SaaS Security Posture Management
Protect SaaS data with SpinOne SaaS Security Posture Management (SpinSPM)
SSPM Advantages for Enterprise
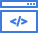
Over 80% of organizations have SaaS misconfigurations and risky, third-party applications that lead to immediate security threats. For Security teams who need to reduce risks of misconfigurations and Shadow IT, SpinSPM is a SaaS Security Posture Management solution that provides full visibility and automated incident response to save time, reduce security costs, and improve compliance. Unlike other SSPM solutions, SpinSPM provides automated, in-depth risk assessments outlining security and compliance risks by leveraging our unique database of over 400,000 apps and browser extensions assessed by AI algorithms.
SpinSPM is recommended and integrated by Google, recognized as a Strong Performer in the Forrester SSPM Wave report, and trusted by 1,500+ organizations worldwide.
SaaS security for every use case
Related Solutions
Application & Browser Extension Risk Assessment Tools
Why Businesses Choose SpinSPM
What Makes SpinSPM Different?
Powerful Assessment Done in Minutes

SpinSPM is the only SSPM solution that assesses browser extension risk for Microsoft Edge and Google Chrome. In fact, SpinOne was selected by Google to be integrated into its Console to assess the risk of sanctioned and unsanctioned browser extensions.
Shadow IT and Third-party App Discovery

SpinSPM has discovered and assessed over 400,000+ OAuth applications and browser extensions using its AI-algorithms, helping organizations reduce risk assessment time from months manually to seconds automatically.


Granular Risk Assessment

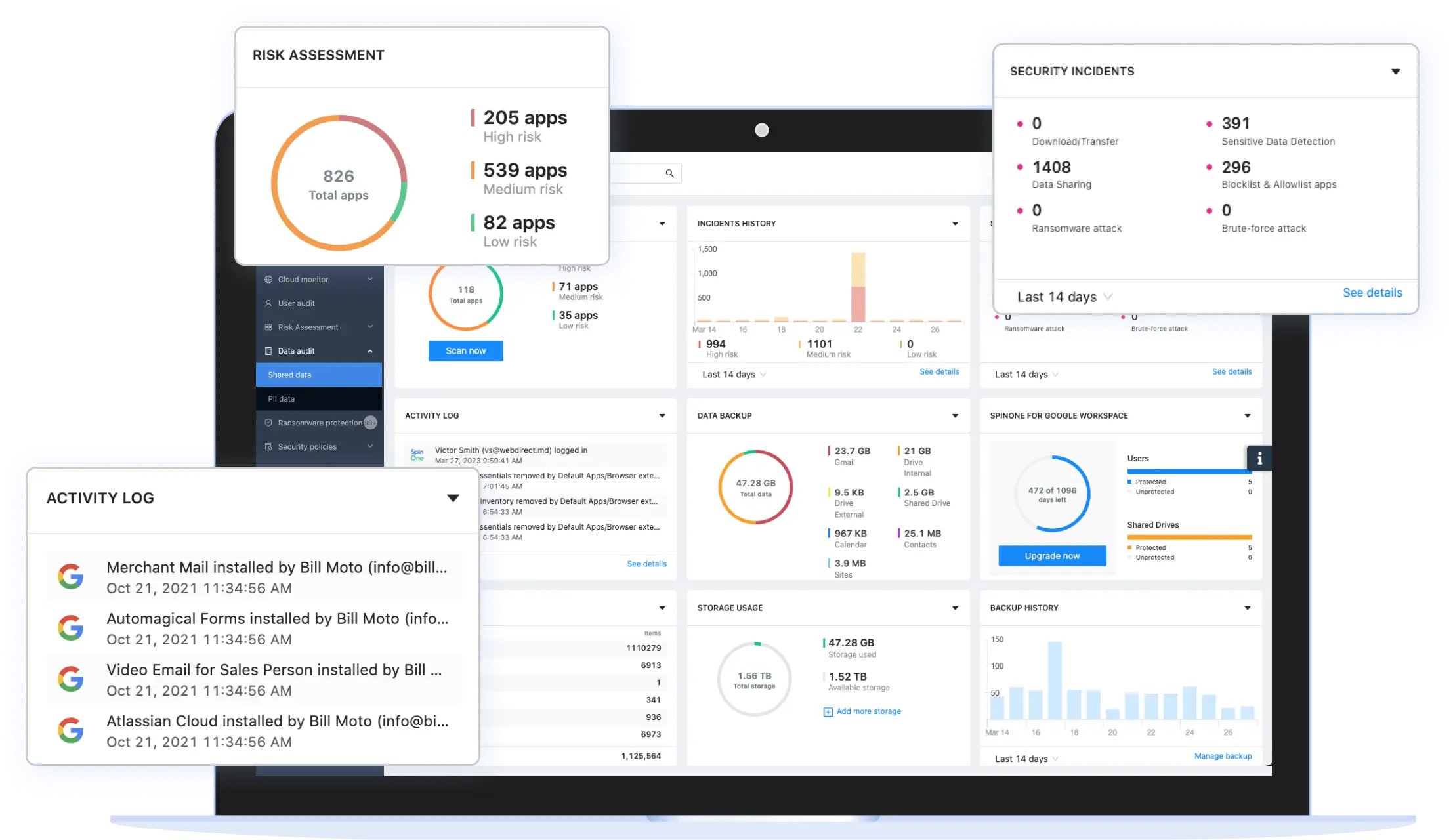
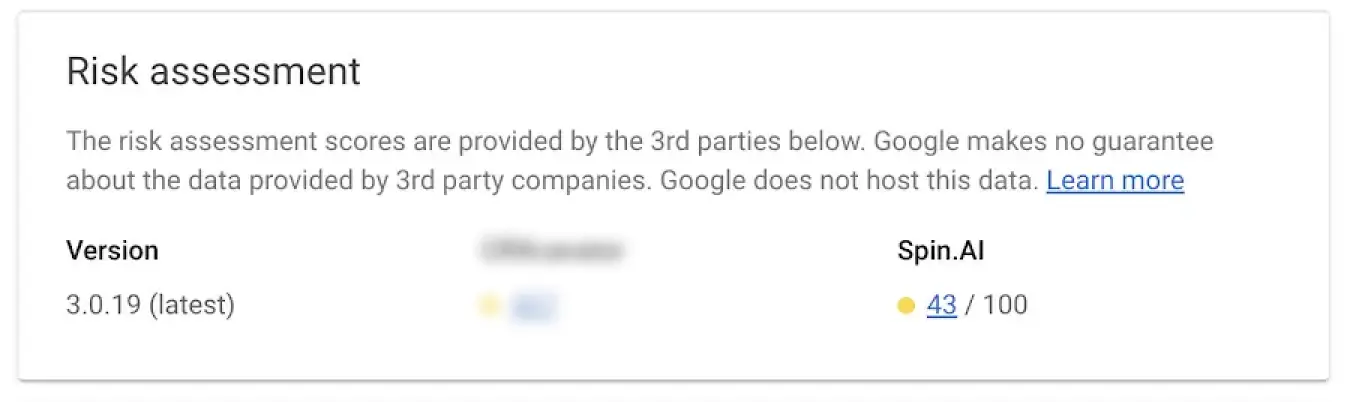
SpinOne uses over 15 factors to assess the application and extension risk, and breaks the assessment down into the following sections: scope of permissions, external communications, business operation risk, security risk, and compliance risk. Based on this data each app receives a security score from 0 to 100 to zero in on the riskiest applications and extensions and facilitate your decision-making process.
Customizable and Automated Access Management and Incident Response
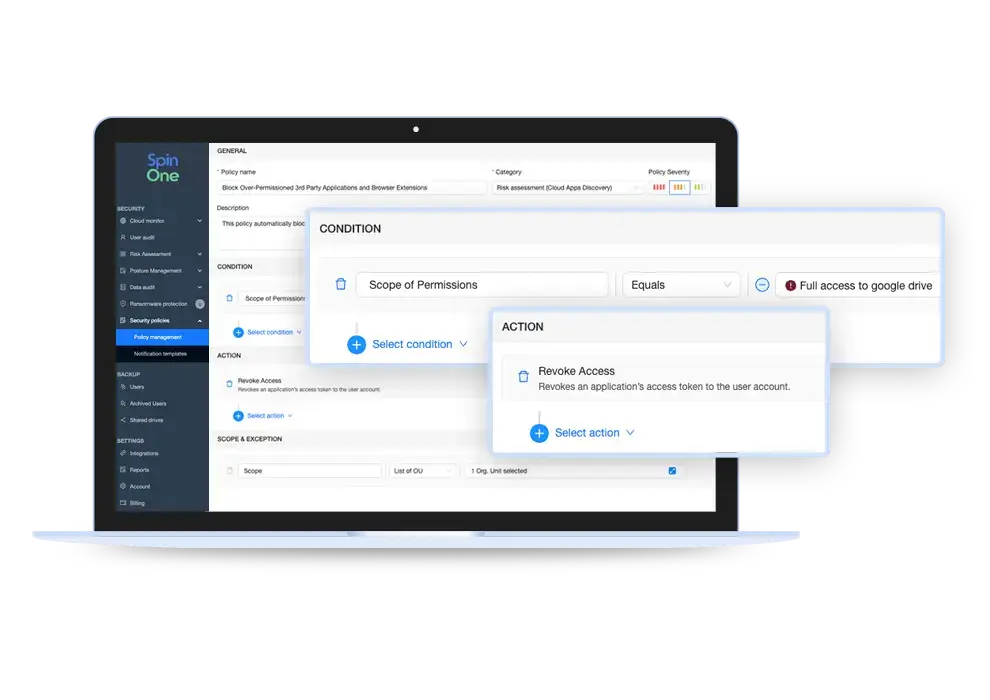
SpinSPM offers full control over access management and incident response cases by providing organizations the ability to customize their responses so they can fulfill their unique use cases. SpinOne also automates the access management and incident response process through highly configurable policies.

All-in-one SaaS Security Platform
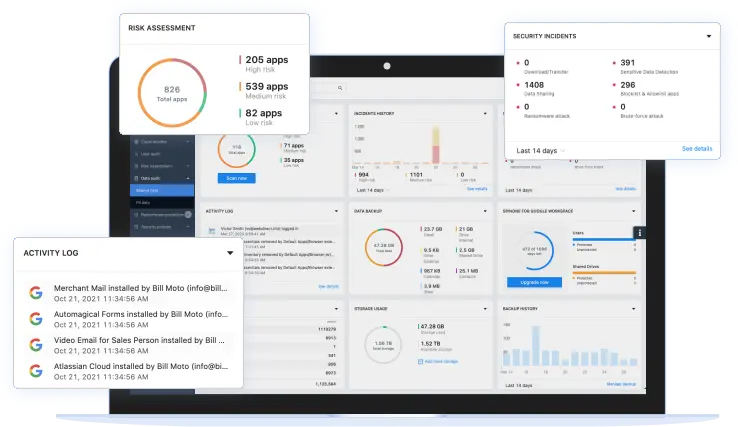
SpinSPM is a solution within SpinOne, the all-in-one SaaS security platform for mission-critical SaaS apps, that protects SaaS data for Google Workspace, Microsoft 365, Salesforce, and Slack. SpinOne provides SSPM, SaaS DLP, SaaS ransomware protection, and SaaS backup for more than 1,500 organizations worldwide to enhance cyber resilience, streamline security operations, and reduce security costs.
Recognition

- Best Ransomware Protection
- Market Leader SaaS/Cloud Security
- Hot Company Secure SaaS Backup
Business Intelligence Group Award for Business 2023
- Dmitry Dontov Named Small Business Executive of the Year
- Next Gen SaaS Security
- Hot Company in App Sec
- Hot Company in DLP
- Cutting Edge Ransomware Protection

2023 Cyber Top Innovation Award
- Presented by Enterprise Security Tech

Top 10 SaaS Solution Providers
- According to GRC Outlook Magazine

Top Cloud Security Solutions Provider
- According to Enterprise Security Magazine

2021 Cloud Computing Security Excellence Award
- Presented by Cloud Computing Magazine

2023-24 DCIG Top 5
- Top SaaS Backup Solution for Microsoft 365
What is SaaS Security Posture Management (SSPM)?
The growing risks of uncontrolled Shadow IT and cloud configuration call for a solution that will help companies close these security gaps.
SaaS Security Posture Management (SSPM) refers to the security solutions and tooling needed for automated continuous monitoring and visibility of an organization’s SaaS apps in the cloud SaaS environment.
It helps to minimize cloud misconfigurations and security risks of SaaS apps and provides native security controls to help protect sensitive data housed in cloud services. In addition, it bolsters the security team by providing 24x7x365 monitoring of the environment, quickly detecting security gaps in cloud apps, and allowing SecOps to address security issues effectively or use automated responses to remediate these.
Frequently Asked Questions
- SpinSPM FAQs
- SSPM FAQs
How does SpinSPM help organizations secure their clouds?
While cloud SaaS is ripe with modern tools and technologies empowering businesses, it can equally be filled with security pitfalls using SaaS applications. For example, cloud misconfigurations, risky third-party applications, shadow IT, ransomware, data leakage, and many other threats can jeopardize critical and sensitive data and lead to security breaches. SpinSPM provides the capabilities needed for automated continuous monitoring and visibility of an organization’s SaaS apps in the cloud SaaS environment. It helps to minimize cloud misconfigurations and security risks of SaaS apps and provides native security controls to help protect sensitive data housed in cloud services. In addition, it bolsters the security team by providing 24x7x365 monitoring of the environment, quickly detecting security gaps in cloud apps, and allowing SecOps to address security issues effectively or use automated responses to remediate these.
Does SSPM cover third-party applications as well?
Yes. SSPM helps you inventory and gain visibility of all third-party cloud services, mobile apps, generative AI (GenAI) apps, and SaaS apps that have access to Google Workspace, Microsoft 365, and Slack and understand who has access to these apps. Unlike other SSPM solutions, SpinSPM goes a step further by also providing visibility into third-party browser extensions.
How do I get started with implementing SSPM for my organization?
Implementing SSPM and understanding SaaS security posture is incredibly important as it helps organizations understand their vulnerabilities and how these can be corrected. An SSPM checklist can help you get started, including these steps:
- Evaluate data that isn’t protected
- Provide visibility to data sharing
- Detect and remediate malicious threats
- Harden SaaS configurations
- Evaluate the risks of SaaS apps
Why Do Enterprises Need SaaS Security Posture Management (SSPM)?
Over 75% of third-party SaaS applications are considered medium or high-risk applications according to our App Risk Report. And nearly 50% of installed extensions are high risk according to our Extension Risk Report. To respond to these SaaS risks, SSPM provides automated visibility and scanning of configurations, settings, and permissions to ensure these are configured according to security and compliance best practices. SSPM automation saves manual hours for SecOps professionals since SSPM can carry out the tedious manual tasks of analyzing configurations and continuously scanning for security and compliance risks.
What is the SpinSPM pricing model?
Please see the pricing page for details on SpinSPM and all our packages.
Does SpinSPM support compliance with industry regulations such as GDPR or HIPAA?
Yes, SpinSPM helps support compliance with GDPR, HIPAA, and other laws, regulations, and standards by offering secure 1x or 3x daily backups, 256-bit AES encryption, automated policy-based controls over data sharing, robust access control, and more.
Can SpinSPM be deployed on-premises, or is it cloud-based only?
SpinSPM is an exclusively SaaS-based solution. It cannot be deployed on-premises.
Does SpinSPM scale with the growth of an organization’s SaaS usage?
Yes, SpinSPM can scale effectively with an organization’s SaaS usage growth. It is designed to handle large and complex SaaS environments, scaling to support additional users, applications, and data volumes as the organization expands. In addition, you can adapt security policies, monitor settings, and ensure compliance measures to suit your organization’s evolving needs.
What kind of reporting and analytics does SpinSPM offer?
All essential alerts, reporting, and analytics are accessible on a unified SpinSPM dashboard. Administrators can enable real-time alerts by connecting with Splunk, ServiceNow, Jira, and Slack. Furthermore, SpinSPM offers detailed activity reports on a weekly and monthly basis.
How many third-party applications does SpinSPM detect?
SpinSPM leverages a unique database of over 400,000 apps and browser extensions assessed by our AI algorithms. It can detect a wide range of third-party applications, generative AI (GenAI) apps, and SaaS apps that have OAuth access to the SaaS data we protect in Google Workspace, Microsoft 365, Slack, and Salesforce.
What are the key benefits of SpinSPM?
SpinSPM enhances your overall security posture, reduces security costs, and improves compliance by:
- reducing the risk of misconfigurations and shadow IT
- providing automated, in-depth risk assessments
- ensuring complete visibility over your SaaS environment
- providing automated incident response
What is the recommended workflow with SpinSPM?
As an administrator, you first install the SpinOne app from the Google or Microsoft Marketplace and then set up necessary security posture management policies to identify misconfigurations, Shadow IT, and other threats. Once configured, SpinSPM initiates automated application risk assessments and provides automated incident responses.
What type of access permissions does SpinSPM require and why?
To start using SpinSPM, an administrator login is required. Admin-only access heightens data security and enables more efficient supervision and administration of the platform’s features
What vendors have integrated with the Spin.AI Chrome Extension Risk Assessment?
What is SaaS security posture?
An enterprise’s security posture refers to the overall security state of all software, hardware, configurations, services, networks, and applications as part of the technical landscape. It is a good indicator of how the organization can defend against security threats and security risks as these come along. When related to SaaS, all the same principles apply. However, the underlying infrastructure security is fully managed since SaaS is located in a cloud provider data center. Therefore, the focus shifts to the security stance and configuration of the SaaS applications.
How to choose the Right SaaS Security Posture Management (SSPM) Solution for Your Organization?
To choose the right SaaS Security Posture Management (SSPM) solution for your organization, consider the following factors:
- Centralized Platform: Opt for a solution with comprehensive functionality to avoid using multiple tools.
- Integrations: Ensure compatibility with the tools your business already uses.
- Monitoring & Incident Reporting: Look for 24/7 monitoring and effective reporting methods, like email alerts.
- Application Coverage: Confirm how many applications the SSPM detects and how often the database updates.
- Risk Assessment: Evaluate the criteria and scoring method for app risk assessment.
- Access Revoke: A feature to revoke high-risk app access is essential for swift risk mitigation.
- Blocklisting & Allowlisting: Supports a zero-trust approach, preventing shadow IT issues.
- Security Policies: Ensure the SSPM allows configurable security policies based on app risk.
- Employee Request System: Streamlines app acquisition requests for IT management.
- Customization: Look for platform customization to align with your unique security needs.
- Support: Confirm the availability of round-the-clock support.
- Pricing: Assess the value in terms of cost savings, automation, and incident prevention.
What are SSPM Key Features and Capabilities?
The three key features of every SSPM include detection, assessment, allowlisting and blocklisting. Detection is essential as cloud environments usually lack functionality that provides visibility into the OAuth applications that have access to them. Assessment is essential to make informed decisions on whether to keep an application or block it. It helps the security team cut time on manual app risk assessment. Finally, the ability to create allowlists and blocklists can automate even further the process for the team.
What is the difference between SSPM and CASB?
Many people, and even cybersecurity professionals, find it difficult to tell the difference between CASB and SSPM solutions. There are some similarities between them. For example, both are security solutions that are deployed in the cloud and help prevent cyber incidents.
However, CASB differs from SSPM when it comes to application, deployment, timing, and scope. Let’s take a closer look at each of these aspects.
Application: CASBs work with both on-premise and cloud environments, while SSPMs are cloud-only solutions.
Deployment: SSPMs are typically subscription-based, whereas CASBs can be either SaaS or on-premise tools, sometimes requiring additional hardware to operate.
Timing: Unlike SSPMs, CASBs do not identify the security incidents after they take place.
Scope: CASBs mainly manage cloud data access, while SSPMs offer a broader view, identifying vulnerabilities and helping to remediate them across the entire cloud environment.
Streamlined Enterprise Security for SaaS Data
SaaS data security is our top priority. We’ve introduced several processes and regulations to protect your enterprise SaaS data and enhance compliance.