SaaS Security Posture Management (SSPM) vs. Traditional Security Measures: A Comparison
What to choose and which is better? Today we compare SaaS Security Posture Management (SSPM) vs. Traditional Security Measures.
Traditional Security
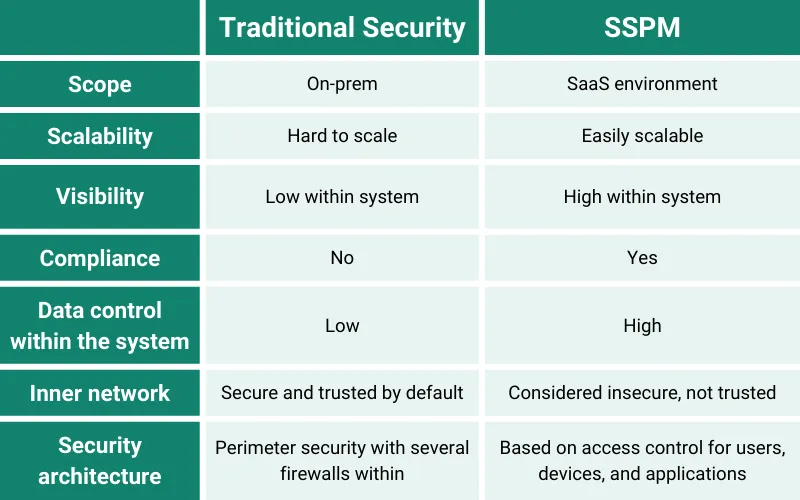
When talking about traditional security, we usually imply the security architecture that has existed for a couple of decades now. It is still used by companies that have on-prem IT systems.
The architecture of such security is quite simple. You have a network of computers, usually located in one place. They are interconnected and exchange data. You trust these devices by default because they exist within the “perimeter.”
Any devices or applications outside the network connect with it via security equipment and software that prevents dangerous transmissions of data (e.g., a cyber attack).
Within the network, you can have one or several data centers, and your devices are connected to it. In addition to that, you can build inner firewalls, to add one more security layer.
Such a system has a limited and well-protected number of connections with the “outer” world. It is hard to scale it. And visibility within the network is limited.
SaaS Security Posture Management
In the past decade, we’ve seen companies rapidly moving their operations to the cloud and then SaaS platforms. Cloud office suites like Google Workspace or Microsoft 365 provided immense capabilities for businesses of all sizes. They attracted clients with multiple possibilities including:
- cutting costs on building and maintaining internal IT infrastructure,
- working and hiring people all over the world
- greater computing powers at lower prices
- flexibility and scalability that on-prem solutions lacked
- constantly growing number of third-party productivity applications.
Unfortunately, some of the strongest and most wanted features of SaaS applications quickly became their weaknesses.
For example, the access to the environment from any point in the world made them easy targets for cyber attacks. Now any user could be a criminal in disguise. And the growing amount of third-party applications with easy OAuth access turned out to be a Shadow IT nightmare.
At the same time, legislations of many countries began catching up with the digital transformation of the world. New laws and regulations regulating data security were introduced. They mandated certain security measures and provided fines for non-compliance.
The traditional security architecture wasn’t effective in the cloud with its hundreds of entry points that can be opened anywhere around the world and enhanced security compliance audit. That’s how the idea of the new security architecture came into being.
SaaS Security Posture Management is the approach to SaaS security that is based on data visibility, misconfiguration detection, and application control.
Learn more about SSPM here.
SSPM vs. Traditional Security
In this section, we sum up the differences between SSPM and traditional security. Both are good security architectures in their respective areas. SSPM is great for SaaS environments, and traditional security is great for on-prem systems.
SpinOne SSPM – the best choice for your organization
To protect your SaaS environment, use modern SaaS Security Posture Management – SpinOne. It works for Google Workspace and Microsoft 365. The functionality includes:
- Control of misconfigurations in the cloud
- Detection and risk assessment of OAuth applications
- Detection of abnormal data behaviour
- Control of insider threats like unauthorized access.
- Monitor of abnormal user behavior.
- Enhanced automation through security policies.
- Immediate alerts and advanced reporting.
FAQs
What is SaaS security posture management?
SaaS Security Posture Management is an umbrella term for tools that help improve security within SaaS environment.
What is Traditional IT security architecture?
Traditional IT security architecture is the security build for on-prem environments. It focuses on building strong perimeter secuirty while trusting inside devices.
What is the difference between SSPM and CSPM?
Cloud Security Posture Management includes security posture management solutions for all cloud environments (IaaS, PaaS, SaaS). SSPM only focuses on SaaS solutions.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...

