Prevent Session Token Theft
In cybersecurity, your weakest link can quickly lead to compromise. Unfortunately, organizations often underestimate a significant cybersecurity threat – session token theft. With these hidden keys, hackers can infiltrate secure systems, bypassing multi-factor authentication. Malicious browser extensions and third-party SaaS applications can easily steal session tokens. How? Let’s learn about session tokens, their role in authentication, and the threat they pose when they fall into the wrong hands.
What Are Session Tokens?
Session tokens are digital keys, small pieces of data that websites use to track a user’s activity during a web session. They hold the identification information of a user and are generated after successful login credentials have been provided. Session tokens are usually stored as cookies, hidden fields, or URLs.
They are essential to the functioning of the modern web, providing a seamless, personalized browsing experience. These session tokens are often stored locally and allow seamless browsing without reauthenticating. Let’s see how.
Role of Session Tokens in Authentication
Session tokens play a crucial role in authentication processes. For example, after a user logs into a web service, their credentials are validated, and a unique session token is generated. This token is sent to the user’s browser and stored there for the duration of the web session.
For every subsequent request made by the user to the server, this session token is sent along. The server uses the token to recognize the user and confirm they are authenticated without requiring the user to re-enter their credentials. Essentially, session tokens maintain the ‘state’ of the user, allowing them to interact with web services in a stateful manner despite the stateless nature of the web.
Bypassing Multi-Factor Authentication
Session tokens can bypass multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide two or more verification factors. However, once MFA has been passed and a session token is generated, the token grants access to the user for the duration of the session.
If cybercriminals steal this session token, they can impersonate the authenticated user, gaining access to sensitive data and systems without MFA prompts. This ability to evade one of the most secure forms of authentication emphasizes the threat posed by session token theft.
Illustrating the danger posed by stolen browser session tokens, in March 2023, popular tech YouTuber Linus Sebastian of the renowned “Linus Tech Tips” channel suffered a high-profile breach of three YouTube channels due to stolen session tokens. According to Sebastian, attackers could compromise “all user data from both their installed browsers,” which included session tokens, giving the bad actor “an exact copy” of the browsers that they could export and login without needing to enter security credentials, including MFA.
Whether it is YouTube, SalesForce, Microsoft 365, Google Workspace, or other SaaS services, attackers can compromise these environments using stolen session tokens. With the rise of organizations using MFA on SaaS solutions across the board, hackers are more commonly targeting browser session tokens to bypass MFA and other security measures. In addition, it helps to illustrate the danger of malicious software that compromises client systems and the data they can access.
The Threat of Malicious Browser Extensions
Malicious browser extensions pose a significant risk in stealing session tokens. It is because they often present themselves as useful tools to improve the user’s browsing experience. However, once installed, they can access all data on the web pages visited by the user, including session tokens.
These extensions can be engineered to silently siphon off session tokens and send them to a remote server controlled by the attacker. Cybercriminals can then use these tokens to impersonate legitimate users and gain unauthorized access to sensitive information or systems.
The Role of Malicious Third-Party SaaS Applications
The SaaS ecosystem is another area where session tokens can be compromised. Many SaaS applications require access to user data to function. However, malicious SaaS applications can abuse this access to steal session tokens.
For example, a malicious SaaS application might request user email access. Once granted, it can siphon off session tokens stored in the user’s emails, granting the attacker access to any accounts associated with these tokens.
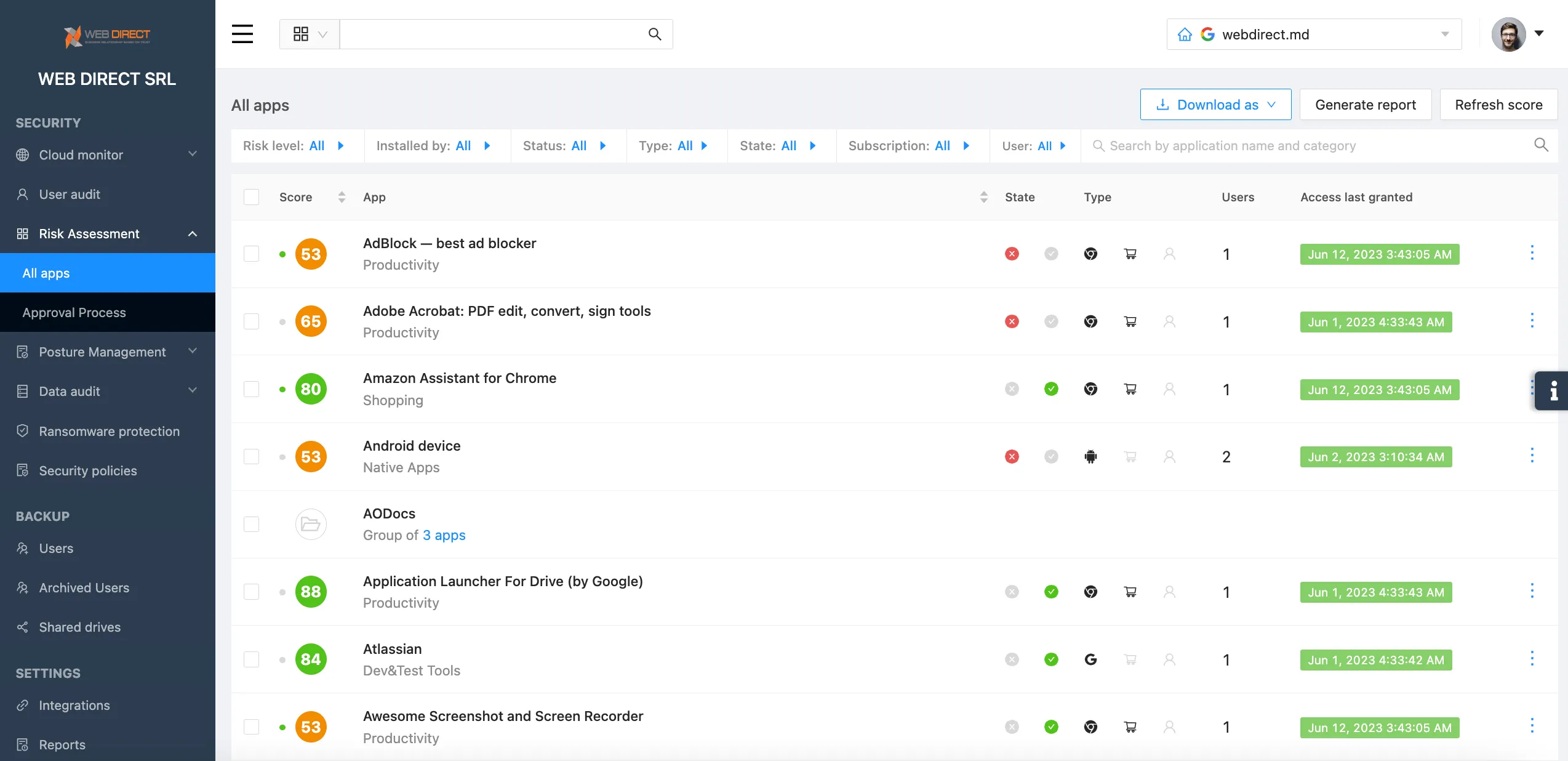
SpinApps – Protecting your session tokens
As a pioneering solution in the realm of SaaS security, SpinOne provides the needed line of defense against the threat of session token theft using malicious browser extensions or SaaS apps. Selected by Google, SpinOne offers comprehensive risk assessment and visibility into the potential dangers posed by third-party applications – enabling businesses to safeguard their SaaS ecosystems effectively.
SpinOne offers a unique advantage in the battle against session token theft. It scrutinizes app extensions and third-party applications, evaluating over 15+ features for each detected SaaS application. It enables businesses to understand and manage the risks associated with each application, minimizing the potential for session token theft.
Additionally, SpinOne:
- Supports platforms beyond Google Chrome extensions, such as Microsoft Edge
- Supports both Google Workspace and Microsoft 365
- Automates installation, detection, assessment, and updates on OAuth token refresh timings
- Provides granular controls and policies for SaaS Access Management Automation
- Enables the creation of policies for allowing or blocking applications based on their:
- Risk Score
- Application ID
- Category
- Developer
- Application Name
If you would like to speak with a Spin Solution Engineer to learn how SpinOne can protect your environment from malicious cloud SaaS apps, click here to schedule a demo.
Wrapping Up
The theft of session tokens presents a growing threat in today’s digital landscape. The danger lies in their ability to grant cybercriminals easy access to sensitive systems and data, bypassing even multi-factor authentication. In addition, malicious browser extensions and third-party SaaS applications effectively allow cybercriminals to steal these tokens, often without the user’s knowledge.
Safeguarding against these threats requires a comprehensive understanding of the risks and adopting adequate technologies and security measures. Regularly auditing browser extensions, limiting the access of third-party applications, and enforcing secure session management practices are essential steps in preventing session token theft.
FAQ
What are web sessions?
A web session is a series of transactions between an application and a user. It is carried out through request and response. Modern apps collect and store the data or status of a user so that they could deliver a continuous and integral user experience. For example, they store information about language preferences. Apps have sessions for non-authenticated and authenticated users.
Is the session token secure?
A web session is a series of transactions between an application and a user. It is carried out through request and response. Modern apps collect and store the data or status of a user so that they could deliver a continuous and integral user experience. For example, they store information about language preferences. Apps have sessions for non-authenticated and authenticated users.
Can session tokens be stolen?
Hackers can steal session tokens using different programs or malicious code. Such tools should be running on the user’s side.
What is Multifactor Authentication?
Multifactor authentication is a type of authentication in an application that requires two or more different verification methods. An example of MFA is when you enter your credentials in an app and then need to verify this action on your mobile device.
What is the difference between basic authentication and session authentication?
Basic authentication requests user credentials every time a user accesses the application. Session authentication will remember the device the user used to log in for the first time. In the future, the application will not require the user to repeat the login on that device. This method has its advantages and threats.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Midnight Blizzard Attack on Microsoft: Key Lessons for Strengthenin...
Midnight Blizzard Attack on Microsoft: Key Lessons for Strengthening Your SaaS Security From November 2023...
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...


