Guide to Detect and Prevent Insider Threats in the cloud
Cybersecurity is one of the words businesses need to take seriously today. Organizations that let their guard down quickly understand just how devastating the consequences can be for their business. These include ransomware attacks, data leaks, double extortion, damaged business reputation, and the potential for further repercussions for years to come. While organizations often think about cybersecurity threats that originate outside the organization, and rightly so, there is another type of threat that can be equally sinister and can lead to all kinds of security issues for companies – insider threats. In this guide to detect and prevent insider threats in the cloud, we will look at this type of cybersecurity threat and how organizations can successfully defend against this dangerous threat to their business-critical data.
What are insider threats?
Unlike attacks from a ransomware gang or other threat actors on the outside, insider threats come from the very heart of your business, your own employees. This description may be a bit perplexing as many may assume that cybersecurity threats are only those on the outside of the organization. However, in looking at threats to your data, insider threats can arguably be more dangerous to your data than threats coming from the outside.
Insider threats are extremely dangerous since insiders already have legitimate access to business-critical systems, including cloud SaaS environments. Also, they have familiarity with critical systems and data locations. So, combined, they already have what it may take an attacker months to gain – high-level access and knowledge of the systems inside the network.
Worse yet, an insider threat may include a privileged user who may have administrator access to specific systems and has all the means to perform damage to your data. With this level of access, a user may have unfettered access to databases, files & folders, internal sites, sensitive data, email systems, network administration, or any other systems.
The statistics are clear that insider threats are not slowing down. For example, one report found the cost of addressing an insider security problem increased by 34% to $15.38 million in 2022, up from $11.45 million in 2022. It is easy to see how insider threats have the potential to be some of the most devastating attacks organizations can suffer. However, insider threats can come in many different forms. So, what are the different insider threat types?
Insider threat types
There are several types of insider threats. It is important to note that with some insider threats, there may not always be malicious intent. However, the results can be very similar. Note the following types of insider threats that can bring about tremendous damage to your business.
- Not malicious but negligent employees
- Collaborators with attackers
- Malicious insiders
- Third-party contractors or partner organizations
- Credential theft
1. Not malicious but negligent employees
The first category is prevalent. Employees with no malicious intent may inadvertently cause data loss or data leak for the entire organization. How is this possible? All of us as users are subject to making mistakes and having moments of negligence or bad judgment. Additionally, organizations with insiders that fall into this category may not invest in proper cybersecurity training for end-users.
A recent post cited staff negligence as a major reason for insider security incidents. In citing findings from the Ponemon Institute survey, 56% of insider-related incidents are caused by a negligent employee. In addition, 26% of incidents were linked to criminal activities, while 18% were caused by theft of employee credentials.
What are examples of negligent employees causing damage to an organization? Examples include an employee accidentally sharing sensitive information from a cloud SaaS environment to many recipients outside the organization, inadvertently installing a malicious cloud SaaS application allowing ransomware to infect and hold business-critical data hostage, or an employee deleting the wrong data from a file share. All of these events could lead to devastating consequences for the business.
2. Collaborators with attackers
Due to the influence of the dark web and the lure of easy money, some insider threats come from users who conspire with attackers on the dark web to carry out malicious activities inside an organization. Users who collaborate with attackers may become involved in fraudulent activities, steal intellectual property, or help attackers gain access to critical systems. While this type of insider threat is one of the less common types of threats that organizations deal with, it is still a significant cybersecurity risk.
3. Malicious insiders
The third type of insider threat comes from the all-out “malicious” employee. This type of insider threat carries out malicious activities knowingly and deliberately. They may be enticed by the lure of getting their hands on sensitive or intellectual property that could be richly rewarded by competitors or those on the dark web. Others may be disgruntled or upset at specific individuals in the management hierarchy or their direct supervisor.
Whatever the case, malicious employees are extremely dangerous since they likely carry out their activities covertly and slyly, making them very difficult to detect. They can inflict untold damage on an organization by intentionally leaking critical data, compromising sensitive systems, or smuggling intellectual property out of the sanctioned environment.
A high-profile example of a disgruntled employee attempting to inflict as much damage as possible was Han Bing, a former database administrator for Lianjia, a Chinese real-estate company. He used administrator privileges to access the financial system and delete all stored data from two database servers and two application servers—this crippled Lianjia’s operations for some time.
4. Third-party contractors or partner organizations
Organizations may not consider third-party contractors or partner organizations a risk or threat until a breach or another security incident occurs. However, businesses must maintain visibility of the activities and access of any third-party contractor or partner organization. When third-party contractors or partners are brought into the organization, they are granted access to various resources. Anyone working as a third-party contractor or partner organization could fall into the abovementioned categories.
In the Ponemon Institute survey conducted among 1000 IT professionals that have experienced a cybersecurity incident due to an insider threat, staff or contractor negligence accounted for roughly $6.6 million in damages due to insider threats directly resulting from their involvement.
5. Credential theft
The final insider threat to discuss is credential theft. Attackers commonly try to compromise legitimate user credentials, providing an easy path into critical business systems. While stolen credentials aren’t really the legitimate user trying to carry out malicious activities, an attacker possessing legitimate credentials can do the same things that a malicious insider can do. Moreover, compromised credentials can be tough to detect as the user activity may appear to be just legitimate user activity.
According to the IBM Cost of a Data Breach Report 2021, breaches caused by stolen/compromised credentials took the longest number of days to identify (250) and contain (91) on average, for an average total of 341 days.
How do you know if you are at risk for an insider threat?
There are many signs that your organization is ripe for falling victim to an insider threat.
- Your organization may not be properly training end-users to recognize cybersecurity risks or understand the compliance laws and regulations that affect the business
- There are weak passwords in use in your organization, and you do not enforce multi-factor authentication
- You have cloud Software-as-a-Service (SaaS) environments that lack controls or policies in place to prevent users from sharing sensitive information outside the organization or installing potentially malicious apps
- There is no consistent policy regarding device usage and securing end-user devices with endpoint security and using other security standards, such as device encryption
- Employees are allowed to copy data from sanctioned business cloud SaaS environments to personal cloud SaaS solutions and storage
- You have no controls in place to discourage Shadow IT
- There is no visibility or auditing of employee actions, both on-premises or in cloud SaaS environments
- You don’t have a solution to backup and protect cloud SaaS data
Protect against insider threats
Protecting against the damage caused by insider threats must be a priority for businesses dealing with modern security and compliance concerns. Addressing insider threats requires using the proper tools to monitor end-user activities and put the appropriate controls in place, including in cloud SaaS environments. Not the following considerations for protecting your organization from insider threats:
- Visibility – One of the crucial aspects of protecting against insider threats is having visibility into employee activities and actions. Businesses often lack the tools to have proper visibility into what employees are doing, which data they are accessing, and which data they are sharing with outsiders, especially in cloud SaaS environments. Proper visibility should include login activities of users, user settings updated, group memberships updated, data shared accessed and shared with others, etc.
- Policies and controls – Proper policies and controls provide the guardrails needed to protect critical systems and data. With appropriate policies and controls, end-users can’t accidentally or inadvertently perform certain actions they may otherwise be able to without proper controls in place. For example, by default Google Workspace and Microsoft 365 allow users to install any third-party apps from the respective cloud SaaS marketplaces. These default settings greatly increase the risk of Shadow IT in the environment, malicious apps, and the potential for data leaks with insecure or “leaky” apps.
Detect and Prevent Insider Threats in the cloud with SpinOne
The ability to detect and prevent insider threats in cloud SaaS environments is crucial as most businesses leverage cloud environments and store large amounts of critical data in the cloud. Moreover, many organizations face challenges when using native security tooling in cloud SaaS environments and find these missing features and functionality.
The SpinOne platform is a next-generation cybersecurity solution empowered with artificial intelligence (AI) and machine learning (ML) that monitors your cloud data, detects abnormal behavior, and notifies your security team or cloud SaaS administrator. SpinOne provides the critical visibility needed to discover insider threats and malicious end-user behavior, such as abnormal data downloads, inappropriate data sharing, compromised logins, and other user actions.
Note the following data audit features found in SpinOne:
- View all data shared in the cloud SaaS environment
- View ownership of files
- See which users shared which data and who it is shared with
- Use SpinOne security policies to apply rules to files based on
- Discover sensitive information such as credit card numbers (CCNs) shared using email
- View and sort data by an individual
- Generate data audit reports and export the audit reports as needed
SpinOne provides all the above features in a simple and easy-to-use Data Audit dashboard.
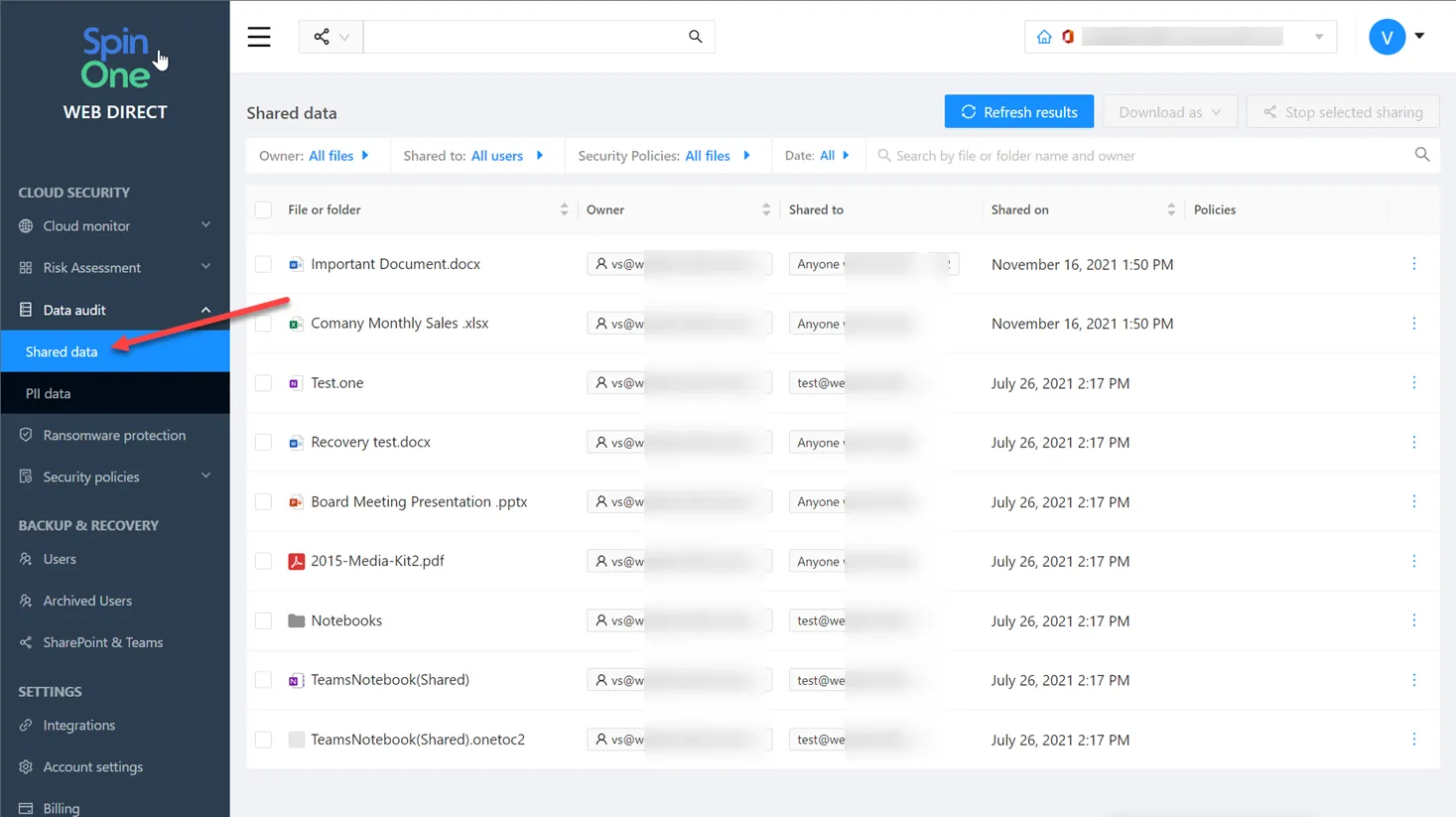
The SpinOne Activity log provides full visibility to cloud SaaS activities and SpinOne-specific activities.
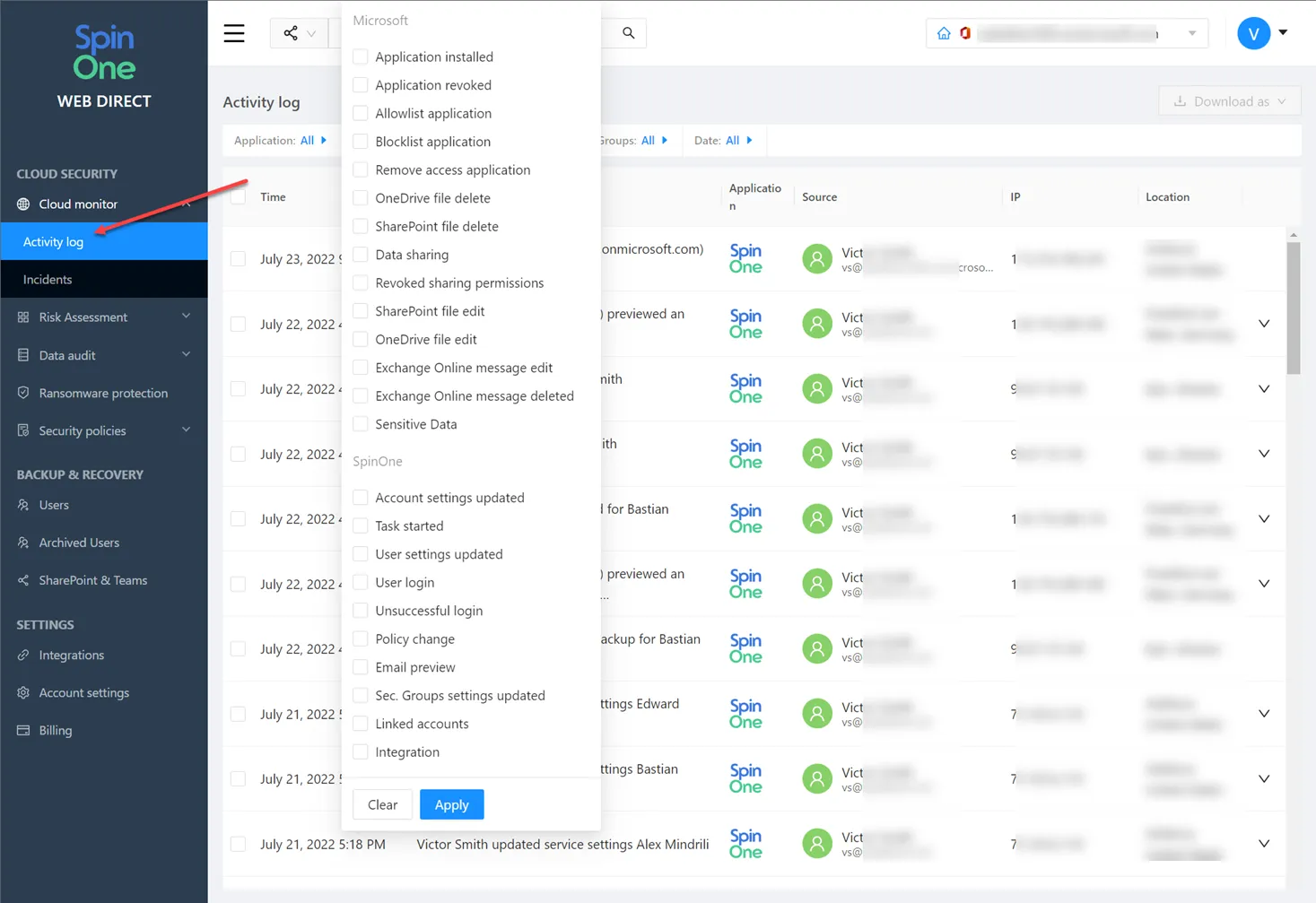
Using SpinOne, businesses have full visibility and control over third-party cloud SaaS applications used in the cloud SaaS environment, including fully automated risk assessment capabilities. Organizations can use the automated risk assessment to create security policies to enforce which apps can be installed in the environment, effectively eliminating Shadow IT activities and malicious cloud SaaS apps.
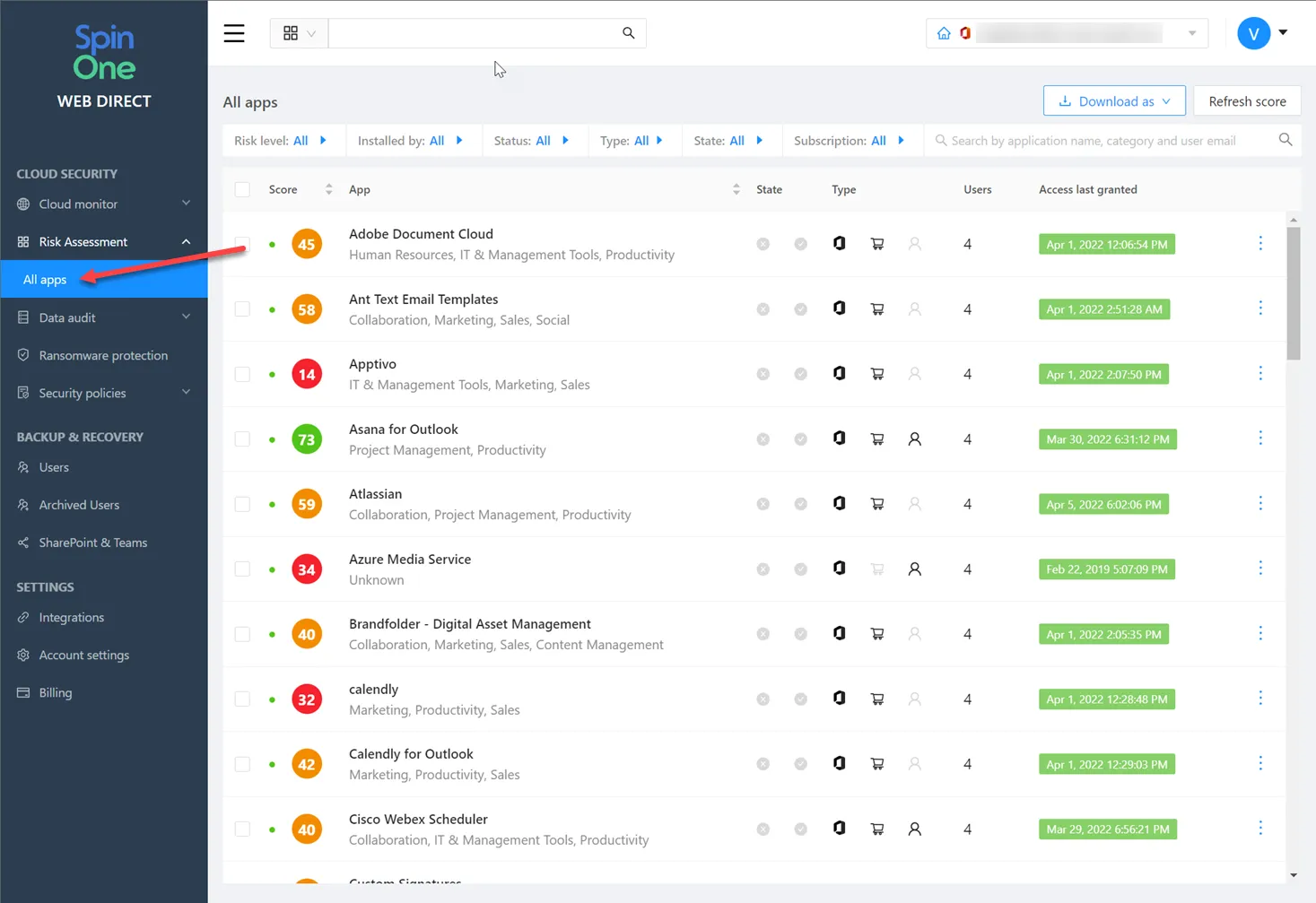
Using the built-in features and capabilities provided by SpinOne, organizations have the security and protection tools needed to combat the insider threat risk in cloud SaaS environments. In addition, it provides the visibility and controls required to bolster the cybersecurity posture of SaaS environments, helping to discover inappropriately shared resources and control data sharing altogether, along with the complete visibility of actions and events using the SpinOne cloud monitor.
We have only scratched the surface of the functionality offered. Learn more about SpinOne and how it can help you protect your organization from insider threats, ransomware, data loss, data leaks, and many other security concerns here:
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


