How to Develop Cloud Backup and Data Loss Protection Strategy
Protecting your business-critical data today is of utmost importance. Most organizations carry out data-driven operations and rely on critical data to be available at all times, without disruption. With this crucial requirement for data availability, businesses must have the protections and safeguards to protect against data loss for multiple reasons, including ransomware. With more critical data stored in cloud Software-as-a-Service (SaaS) environments, how can you develop a cloud backup and data loss protection strategy?
Why do you need backups in the cloud?
Cloud computing has become a game changer in terms of the productivity of many businesses. Unfortunately, it comes at a price. The new risks brought by cloud technology need a new approach. Still, some people are hesitant.
Do you really need backups of your critical cloud data? The short answer is, surprisingly, yes. Unfortunately, many admins and business stakeholders may assume cloud backups are redundant and serve no purpose in ultra-resilient cloud hyper-scale data centers. However, those assumptions are dangerous for a few reasons.
Cloud backups help to protect critical data, e.g., customer data, stored in the cloud.
While the hyper-scale cloud providers have incredibly resilient and highly available infrastructure from a hardware, network, and security perspective, you still must cover the bases of protecting your data for a few reasons. These include:
- Human error
- Ransomware
- Hardware failure
- Burden of responsibility
Let’s examine these and see how they weigh into the critical reasons for protecting your data.
1. Human error
Human error is one of the most common reasons companies need to leverage their data protection plans. It is common for a user to accidentally delete data they didn’t intend to delete or become distracted and alter or delete data unexpectedly.
Unfortunately, these data loss events can be very disruptive and negatively affect business continuity. When users are working with shared files or folders, any mishap with accidental data deletion can disrupt operations for many users, not just one. What we have described is unintentional and unintended.
Another situation involving users that can also lead to data loss is malicious or unscrupulous users. Users who feel they have been shorted by the business or have other reasons for feeling ill will can cause much damage. These so-called “insider threats” can be dangerous, difficult to detect, and cause much in the way of data loss.
No matter how resilient or robust cloud infrastructure, including cloud Software-as-a-Service (SaaS) environments, there is no built-in means to protect from unintentional mistakes or malicious insider threats.
2. Ransomware
One of the key cloud security threats today, ransomware is a particular type of malware that uses public key encryption to intentionally encrypt files and folders without your permission to “lock” these so they can’t be accessed without being decrypted. The problem is the bad guys have the key to decrypt the data. Without paying the ransom demanded, you can’t get your data back.
Ransomware can and does encrypt cloud storage locations. For example, it can encrypt cloud data such as cloud email and cloud “drives” that store organization files and present these as shared drives to multiple users. So how can ransomware affect cloud storage locations found in cloud Software-as-a-Service solutions?
There are a couple of primary ways this can happen:
- Malicious cloud applications – The attacker persuades users to install malicious cloud apps that contain ransomware. The apps appear legitimate and masquerade as official apps from known vendors. When an unsuspecting user grants a cloud OAuth token to the malicious application, the malicious app assumes the permissions granted by the user on their behalf. This authorization allows the malicious app to perform encryption activities on areas where it can access the data.
- Cloud file synchronization – Most cloud SaaS services have a file synchronization application allowing users to synchronize files from their local storage to their cloud storage location. If the user’s computer is attacked with ransomware, the ransomware will first encrypt the locally stored copies of the data. The file synchronization utility will view the changes made by the ransomware encryption to the local file copies as changes that need to be synchronized to the cloud. Once the local files are synchronized, the good copies of the files are overwritten with the encrypted copies.
3. Hardware failure
Hardware failure is one of the most prominent cloud storage security risks. Despite the redundancy of cloud data centers, failures and cloud outages can and do happen. While it is not as likely as a data loss culprit, it is still a reason to have a cloud backup strategy. Cloud service providers frequently have outages that can take down access to cloud data for hours. By backing up and protecting your data using a solid backup strategy, you can still gain access to critical data by way of your “offsite” backups in another cloud environment.
4. Burden of responsibility
One of the important reasons to develop a cloud backup strategy protecting against data loss is the burden of responsibility that falls on the customer when it comes to protecting their data. Today’s cloud service providers operate under what is known as the shared responsibility model.
With the shared responsibility model, the cloud service provider is responsible for the physical infrastructure, network, data center security, and other physical aspects of the environment. While they provide a best effort approach to protecting your data from failures and other reasons related to the physical security of the environment, ultimately, the final burden to protect the data falls to the customer.
Note the following as detailed by Microsoft:
For all cloud deployment types, you own your data and identities. You are responsible for protecting the security of your data and identities, on-premises resources, and the cloud components you control (which varies by service type).
Regardless of the type of deployment, the following responsibilities are always retained by you:
- Data
- Endpoints
- Account
- Access management
Google notes very similar details related to their cloud SaaS platform:
In SaaS, we own the bulk of the security responsibilities. You remain responsible for your access controls and the data that you choose to store in the application.
Again, for emphasis, the burden of responsibility for protecting your data falls to the customer. It means that customers need to take their cloud backup strategies seriously and develop a cloud backup data protection strategy.
How to develop a cloud backup and data loss protection strategy
A cloud backup and ransomware protection strategy are crucial to protecting your data in harmony with the shared responsibility model. Note the following steps to develop a cloud backup and data loss protection strategy.
- By all means, back up your cloud data!
- Learn from the 3-2-1 backup best practice
- Use an enterprise backup solution for cloud SaaS backups
- Control third-party applications in your cloud SaaS environment
- Use ransomware protection
1. By all means, back up your cloud data!
The first step to developing a cloud backup and ransomware protection strategy is back up your cloud data. For the reasons already listed above and many others, these cloud services are necessary to ensure you can recover business-critical data in the event of human error, ransomware attack, and cloud hardware failure. As stated, by all means, businesses need to back up their cloud data!
2. Learn from the 3-2-1 backup best practice
The 3-2-1 backup best practice has been an industry standard for quite some time. It emphasizes the need to have at least (3) copies of your data stored on (2) types of storage media, with (1) copy stored offsite. With cloud backups, the 3-2-1 backup best practice has many principles that still apply. In particular, storing a copy of your cloud data outside the cloud environment, you are protecting.
Organizations need to be careful as many cloud data protection solutions on the market store the backups of cloud SaaS data in the same cloud. In other words, your backups are stored in the same cloud as your production data. Just as you would never store your backups on the same hard drive as the data you are protecting in an on-premises environment, best practice dictates cloud backups should be stored in another cloud environment to ensure accessibility in the event of a cloud outage.
3. Use an enterprise backup solution for cloud SaaS backups
Many organizations may rely on the built-in file versioning found in popular cloud SaaS solutions like Google Workspace or Microsoft 365. However, relying on file versioning does not stick with the best practices outlined in the 3-2-1 backup best practice and can potentially lead to data loss. Cloud backup security issues are extremely rare. That’s why many experts suggest using these solutions.
Keep in mind that the shared responsibility model puts the burden of responsibility for protecting data on the customer. Since the file versioning capabilities found in Google Workspace and Microsoft 365 are part of the services offered by the cloud service provider, the customer would be leaning on the cloud service provider for protecting data and not the other way around.
Using an enterprise backup solution for cloud SaaS backups allows customers to take responsibility for protecting their cloud data. In addition, it enables storing cloud SaaS backups outside the protected cloud SaaS environment.
4. Control third-party applications in your cloud SaaS environment
In addition to enterprise backups of their business-critical cloud SaaS data, organizations need to bolster their cloud SaaS security posture by controlling which third-party applications users can install in the cloud SaaS environment. As mentioned earlier, attackers often prey on unsuspecting end-users with malicious cloud SaaS applications.
By default, cloud SaaS environments like Google Workspace and Microsoft 365 allow users to install any third-party application or browser plugin attached to the cloud SaaS environment. By removing this carte blanche approach and controlling which cloud SaaS applications can be installed in the environment, businesses can drastically reduce the ransomware attack surface in their cloud SaaS environment.
5. Use ransomware protection
Most cloud SaaS solutions offer limited ransomware protection capabilities that are reactive in nature. Using third-party ransomware protection for cloud SaaS environments is a great way to bolster the cybersecurity posture of your cloud SaaS environment. In addition, it can play an integral part in developing a cloud backup and ransomware protection strategy.
One common theme with the ransomware incident response plan is that it requires many manual tasks and steps. Unfortunately, there are just several tasks that require manual efforts with traditional infrastructure housed on-premises. However, even with cloud SaaS environments, organizations can be challenged to stop, clean up, and recover from ransomware effectively.
SpinOne – Automated cloud SaaS backups and ransomware protection
SpinOne is a cloud SaaS data protection and cloud security solution leveraging artificial intelligence (AI) and machine learning (ML) capabilities to automate and streamline cloud SaaS backups and cybersecurity in the cloud. SpinOne offers enterprise-grade cloud-to-cloud backups allowing organizations to protect their critical data effectively. What’s more, SpinOne enables businesses to choose which cloud they want to use to store their cloud SaaS backups.
Note the following capabilities:
- Automated 1x/3x a day Backup
- Multiple storage locations (AWS, GCP, Azure, custom)
- 99.9% accurate granular recovery
- Fast restoration
- Easy data management
- Archived users
- Flexible retention policies
- Centralized Admin Panel
- 24/7 support: chat, email, phone
- Compliant backup: SOC 2, EU Privacy Shield, and GDPR
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
SpinOne intelligently leverages cloud SaaS backups as a powerful component in its automated ransomware protection capabilities. The ransomware protection module provides an automated five-step response, which includes:
- An automatic cybersecurity scanner, empowered with artificial intelligence that helps detect ransomware activity automatically 24x7x365
- If ransomware is discovered, SpinOne automatically blocks the ransomware process
- It automatically identifies any files affected by the malicious process
- Files are automatically recovered – leverages the automated cloud SaaS backups
- SpinOne notifies the cloud SaaS administrator about the ransomware attack
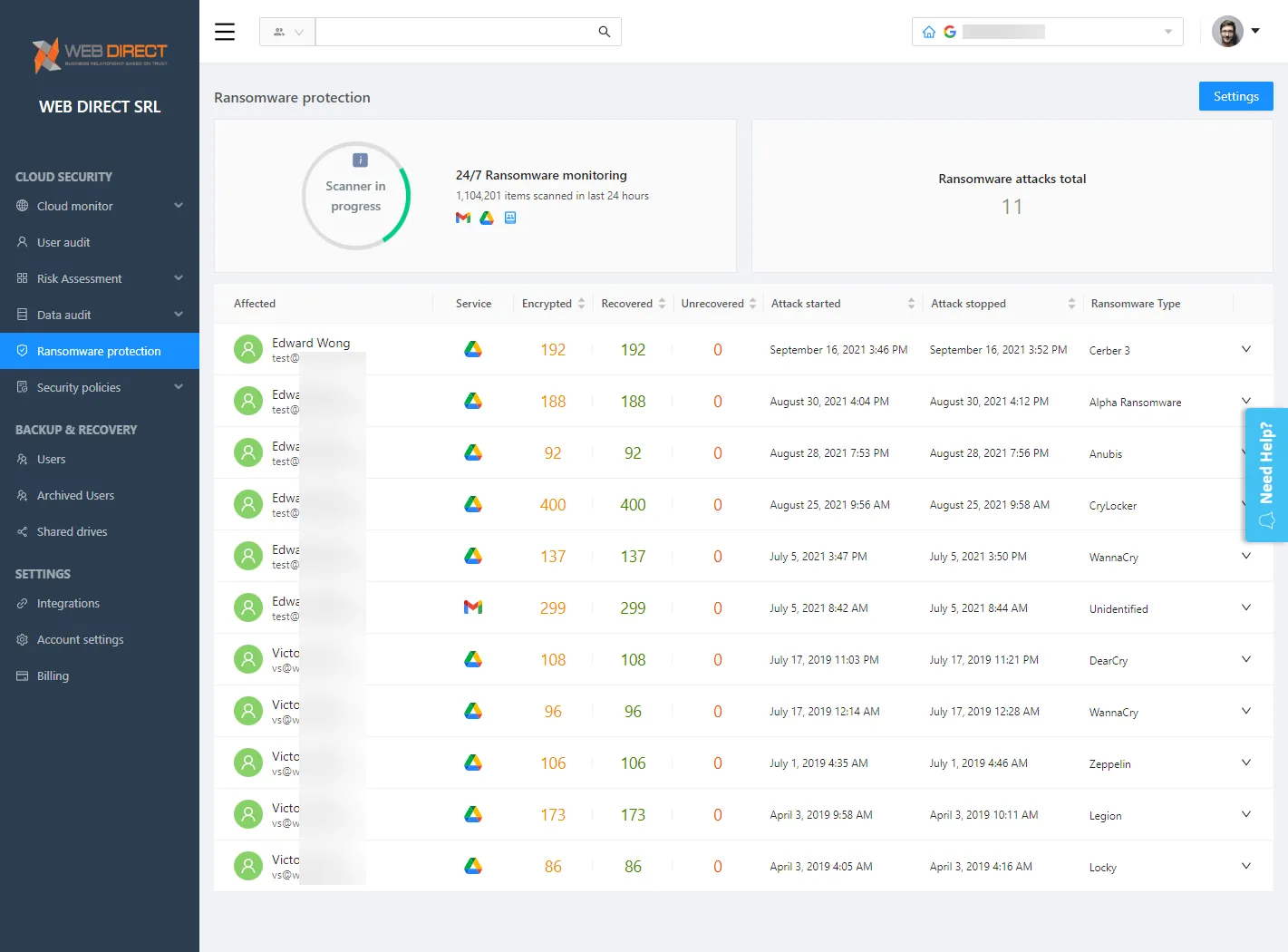
The effective combination of enterprise-grade backups and AI-assisted cybersecurity provided by Spinone helps meet the challenges of protecting against ransomware and other cybersecurity threats in cloud SaaS environments. In addition to automated backups and ransomware protection, SpinOne also includes the tools needed to monitor insider threats, third-party applications, and alerting capabilities.
- Insider threat protection – Alerts to threats from inside the organization and easily spot anomalous behaviors coming from unscrupulous employees or a potentially compromised account
- Third-party apps control – Businesses can control which third-party apps and browser extensions users can install in the cloud SaaS environment. SpinOne’s policy-based controls significantly reduce the risk of ransomware coming from malicious applications granted OAuth authorization from an unsuspecting end-user
- Alerting and Reporting – This allows businesses to easily meet compliance requirements and maintain visibility with the comprehensive alerting and reporting provided by Spin
SpinOne’s intelligent, automated cybersecurity solution helps eliminate slow and inefficient manual steps needed when ransomware attacks occur in cloud SaaS environments. Instead of taking days to recover, SpinOne enables businesses to recover in as little as 2 hours and reduce recovery costs by up to 90%.
Learn more about how SpinOne can protect your environment here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...



