Remote Workforce Risk
SpinOne protects businesses by helping them connect with their remote workforce securely and by mitigating cloud security risks.
Businesses that ignore cloud SaaS security face many threats, including cloud data leakage, compliance violations, and ransomware. By understanding the top security concerns for the remote workforce and taking the time and effort to mitigate them, you can protect your company’s SaaS data.
Top 3 Remote Work Cloud Security Risks in 2022
Insecure remote networks and devices. With the increasing number of employees working remotely, security threats are evolving to be more diverse, complex, and potentially severe. SaaS threats can now infiltrate home networks and personal devices, threatening corporate data and sensitive information. Remote employees have access to confidential corporate information and data anywhere, putting teams and departments at risk of malware, ransomware, and data breaches. Recent surveys reveal that more than 50% of businesses have lost data due to employee negligence.
Third-party cloud SaaS applications. Google and Microsoft give you access to thousands of third-party applications in their respective cloud SaaS environments. Third-party cloud SaaS applications can augment your core business. SaaS apps can help automate routine tasks, fix common errors, and reduce the amount of time you spend on in-house development. The flipside of cloud SaaS applications is security threats. For example, malicious hackers create fake apps to steal your data, spy on your network traffic, or turn your PC into a botnet zombie, masquerading a malicious application as a legitimate one. Unsuspecting end-users may grant high-level permissions to cloud SAAS applications without much scrutiny.
Phishing, ransomware, and SaaS data breaches. Remote employees are more susceptible to phishing and ransomware attacks than employees working on-premises. Data breach risks can also be enhanced with remote workforces. They may be more apt to be responsible for cybersecurity breaches due to increased distractions, insecure networks, and more. Businesses today must have highly robust cybersecurity defense solutions that protect cloud SaaS environments from ransomware, data loss, and data leak threats.
“The average cost was $1.07 million higher in breaches where remote work was a factor in causing the breach, compared to those where remote work was not a factor. The percentage of companies where remote work was a factor in the breach was 17.5%. Additionally, organizations that had more than 50% of their workforce working remotely took 58 days longer to identify and contain breaches than those with 50% or less working remotely. IT changes such as cloud migration and remote work increased costs, yet organizations that did not implement any digital transformation changes as a result of COVID-19 experienced $750,000 higher costs compared to the global average, a difference of 16.6%.”
— IBM Cost of a Data Breach 2021 report
Keep Your Remote Workforce Protected
SpinOne is a robust data protection and cybersecurity solution for modern cloud SaaS environments, including Google Workspace, Microsoft Office 365, and Salesforce. SpinOne allows businesses to have visibility and control over data sharing, user activity, and third-party cloud SaaS applications in a seamless single-pane-of-glass dashboard.
- Create automated clean backups of cloud SaaS data
- Provide visibility into cloud SaaS events
- View and control cloud SaaS data sharing and downloads
- Automatically audit and control third-party cloud SaaS applications
- Proactively protect cloud SaaS environments from ransomware
All SaaS Security Needs Covered
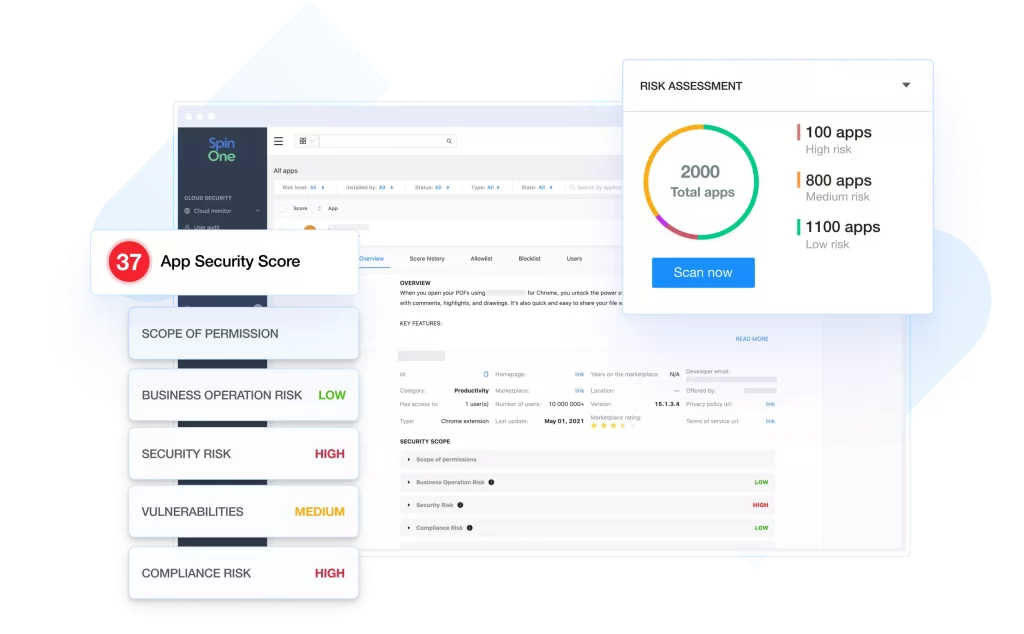
SaaS Application Risk Assessment. SpinOne helps organizations identify if there are any third-party cloud applications or browser extensions integrated into their environment. SpinOne does this by scanning for installed third-party apps and putting these applications through its risk assessment process. SpinOne quickly rates the applications based on cybersecurity and reputation metrics. This way, SpinOne can see both the past and future behavior of the app. This means that if the app’s behavior changes, SpinOne can detect it and block it from SpinOne policies.
- Gain visibility into cloud SaaS and SpinOne events
- View and control cloud SaaS data sharing and downloads
- Automatically audit and control third-party cloud SaaS applications
SaaS Ransomware Protection. SpinOne’s Ransomware Protection module is proactive and uses artificial intelligence and machine learning to combat ransomware attacks. Businesses can limit damage from ransomware, ensuring that critical data is not leaked to the dark web. SpinOne has a variety of security measures in place, such as automation, to make sure you’re always protected from this dangerous cyber threat. It also helps business owners be confident in their cloud SaaS environments, which are defended against hazardous new ransomware threats.
- SpinOne continuously scans for the signs of ransomware attacking the environment
- If ransomware is detected, SpinOne forcibly removes the network connection from the ransomware process
- It performs scans of the environment to find affected files
- Any affected files found are automatically recovered from the last good SpinOne backup (configurable)
- It automatically notifies administrators of the attack and remediation.
SaaS DLP Capabilities. It’s important to back up cloud SaaS data because it can be deleted remotely by an end-user, malicious application, or attacker. SpinOne provides enterprise-grade protection for your cloud SaaS data. It backups your data multiple times per day and recovers it in a granular or bulk manner when needed. The SpinOne’s SaaS DLP features include:
- Automatic backups multiple times per day
- Ability to store backups across numerous cloud storage locations
- Encrypted backups in-flight and at-rest
- 100% recoverability of your data
- Protection from ransomware and other attacks
Best practices for securing the remote workforce
- Secure authentication
- Protect against phishing attacks
- Visibility of user behaviors, applications, and data sharing
- Ransomware protection
- SaaS application security automation
Start Making the Most of Your SaaS Security
It only takes a few steps to get started with our demo.