SaaS Security: Third-party Application Risk Mitigation Guide
Business productivity generally comes down to critical applications that allow employees to interact with sanctioned services and business-critical data. Organizations are migrating to cloud Software-as-a-Service (SaaS) environments in mass as hybrid work configurations continue moving forward. One of the tremendous value-adds with cloud SaaS environments is integrating third-party applications for extended features and capabilities in the environment. However, while they are great for extended features and capabilities, these add cybersecurity risks. In this article, we are discussing cybersecurity risks associated with third-party cloud SaaS apps as well as efficient methods of application risk mitigation.
Third-party cloud SaaS applications – Extended capabilities and SaaS security risks
Not only do cloud SaaS environments like Google Workspace and Microsoft 365 have robust native applications as part of the offering, but there are also thousands of third-party applications that can integrate with the cloud SaaS environment, extending capabilities and features.
These cloud SaaS apps include business tools, productivity apps, education, communication, utilities, and many others. By default, users can download and integrate third-party applications into the sanctioned cloud SaaS environment in either Google Workspace or Microsoft 365.
Google Workspace Marketplace
While third-party applications can add capabilities far beyond those natively provided by the cloud SaaS service provider, these introduce cybersecurity risks in the environment. How so?
Even legitimate third-party applications may have their own set of security standards, data risks, and other concerns associated with integrating them with your business-critical data. These applications assume the permissions of the user granting it access to the environment. While it may be ok for a particular user to have the ability to read data that could be considered sensitive, it may not be ok for the application to assume these same permissions.
Third-party applications can be granted elevated permissions to all sorts of business-critical and even sensitive data due to cloud OAuth permissions delegation. OAuth permissions delegation gives an authorization token to cloud SaaS applications that allow “acting on behalf” of the user granting the OAuth token. Thus, it enables users to integrate third-party applications without the application knowing the user’s password.
Cloud SaaS OAuth tokens are persistent and even bypass two-factor authentication. As a result, they must be issued with care. For example, imagine a malicious third-party cloud SaaS application or browser plugin granted access to business-critical data in your cloud SaaS environment. It could delete, leak, or easily steal data. Worse, it could have the ability to launch a ransomware attack in the environment.
Businesses must maintain visibility and control over cloud SaaS applications, including third-party applications and browser plugins, installed in the environment. A single malicious cloud SaaS application or browser plugin granted permissions to the environment can jeopardize a business’s entire data set from a security perspective.
Remote work leading to more security threats
The now majority remote workforce has led to further cybersecurity vulnerabilities. Remote workers tend to be more distracted and laxer in overall security awareness working from home. Statistics show that remote work increases cybersecurity risks and the overall cost of a data breach. Note in the IBM Cost of a Data Breach 2021:
The average cost was $1.07 million higher in breaches where remote work was a factor in causing the breach, compared to those where remote work was not a factor. The percentage of companies where remote work was a factor in the breach was 17.5%. Additionally, organizations that had more than 50% of their workforce working remotely took 58 days longer to identify and contain breaches than those with 50% or less working remotely. IT changes such as cloud migration, and remote work increased costs, yet organizations that did not implement any digital transformation changes as a result of COVID-19 experienced $750,000 higher costs compared to the global average, a difference of 16.6%.
As employees work remotely, they may be more likely to grant permissions requested by third-party applications. Remote employees may also be more likely to fall victim to phishing attacks where an attacker masquerades a malicious application as legitimate.
For example, an employee may get an email posing as a “security update” for their cloud SaaS environment. While it is a malicious app, employees may think they are granting permissions to a sanctioned or legitimate application. A malicious application requesting permissions looks identical to any other application that may request permissions to cloud SaaS data.
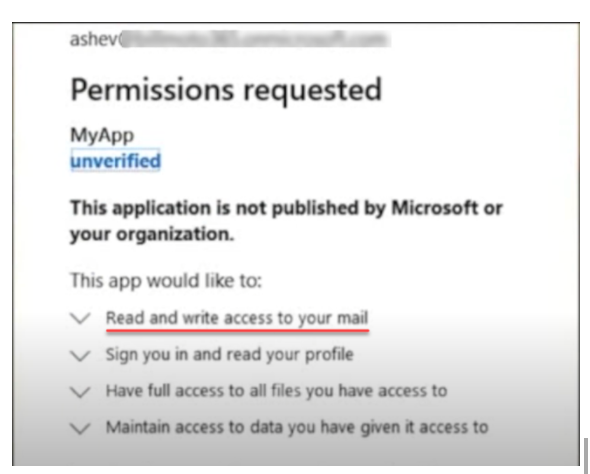
In the example below, a malicious application is requesting:
- Read and write access to your mail
- Sign you in and read your profile
- Have full access to all files you have access to
- Maintain access to data you have given it access to
The malicious application can read, delete, steal, or ransomware your data with this set of permissions.
Cloud SaaS application requesting permissions
Organizations can’t rely 100% on email filtering and other security measures to filter out malicious emails before making it to the end-user mailbox. So how can organizations take control of cloud SaaS applications and ensure business-critical data is protected?
Prevent third-party application risk and threats in cloud SaaS
Organizations looking to prevent data protection and security issues with business-critical data must take control of cloud SaaS applications and browser extensions allowed to integrate into the environment. SpinOne is a SaaS Security Posture Management (SSPM) platform that provides world-class data protection and security for Google Workspace and Microsoft 365 cloud SaaS environments.
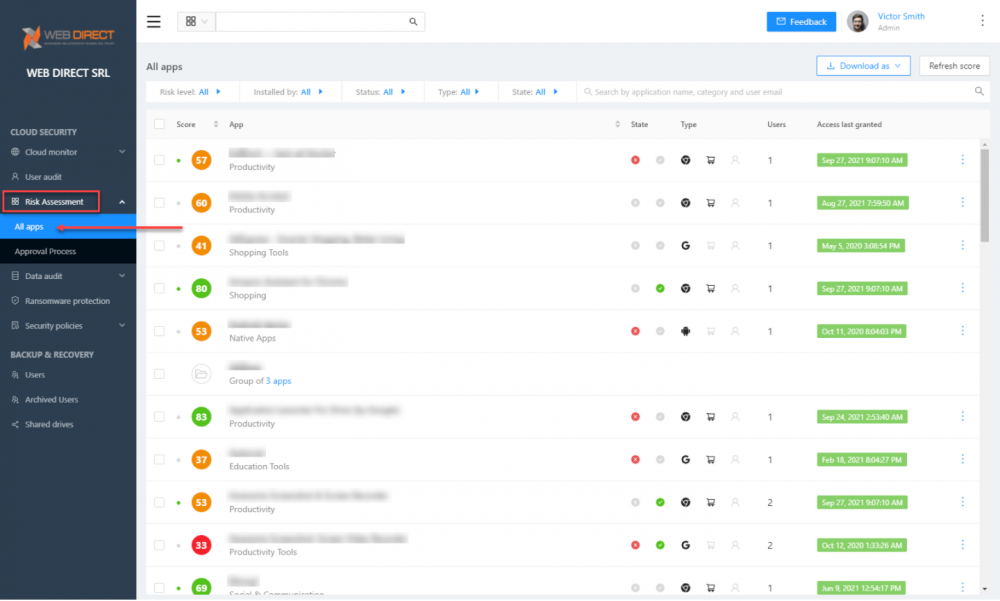
SpinOne provides visibility, control, and approval workflows for integrating cloud SaaS applications into the environment. In addition, using the SpinOne Risk Assessment module, organizations can proactively monitor and secure their cloud SaaS environments from the risk of malicious applications. SpinOne uses artificial intelligence (AI) and machine learning (ML) to scan and assess the risk of any integrated third-party application automatically. It can perform in seconds to minutes what would take a SecOps professional hours to do for a single application.
Note the following visibility IT admins get to third-party applications:
- Risk assessment score
- App name
- State
- Type of application
- Users who have installed the application
- When access was last granted.
SpinOne’s Risk Assessment module provides automated auditing of cloud SaaS applications
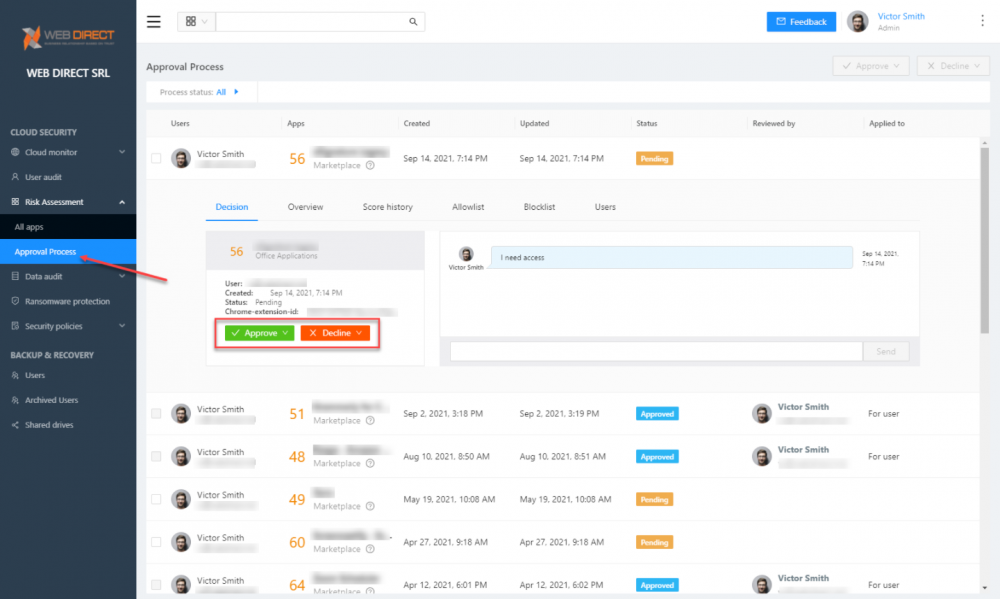
SpinOne provides a streamlined approval workflow that allows easily approving or declining applications requested by end-users.
SpinOne approval process for approving or declining cloud SaaS application access
Using SpinOne policies, organizations can define explicit applications allowed for installation in the environment. Additionally, once an application is blocked, any attempts to install the application in the environment will be disallowed.
SpinOne’s policy-based approach ensures business-critical data is protected from rogue or untrusted applications that users may fall victim to in a phishing attack. In addition, to bolster the protection offered by the cloud SaaS application risk assessment, SpinOne has industry-leading ransomware protection for Google Workspace and Microsoft 365.
The proactive ransomware protection provided by SpinOne uses security automation to stop ransomware quickly. It carries out the following actions, proactively combatting ransomware:
- SpinOne continuously scans for the signs of ransomware attacking the environment
- If ransomware is detected, SpinOne forcibly removes the network connection from the ransomware process
- It performs scans of the environment to find affected files
- Any affected files found are automatically recovered from the last good SpinOne backup (configurable)
- It then automatically notifies administrators
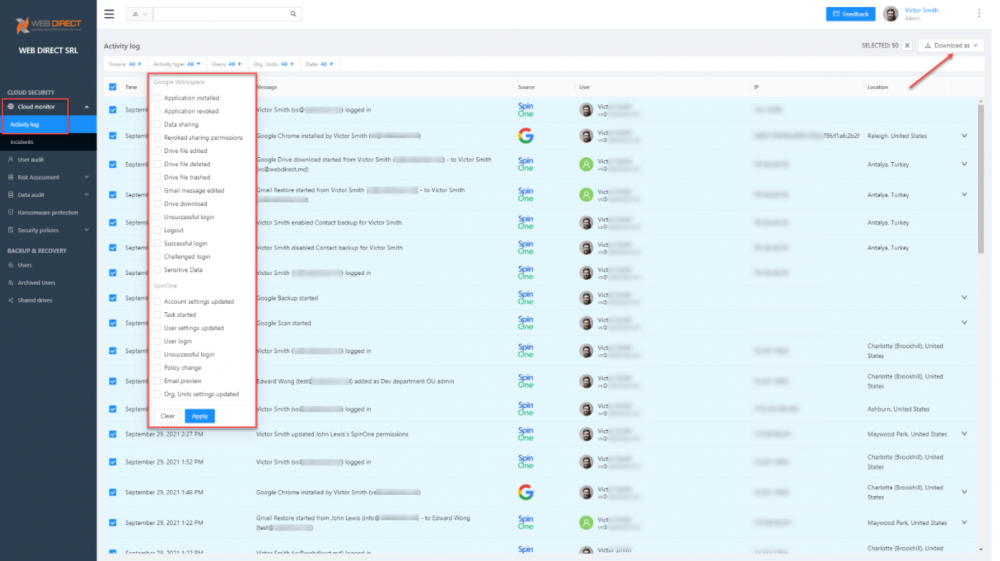
This proactive cloud SaaS application security and ransomware protection approach provides the 1-2 punch organizations need to defeat cloud SaaS ransomware attempts. In addition to the assessment and monitoring of cloud SaaS applications and ransomware protection, SpinOne gives IT admins and SecOps professionals visibility to user activities in the cloud SaaS environment. The SpinOne Cloud Monitor > Activity Log dashboard shows cloud SaaS activities and SpinOne-specific logging in a single-pane-of-glass view.
SpinOne Cloud monitor activity log
If you want to learn more about the robust cybersecurity and data protection features offered by SpinOne and sign up for a demo call, click here.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...