How to Mitigate Advanced Threats and Attacks against Cloud Service Providers
The world of cybersecurity threats is a diverse and very threatening world filled with many challenges and obstacles for businesses. Even as enterprises transition away from the world of on-premises datacenters into the cloud, security is still very much a top priority. In addition, modern cybersecurity threats are very sophisticated and advanced compared to where things were only a decade ago. For example, cloud service providers have become a new attack vector.
Cloud SaaS environments are increasingly visible on the radar of cyber attackers as businesses transition more business-critical data to these robust environments. Additionally, as threats continue to become more advanced and sophisticated, these advanced threats are increasingly targeting cloud environments. What advanced threats and attacks are on the horizon for cloud SaaS? How can organizations protect themselves?
Advanced threats and attacks on the horizon
There is no question the level of sophistication and advanced tactics used by attackers is on the increase. As a result, cybercriminals are looking for new and effective ways to attack businesses. An increasingly vulnerable attack vector for cloud SaaS environments includes cloud applications and cloud application providers. What are cloud applications?
Both Google and Microsoft provide access to a marketplace of third-party applications that allow extending the capabilities of the cloud SaaS environment. Organizations have ala carte style access to these marketplaces that enable picking and choosing applications that align with the needs of their business.
However, integrating cloud applications into the sanctioned cloud SaaS environment brings risks. For example, the marketplaces for both Google and Microsoft contain thousands of applications from third-party vendors that may or may not be reputable. Even with the efforts of cloud service providers to keep malicious applications from appearing in the marketplace, these are always a risk.
Even outside the marketplace, attackers write malicious cloud applications or browser plugins that easily masquerade as legitimate applications. For example, phishing emails that appear legitimate may persuade users to grant OAuth permissions to a malicious application. However, once the OAuth permissions are granted to the malicious application, it assumes the same level of permissions the user has to the data.
A malicious cloud application can house ransomware. With the proper access and permissions, cloud ransomware can crawl through cloud environments much like on-premises environments. Yet, another type of threat targeting software of all varieties, including cloud applications, is the supply chain attack. Supply chain attacks represent a significant risk to businesses using third-party software.
Supply chain attacks – a danger for cloud service providers
Supply chain attacks are a modern, sophisticated, and very effective way to target organizations worldwide. So what is a supply chain attack? Supply chain attacks introduce compromise at the very source of a trusted and legitimate hardware and software vendors. An attacker carries this out by infiltrating the trusted vendor environment and placing malicious code or malicious hardware components “part of” the trusted vendor’s hardware or software.
By compromising a single vendor, supplier, distributor, or someone else in the “supply chain” of the hardware or software, attackers can essentially turn those trusted hardware or software components into trusted malware coming into an organization. Thus, with one well-placed supply chain attack, cybercriminals can create a fast path into the networks of all the supplier’s customers, which can number into the thousands or even millions.
Ransomware Attacks Surge in 2020-2021
To understand the severity and seriousness of the supply chain attack, we only have to go back to December 2020, when news broke of a devastating supply chain attack on the SolarWinds Orion Network Management System (NMS). The supply chain attack with SolarWinds led to the compromise of FireEye and the US Treasury Department, among thousands of other victims, compromised due to the fallout of the attack.
The SolarWinds supply chain attack was carried out using SolarWinds’ own servers with an SSL certificate registered to SolarWinds. It is believed the certificate itself was not compromised, and the attackers were simply deploying through SolarWind’s own channels. Attackers then proceeded to push out malicious updates using the compromised SolarWinds supply chain. It illustrates just how dangerous a supply chain attack of a trusted vendor can be.
On July 2, 2021, attackers carried out a similar supply chain attack on the Kaseya VSA software used by MSPs worldwide, putting thousands of MSP customers at risk for malicious compromise. According to some estimates, 800-1500 SMBs may have experienced ransomware attacks due to the incident.
Due to the attack on Kasey, the Cybersecurity and Infrastructure Security Agency (CISA), in conjunction with the FBI, released guidance for MSPs and their customers affected by the attack. You can read the specific direction from the CISA-FBI alert here: CISA-FBI Guidance for MSPs and their Customers Affected by the Kaseya VSA Supply-Chain Ransomware Attack.
This type of attack can also affect cloud application providers as the same scenario can unfold. If a trusted cloud SaaS application installed in thousands of cloud SaaS environments is maliciously compromised, all environments with the cloud app installed are a risk of malicious activity. Therefore, organizations must effectively audit cloud applications for changes in behavior, intent, and the data they can access. In addition, strong SaaS ransomware protection is required to protect business-critical data from malicious attacks from cloud applications and other sources.
SpinOne Risk Assessment and Ransomware Protection
Today, the risks to business-critical cloud SaaS environments are too numerous and diverse to protect against these using manual processes and defenses. Instead, businesses today must employ effective cybersecurity automation to protect their business-critical data.
SpinOne provides automated risk assessment for cloud SaaS applications and browser plugins to dynamically and continuously assess the specific risk they bring to the environment. It could take hours per cloud application for a trained SecOps professional to adequately determine the threat posed by one cloud application. Using artificial intelligence (AI) and machine learning (ML), SpinOne can do this in seconds. If you extrapolate the time required using manual efforts vs. SpinOne for your cloud apps risk assessment, there is no comparison between the time savings alone.
With SpinOne, every single app that has access to your sensitive data gets an AI-based security assessment. It allows IT admins to build cloud SaaS policies to allow or block applications based on the security score. In addition, admins can revoke access to risky apps or extensions that are not allowed to access your cloud SaaS environment.
Note the following key benefits
- Cloud administrators can also determine when new SaaS apps get installed or uninstalled
- Automatically review cloud SaaS applications
- Identify apps not allowed in your organization
- Allow or block apps and extensions
- Once an app is added to a block list, SpinAudit will automatically block access if users attempt to install it again
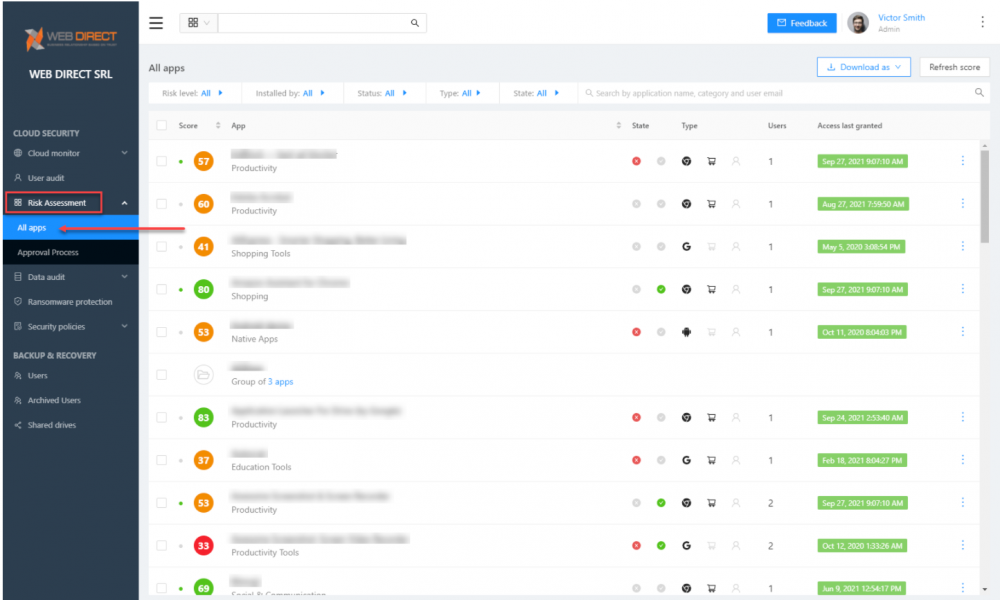
SpinOne provides granular visibility and control over cloud SaaS applications from a simple, intuitive dashboard. IT admins can view the cloud SaaS app name, type, score, state, users, and if access has been granted.
Viewing cloud SaaS applications with the SpinOne Risk Assessment
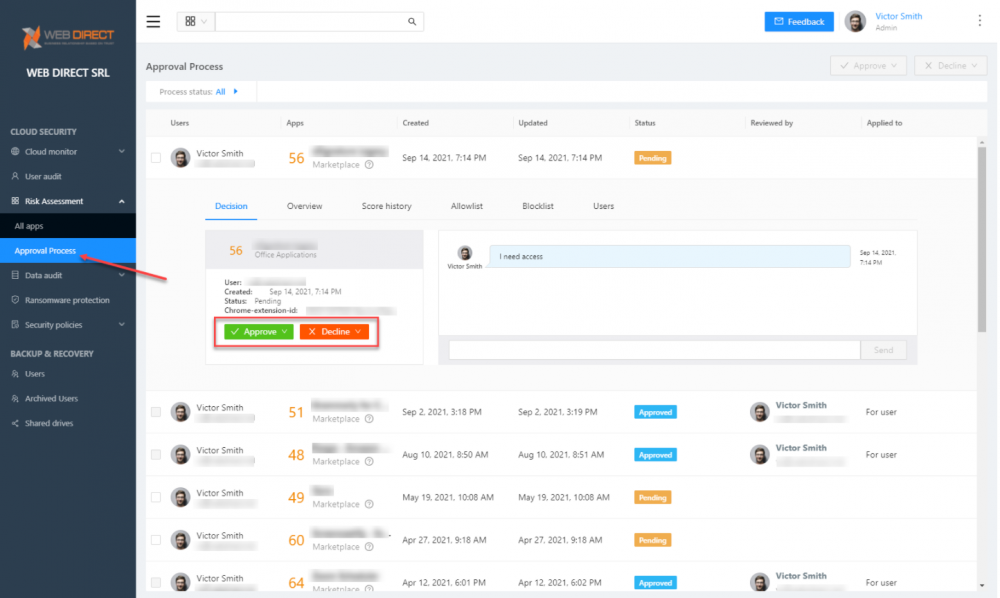
SpinOne allows approving or declining access to cloud applications using a streamlined approval process workflow.
Admins can approve or decline cloud SaaS applications
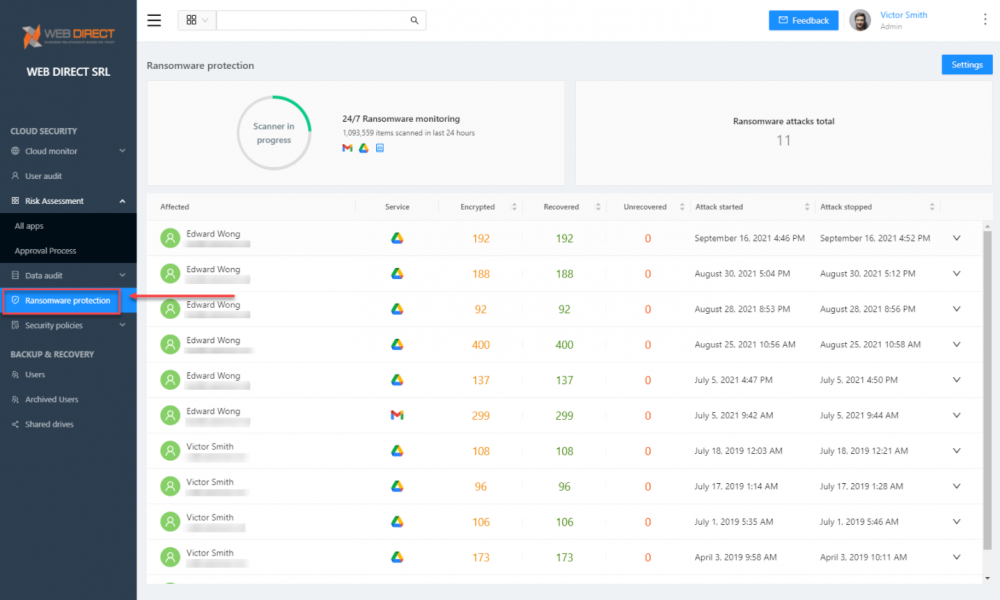
In conjunction with the risk assessment, SpinOne provides industry-leading ransomware protection for a truly multi-layered cybersecurity posture. You can view the SpinOne Ransomware Protection in a simple dashboard. However, there are very complex AI and ML technologies working underneath to protect your organization from ransomware proactively. With SpinOne Ransomware Protection, it performs the following:
- Continuously scans the cloud SaaS environment for signs of a ransomware attack
- Once a ransomware attack is detected, SpinOne blocks the ransomware at a network level
- SpinOne then scans for any files affected
- SpinOne proactively and automatically restores the files to the last good state contained in the backup (configurable) if any files are affected.
- SpinOne automatically notifies administrators of the attack and remediation tasks performed.
SpinOne Ransomware Protection
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...