Enterprise Guide to Security Automation

Automation is one of the most powerful tools in enterprise technology today. Organizations are moving too fast and using too many technologies, services, applications, on-premises, cloud, hybrid cloud, multi-cloud, and SaaS solutions to manually manage and secure their environments. One area where automation is vital to the evolving technology landscape is security. New cybersecurity risks and threats come out of nowhere, and new attacks and vulnerabilities continue to threaten the safety of business-critical data. Using security automation, companies can successfully meet the cybersecurity challenges of the new cloud era. This enterprise guide to security automation will see how businesses can effectively meet future security challenges, including in cloud Software-as-a-Service (SaaS) environments.
Complex security challenges face organizations
Organizations today are facing monumental challenges related to cybersecurity in the enterprise. As businesses continue shifting their infrastructure landscape to include on-premises resources, cloud infrastructure, and cloud SaaS environments, there is no longer a perimeter. Instead, data, services, applications, and network resources can connect from anywhere to anywhere.
Antiquated cybersecurity notions of an edge firewall protecting everything from the outside and trusting everything on the inside are long gone. As businesses transition to the cloud, including cloud SaaS environments, and they have shifted to a hybrid workforce, it represents a paradigm shift in how they think about cybersecurity.
As the disruption of the past two years has shown, many organizations quickly realized their security strategy was not equipped to deal with the modern cloud-centric model that became the target of businesses everywhere with the shift to hybrid work.
Moreover, attackers are taking advantage of the underprepared and distributed enterprise environment, carrying out attacks in the on-premises data center and across cloud infrastructure and cloud SaaS environments. We have seen an explosion of ransomware in the past few years. The situation seems poised to worsen as cybercriminals have more tools at their disposal.
Developments such as Ransomware-as-a-Service (RaaS) and Initial Access Brokers (IABs) provide everything even a novice hacker needs to carry out a ransomware attack. In the same way that we use Software-as-a-Service (SaaS) environments without thinking about the underlying infrastructure, attackers are using RaaS to carry out ransomware attacks without worrying about the underlying complexities required to carry out the attack.
Ransomware groups are providing Ransomware-as-a-Service on the dark web to bring in even more revenue to carry out even more attacks. Ransomware groups operate like a corporate environment with paid developers, marketing, HR, accounts, etc.
Organizations face a complex security dilemma with the increased distributed surface spanning multiple environments and increasing attacks, ransomware, vulnerabilities, and dark web crime syndicates. These challenges cannot be overcome by conventional, manual processes carried out by a traditional security operations center.
Security automation is needed
With the sheer scope of an organization’s data landscapes and the number of attacks carried out today, it is becoming impossible to protect your organization’s data using only manual processes. Traditional security monitoring and remediation are very “human-driven,” with a person watching consoles, looking for anomalies, and remediating these.
However, now that organizations are using cloud SaaS environments and employees and data are more distributed than ever, this approach is no longer adequate to protect against the sheer number of attacks and anomalous cybersecurity signals.
Another growing problem for organizations today looking to staff skilled cybersecurity professionals is the growing lack of cybersecurity talent to fill the roles needed in organizations today. Additionally, like many other technology fields, cybersecurity is accelerating at warp speed, leaving a gulf in the cybersecurity talent needed to fill security roles in the enterprise today.
According to Cybersecurity Ventures, the number of unfilled cybersecurity jobs worldwide grew 350% between 2013 and 2021, from 1 million to 3.5 million. Do the lack of cybersecurity professionals really have an impact in the environment? Yes, it does. According to one ISC2 study, it leads to the following challenges for companies surveyed:
- Misconfigured systems (32%)
- Not enough time for proper risk assessment and management (30%)
- Too much lag time for patching critical systems (29%)
- Oversights in procedures and processes (28%)
- The inability to keep on top of active threats against company networks (27%)
- Rushed deployments (27%)
The expanding and diverse data and technology landscape and the growing shortage of skilled cybersecurity professionals create a perfect storm. One of the solutions to both issues is the use of proper security automation.
Security automation provides a powerful way to analyze and remediate cybersecurity anomalies faster than any human can. Additionally, security automation uses automated processes to perform the heavy lifting of the often very mundane, repetitive, and challenging task of examining all of the cybersecurity signals flowing into your environment and looking for anything anomalous.
It frees up skilled cybersecurity professionals for more high-level and more valuable security tasks for the business. This helps retain cybersecurity talent as they are tasked with far more rewarding activities. It also helps to eliminate the human equation leading to human errors stemming from “alert fatigue” and other problems.
Moreover, modern security automation solutions use technologies such as artificial intelligence (AI) and machine learning (ML), allowing security automation to make “intelligent” decisions based on sophisticated data models. Both AI and ML allow organizations to analyze and create a baseline of what normal activity looks like in the environment. Machine learning models can then be “trained” to recognize abnormal behaviors in the environment.
The superior efficiency and split-second decision-making provided by modern security automation help improve businesses’ security posture. It also helps to even the playing field for businesses fighting against today’s sophisticated tools used by cybercriminals. But, while it is easy to see the benefits of security automation in the environment, how can businesses implement it? What factors need to be considered?
Google Workspace Backup Solution Comparison Table
View our competitive pricing chart
*Contact Us for current pricing.
Enterprise Guide to Security Automation
Security automation, like any tool, must be used effectively and appropriately to realize the benefits fully. Let’s look at the following recommendations for implementing security automation in your organization:
- Know when security automation is needed
- Understand which processes to automate
- Do not forget cloud environments
- Use policy-driven security automation
- Use the right security automation solution
1. Know when security automation is needed
There are many tell-tale signs that security automation is needed in your environment. Especially if cybersecurity breaches and other even minor security events are making their way past your security mechanisms in place, it is probably time to start looking at introducing security automation in the environment. Note the following:
- There are security or security-related tasks that take up too much time for a cybersecurity professional to carry out manually
- You have had breach events that have gone unnoticed or were not detected appropriately
- You have an alerting system in the environment, but most alerts go unnoticed
- Security events are taking an excessive amount of time to resolve
- You can’t find enough security talent to fill the needed roles
In general, automation can yield tremendous benefits if your available cybersecurity personnel focus a lot of their time and energy on low-level tasks such as searching through logs, performing routing security triaging, and other tasks.
2. Understand which processes to automate
Automation is an excellent tool as part of a larger cybersecurity picture. Securing business-critical technical resources is a multi-layered approach. So, that being said, automation does not solve every single security challenge, nor does it eliminate the need for humans as part of the overall security equation.
Artificial Intelligence (AI) and machine learning (ML) are pushing the envelope of what is possible in security automation and provide surprising abilities to correlate data and make split-second decisions. However, security challenges still require human reasoning and correlation to be involved, especially to analyze if certain events are false positives or real cyberattacks.
Much of where and when automation is involved may also depend on the capabilities of the cybersecurity solution used. For example, more advanced enterprise security solutions taking advantage of AI and ML will likely be able to carry out more high-level security capabilities.
3. Do not forget cloud environments
One of the mistakes organizations make in thinking about their cybersecurity posture is cloud environments, specifically cloud SaaS. There is a mistaken mindset that cloud SaaS means the cloud vendor is taking care of everything related to security for you. While cloud hyperscalers take care of the physical security of their data centers and underlying infrastructure, your data is still your responsibility, as noted in the shared responsibility model from Microsoft.
Don’t forget about cloud SaaS environments for effective cybersecurity automation. Leverage cybersecurity solutions that leverage AI and ML to help secure your cloud SaaS environment from data leaks, insider threats, ransomware, and others.
4. Use policy-driven security automation
Policy-driven automation takes the heavy-lifting out of configuring security automation and helps align security configurations with the needs of your business. With policy-driven automation, the security configuration itself can be automated. Once the policy change is made, the security configuration is updated to reflect the policy configuration.
Policy-driven security automation also provides many benefits to compliance and audit purposes, as the security policy is, in essence, documentation for the security setting deployed in the environment.
5. Use the right security automation solution
As we have already mentioned, the security solution you choose directly affects businesses’ security automation capabilities. Modern cybersecurity solutions provide security automation that provides policy-driven automation. In addition, leveraging artificial intelligence (AI) and machine learning (ML) capabilities help elevate the level of security automation that can be performed, allowing intelligence split-second decision-making to bolster your security posture.
SpinOne – Intelligent security automation for cloud SaaS
As more organizations move to cloud SaaS environments like Google Workspace and Microsoft 365, securing and protecting business-critical data in these environments is critical. SpinOne is a modern SaaS Security Posture Management providing intelligent security automation for cloud SaaS environments, driven by artificial intelligence (AI) and machine learning (ML) technologies.
SpinOne provides policy-driven security automation allowing businesses to automate the security configuration of their cloud SaaS environment, including a new SpinOne Policies feature. Note the following policies provided by SpinOne:
- Risk assessment policies – The SpinOne risk assessment policies allow cloud SaaS administrators to take action against applications and extensions meeting certain conditions, such as a risk score threshold
- Data policies – Data policies allow administrators to set conditions on cloud storage sharing from their organization
- Domain policies – These policies allow admins to continuously analyze the cloud SaaS environment, detecting things like abnormal downloads and logins.
- Default security settings – The default security policies allow defining settings for applications and Chrome extensions and relate to the risk assessment capabilities provided by Spin
- [NEW!] SpinOne Policies – The new SpinOne policies for Google Workspace Security provide policy-driven automation of onboarding, offboarding, and add-ons management
With the new SpinOne Policies, Spin takes the heavy-lifting out of day-to-day operations that directly impact security – onboarding, offboarding, and Add-Ons management in Google Workspace environments.
Onboarding & Offboarding Entities and Add-Ons management
As organizations hire new employees and shared folders are created, many crucial steps are needed to protect business-critical data. Note the following Onboarding & Offboarding Entities and Add-Ons management capabilities:
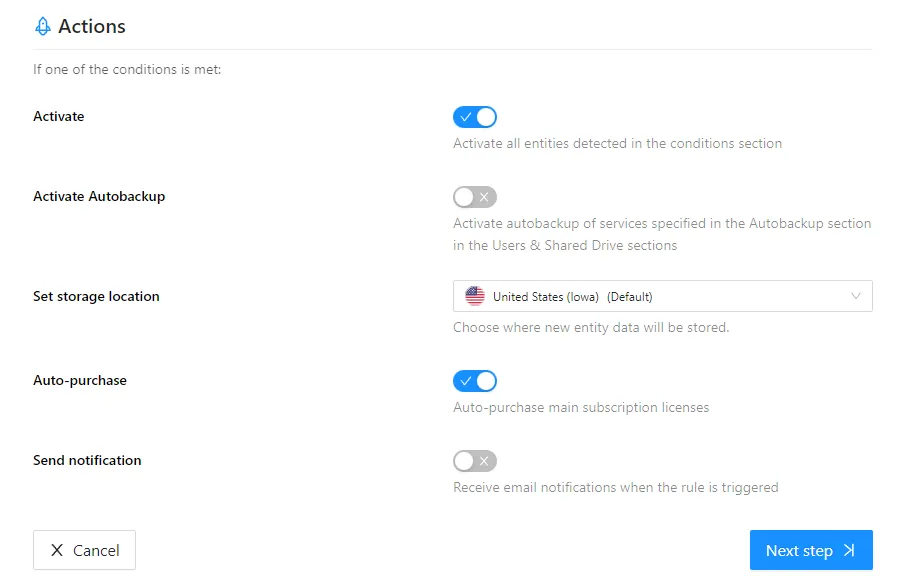
Onboarding:
- Activate – activate all entities detected in the Conditions section. If a user is being activated, a license will be utilized
- Activate Autobackup – enables autobackup based on the configurations specified in the Autobackup section for Users and Shared Drives, respectively
- Set storage location – specify where the entity’s data will be stored. Admins can choose the default storage location for their organization or specify a different area
- Auto-purchase – if there are no available licenses for activating a user, the policy will auto-purchase licenses utilizing the payment method on file
- Send notification – the policy will send a notification to the administrator notifying of what actions were taken place
Offboarding
- Change status- allows converting an activated entity to a different status
- Archive – replaces the main subscription license with an archive license for users
- Deactivate – deactivates the User or Shared Drive from SpinOne (NOTE: Deactivated entity data will be automatically deleted in 30 days. In case an entity has been accidentally deactivated, there is a 30-day grace period to reactivate)
- Suspend Backups – turns off auto backups for detected entities. This is useful for maintaining a snapshot history
- Auto-purchase archive licenses – if there are no available archive licenses for archiving a user, the policy will auto-purchase licenses utilizing the payment method on file
- Send notification – the policy will send a notification to the administrator notifying of what actions were taken place
Add-ons management
- Storage Add-Ons – applicable to the SpinOne, SpinSecurity, and SpinBackup subscription plans
- Apps Add-Ons – applicable to the SpinApps subscription plan only
Final Notes
Automation provides a powerful way for organizations to meet the challenges of cybersecurity in the new cloud era, and it also helps to deal with the shortage of cybersecurity talent. Organizations can automate low-level security tasks with effective security automation, burdening cybersecurity professionals who may already be “alert fatigued.”
Modern security automation platforms use artificial intelligence (AI) and machine learning (ML) to make intelligent split-second decisions based on security signals in the environment. SpinOne is a robust cybersecurity solution for cloud SaaS environments using AI and ML technologies to provide policy-driven automation. The new SpinOne Policies help automate activities such as onboarding and offboard and add-ons management, assisting businesses to protect their business-critical data in the cloud.Learn more about SpinOne and its effective policy-driven security automation here: Spin Technology data protection and cybersecurity
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
What You Need to Know About AT&T’s Data Breach and How t...
Arguably, it is one of the worst breaches that has happened recently. AT&T disclosed in...
Lessons from the Twilio Breach: Securing SaaS Applications Against ...
Another recent security breach has made organizations think yet again about SaaS apps they may...
Unpacking the CrowdStrike Outage: Causes, Impacts, and Protecting Y...
A major global IT outage occurred on Friday, July 19, 2024, causing widespread disruptions across...



