They lack in the following two crucial ways:
- They do not include an enterprise backup solution
- They lack security automation
Neither Google nor Microsoft includes an enterprise backup solution
As of the time of this writing, neither Google nor Microsoft offers what is documented as a “backup solution.” Instead, both tout “versioning” and “deleted items” recovery. These are limited in several key areas when it comes to considering these backups.
- Retention is limited by the cloud vendor, not you as the organization
- End-users with write permissions can delete the entire version history
- Using Compliance Retention can help cover gaps in the normal retention policies of versioning. However, it is limited to higher-level plans
- Your “backups” are stored in the same cloud as “production.” If you have a production outage, most likely, you can’t get to your backups either.
They lack security automation
In addition, while Google and Microsoft have cybersecurity capabilities included in their enterprise cloud SaaS offerings, these often lack security automation. For example, the response to ransomware is reactive instead of proactive. Ransomware is often allowed to encrypt large numbers of files with only a notification to inform the cloud admin that ransomware is detected. Instead, the admin is directed on how to recover the organization’s data.
Note in the Ransomware detection and recovering your files KB, Microsoft mentions the following:
“Ransomware detection notifies you when your OneDrive files have been attacked and guides you through the process of restoring your files. When Microsoft 365 detects a ransomware attack, you’ll get a notification on your device and receive an email from Microsoft 365. If you’re not a subscriber, your first notification and recovery is free.”
SpinAudit SaaS application automated risk assessment
Organizations moving to the cloud can be overwhelmed by security implications and concerns with cloud data and third-party applications. Performing a risk assessment of all cloud applications and browser plugins using manual efforts would be impossible. SpinOne provides an automated way to assess third-party applications’ business, security, and compliance risks. Consider how SpinAudit helps to automate the risk assessment lifecycle of SaaS applications. It provides the following risk assessment automation.
Continuous risk level analysis of applications – SpinAudit detects when new apps are installed or uninstalled. It automatically reviews the application and identifies apps that have been blocked. Once SpinAudit has blocked an app, its access is revoked any time a user attempts to install it in the cloud SaaS environment.
User behavior analysis – Determine important cybersecurity information about user behavior, including when they are accessing, what applications they are using, which IP they are connecting from, and geolocation.
Understand how cloud data is accessed and shared – See which files are accessed and shared with whom. Easily see if the information is shared publicly. Capture events in historical dashboards. Identify sensitive information such as Credit Card Numbers (CCNs).
Implement security policies – Use granular policies in customizing apps and data audits, and domain audit-related policies. It allows for specific rule scopes, exceptions, and notification settings on a per-rule basis.
Use modern cloud cybersecurity protection
We have already seen how dealing with the cybersecurity skills gap requires using security automation, artificial intelligence (AI), and using the right tools and solutions to enforce and ensure security. Securing modern cloud SaaS environments requires the same approach.
SpinOne is a modern cybersecurity platform that leverages artificial intelligence (AI) and security automation to secure your business-critical cloud SaaS environments. In addition, it provides industry-leading ransomware protection that leverages security automation, not reactive notification-only processes.
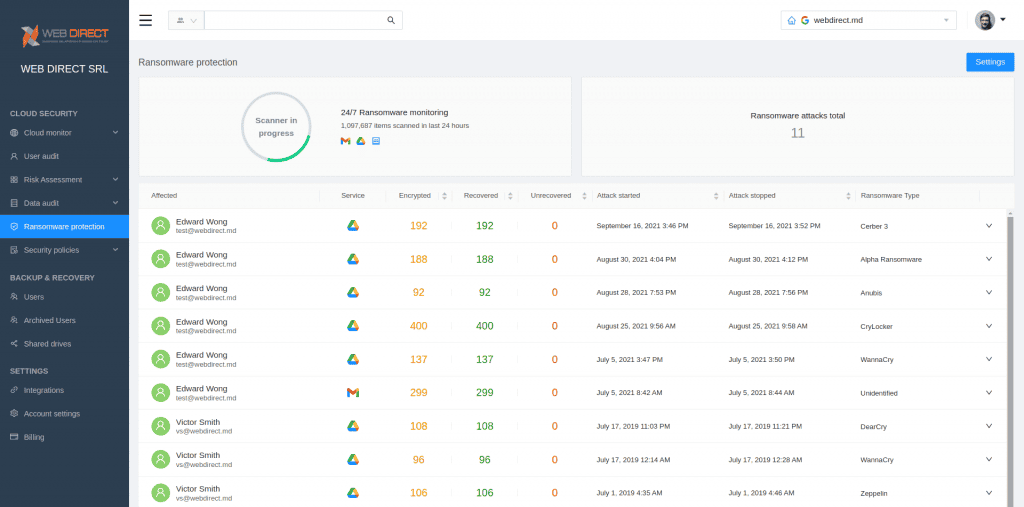
SpinOne Ransomware Protection uses an automated workflow to handle ransomware infections in your Google Workspace or Microsoft 365 environment, including
- 24x7x365 scanning of your business-critical data
- When ransomware is detected, the source of the attack is immediately blocked
- The data is scanned to detect any files that were affected before the ransomware process was blocked
- Affected data is automatically restored without administrator intervention (this is configurable)
- Admins are automatically notified of the ransomware attack and the remediation actions taken
The fully automated, proactive ransomware protection that SpinOne provides allows businesses to drastically reduce the number of cybersecurity professionals needed to monitor and protect cloud SaaS environments.
SpinOne also includes an AI-driven cloud applications audit that, in seconds, can access the risk of a cloud application and determine if the application is malicious. Organizations can leverage SpinOne to automatically assess and audit cloud applications, allow or block applications. This audit process happens continuously and can quickly discover malicious activity from a once-safe application.
Concluding
CISOs at the helm of the security strategy for today’s businesses face many challenges. The growing number of ransomware attacks, malicious data breaches, and other cybersecurity events emphasize the need for businesses to give attention to good cybersecurity practices. With the cybersecurity skills shortage, there can be challenges with staffing the right skillsets and implement strong SecOps operations. Businesses can close the cybersecurity skills gap by evangelizing cybersecurity learning and providing the resources needed for young ones and graduates to gain exposure to the cybersecurity career field. The cybersecurity skills gap can also be closed by implementing cybersecurity automation, simplifying toolsets, ensuring good cybersecurity hygiene, and protecting cloud environments. SpinOne provides AI-driven cybersecurity automation to protect cloud SaaS environments from the threats facing organizations today, such as data breaches and ransomware.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Midnight Blizzard Attack on Microsoft: Key Lessons for Strengthenin...
Midnight Blizzard Attack on Microsoft: Key Lessons for Strengthening Your SaaS Security From November 2023...
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...