Mobile Ransomware Attacks. Device Security
While ransomware has been a persistent threat for over two decades, the rise of mobile ransomware attacks in recent years has intensified concerns. As the world becomes increasingly dependent on online and wireless connections, the prevalence of mobile ransomware attacks has escalated, capturing widespread attention in the 21st century.
Brief Definition
Ransomware is a kind of malicious software or malware. As its name suggests, these cyber attacks lock computers, mobile devices or files so that owners have their access restricted unless they pay a ransom. In other words, it kidnaps your data or device.
There are two types of ransomware: blockers and encryptors. The former blocks a computer or device and sends a message telling the victim to send money for the system to be unlocked, whilst the latter encrypts files and will require ransom in exchange for the decryption key.
Encryptors are also the worse of the two. Blockers can be reversed by reinstalling the OS to recover data, but encrypted files due to ransomware attacks can only be opened by their corresponding decryption keys, no matter where you transfer the files, even on a freshly reinstalled OS.
They’ve infected all operating systems, whether Linux, Windows, Apple OS, or Android. Numerous types have also appeared, all of them having their own infection tactics, file targets and ransom amounts.
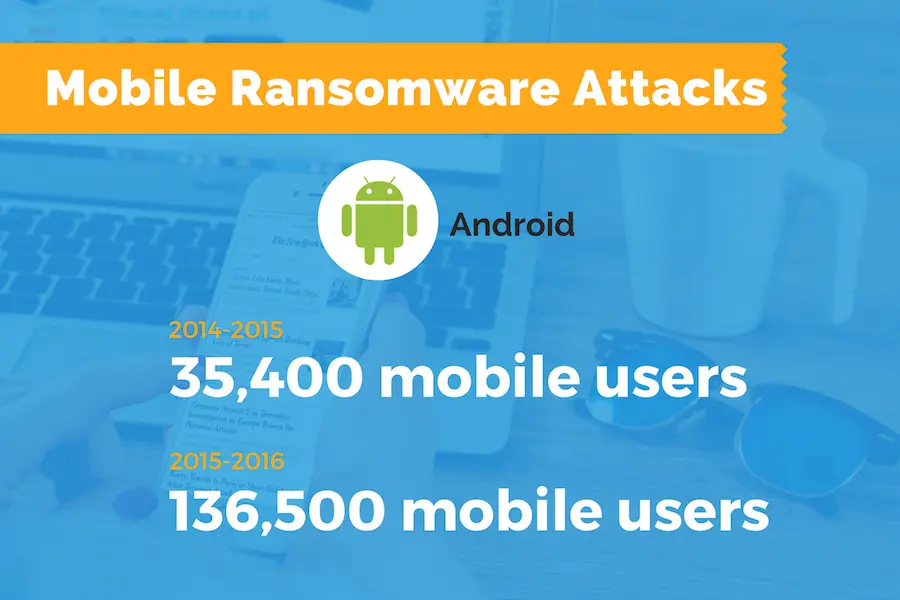
Damage in Figures
As the number of smartphone users grows, mobile ransomware attacks get more prevalent as well. In fact, last 2014-2015, there were just over 35,400 mobile users who got attacked. But in 2015-2016, this number increased by almost 400% to more than 136,500 victims. What’s worse, these numbers were just for Android ransomware.
Although iOS gadgets were relatively more secure from mobile ransomware due to tight security in App Store, they’re far from immune. In 2015, different variants of malware spread across App Store apps such as XcodeGhost and Youmi, which infiltrated around 4,000 apps and over 250 apps, respectively. Once inside a device, they send the personal credentials of the owner to the attackers, including credit card or bank details. They’re not ransomware per se, but they prove that iOS devices have been breached all the same.

Protect Yourself
Back up your files regularly, especially ones with sensitive information. It’s better if you can avoid putting this info in your device altogether. Unfortunately, a lot of times people use their smartphones for jobs and other transactions so there will be corporate files and other data like credit card details, personal info, etc. in these mobile devices.
In that case, be sure to back up the files in secure locations. Google made this process easier by integrating a single account from each user to be utilized on their services such as Gmail, Google Drive, Calendar, and others.
Saving backup files online in cloud storage is efficient and convenient, and their security is enhanced as often as possible through testing of groups like Cloud Security Alliance. For more safety though, Spinbackup and other cloud security programs enable users to further protect their data or restore them in case of loss due to a virus or ransomware attack.
A good rule of thumb, however, is to have a copy of your files in offline storage such as external drives as well. Just update them on a scheduled basis.
Be extra careful and avoid suspicious links or websites. Though premium smartphones have security features like Touch ID and other fingerprint scanners, these mostly work as outbound protection, i.e. for online purchases. Ransomware attacks are inbound, such that the hackers look for a security breach while you’re browsing the internet and opening websites, after which they send malware through the gap.
Remember to check and apply updates for your software. Releases like Android’s August Security Update, which comes in two patches, are crucial for the protection of your data. The first update contains major security fixes for all Android devices, while the second is for drivers and kernel-related improvements.
Consider upgrading your device as well. Some service providers have trade-in options, such as O2’s Refresh for example, wherein a subscriber can swap out his/her device anytime during contract period. Getting a newer model with better security features can mean the difference in being more vulnerable or not.
Exclusively written for Spinbackup
by TheTechAware
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
6 Common Mistakes in Google Workspace Backup
Google Workspace is a set of productivity apps, including Gmail, Drive, Docs, Meet, and Calendar...
Google Workspace vs. Microsoft 365 comparison
With so many productivity suites available, it can be overwhelming to decide which one is...
Top 10 Low-Risk Applications and Extensions for Google Workspace
Google Workspace is an extremely popular SaaS productivity suite used by millions of organizations today....


