Cloud App Security Best Practices for Google Workspace and Office 365
Cloud applications became tightly woven into the modern workflow. On average, a company with 200 to 500 employees uses 123 SaaS apps. No wonder, apps help companies to improve communication and productivity. However, there are significant security risks related to data loss and leakage, malware infections, and compliance violations. That’s why app security should become a high priority. As cloud security experts, we’d like to share 5 cloud app security best practices to help you control your apps and protect your data.
Cloud App Security Best Practices
Cloud app security requires a multi-layered approach to cover a wide range of threats, risks, and challenges. Here are some of the best security practices to ensure that the apps you use won’t compromise your data.
Control Shadow IT
Understanding what apps can access your data is a fundamental aspect of cloud security. However, not all apps with access to your environment are visible at first glance. According to Microsoft’s research, 80% of employees use non-sanctioned apps. This situation is known as shadow IT. Shadow IT grows rapidly together with the role of cloud data and collaboration.
The usage of unapproved and unmanaged apps is a major risk for a company’s security and compliance. A risky app can lead to malware attacks, data loss, and unauthorized access. On top of that damages, you may face fines for compliance violations if any sensitive data is compromised during an incident.
That’s why getting full visibility and control over all cloud apps, both approved and unapproved becomes a serious issue. So how to control shadow IT efficiently? Find out in our article about 4 Rules and 3 Tools to manage the shadow IT.
Implement Cloud App Security Audit and Risk Assessment
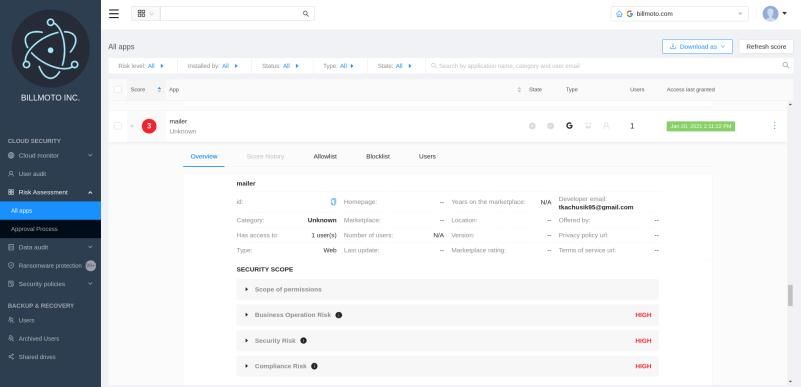
App risk assessment is a vital part of cybersecurity risk assessment. The core idea behind app assessment is simple—you have to separate the wheat from the chaff. The assessment process can be divided into several stages.
- Develop appropriate procedures and define acceptable risks.
- Measure how risky are the apps you use and assign a security score. This score will help you to determine what apps are safe or too risky to keep using.
- Perform app whitelisting/blacklisting based on security score and your policies. In other words, split all apps into two groups. Whitelisted apps are safe to use, and blacklisted apps should be disconnected.
After the application assessment and whitelisting are performed, your cloud environment will be safer. However, mind that apps can be updated and become more/less secure. That’s why risk assessment should be ongoing.
Create a Data Loss Prevention Strategy
App security is one of the key elements of the corporate digital ecosystem covered by Data Loss Prevention (DLP) policies. Creating and implementing a policy is a way to structure your app security measures and get additional control over your data. With DLP policies and tools configured, you’re less likely to face data loss, damage, or leakage.
While creating a policy, make sure it includes various security measures and processes: application assessment, unauthorized access prevention, sharing control, data backup, malware protection, and others. To enforce your DLP policies, you can use a variety of tools (here you can read more about DLP tools and their advantages).
Protect Your Cloud Environment Against Ransomware
If a ransomware attack happens, your data becomes locked, and hackers demand money to release it. Fake apps can be a source of a ransomware attack. Apart from that, even legitimate apps can be an attack vector due to security vulnerabilities.
There are many measures you can take to stop ransomware. Traditional ways to prevent ransomware are efficient only to a certain degree. For example, arranging security awareness training reduces the probability of user error. However, the training process is expensive and doesn’t guarantee that a user will never make a slip.
That’s why protecting your cloud data from ransomware requires a multi-layered approach and specialized tools.
Automate Application Security
We’ve mentioned the importance of automation before, but it’s time to emphasize it once more. All processes can be done manually, but it’s better to automate them. Why? Firstly, you’ll save the time of your IT specialists. Secondly, automated tools reduce the probability of human error while managing cloud data.
What automation tools are there? Generally, app security functionality is often included in CASB services. Also, there are specialized solutions. For Microsoft Office 365 users, there is a native solution—Cloud Apps Security. What’s about Google Workspace (former G Suite)? The users should rely on third-party tools for Google Workspace to get advanced visibility and control over their cloud apps.
Was this helpful?
Latest blog posts
How to Create an Effective Cybersecurity Risk Assessment Matrix
Article Summary: This article explores how to create a cybersecurity risk assessment matrix to identify,...
Securing the Gateway: How Browser Extension Risk Assessment Protect...
Browser extensions are a normal component of today’s modern web browsers. They serve the purpose...
How to Restore Outlook Emails: A Step-by-step Guide
Article Summary: This guide provides a detailed, step-by-step process for recovering deleted Outlook emails, whether...