Ryuk Ransomware: Data Protection Strategies
The average ransomware demand continues to grow (up to $41,198 in Q3 2019, compared to $5,973 in the same period last year). One particular virus is to blame. We are talking about the Ryuk ransomware. This infamous malware shows: hackers are getting more serious than they have ever been before.
What is Ryuk Ransomware
Ryuk is a highly dangerous ransomware that targets companies and governmental organizations alike. This ransomware encrypts cloud data, damaging the whole network of an organization. Ryuk virus has made a name for itself targeting businesses that supply services to other companies — particularly cloud-data firms — with the ransom demand set according to the victim’s financial capability.
Firstly detected in 2018, Ryuk has extorted at least $3,7 million, just in the first 52 payments. Ryuk targets large organizations, using advanced encryption algorithms that are extremely hard to decrypt.
The ransom demand is insane: up to $14 million (!) in Bitcoin. To compare, the infamous WannaCry demanded nearly $300 for decryption. Due to Ryuk, the average ransomware demand has grown to $41,198.
The ransom demand is set according to the approximate value of the encrypted data. This is evidence of solid research done by hackers before the attack.
Taking into account Ryuk’s advanced technology and financial research, it’s safe to conclude: Ryuk authors are not some home-grown rookies, but serious and well-organized professionals.
How Ryuk Works
Similar to other ransomware, Ryuk spreads by phishing emails or malicious pop-ups. Once a user clicks the infected link, Ryuk gets into the system. After some time, Ryuk encrypts the business-critical data. The damaged files can’t be decrypted without a special digital key that hackers promise to provide once the ransom is paid. You can read more about how ransomware works in our recent article.
Contrary to the majority of ransomware families, Ryuk is targeted. It means that instead of randomly sending phishing emails to anyone, hackers carefully choose the target to infect with Ryuk.
The targets are usually enterprises that have a lot to lose and will be willing to pay to get their data back. Ryuk works like a secondary payload through botnets Emotet and TrickBot.
Hackers send emails with infected attachments> User clicks the attachment > Botnet (Emotet or TrickBot) is downloaded > Virus moves through the infected network > Ryuk is executed > Data becomes encrypted > User gets a ransom note
When infiltrating the system, Ryuk converts non-executable files in the .ryk file extension. In all infected folders, you can find a text file called RyukReadMe that notifies you about the attack. Also, the note mentions a Bitcoin address for paying a ransom to get your files back.
What makes things worse is that Ryuk can stay silent for weeks or months to gather more information and maximize the impact. The virus identifies the shared folders and deletes the virtual shadow copy. This means hackers can simply ban the Windows System Restore option. Therefore, if you don’t have an external backup, you may not be able to recover your files.
Ryuk often encrypts Microsoft Office 365 data, that’s why the organizations must have a backup for Office 365 and use ransomware detection software that can stop the ransomware attack from spreading through the network. We’ll talk about it in detail at the end of the article.
Recent Ryuk Attack
Florida ransomware attack, June 2019. Ryuk attacked two city councils in Florida: Lake City, and Riviera Beach City. The attack immobilized local networks, forcing the councils to pay. The sum paid to hackers exceeded $1 million.
La Porte County, July 2019. The county in Indiana suffered an attack that affected nearly 7% of the local administration’s laptops.
Hackers collected $130,000 in Bitcoin as a ransom to restore systems after the attack. However, the network still took days to recover completely.
VCPI attack, November 2019. The attack targeted a Milwaukee-based IT company operating with cloud data. As a result, the workflow of 110 clients across 45 U.S. states was disrupted. More than 80,000 computers and servers powering care facilities were affected.
Ryuk infected Office 365 accounts of the company. Hackers demanded $14 million in Bitcoin to decrypt the damaged data.
The initial infection, presumably, occurred in September 2018. That means the virus had been moving through the system for 14 months before the encryption started.
What Can You Do if Ryuk Infection Happens?
There is no reliable Ryuk decryptor on the market, and an available one seems to be broken. That’s why in case of infection you have just three options: say your data goodbye, pay the ransom, or restore damaged files from backup. You won’t be happy with the first two. Accepting data loss leads to huge financial and reputational damage. Paying up might be just a waste of money, as hackers may not give you the decryption key.
Restoring encrypted files from a backup is the only valid solution. If you backed up your data, you can be sure that you can recover it in case of an attack. Backup is proven to be effective against Ryuk: Louisiana’s Office of Technology Services avoided paying the ransom due to recovering its computer systems from backups and getting rid of Ryuk.
Ryuk Ransomware Prevention
Universal ransomware protection rules can be applied to Ryuk as well. As we’ve mentioned before, having a backup is a great way to keep your data safe from ransomware.
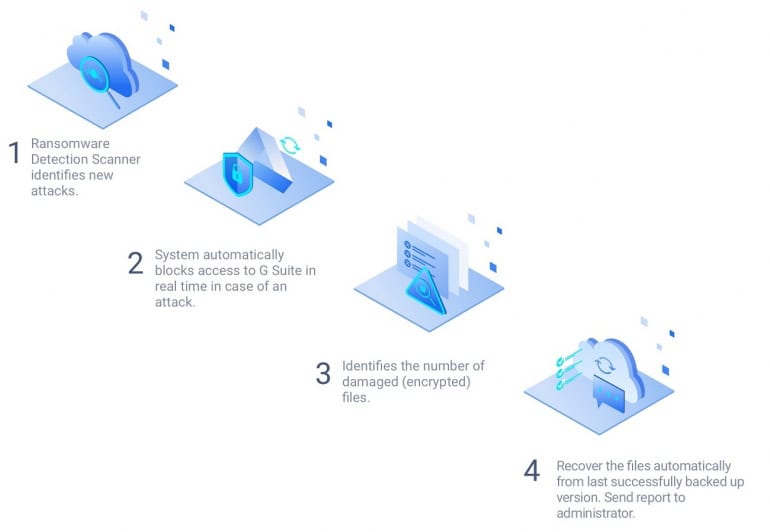
Though being very effective, recovering files from a backup take some time. That’s much better than paying a ransom, but while you’re waiting for your data to recover, your business is losing money. That’s why the best way to protect your data from Ryuk is by combining backup with ransomware detection tools. These tools detect a ransomware infection ASAP and stop the infection process, which results in a lesser number of files compromised and faster recovery from a backup.
In addition to backup, we offer ransomware protection software for Microsoft 365 or Google Workspace (G Suite). SpinOne identifies ransomware and blocks its source, keeping the number of affected data as low as possible. After the threat has been neutralized, all encrypted files are recovered from a backup automatically.
Here you can read more about SpinOne and how it protects you against ransomware.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...
Data Loss Prevention Techniques for 2025 and Beyond
It’s painstakingly clear that data loss is a major challenge facing businesses today. Our experts...
What is SaaS Security? Challenges & Best Practices
Businesses increasingly rely on Software as a Service (SaaS) for increased efficiency, collaborativeness, and scalability....


