Ransomware – CISO’s worst nightmare: Detect, Block, Prevent
In the first two CISO cybersecurity guides, we have taken a look at the evolving threats facing organizations today. There are many ominous and dangerous risks to business-critical data against which businesses must defend. With the wide range of threats, organizations need robust cybersecurity solutions. SpinOne provides the seamless tools necessary to secure cloud SaaS environments proactively, using next-generation technologies. In part three of the CISO cybersecurity guide, we will see how SpinOne helps businesses defeat arguably the most dangerous threat to their data, ransomware.
Ransomware – The CISO’s worst nightmare
There is no question that a widespread ransomware attack is one of the worst nightmares for any CISO and business in general. Is ransomware becoming an issue for organizations today? Most definitely. A look at ransomware statistics from this past year should help companies appreciate that ransomware is a tremendous threat. Consider the following:
- Ransomware increased by 485% in 2020 compared to 2019
- The average cost of ransomware according to the IBM Cost of a Data Breach Report 2020 – $4.44 million
- In 2020, 73% of all ransomware attacks were successful
- 10% of all cyberattacks carried out now involve ransomware
- In 2021, ransomware will attack organizations every 11 seconds, with damages totaling $20 billion
Ransomware is growing in its use and pervasiveness in the underworld of cybercriminals. It is primarily due to the effectiveness of ransomware in achieving the end goal – ransom payment. In May 2021, a ransomware attack on Colonial Pipeline effectively shut down a significant fuel pipeline from Houston to the northeast that supplies nearly half the fuel consumed along the Eastern Seaboard. It took six days for Colonial Pipeline to restart operations. However, it was not without hard decisions being made.
Colonial Pipeline Attack
Colonial reportedly decided to pay hackers a $4.4 million ransom on the same day of the attack. It still took them six days, as mentioned, to restore operations. It is a sobering wake-up call to CISOs everywhere. Ransomware is a highly disruptive, effective, and damaging cyberthreat that can disrupt business for even major organizations with seemingly robust cybersecurity strategies.
Not long after the ransomware attack on Colonial Pipeline, JBS, the world’s largest meat processing company, suffered from a major ransomware attack. The attack left the meat processing business struggling to bring operations fully back online.
These recent attacks on critical infrastructure have led to the recent development of the U.S. Justice Department, prioritizing ransomware attacks on the same level as terrorism. As reported by CBS News:
“In a memo to federal prosecutors on Thursday, the Justice Department’s second-in-command pressed investigators to step up efforts to track down and prosecute the criminal gangs carrying out the attacks. The memo noted the “destructive and devastating consequences” the attacks are having on critical infrastructure.
“We recognize this is an increasing threat,” White House press secretary Jen Psaki said Thursday.
The White House had an extraordinary warning to American companies, telling them to beef up their cybersecurity because “no company is safe.”
With government involvement, ransomware is now considered a top threat among other threats to the public, such as traditional terrorism. The new wave of attacks has increasingly targeted critical infrastructure industries and businesses, which leads to escalated risks across the board.
Three reasons to bolster security against ransomware
Global ransomware damage costs (source: CyberCrime Magazine)
According to Cybersecurity Ventures
Ransomware will cost its victims more around $265 billion (USD) annually by 2031, Cybersecurity Ventures predicts, with a new attack every 2 seconds as ransomware perpetrators progressively refine their malware payloads and related extortion activities. The dollar figure is based on 30 percent year-over-year growth in damage costs over the next 10 years.
Ransomware is highly problematic, even for companies using cloud SaaS environments. Why is this the case? There are three reasons that companies need to “double down” on ransomware attacks, even with cloud SaaS environments.
- Paying the ransom is no guarantee you will get your data back
- New ransomware variants are increasingly using the threat of releasing data to the Internet
- Cloud SaaS providers can throttle restore operations
1. Paying the ransom is no guarantee you will get your data back
The FBI and other law enforcement organizations do not support paying the ransom demanded by attackers using ransomware. There is no guarantee, even when paying, that you will get your data back. The process decryption process, even with the ransomware key, can be slow. Colonial pipeline reportedly paid almost $5 million in ransom to the attackers, only to use their backups to restore operations since the decryption process was too slow using the hacker-provided key.
2. New variants are increasingly using the threat of releasing data to the Internet
More often than not, ransomware variants are threatening to release your company data to the Internet along with holding it hostage. This approach helps to ensure that even if your business has data backups, the ominous threat of your data leaking to the Internet is equally destructive and helps to force ransom payment. It helps underscore the need to stop a ransomware attack as soon as possible before the bulk of your data is held hostage and leaked.
3. Cloud SaaS providers can throttle restore operations
To help support cloud SaaS environments’ performance in general and prevent “noisy neighbor” scenarios, cloud SaaS providers, including Google Workspace and Microsoft 365, are throttling API calls to back-end cloud SaaS APIs. This throttling effectively limits write operations to cloud storage, among others. As an example, regarding the throttling in place in Microsoft Graph, the API frontend to Microsoft 365, Microsoft notes:
“When a throttling threshold is exceeded, Microsoft Graph limits any further requests from that client for a period of time. When throttling occurs, Microsoft Graph returns the HTTP status code 429 (Too many requests), and the requests fail. A suggested wait time is returned in the response header of the failed request. Throttling behavior can depend on the type and number of requests. For example, if you have a high volume of requests, all request types are throttled. Threshold limits vary based on the request type. Therefore, you could encounter a scenario where writes are throttled but reads are still permitted.”
Again, this underscores detecting and preventing ransomware attacks in cloud SaaS environments as quickly as possible. The less data that needs to be restored, companies are less likely to hit this threshold.
Detect, Block, and Prevent Ransomware with SpinOne
CISOs must protect cloud SaaS environments with proactive ransomware protection to pinpoint a ransomware infection and stop it from spreading quickly. Ransomware can infect cloud SaaS environments by attack vectors, including OAuth compromise and file synchronization from on-premises to the cloud. Let’s examine how the SpinOne Ransomware Protection module provides the protection needed by CISOs looking for a seamless way to protect their environment from ransomware proactively.
SpinOne advanced ransomware threat protection capability uses a combination of AI-powered threat intelligence and behavior-based detection to stop ransomware before it compromises your organization and its business-critical data. SpinOne provides the deepest visibility into ransomware sequences and detects behaviors indicative of ransomware. The behavioral rules detect and block advanced threats across the entire lifecycle.
SpinOne uses next-generation artificial intelligence (AI) and machine learning (ML) to help defeat ransomware in cloud SaaS. CISOs can view the SpinOne AI/ML engine as an automated SecOps team working night and day, watching for subtle anomalies more efficiently than humanly possible. The SpinOne Ransomware Protection module uses a four-step approach to defeat ransomware:
- SpinOne algorithms scan and detect a ransomware attack underway
- It automatically blocks the source of the attack
- SpinOne scans to find any files affected by the ransomware attack
- Files are restored automatically to their pristine state from SpinOne backup.
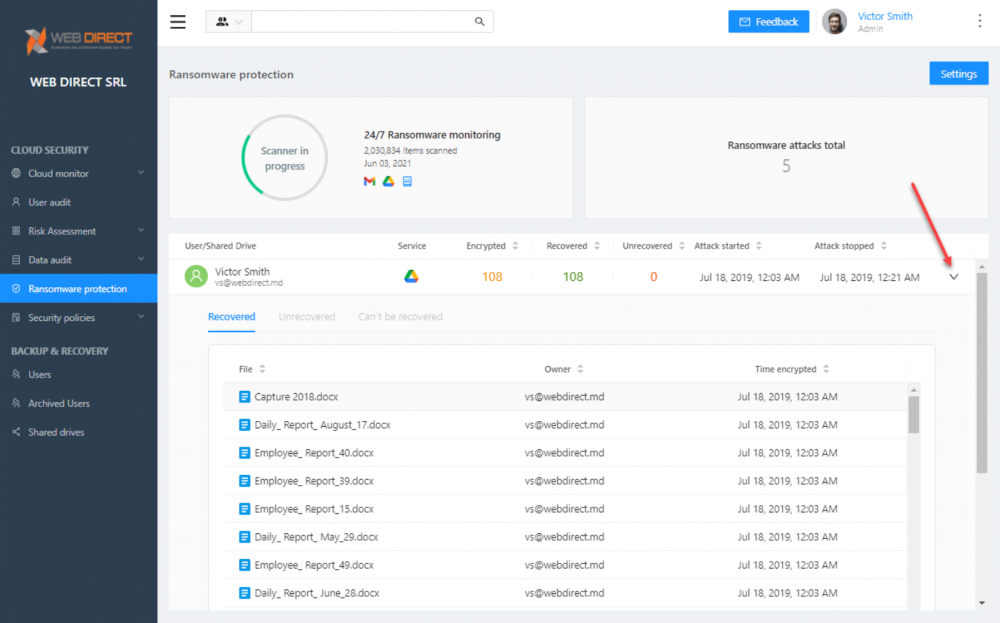
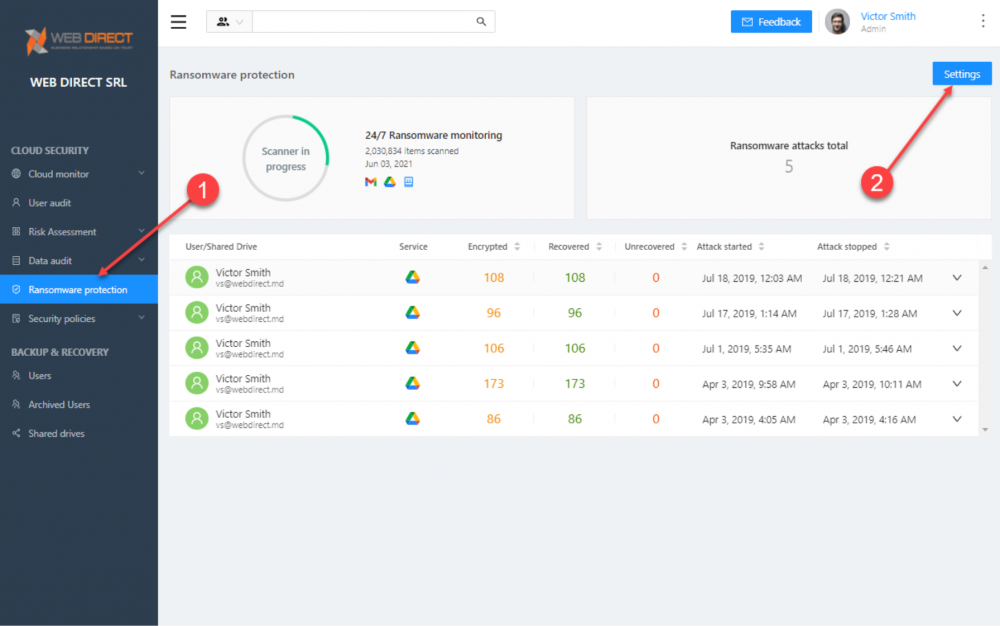
What CISOs will love about SpinOne is both its power and its simplicity. Despite featuring world-class ransomware protection with AI and ML working under the hood, it is simple and easy to implement and manage. By clicking the Ransomware Protection menu item, you will be able to view the Ransomware Protection module. It will display the previous recent history of ransomware attacks detected, files encrypted, and items recovered.
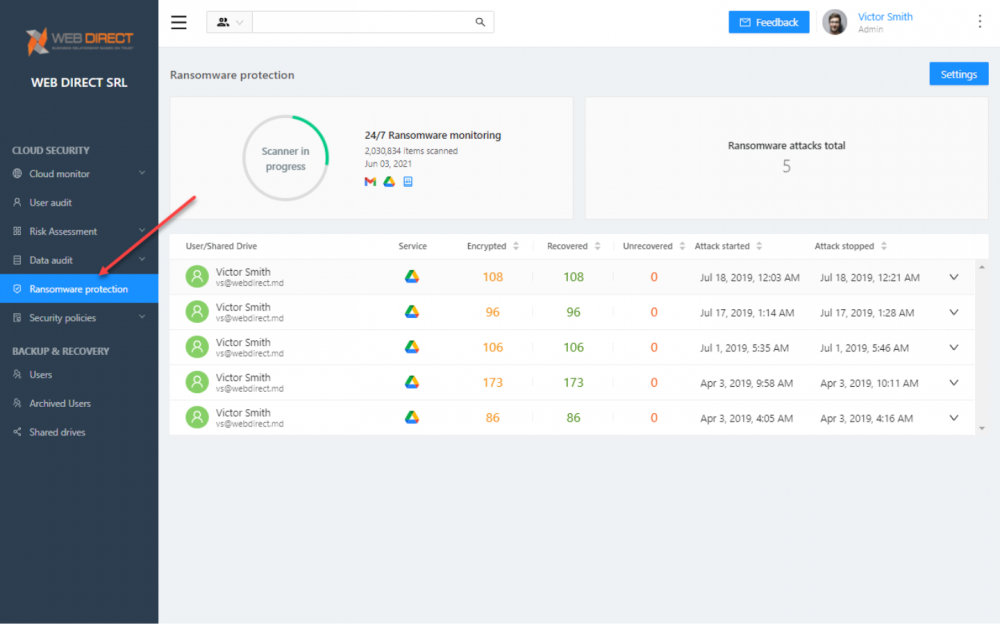
You can view the details of each ransomware event by clicking the dropdown arrow to the right of each event. By clicking the dropdown arrow, you will see the specific files affected by the ransomware event.
Viewing the details of the ransomware attack event
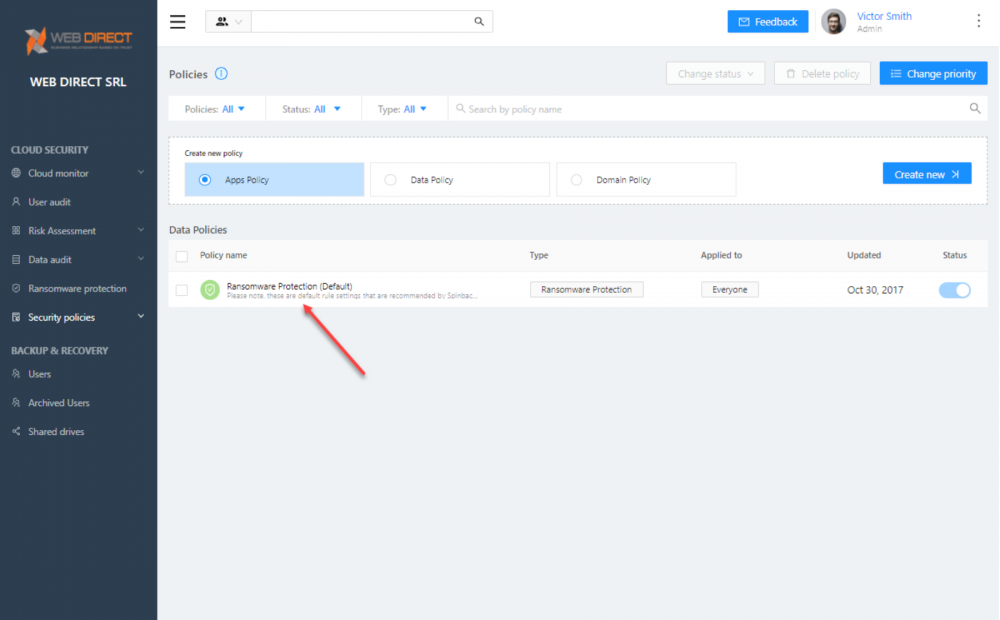
To see just how easy the Ransomware Module is to configure, click the Settings button
Viewing the settings for the Ransomware Protection module in SpinOne
You will see the Ransomware Protection (Default) policy in place protecting your organization. By default, this policy applies to everyone in the organization. Click the name of the policy to view the granular settings.
The default Ransomware Protection module in SpinOne
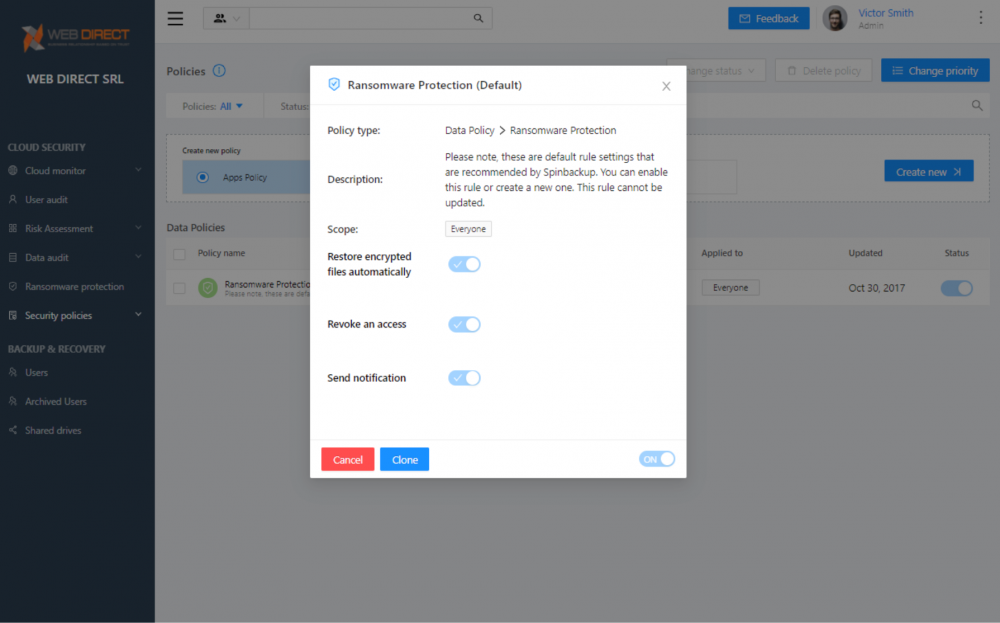
Each Ransomware Protection policy configuration contains the following configurable settings:
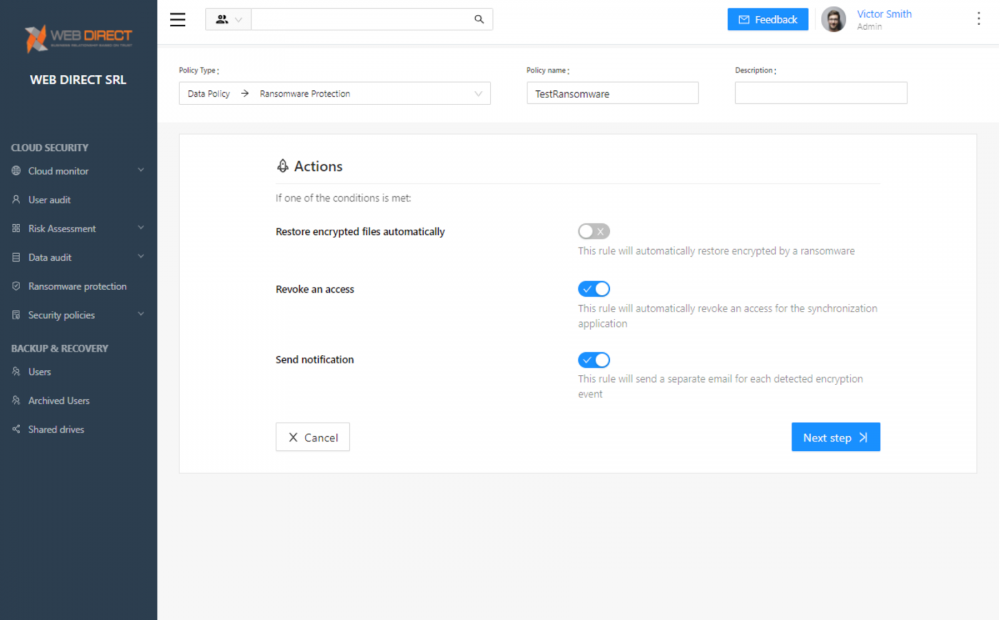
- Restore encrypted files automatically – Choose whether or not you want SpinOne to automatically restore files from the latest backup that are affected by ransomware
- Revoke access – Configure SpinOne to revoke access to a malicious ransomware process automatically
- Send notification – Automatically notify SpinOne administrators of the event.
Ransomware Protection options
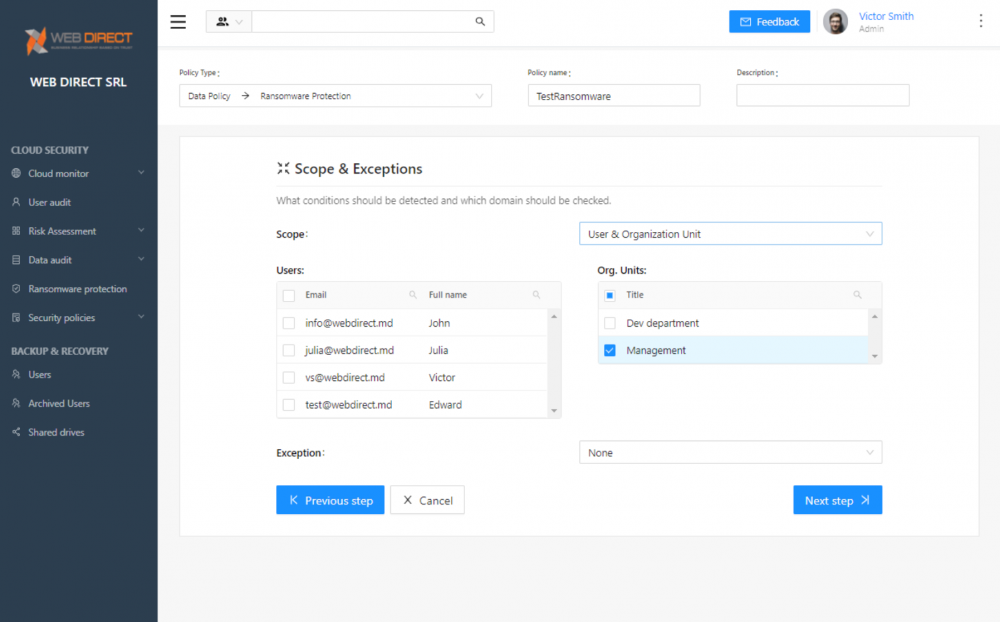
Aside from using the default Ransomware Protection policy by default, you can create a custom policy and settings for the Ransomware Protection module and customize the users or groups to which the policy applies. Below is an example of a policy that does not automatically restore encrypted files but revokes access and sends notifications.
Creating a custom Ransomware Protection Policy
Ransomware Protection policies can be scoped to users and organizational units in the organization.
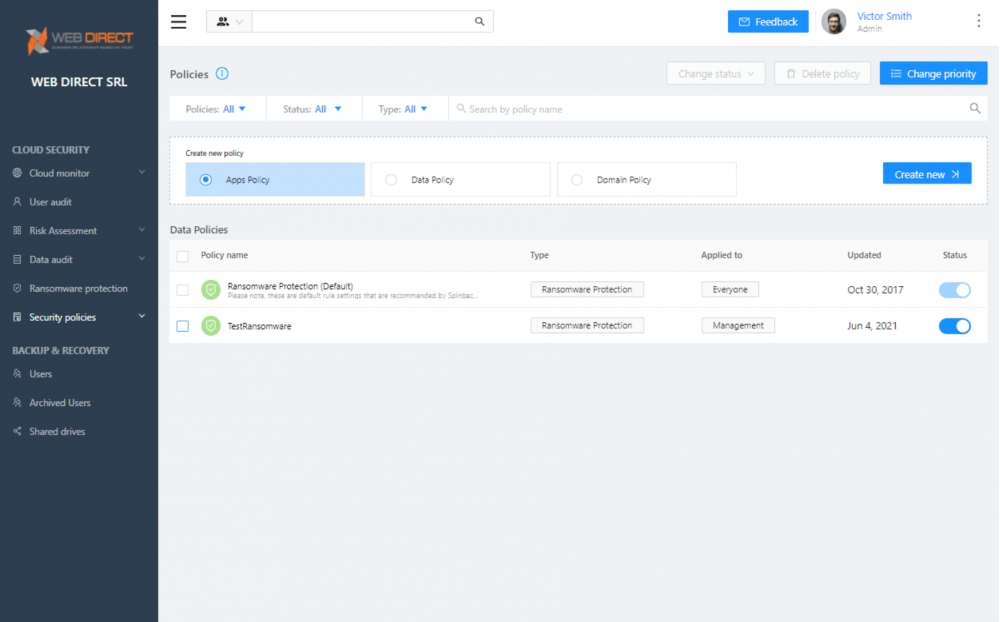
After creating the new policy, it will display in the Ransomware Protection dashboard.
Custom Ransomware Protection policy successfully created
Ransomware protection solution benefits: stop the ransomware attack and keep your SaaS data safe with SpinOne
The beauty of the SpinOne Ransomware Protection module lies in its effectiveness and simplicity. Under the cover of the simple settings in the GUI lies a robust ransomware protection solution driven by artificial intelligence (AI) and machine learning (ML) technology.
Why SpinOne for Ransomware Protection: Achieving No Downtime
Downtime is an inevitable negative result of any ransomware attack. On average downtime is 16 days, which results in millions of dollars for your business. The main reasons for downtime are:
- Lengthy manual processes
- Huge amounts of damaged data
- API limits of cloud service providers
SpinOpe allows you to reduce downtime from 16 days to 1 hour and cut recovery costs by over 90% per ransomware attack with recovery happening in minutes instead of days or weeks.
Using SpinOne, businesses can proactively defend their cloud SaaS environment using a next-generation tool written to meet the challenges of fighting threats such as ransomware in the cloud. Using the SpinOne approach, businesses can go after ransomware before it encrypts large amounts of data. This capability helps to significantly minimize the threat of data leakage used as leverage by hackers, the risk of paying for a decryption key that may or may not work, or running into the hurdle of throttled API connectivity in the cloud.
Ransomware should undoubtedly be a key topic for CISOs across all businesses and industries as it continues to grow more ominous and effective in holding business-critical data hostage. CISOs and organizations today must meet the threat of ransomware head-on. SpinOne provides the solution necessary to proactively and automatically protect against and recover from a ransomware attack.
Learn more about how SpinOne can defend your organization against ransomware here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...