How to Close Security Gap of Evolving Cloud Ransomware
It can be one of the most feared words in cybersecurity – cloud ransomware. Ransomware is arguably one of the most successful and lucrative malicious tools used by hackers today. It does not discriminate or show mercy to victims. What is more worrisome is it is evolving. New strains and variants of ransomware are continuing to pop up with new features and capabilities.
Many of the new malicious features in ransomware are now targeting cloud SaaS environments. Attackers are following businesses as they are migrating to cloud SaaS environments in droves. As organizations migrate to cloud SaaS, they have to consider evolving cloud ransomware and protect business-critical data accordingly.
Evolving cloud ransomware
Compared to the early days, modern ransomware variants are much more sophisticated, robust and use new and more sinister ways of forcing victims to pay ransom demands. In addition, new ransomware variants also include cloud awareness and capabilities.
For business-critical data, it means you have to be “on your toes” to ensure you are protected from ransomware, regardless of whether data exist on-premises or in the cloud. Unfortunately, cloud ransomware is real and in the wild already. So how can cloud ransomware encrypts organization data in cloud SaaS environments without file shares and other legacy attack points often used on-premises?
Cloud ransomware attacks can happen quickly and quietly using technologies that power applications integration. Let’s note the following scenario in a Microsoft 365 environment:
1. A user receives an email from “Security Team” with the subject of “Important Notice.”
2. The user notices no misspellings or other obvious cues that might indicate the email is not legitimate.
3. After clicking on the link in the email, it takes the user to a very familiar “permissions required” dialog box. It requests a common set of permissions that are not entirely unusual – read and write access.
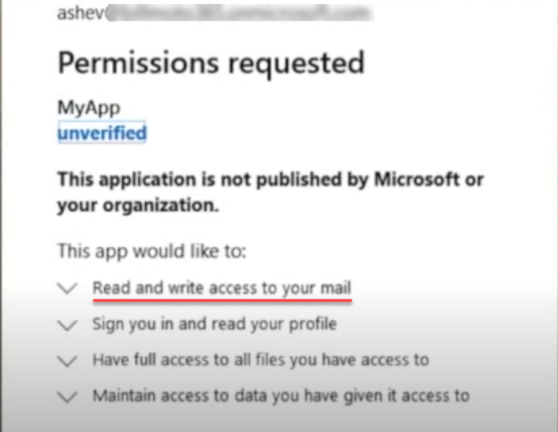
A malicious program requesting read and write permissions
4. The user clicks the Accept button
5. What has actually happened is the user has given permissions to the hacker’s ransomware application.
6. The hacker can now see all of the user’s emails. He can read, delete, steal information, or use the malicious application to start a ransomware attack.
7. After the hacker initiates the ransomware trigger, the user’s email is encrypted in real-time, one by one. In a few seconds, the user receives another email from the “Security team.” It reads, “if you want your data back, you will need to make a payment.”
As discussed, attackers can easily take control of a user’s data with only a few simple permissions granted. However, when receiving emails and other messaging that appear legitimate, end-users are often quick to grant permissions requested to cloud applications.
OAuth permissions delegation
Cloud ransomware abuses the technology that makes cloud permissions delegation possible – OAuth. OAuth permissions delegation is a mechanism that allows granting access to an application on “your behalf” without giving the application your password. A token is issued instead of the user password when a user grants permissions to an application. The authorization token allows the application to assume the permissions granted by the user.
This authorization model prevents the application from possessing the user’s password (which is more secure) and allows the application to carry out actions in the environment. However, in the case of a malicious cloud application, the authorization token is all it needs to carry out malicious activities.
Unfortunately, the mobile device era has conditioned most users to grant any permissions requested. Most of us are guilty of not scrutinizing the application permissions requested when installing applications on our mobile devices. The same is true of cloud SaaS environments. Most users generally assume the requested permissions are legitimate.
Attackers are playing on this prior conditioning. Making malicious applications appear legitimate and sanctioned can easily persuade end-users to grant the permissions requested. What’s worse, applications granted OAuth authorization tokens are persistent, even bypassing two-factor authentication configured on an account.
Cloud SaaS applications auditing and ransomware protection needed
Today, businesses can no longer assume applications granted permissions by users to integrate into cloud SaaS environments are legitimate and trustworthy. As a result, proactive cloud SaaS applications auditing is required to ensure each application integrating with the cloud SaaS environment is sanctioned by the business and is safe from a cybersecurity standpoint.
In addition to auditing cloud SaaS applications, businesses must have a robust ransomware protection solution. Organizations must protect business-critical data from ransomware threats proactively. Why is proactive ransomware protection needed?
Both Google Workspace and Microsoft 365 have various cybersecurity protections in place for helping to secure data. However, when it comes to ransomware, both are reactive in how they handle a ransomware attack. At best, IT admins are notified if signs of a ransomware attack are found in the environment.
Time is of the essence when ransomware attacks cloud SaaS environments. The quicker a ransomware attack can be remediated and stopped at the source, the less data will be affected. It directly impacts Restore Time Objectives (RTOs) and the sheer amount of data that needs recovering.
In addition, Google and Microsoft both are throttling API access from customers. When businesses have to recover data in their cloud SaaS environments, it requires API calls. The more data a business needs to recover, the more likely API throttling will apply, drastically impacting data recovery times.
Auditing cloud SaaS applications and enforcing proactive ransomware protection helps to ensure your business-critical data is protected from malicious threats and proactively remediate these.
SpinOne Risk Assessment and Ransomware Protection
Manually auditing cloud SaaS applications for threats is time-consuming and tedious. For example, monitoring for the signs of a ransomware infection across your entire cloud SaaS landscape using manual processes is virtually impossible. SpinOne provides a robust cybersecurity solution that allows businesses to both protect and secure their data.
SpinOne provides a robust cybersecurity risk assessment for cloud SaaS applications integrating into your cloud SaaS environment. It automatically scores applications based on intent, reputation, and other critical metrics. This assessment process is continuous. If a once-safe application begins to demonstrate malicious activities, SpinOne quickly flags it.
Auditing a single cloud SaaS application might take a SecOps professional hours to do correctly. Using artificial intelligence (AI) and machine learning (ML), SpinOne can perform the same process in seconds to minutes.
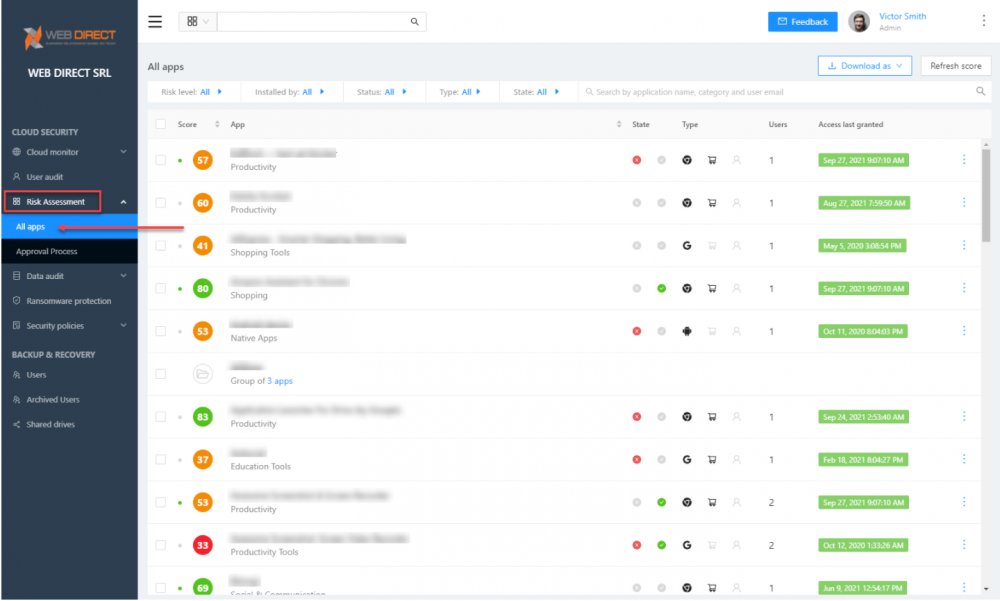
SpinOne Risk Assessment provides quick and effective risk assessment scoring of cloud SaaS applications
It provides an effective and efficient approval workflow for cloud SaaS applications.
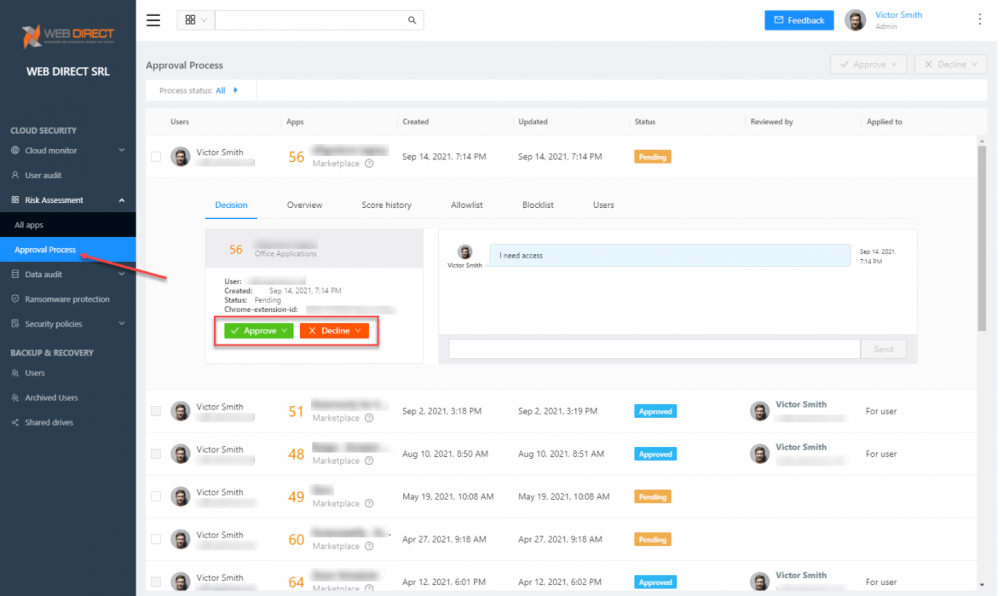
SpinOne Risk Assessment allows approving or declining cloud SaaS applications in the environment
SpinOne’s Risk Assessment scanning protects your environment from malicious cloud SaaS applications. Even if a user attempts to grant a malicious application OAuth permissions to the environment, SpinOne blocks the request.
In addition, SpinOne provides industry-leading ransomware protection for cloud SaaS environments. The Ransomware Protection module provided by SpinOne proactively monitors, protects, remediates, and notifies in the event of a ransomware attack. It does this with the following workflow:
- It continuously scans the cloud SaaS environment for signs of ransomware
- If ransomware is detected, SpinOne blocks the ransomware process at a network level
- SpinOne scans the environment for any files affected by the ransomware process
- It proactively and automatically restores any affected files using the latest version contained in SpinOne backups
- IT admins are notified
The intuitive and straightforward Ransomware protection dashboard displays any ransomware activity. It includes files affected, files recovered, when the attack started, stopped, etc.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....


