OneDrive Ransomware Protection Guide

Ransomware is arguably the most concerning threat to cybersecurity experts and business leaders alike. It can render business-critical data inaccessible and unusable and do this with very few indicators that anything is wrong until the characteristic ransom demand screen pops up on a client’s computer. Despite common misconceptions, cloud office suites are also infected by ransomware. In this article, we discuss OneDrive Ransomware Protection.
First of all, it is important to better understand what ransomware is exactly. Understanding how it works, how it can infect your environment, and how you can protect your valuable business-critical data, are key to successfully defeating it. Ransomware is a specialized type of malware that holds your data “hostage” and uses the demand for a ransom payment to return access to your data.
How is ransomware able to successfully “lock” you out of your own data?
Ransomware slyly infiltrates your own computer, assumes the identity of the user you are logged in with (with all the permissions and rights given), and encrypts all the files, folders, and other data to which you have access. 01 This can include all data that is stored locally, data that exists across shared network drives, and even data that is housed in your Microsoft 365 environment. Below is an example of a ransom demanded by one of the popular ransomware variants known as CrytoLocker. Many may underestimate the threat of ransomware on business-critical data stored in cloud environments, even discounting this threat altogether.
How can ransomware variants like CryptoLocker infect files that are stored in your Microsoft 365 OneDrive for Business storage?
A tremendous threat to your cloud environment is file synchronization. Most of the popular cloud SaaS offerings including Office 365 provide the ability to synchronize files stored on-premises with your Microsoft 365 OneDrive for Business storage. This allows keeping copies of files both locally and in the cloud for collaboration purposes. Cloud synchronization generally works based on detected file changes between on-premises and cloud copies of your data. If a file is updated, the file synchronization trigger is activated and the copy of the file in Microsoft 365 OneDrive storage is updated with the copy stored locally.
When the ransomware encrypts a locally synchronized OneDrive file, the ransomware encryption of a file is viewed as a simple “change” in the file and is synchronized. Thinking about ransomware, from a security and business continuity perspective, is extremely dangerous. Since OneDrive for Business storage can be shared across many users for collaboration purposes, it provides an extremely enticing target for ransomware. A single end-user who is infected with ransomware can inadvertently synchronize ransomware encrypted files to the cloud resulting in file access disruption for all users attached to shared OneDrive storage.
File Sync can propagate ransomware
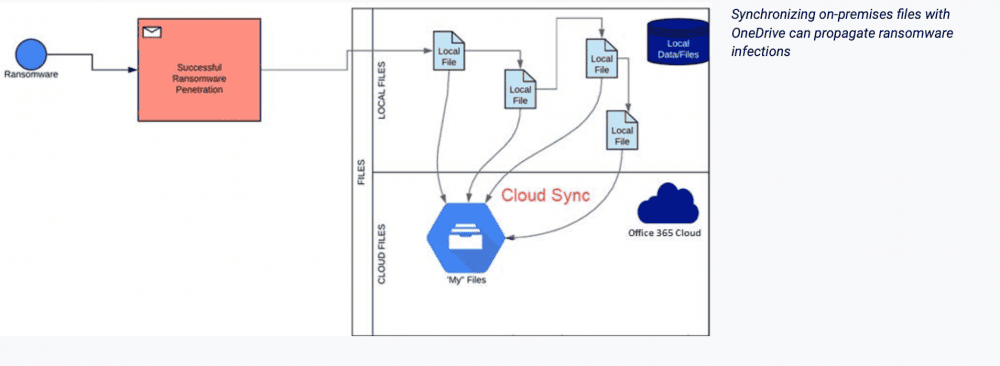
Synchronizing on-premises files with OneDrive can propagate ransomware infections
Aside from OneDrive file storage targeted by ransomware, there is another dangerous target in your Microsoft 365 environment that can cause major business continuity issues. That target is your Microsoft 365 email.
Ransomcloud
The emerging cloud security threat
Another ransomware variant that can wreak havoc on your Microsoft 365 environment does not affect OneDrive storage but rather your Microsoft 365 email. This type of ransomware attack has been named “Ransomcloud” by “black hat” turned “white hat” hacker, Kevin Mitnick who exposed this threat to the masses. Ransomcloud has been demonstrated to do what no other ransomware variant before it could. It can successfully encrypt a Microsoft 365 user email inbox so that all emails are encrypted in real-time after infection occurs.
Alarmingly, all the end-user has to do to fall victim clicks a simple “permissions allow request” to a fictitious email attachment posing as a legitimate Microsoft service. Email in most organizations is the primary communication platform. Ransomware that denies access to your organization’s email resources can certainly result in major challenges to your business continuity.
How does Microsoft 365 protect from ransomware?
Does Microsoft protect you from ransomware? Files Restore Not entirely as we will see. However, there are native tools available in your Microsoft 365 environment that can reduce the threat of ransomware and remediate its effects to some degree. Let’s take a look at the following native built-in tools to protect and secure your Office 365 environment from ransomware:
- Damaged files restore
- Ransomware detection and recovery
How does each of these mechanisms protect you from data loss? Are they enough?
Damaged Files Restore
Microsoft has included a new feature called files to restore in both OneDrive for Business and Personal editions. Files restore is a new feature in OneDrive that allows you to recover an entire OneDrive to a previous point in time within the last 30 days. This feature can recover files that have been deleted as the result of a mass file delete operation, corruption, accidental unintended file saves, ransomware, or any other catastrophic event.
The Restore your OneDrive option is found under account options for OneDrive. The interface for using files restore is fairly simple and intuitive. You can either choose a recovery date by using the Select a data dropdown menu, or you can use the slider found below.
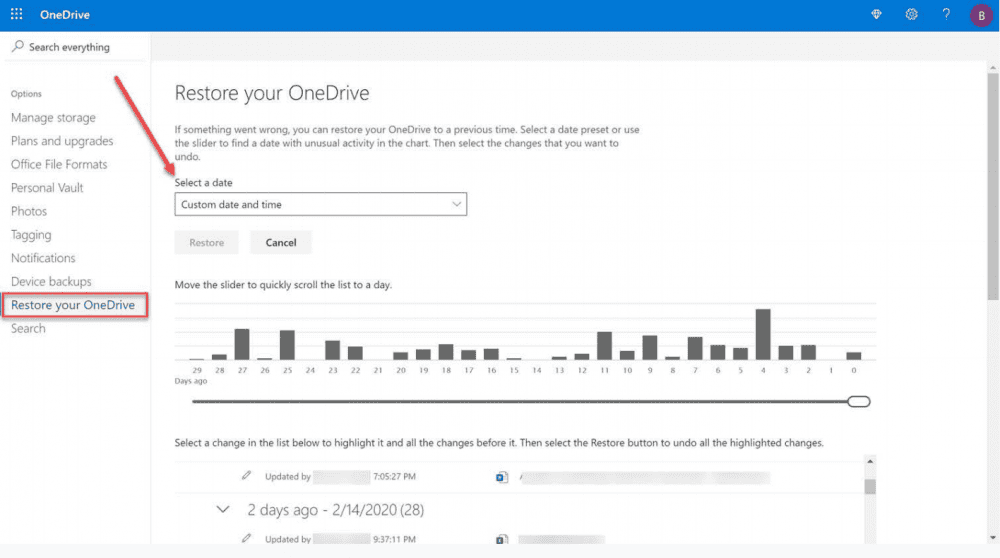
Using the Files Restore to recover files in OneDrive
The files restore capability in OneDrive is a great new feature to help recover your data from corruption as a result of a ransomware attack. Even though the files restore is a great start to native functionality that can help protect your data, it has limitations to be aware of. As mentioned above, the files restore operation can only restore files within a window of 30 days. There may be cases where data corruption or file damage may fall outside of this window of time. Think about a case where a business-critical spreadsheet is only accessed monthly.
There is no automated workflow initiated to automatically recover data affected by a ransomware
What if damage to the spreadsheet is only discovered outside of the files restore 30-day time period? Additionally, the files restore operation is a manual process. There is no automated workflow initiated to automatically recover data affected by a ransomware attack. It is dependent upon the Microsoft 365 administrator to initiate this process. When hours or even minutes count to your business, manual processes can lead to extended disruption to business continuity. Lastly, at this time, the files restore operation only covers OneDrive and SharePoint files. Microsoft 365 email is currently not protected by the files restore functionality to allow rolling an email inbox back to a previous point in time or granularly recovering specific emails. This means there is currently no protection using files restore for a “Ransomcloud” attack.
Ransomware detection & recovery in Microsoft 365 environment
Microsoft has also introduced a service that works in tandem with the files restore functionality called ransomware detection & recovery. This new capability allows Microsoft 365 to now detect ransomware attacks proactively and help facilitate restoring OneDrive to a point in time before a ransomware attack.
If a ransomware attack is detected, Microsoft 365 sends an alert via email, mobile, or desktop notification. In the notification, a link is included to the files restore dashboard with the recovery point in time automatically selected to revert files to a known good state. The process guides you through restoring files to a healthy state, before the ransomware attack.
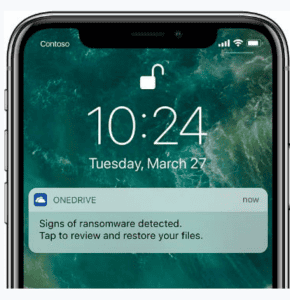
Mobile notification from Microsoft 365 of a ransomware attack (Image courtesy of Microsoft)
The new ransomware detection & recovery capability found in Microsoft 365 is a welcomed new Microsoft 365 feature that helps to speed along the process of manually restoring files using the files restore feature. However, the process to recover data relies on human intervention and using the manual steps required to roll back to a recovery point using files restore.
Native Microsoft Tools Are Not Enough
Weaknesses of Native Microsoft 365 Ransomware Tools. How to Protect Microsoft 365 from Ransomware
While the files restore tool and ransomware detection & recovery functionality are great steps in the right direction for protecting your Microsoft 365 environment from ransomware using native tools, they may not be enough. There are currently gaps in the services covered, the recovery window, and the process to recover your data using these native capabilities:
You aren’t able to recover individual files from earlier recovery points while maintaining the files that were added later. In other words, you can’t recover files selectively. After clicking restore to a specific date, files added later the recovery point will be deleted.
The possibility of recovery is only for the next 30 days until today. If the attack occurred more than a month ago and you discovered the attack later than a month ago, you won’t be able to roll back the changes and restore your OneDrive.
Data recovery doesn’t occur automatically. User intervention is always required.
Bolstering Microsoft 365 data protection and security with a capable third-party solution that provides automated protection, recovery, and security features is a must.
How to Protect Microsoft 365 from Ransomware
There are additional best practices and recommendations that can help protect your Microsoft 365 environment from the threat of ransomware. These include:
Using a cloud anti-malware solution
Effective Microsoft Office 365 security often starts with a multi-layered approach. Protecting end-user devices from malware is a necessary part of your overall security posture. This includes automatic scans, periodic file scans, automatic download of signature updates, alerting, cleaning, and other operations for end-user clients.
Exchange Online Protection (EOP) filtering and customizations
Exchange Online Protection (EOP) is on by default in Microsoft 365. Customizations can be made by each company for filtering specific email content or to block custom patterns for various content. Along with the real-time and automatic response provided by EOP, the customizations can provide great protection against ransomware.
Prevent dangerous files through email
Microsoft allows you to protect your business against ransomware even further by preventing potentially dangerous files altogether. These include Javascript, batch, and executables from being opened in Outlook.
Using Advanced Threat Protection (ATP)
Microsoft 365 ATP is an optional service that is provided in some plans or included in higher tiers of Microsoft 365. It is a filtering service that provides additional protection against specific types of malware, including ransomware. Utilizing a feature called safe attachments, it can provide much better protection against zero-day ransomware (new ransomware for which there is no known signature or pattern).
Use SharePoint Online and OneDrive for Business recycle bins
Included versioning with SharePoint and OneDrive for Business does not protect against ransomware that copies, encrypt, and then deletes the original files. In this case, the SharePoint Online and OneDrive for Business recycle bins can restore files that are up to 90 days old. If under 30 days, the files restore feature can also be used.
Actionable tips for securing the remote workforce post-pandemic
There is no question the threat landscape is more ominous than ever, and the risks to your business are certainly not trivial. What tips can help IT admins to secure the remote workforce in the post-pandemic era? Let’s consider the following:
- Secure authentication
- Protect against phishing attacks
- Visibility of user behaviors, applications, and data sharing
- Ransomware protection
- Threat automation
How to Protect OneDrive Against a Ransomware Attack
OneDrive is part of your Microsoft 365 ecosystem. To protect OneDrive from ransomware attacks, you need to take all the measures for Microsoft 365 ransomware protection we listed above. Keep in mind, that most of these methods work as prevention and they do not guarantee 100% protection against ransomware. You need a tool that will become the last layer of defense, detect and stop the attack once it has begun. Let’s talk about such tool in detail.
SpinOne, Best in Class Ransomware Protection for Microsoft 365
When the very livelihood of your business is at stake (your business-critical data), you need to use the best solution available to safeguard your data from attack by ransomware. SpinOne for Microsoft 365 from SpinOne is a “best-in-class” solution that provides the tools and capabilities needed to safeguard your data from the dangers of ransomware.
SpinOne is a modern API-driven CASB solution that makes use of machine learning to provide automated intelligence to fight today’s security threats such as ransomware. It does this by using a powerful two-fold ransomware protection architecture that can detect and remediate 99% of all ransomware infections.
Ransomware Risk Management Framework Employed by SpinOne
Detect
Machine learning algorithms monitor Microsoft 365 for any anomalies that indicate a ransomware attack.
Stop
SpinOne provides a quick and effective attack response. The attack source is identified and stopped immediately by blocking the ransomware process.
Remediate
Once the attack is identified and stopped, any files affected by the ransomware attack are identified.
Recover
SpinOne automatically restores the files that have been identified as affected by the ransomware attack. Microsoft 365 administrators are notified of the attack and the automatic recovery.
SpinOne Architecture
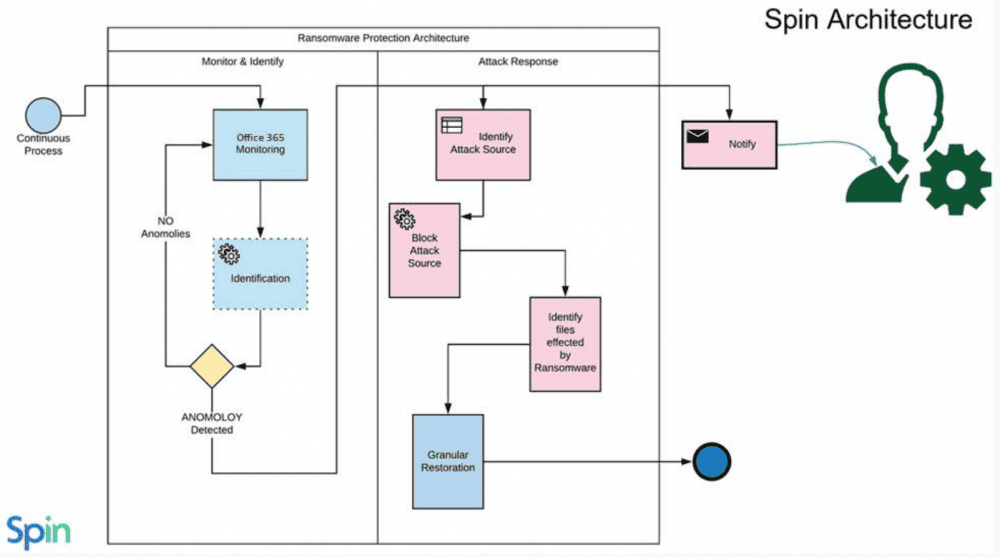
SpinOne provides automated ransomware protection and remediation
SpinOne’s two-fold, automated Microsoft Office 365 ransomware protection is unique among its competitors. Not only does SpinOne backup your business-critical data, it proactively monitors and secures your data against the very threats that often require data recovery such as ransomware.
FAQ
Does Microsoft provide support for ransomware-related issues with OneDrive?
No. You need a third-party tool to protect against ransomware-related issues in OneDrive.
What should I do if I suspect a ransomware attack on my OneDrive files?
We suggest disabling access to your account for all the applications. Then, change your password and set up multifactor authentication. Next, inform the law enforcement. Next, try to get a decryptor or restore data from a backup.
Can I access my OneDrive files during a ransomware attack?
You can access all files during and after the attack. However, the data in them will be encrypted.
How does OneDrive’s version history help in ransomware situations?
It could help if you’re lucky to get infected with a very old strain of ransomware. However, most modern strains encrypt file versions too.
What are the common OneDrive signs of ransomware detected?
The common OneDrive signs of ransomware detected are the encrypted files.
Does OneDrive protect against ransomware?
No, OneDrive doesn’t protect against ransomware.
How to protect OneDrive against a ransomware attack
To protect OneDrive against ransomware, business needs to purchase ransomware detection and response tool. We suggest SpinOne.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Reducing Browser Extension Risk with Spin.AI Risk Assessment + Perc...
April 24, 2024Spin.AI is collaborating with Perception Point: integrating the Spin.AI Browser Extension Risk Assessment within the... Read more
How to Restore A Backup From Google Drive: A Step-by-Step Guide
April 10, 2024Backing up your Google Drive is like making a safety net for the digital part... Read more
Protecting Partner Margins: An Inside Look at the New Spin.AI Partn...
April 2, 2024Google recently announced a 40% reduction in the partner margin for Google Workspace renewals –... Read more


