How to Bolster Compliance with SaaS Security Automation
A pressing challenge for businesses today in addition to SaaS security is compliance. No matter what industry or business sector, most organizations today fall under some compliance regulation. Compliance regulation frameworks serve a positive purpose for the people and data they protect. However, they can present challenges for businesses required to comply with them.
One of the challenges businesses have with compliance is having the right tools to comply with the various best practices and security requirements outlined in compliance frameworks. It is especially the case in cloud SaaS environments where many businesses struggle to control and secure their data. What cloud SaaS compliance issues do businesses face with user activity, cloud SaaS applications, and data access? How can companies bolster compliance with automated security processes?
What is compliance and why is it important?
Compliance frameworks are created to help establish a set of standards and requirements that are deemed essential. They are created and mandated by recognized governing bodies that decide the requirements of a particular compliance framework and its enforcement.
Compliance frameworks and their associated regulations help businesses manage risk acceptably. However, these serve other valuable purposes. These include protecting businesses and their reputations and customers and their data. Whereas early on, compliance frameworks offered suggestions and guidelines, today’s modern compliance frameworks enforce costly fines and penalties for organizations in violation of various compliance regulations.
For example, the General Data Protection Regulation (GDPR) provides some of the most severe penalties of modern compliance frameworks. For especially severe violations listed in Art. 83(5) GDPR, businesses can be fined up to 20 million euros, or in the case of an undertaking, up to 4 % of their total global turnover of the preceding fiscal year, whichever is higher.
Generally, businesses that fall under the oversight of compliance frameworks must undergo regular compliance audits. During the audit, the company must demonstrate they meet the requirements outlined by the compliance framework. It emphasizes the need also to have proper auditing and reporting capabilities as compliance auditors generally request certain reports as part of compliance audits.
What compliance issues are businesses facing in cloud SaaS security?
Compliance and security go hand-in-hand. If an environment has security issues, there will also certainly be compliance issues. When it comes to Information Technology, one of the primary goals of compliance regulations is to ensure data security.
It can be challenging for organizations to properly implement security and, in turn, compliance in cloud SaaS environments. Why is this the case? The security of organizations who migrate to cloud SaaS environments can suffer from a lack of visibility and control in key areas, including:
- User activity
- Cloud SaaS applications
- Data sharing and access
Why are these areas important for ensuring proper data security, and by extension, compliance?
User activity
For proper securing of business-critical and sensitive data that falls under the purview of compliance regulations, businesses must have visibility into user activities that may create security or compliance issues.
For proper compliance and compliance auditing, businesses need to know when users are accessing the cloud SaaS environment, what applications they use most, and when. They also will want to know how they connect, from what IP address, country, or city. IT admins should be alerted when there are abnormal logins or brute force attacks against your organization.
Cloud SaaS applications
Cloud SaaS applications can introduce tremendous security and compliance risks in your cloud SaaS environment. While legitimate and reputable cloud SaaS applications can extend the features and capabilities of cloud Software-as-a-Service environments, they introduce risks associated with enabling third-party access to your data.
Additionally, malicious third-party applications and browser plugins granted permissions to the environment can delete, steal, leak, and ransomware your data. As a result, organizations must audit cloud SaaS applications closely and control which applications can access business-critical data. By default, users can install and integrate cloud applications at will. With a simple OAuth permission prompt, users can grant access to a third-party application, which could be malicious.
For compliance and audit purposes, organizations need to have visibility, control and reporting on which applications are accessing which data.
Data sharing and access
A tremendous security concern for organizations is sharing business-critical and potentially sensitive data. Like installing third-party applications, cloud SaaS environments make it easy for users to share data, both internally and externally.
Users can accidentally share sensitive or other confidential data outside the environment with little effort. It underscores the need for organizations to maintain visibility to data sharing in their cloud SaaS environments, especially any data sharing containing sensitive information, and audit access.
Take control of your compliance with SaaS Security automation
As we have described, much of the challenge with cloud SaaS compliance lies with having visibility, controls, and reporting capabilities. SpinOne is robust data protection and security solution that takes the heavy-lifting out of compliance challenges in cloud SaaS.
Using SpinOne, organizations have visibility into user activity, cloud SaaS application use, and data sharing and access. Using the SpinOne Cloud monitor Activity log, IT admins can quickly see user activity from the cloud service provider and SpinOne policies. Administrators can also select any of the events and download these for reporting and documentation purposes.
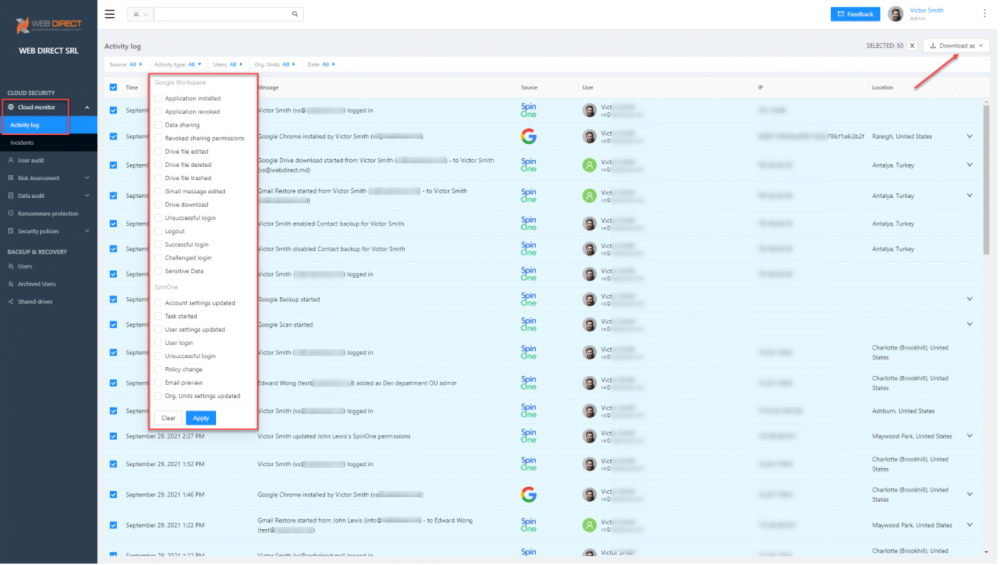
Spinone Cloud Monitor User Activity dashboard
With SpinOne, it is easy to audit third-party applications in your cloud SaaS environment. The Risk assessment dashboard includes visibility to all apps and automatically assigns a risk score to the application based on reputation and behavior metrics. Admins can approve or decline applications. Also, these can be downloaded for compliance documentation as needed by auditors. Note how you can refresh the application risk score. SpinOne continuously audits application risk, even for trusted applications.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


