Complete Offboarding Checklist To Preserve Data Security

One of the critical business processes in that organizations must give due diligence from a security and compliance perspective is employee offboarding. Failing to take care of this crucial process could potentially leave data accessible by former employees and can open your businesses up to all kinds of compliance violations. Therefore, companies need to execute an offboarding checklist that helps ensure all the appropriate offboarding procedures are accomplished promptly after an employee’s departure.
Risks associated with improper employee offboarding
Let’s focus on risks associated with improper employee offboarding and what security and compliance challenges can result. Note the following:
- Lost data
- Compliance and regulatory violations
- Stolen data
- Confidentiality breach
- Overspending
Let’s take a closer look at how each of these detrimental outcomes can happen with improper employee offboarding.
1. Lost data
Leaving access available for employees that have recently left the company can lead to all sorts of data security risks, including data loss. In addition, depending on how and why an employee left the company, emotional elements can lead to a former employee intentionally causing data loss that they know will make things difficult after their departure.
Sometimes, due to “imposter syndrome” or other feelings, a departing employee may want the company to feel their absence as much as possible. Deleting data, documentation, and additional information serves this purpose. Needless to say, improper employee offboarding can undoubtedly lead to cases of data loss by disgruntled or unscrupulous employees.
2. Compliance and regulatory violations.
Compliance and regulatory violations can cost your business dearly. Today’s compliance regulations have real “teeth,” and the fines that can be leveraged from a compliance violation involving gross negligence are not trivial. Today’s most stringent compliance frameworks include:
- General Data Protection Regulation (GDPR)
- Health Insurance Portability and Accountability Act (HIPAA)
- California Consumer Privacy Act (CCPA)
- Payment Card Industry Data Security Standard (PCI-DSS)
- Personal Information Protection and Electronic Documents Act (PIPEDA)
3. Stolen data
Departing employees can also cause harm in another way, stolen data. Instead of causing data loss, an unscrupulous employee may take data with them. In addition, they may leave one company to join the ranks of the competitor and attempt to download as much information as possible to have advantages in their new role. This information may include proprietary or intellectual property, customer information, or other sensitive data.
Typically, employees on their way out may attempt to take data with them before their last day of employment. Therefore, in addition to proper offboarding processes to help curtail stolen data, organizations must have other cybersecurity measures in place.
4. Confidentiality breach
Closely tied in with data loss, stolen data, and compliance violations, confidentiality breaches can happen when former employees have access to sensitive or confidential information that may lead to the data being exposed improperly. It can also happen without malicious intent if the employee still possesses sensitive data and inadvertently exposes it.
It emphasizes the need for organizations to reclaim all company-owned electronic devices, revoke access to sensitive information repositories, and follow through with all the items on their offboarding checklist to preserve data security.
5. Overspending
Most organizations today are utilizing cloud Software-as-a-Service (SaaS) environments that are billed on a subscription basis. As a result, businesses can inadvertently allow dozens of accounts or more in larger organizations to accumulate without ending the subscriptions for cloud SaaS environments like Google Workspace and Microsoft 365.
While each individual subscription may represent minimal cost, the cumulative spend on cloud SaaS accounts, storage, and respective services can add up. When employees are appropriately offboarded, services are de-provisioned, and license costs are kept to a lean stance in the overall pool of subscription services.
Complete offboarding checklist to preserve data security
A lack of employee offboarding is extremely dangerous to business-critical data and an organization’s compliance stance. Former employees must be offboarded correctly. It limits the danger to both the employee and the company. When it comes to offboarding, businesses need to follow a thorough offboarding checklist to help preserve data security and bolster compliance objectives. What should be included in an offboarding checklist?
Consider the following points:
- Keep the lines of communication positive
- Communicate the departure with the team
- Conduct an exit interview
- Recover corporate assets
- Control email forwarding and file sharing
- Reset shared passwords
- Migrate data between accounts
- Revoke application access
- Reassign or discontinue cloud SaaS licenses
1. Keep the lines of communication positive
One of the things that can quickly sour the relationship between exiting employees and their current employer is negative talk regarding their move. Instead, be positive and supportive, and ultimately, congratulate them on their next move! Keeping the communication positive will help engender feelings of goodwill on both sides. In addition, if there were any tendency towards any unscrupulous activity on the part of the exiting employee, any negative interactions would make this behavior more likely.
2. Communicate the departure with the team
Fellow teammates should be made aware of the departure of an exiting employee. It helps to make everyone aware of this future event so they can begin curtailing any sharing of sensitive information and communications with them. Undoubtedly, the employee will already have access to information that would be sensitive. Therefore, it is wise not to add to this store of data or information shared with them late into their notice period. It also helps fellow team members to be vigilant of any strange behaviors, activities, or requests from the exiting employee.
3. Conduct an exit interview
The exit interview is a critical part of the overall offboarding process. It allows the employee to leave on good terms, air any challenges, issues, or grievances they may have, and provides a critical opportunity for proper security processes. In addition, at the exit interview, employees can return company devices in their possession, such as laptops, mobile devices, tablets, key fabs, etc. The employer can also get their contact information to reach them after their last day if that is possible.
4. Recover corporate assets
Recovering corporate assets deserves a spot on the checklist as its own process. However, even though it may be part of the exit interview, some organizations may not retrieve assets at this stage. In addition, with many employees working remotely or as part of the hybrid workforce strategy, it may not be possible to return these in person at the exit interview. Therefore, businesses need to have processes to take care of this aspect of the offboarding process, even if the employee works remotely.
5. Control email forwarding and file sharing
Another item on the offboarding checklist that organizations need to give due diligence on is disabling the means of data exfiltration. Two of the easiest ways for data exfiltration are email forwarding and file sharing. Especially when using cloud SaaS environments with the easy ability to share data and copy data, it can create enhanced risk for data exfiltration happening with exiting employees.
Unfortunately, businesses often start thinking about data leaks when offboarding employees. However, organizations must have technologies for all employees to control a possible Microsoft or Google data leak, including data shared outside the cloud SaaS environment, notwithstanding the offboarding process.
6. Reset shared passwords
Users in the organization may have access to shared passwords. For example, suppose an exiting employee can access shared passwords for business-critical resources and services. In that case, password resets for these shared accounts need to happen to maintain security for the service or solution.
7. Migrate data between accounts
Another issue that comes up quite often when an employee leaves is data in their cloud SaaS accounts. Businesses will often maintain unused accounts simply due to the data those accounts contain. As a result, IT may be reluctant to remove the accounts of former employees for fear of critical services tied to the account or business-critical data housed in their cloud storage accounts.
Organizations can be challenged with migrating data from one account to another. So, the easier path is to leave the account. However, as mentioned earlier, it leads to additional spending on unused accounts simply due to the data they contain. With the right technology tools, businesses can migrate critical data from an existing account to the new account of the employee stepping into the role or another designated individual.
8. Revoke application access
Revoking application access as part of the offboarding process is extremely important. Leaving application access open to former employees opens the door to critical security and compliance issues. It can lead to a breach of confidentiality, data leak, and even fines related to compliance violations.
Revoking application access ensures the former employee cannot access critical applications with sensitive data exposed to someone who is no longer with the company.
9. Reassign or discontinue cloud SaaS licenses
We have already alluded to this task in previous points on the list. Reassigning or discontinuing former employees’ cloud SaaS licenses helps keep the spending on cloud SaaS services lean. It ensures the business is not maintaining unneeded SaaS licensing on old, unmaintained accounts. With the right tools to migrate cloud SaaS data between accounts, it is no longer necessary to keep old accounts around to access the information they contain.
Offboard your employees securely with SpinOne
SpinOne helps bolster the offboarding checklist to preserve data security
Properly offboarding employees with cloud SaaS accounts can be a challenge. It is especially true since cloud SaaS environments like Google Workspace and Microsoft 365 lack the seamless tools needed to migrate data between accounts. In addition, companies often find the security and compliance tools challenging to manage or lacking in features, especially with many subscription levels.
SpinOne is robust data protection and security solution providing the technical tools and capabilities organizations need to migrate data of former employees and the necessary security tools to protect against data exfiltration. Note the following features that help businesses bolster their employee offboarding and improve their cybersecurity posture:
- Cloud SaaS backups with the ability to migrate data – With SpinOne, businesses can easily back up the data in one account and migrate the data to another account in the organization. This capability helps to eliminate the need to keep former employee accounts to retain access to the data.
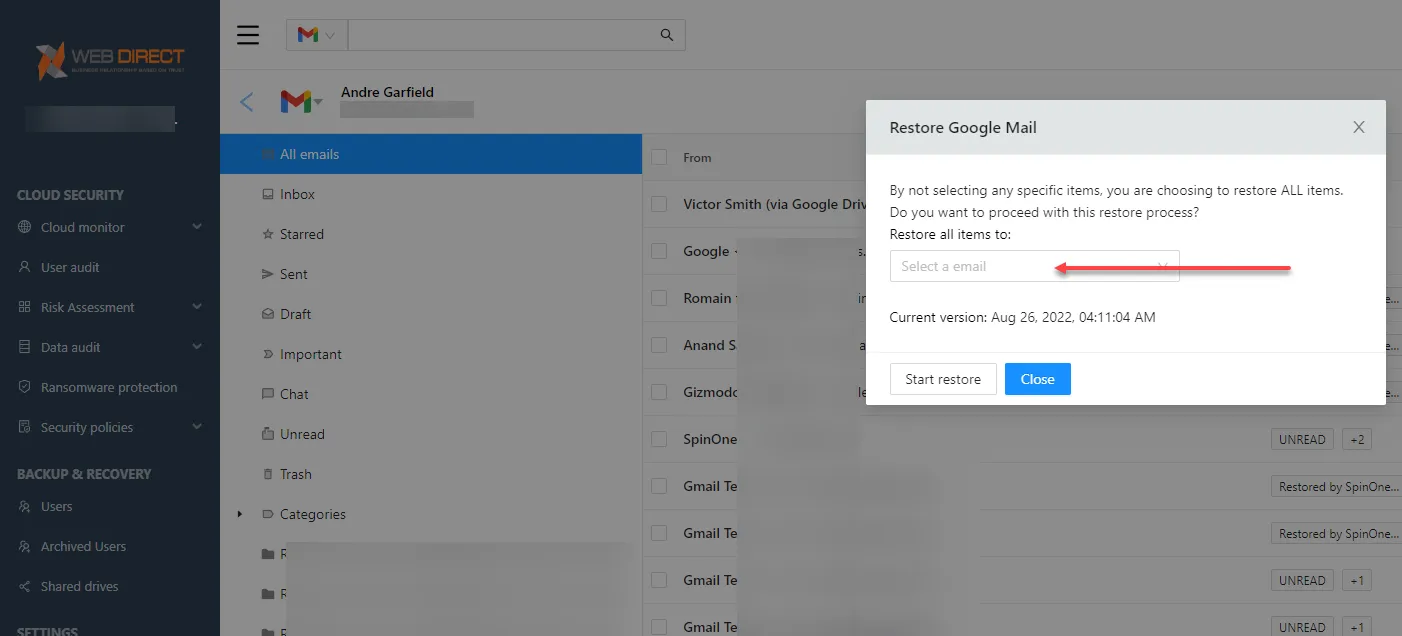
- SpinOne enables easily migrating cloud SaaS data between accounts
- Data Leak Prevention – With SpinOne, admins can see where data is shared inside and outside the organization. It also provides the technical tools needed to block information sharing to eliminate data exfiltration
- Visibility to sensitive data access and transmission – Effectively see sensitive data access in the organization and any sensitive transmitted outside the organization.
- Event Logging – See any data sharing, revoked sharing permissions, files edited, deleted, and permissions changed instantly
- Cloud SaaS application control – Define the organization policy of which cloud SaaS apps are allowed for an organization and prevent users from downloading and integrating any cloud SaaS apps or browser plugins in the organization not defined in the allowlist.
- Audit logs and active history – SpinOne provides a full list of audit logs for the Spin solution and the cloud SaaS environment, so you have a full history of activities for compliance purposes
In addition to the tools provided by SpinOne bolstering employee offboarding, it provides a next-generation cybersecurity solution that helps protect the cloud SaaS environment from modern threats, such as ransomware, shadow IT, and other insider threats.
Learn more about the SpinOne solution and how it can help bolster your offboarding processes and cybersecurity posture here: Enterprise ransomware protection and apps security solutions (spin.ai)
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
What You Need to Know About AT&T’s Data Breach and How t...
Arguably, it is one of the worst breaches that has happened recently. AT&T disclosed in...
Lessons from the Twilio Breach: Securing SaaS Applications Against ...
Another recent security breach has made organizations think yet again about SaaS apps they may...
Unpacking the CrowdStrike Outage: Causes, Impacts, and Protecting Y...
A major global IT outage occurred on Friday, July 19, 2024, causing widespread disruptions across...


