ISO 27001 Checklist and Best Practices
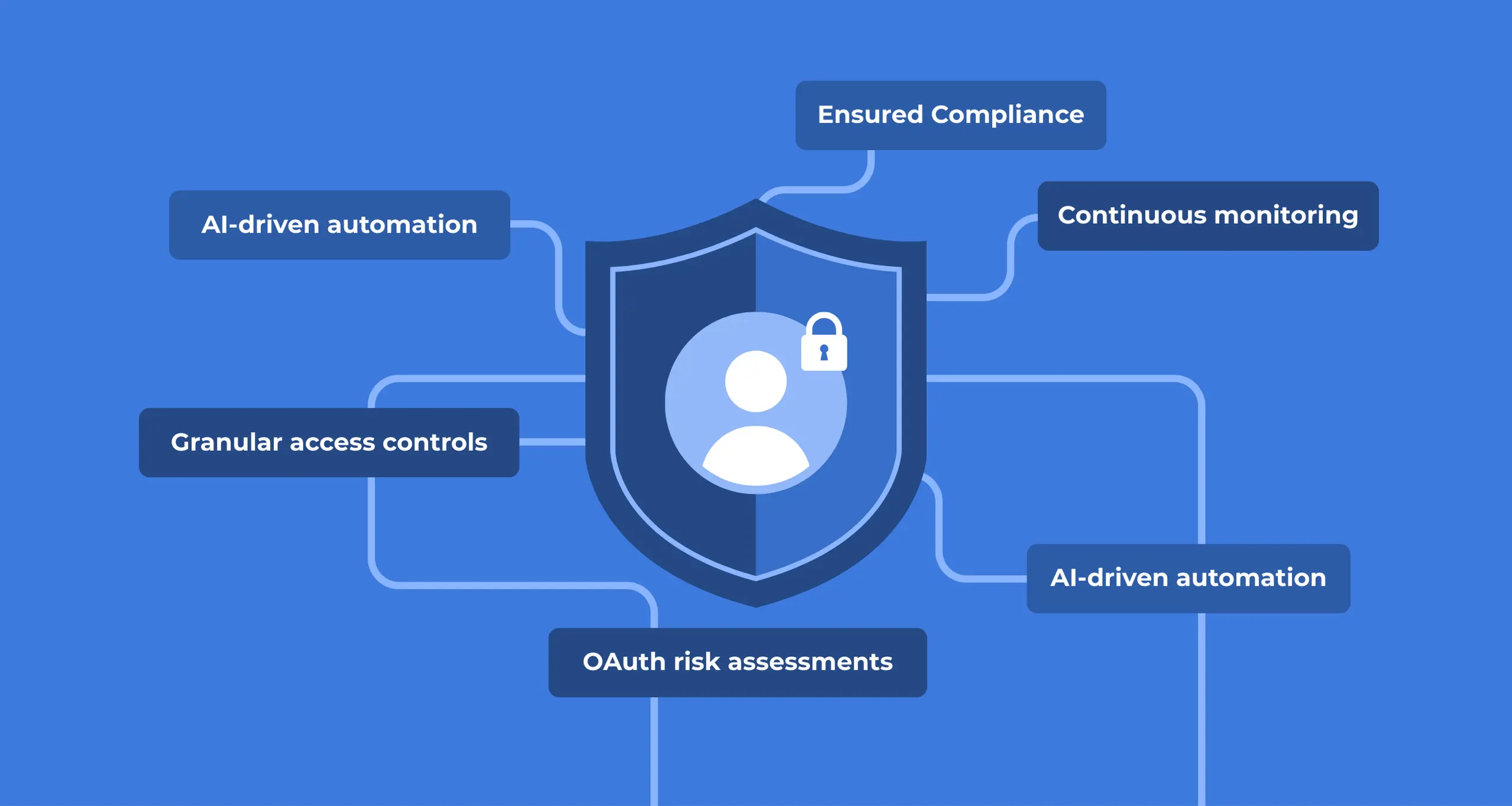
ISO 27001 is a security standard that helps organizations implement the appropriate controls to face data security threats. Completing the ISO 27001 certification process is a great business practice that represents your commitment to data security.
We hope our ISO 27001 compliance checklist will help you to review and assess your security management systems.
ISO 27001 Compliance Checklist
Firstly, it’s important to understand that ISO 27001 consists of rules and procedures rather than a precise to-do list tailored to your organization. Therefore, when we refer to a checklist, we mean a set of practices that will assist your organization in preparing to meet the requirements of the ISO 27001 standard.
ISO 27001 Checklist
Here’s our 12-step checklist:
- Understand your organization’s needs. First of all, you need a clear picture of your organization’s operations and information security management systems. This includes understanding how the ISO 27001 framework can enhance your data protection. Additionally, it’s important to identify the individuals responsible for implementing these measures.
- Define your security policy. A security policy gives a general overview of your security controls and how they are managed and implemented.
- Monitor data access. You have to ensure that your data is not tampered with. That’s why you need to monitor who accesses your data, when, and from where. As a sub-task, monitor logins and ensure your login records are kept for further investigation.
- Conduct security awareness training. Your colleagues should be trained on recognizing data security threats and how to face them to prevent your data from being compromised.
- Implement device security measures. Your devices should be safe—both from physical damage and hacking. G Suite and Office 365 have in-built device security configurations to help you.
- Determine the security of employee offboarding. You have to develop secure offboarding procedures. An exiting employee shouldn’t retain access to your system (unless it is necessary for some reason) and your company should preserve all important information.
- Encrypt your data. Encryption is one of the best data protection measures. Make sure that your information is encrypted to prevent unauthorized parties from accessing it.
- Back up your data. Backup protects you from data loss. In addition to backing up your data, you should specify the backup location, frequency, data retention period, and security measures for both on-premise and cloud backups.
- Monitor data transfer and sharing. You have to implement appropriate security controls to prevent your data from being shared with unauthorized parties.
- Conduct an internal security audit. An audit helps you to get better visibility over your security systems, apps, and devices. This will help you to identify potential security gaps and ways to fix them.
- Keep your hardware safe. You have to keep your company’s hardware (including devices) safe from various sorts of physical harm.
- Determine the effectiveness of your security controls. You need not just have your security controls, but measure their effectiveness as well. For example, if you use a backup, you can track the recovery success rate and recovery time to find out how effective your backup solution is.
How SpinOne Helps You to Protect Your Data
SpinOne is a security platform that protects your G Suite and Office 365 in real-time. Here’s what we offer to help you with protecting your data according to security standards and best practices.
- Automated backup of your G Suite/Office 365 data to the location of your choice. Backup data is stored and encrypted using FIPS 140-2 validated AES-256 encryption algorithm.
- Ransomware protection. We monitor data behavior to detect ransomware attacks and protect your data from them.
- Data audit to track download, sharing, and transfer of sensitive data stored in your G Suite. This will help you to prevent theft and unauthorized access to your data.
- Domain audit to monitor and record your domain activities, including logins.
- Audit SaaS applications connected to your G Suite to detect potential security and compliance risks they may pose.
- SaaS application risk assessment to evaluate the potential security risk of SaaS apps connected to your G Suite.
- An ability to create and customize security policies.
ISO 27001 is one of the data security standards and compliance regulations you may need to meet. Here you can read about the others.
Frequently Asked Questions
What is ISO 27001 compliance?
ISO 27001 compliance refers to adherence to the requirements and guidelines outlined in the ISO/IEC 27001 standard for establishing, implementing, maintaining, and continually improving an organization’s information security management system (ISMS).
What are the key elements of ISO 27001 certification?
Obtaining an ISO/IEC 27001 certification demonstrates to stakeholders and clients your dedication and capability to handle information effectively and securely. The key elements of ISO 27001 compliance include:
- understanding your organization’s needs;
- establishing an Information Security Management System (ISMS);
- conducting a security risk assessment;
- conducting an internal security audit;
- determining the effectiveness of your security controls;
- Conducting a certification audit
What are the key ISO 27001 requirements?
ISO 27001 consists of policies and procedures tailored to your organization, rather than precise requirements. Thus, depending on organization’s needs and complexity, the key ISO 27001 requirements include:
- defining your security policy;
- monitoring data access;
- conducting security awareness training;
- implementing device security measures;
- determining the security of employee offboarding;
- encrypting your data;
- making data backups;
- monitoring data transfer and sharing;
- keeping your hardware safe.