Alarming Ransomware Facts & Stats To Know
Ransomware is a highly lucrative business for attackers who are making millions by victimizing companies and locking up their data. Damages from cybercrime are expected to hit $6 trillion. The highly profitable nature of ransomware attacks is helping to drive the ransomware pandemic. In addition, it helps emphasize businesses need to increase their cybersecurity posture against ransomware and other attacks. Let’s take a look at recent ransomware attacks and the groups responsible. How can businesses protect data, both on-premises and in the cloud?
Top Ransomware Attacks 2023
In 2023, we witnessed an abrupt spike in ransomware attacks. In fact, the number of attacks during Q1-Q2 reported in media exceeded the number of attacks that were reported throughout 2022. In summer, we saw a substantial decline, but cyber crimes have been gaining momentum since mid-August.
The most significant attacks in 2023:
- Application MOVEit
The successful attack on MOVEit resulted in a vulnerability exploit with subsequent attacks on 600 organizations that used the application. The estimated number of victims is 40 million people. The exploit took place in late May, however, the news about new affected firms kept emerging till late September.
- The city of Dallas
The ransomware attack had a horrible toll on the entire city, disabling its police, fire department, and other critical public services. The lingering effects were still tangible several months after the original attack in May. The attack allegedly included the PII theft.
- Point32Health
Throughout the year hackers targeted multiple healthcare organizations. The most impactful events involved Point32Health, the company that oversees health plans for multiple clients, including some major universities.
- Managed Care of North America (MCNA) Dental
In the March attack on one of the largest North American dental insurers, LockBit ransomware gang stole 700GB of sensitive data.
- Prospect Medical Holdings
The major US hospital network was attacked in August. Many institutions of the network suffered outages and downtime.
- Barts Health NHS Trust
This attack encompassed the largest healthcare data breach in UK. The ransomware gang BlackCat (ALPHV) allegedly stole 7TB of sensitive data.
- Johnson Controls International
The multinational giant that employs 100,000 people worldwide and produces industrial control systems and security equipment was attacked in September. The hackers managed to exfiltrate 27TB of data and demanded $51 million. The stolen data allegedly contains the sensitive information of the Department of Homeland Security.
Check out our Ransomware Tracker, the list of Ransomware attacks for the past 4 years that is updated on a weekly basis.
Ransomware Statistics 2023
We collected the most recent ransomware statistics:
- The average ransom payment is $812,360
- The average total cost of ransomware attack is $4.5M
- On average it takes 49 days more to identify and remediate ransomware breach than other types of attacks
- Ransomware comprises 10% of all breaches.
- LockBit gang was behind more than a third of all global incidents (35%)
- The average weekly attacks per organization worldwide reached over 1,130 in 2022
- 36% of companies that paid a ransom to were targeted for a second time.
- 41% of those that paid ransom failed to recover all their data.
- More than 40% of those that paid ransom still had to rebuild their systems.
- 29% of companies that paid a ransom had their data leaked by criminals.
- Almost half of businesses suffered an attack in the past 12 months. 19% of the attacked were victims of ransomware.
- 62% of successful ransomware attacks used phishing as their entry point in the victim’s system. Other popular techniques incliuded credential theft (44%), a third-party supplier (40%), an unpatched server (28%), and brute force credentials, such as password guessing (17%).
- 92% of global organizations have seen at least one email-based ransomware attack in 2022, and 10% say they have received more than 450 such attacks this year.
Ransomware attacks claim millions
The estimates provided by Cybersecurity Ventures detail that ransomware will attack a business every 11 seconds by the end of 2021. In addition, the costs of ransomware attacks are projected to be $20 billion by the end of this year. This estimate seems to be on track due to the frenzy of activity by ransomware gangs already this year.
As we will see in the review of ransomware gang activity, hackers are earning millions of dollars from businesses worldwide, leading to damages and financial losses in the billions of dollars.
Ransomware gang activity
Ransomware attacks are generally carried out by what you see referred to as “ransomware gangs” or ransomware groups. Large-scale attacks on large enterprise organizations are usually carried out by groups of skilled hackers who work together to achieve ransomware payment. The payment of the ransomware demand serves to fund further attacks and efforts of the malicious organization.
These ransomware gangs may have a mission that aligns with a certain nation-state or cause they support. Others may simply be amassing large fortunes by the ransoms collected and also services they sell such as “ransomware-as-a-service” on the dark web. Whatever the case, the damage, and turmoil these are responsible for are hard to fathom.
Ransomware attacks and the gangs responsible
High-profile ransomware attacks seemingly make news headlines almost weekly. Unfortunately, this trend does not look to be ending anytime soon. Ransomware gangs are not biased to a particular industry or business sector. Instead, attackers are choosing targets across many different industries, including manufacturers, transportation, construction, education, healthcare, and critical services industries, to name a few.
In a whitepaper released by eSentire, it noted that eight well-known ransomware gangs were responsible for over 290 ransomware attack in 2021. The income for these various attacks has netted some $45 million for the groups responsible. Let’s look deeper at the attacks these specific ransomware groups are responsible for and their activities so far in 2021. These include:
- Avaddon
- Clop
- DarkSide
- DoppelPaymer
- Ryuk/Conti
- Sodin/REvil
- LockBit
- Black Matter
1. Avaddon
Avaddon ransomware operators have compromised 88 victims total and 47 of these in 2021. They first came onto the scene in early 2019 and are a group that offers Ransomware-as-a-Service to dark web customers. Showing the extent to which these ransomware gangs go to coerce victims into paying ransoms, Avaddon’s site features leaked documents and countdown clocks showing the time victims have left to pay.
Additionally, they threaten to DDoS victim’s sites if they do not pay the ransom demanded. In its beginning operations, Avaddon targeted healthcare organizations extensively and posting stolen data. However, they had since expanded to other business sectors.
In an interesting turn of events, the Avaddon ransomware group shut down its operations in early June 2021. BleepingComputer received a ZIP file by email with all the decryption keys needed for the remaining victims to recover their data.
2. Clop
Clop has a victims list totaling 53, and 35 of those victims have been attacked in 2021. Of note, Clop was the first ransomware group that demanded a ransom of more than $20 million. This ransom demand was related to an attack on the German tech firm Software AG. However, the tech firm refused to pay the ransom.
Clop had success with the “supply chain” attack vector when they compromised many customers of Accellion, a file transfer application used by companies worldwide. They have had other high-profile attacks against Royal Shell, Qualys, U.S. bank Flagstar, Jones Day, University of Colorado, and others.
One of the unique operations of Clop in 2021 was the activity they carried out to contact customers and partners of their victims, urging them to convince the victim company to pay the ransom. If payment was not made, they threatened to leak sensitive information on the dark web.
Early in June 2021, arrests were made against key members of the group. However, it appears the group is still in operation as it resumed attacks only a week after arrests were made, signaling they are still in action.
3. DarkSide
One of the notable high-profile ransomware attacks over the past few months happened on May 9, 2021, and targeted Colonial Pipeline, one of the largest fuel suppliers to the East Coast of the United States. The attack shut down some 6,000 miles of pipeline, causing fuel shortages and other headaches for large numbers of the Eastern U.S. Colonial Pipeline paid the $4.4 million requested by attackers to return access to business-critical data.
On top of the significant disruption and ransom payment just a few days ago, at the time of this writing, Colonial Pipeline is now saying there was also a widespread data breach in addition to the ransomware attack. CNN noted one of the sample letters sent out to businesses noted hackers gained access to names, contact information, birth dates, social security numbers, driver’s license and military ID numbers, and health insurance information.
The ransomware gang responsible for the attack on Colonial Pipeline is known as Dark Side. Compared to other ransomware groups, DarkSide is a newcomer on the scene of coordinated ransomware attacks, only surfacing in the third quarter of 2020. However, despite their new arrival on the scene, they already have a long list of compromises. These include 59 organizations with 37 of these attacks and compromises in 2021.
DarkSide operates a Ransomware-as-a-Service (RaaS) business on the dark web. It has even been speculated that a subsidiary customer of DarkSide using their RaaS was responsible for the attack on Colonial Pipeline and not DarkSide themselves.
DarkSide ransomware group has a history of targeting energy companies. Before the Colonial Pipeline attack, they broke into one of Brazil’s electric utility companies in early February 2021. They also have targeted manufacturers such as The Dixie Group and IT solutions provider CompuCom Systems.
4. DoppelPaymer
In 2019, another ransomware group emerged called DoppelPaymer that has ransomware based on the BitPaymer ransomware. DoppelPaymer is known to target critical infrastructure organizations, including healthcare, emergency services, and other companies. According to DoppelPaymer, they have compromised 186 victims in total and 59 victims since the beginning of 2021.
They continue to have success in collecting ransom payments and seem to have an affinity for state and local governments and educational institutions. The FBI specifically mentioned DoppelPaymer ransomware attacks in their warning of critical infrastructure attacks.
5. Ryuk/Conti
The Ryuk/Conti ransomware group has been around since circa 2018 and, as you can imagine, has many attacks under its belt. The Ryuk/Conti group started with attacks on U.S. companies that included targets among technology companies, healthcare providers, education, financial services, and government organizations.
The group has self-proclaimed to have hit 352 organizations worldwide, with 63 of those attacks happening in 2021. Ryuk ransomware was the variant responsible for attacks across several government agencies in small U.S. communities. The targets included LaPorte County, Indiana ($130,000 ransom), Jackson County, Georgia ($400,000 ransom), and Riviera Beach, Florida ($594,000 ransom).
Ryuk is also the ransomware used in the widespread targeting of U.S. hospitals and health systems. As a result, the FBI and Department of Homeland security issued a warning to healthcare organizations across the U.S.
6. Sodin/REvil
Sodin/REvil is another relatively new ransomware gang that so far has victimized some 161 organizations with 52 attacks in 2021. It has historically targeted mainly manufacturing companies. However, they have also targeted healthcare, transportation/logistics, and construction companies as well.
Earlier this year, Sodin/REvil made bold ransomware demands of Acer Computer and Quanta Computer for $50 million ransom each. However, Quanta computer did not pay, and the Sodin group demanded that Apple pay the ransom instead as they had stolen leaked images of blueprints which they claimed to be from Quanta.
Recently, Kaspersky spotted Sodin/REvil ransomware targeting a known Windows vulnerability and processor architecture in new attacks to spread the ransomware.
7. LockBit
Russian-speaking ransomware gang LockBit and has been active since September 2019 and has targeted thousands of organizations. Operating on a Ransomware-as-a-Service model, the LockBit gang rents access to their ransomware to other threat actors (commonly referred to as affiliates), who are then responsible for breaching enterprise networks to steal data, and then deploy the ransomware payload to encrypt local copies.
While the LockBit gang has been functioning since September 2019 with some success, they launched a new version of their RaaS platform in June 2021. The LockBit debut coincided with the shutdowns of the Darkside, REvil, and Avaddon ransomware operations, which had attracted many of those gang’s affiliates to its RaaS platform.
The group in October 2020 attacked Press Trust of India, downing the news giant’s operations for hours. Press Trust survived the attack without paying a ransom.
On July 28th, 2021, Australia’s cybersecurity agency published a security advisory warning of a significant increase in LockBit ransomware attacks throughout the country. The joint advisory can be found here.
On August 12, 2021, Accenture confirmed that it was hit by a ransomware attack, with a hacker group using the LockBit ransomware reportedly threatening to release the company’s data and sell insider information.
‘If a $45 billion company like Accenture is vulnerable then everyone is vulnerable,’ says Michael Goldstein, CEO of Florida-based solution provider LAN Infotech.
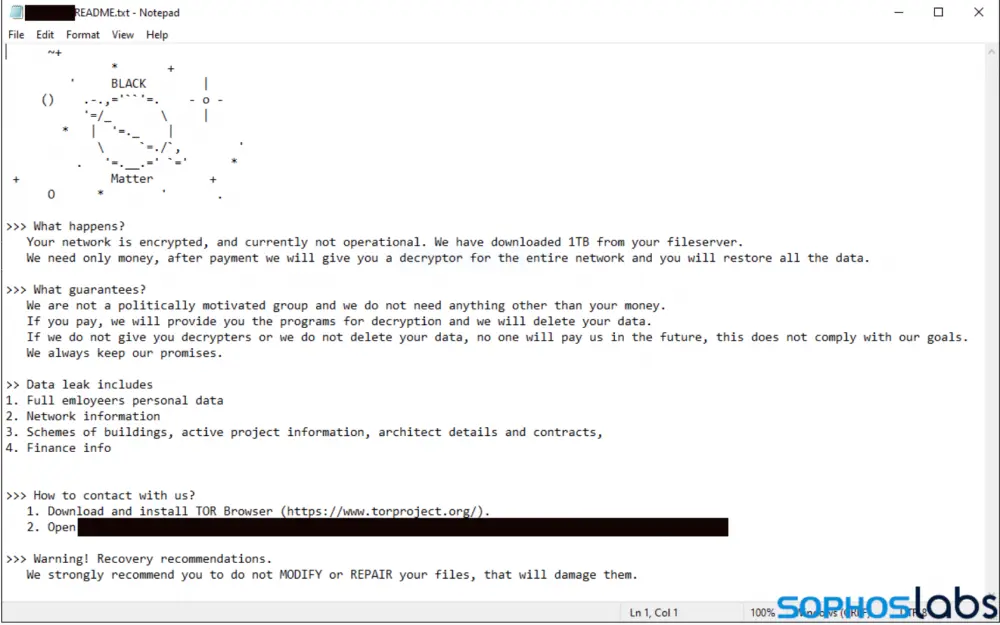
8. Black Matter
A new RaaS emerged in late July. Ransomware called BlackMatter promises to be a replacement for both DarkSide and REvil, combining their most effective features with those of the still-active LockBit 2.0 ransomware.
DarkSide, REvil, and LockBit 2.0 ransomware are said to be incorporated into BlackMatter according to its operators. According to them, despite the fact that they are well acquainted with the Darkside agents, they are not the same actors.
According to Sophos, “there are a number of factors that suggest a connection between BlackMatter and DarkSide. However, this is not simply a rebranding from one to another. Malware analysis shows that while there are similarities with DarkSide ransomware, the code is not identical”.
The BlackMatter ransomware drops a ransom note
Why is cryptocurrency the preferred payment method for ransomware hackers?
A hacker infiltrates a company’s computer system and encrypts the company’s data, halting operations. The data is then held captive by the hacker until a ransom is paid. If payment in Bitcoin or another cryptocurrency is requested, the victim must establish an account on a cryptocurrency exchange, purchase Bitcoin, and transfer it to the hacker’s virtual wallet in return for the decryption key. The key enables the firm to regain access to its data and restart operations.
Because of its pseudonymous nature, cryptocurrency is excellent for ransomware payments; even if you see the ultimate destination wallet into which the ransom payment is placed, you can’t identify who owns or manages the wallet. As a result, ransomware attacks may now be carried out with relative impunity.
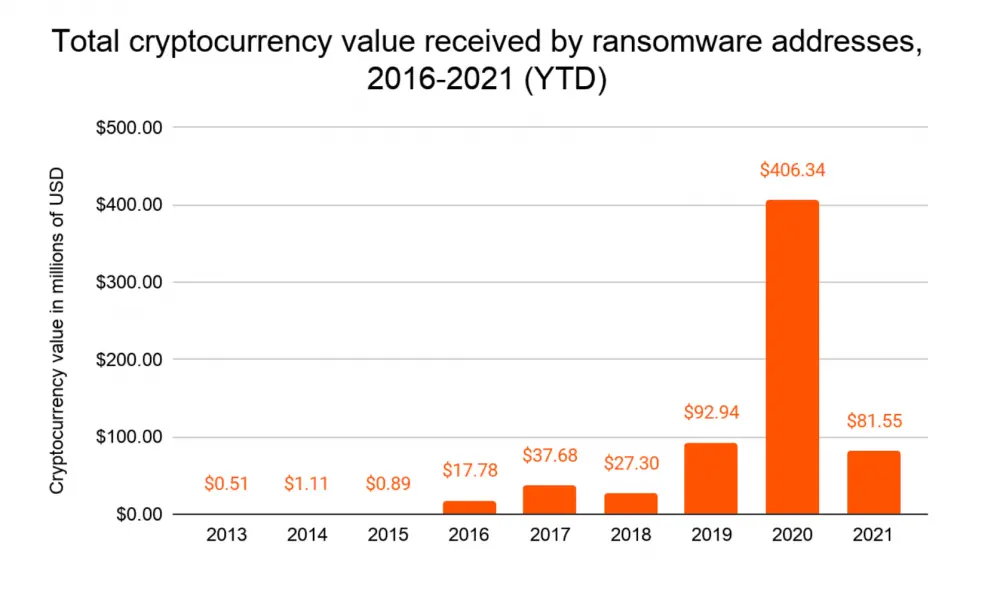
This impunity has resulted in an increase in ransomware assaults and the prominence of the ransomware firm DarkSide, which rents its malware to hackers in exchange for a percentage of any ransom paid. According to Elliptic, a blockchain analytics business, DarkSide, the recipient of the Colonial Pipeline ransom payment, has netted more than $90 million in ransom payments in the last year.
Total cryptocurrency value 2021 received by ransomware addresses 2016 – 2021. Source: Chainalysis
The Cybersecurity and Infrastructure Security Agency (CISA) is leading a ransomware awareness campaign, Reduce the Risk of Ransomware, with information for organizations and individuals to use. Also, CISA is emphasizing nine smart cyber habits that individuals and organizations should implement to avoid falling victim to ransomware.
The U.S. government recommends against paying any ransom to cyber-crime organizations or malicious cyber actors. Paying a ransom only funds cybercriminals, and there is no guarantee that you will recover your data if you do pay.
Check out the Ransomware Awareness Campaign Fact Sheet by CISA.
Cloud environments are not immune
The alarming spread of ransomware should be a wake-up call for organizations worldwide. Your data is not inherently safe, no matter where it is stored. During the pandemic, most businesses shifted gears to ensure remote employees could access data, services, collaboration, and communication tools needed to remain productive.
For many, this meant accelerating cloud migration. Google Workspace and Microsoft 365 have seen tremendous growth for this reason. In addition, ransomware gangs like those mentioned are undoubtedly turning their attention to cloud environments with the end goal of locking your cloud data. They realize businesses are heavily using cloud storage and other tools for production environments.
Businesses have to make sure they have the solutions and capabilities to protect data in the cloud from ransomware. Unfortunately, native cloud SaaS cybersecurity protection is highly “reactive” instead of proactive in its approach to ransomware infection. Note in the Ransomware detection and recovering your files KB, Microsoft mentions the following:
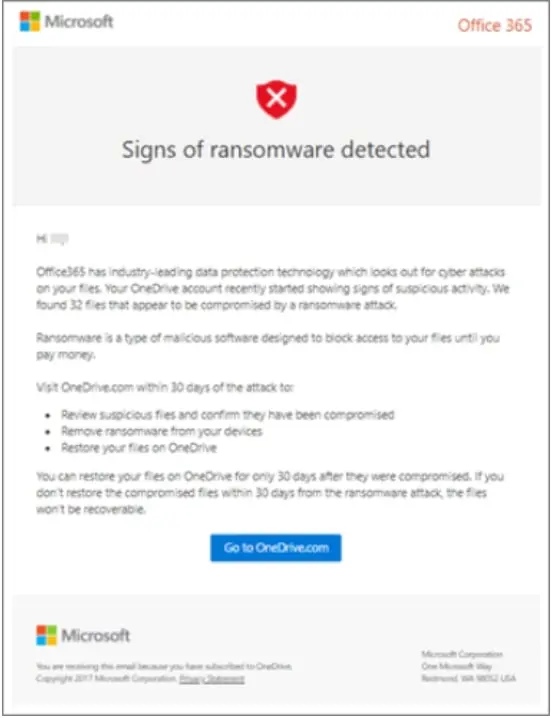
“Ransomware detection notifies you when your OneDrive files have been attacked and guide you through the process of restoring your files. When Microsoft 365 detects a ransomware attack, you’ll get a notification on your device and receive an email from Microsoft 365. If you’re not a subscriber, your first notification and recovery is free.”
Microsoft 365 ransomware detection message
While notifications are great, Microsoft says you will get a note that you have been infected with ransomware and how to restore your data. This approach is not ideal since it is not stopping the ransomware, only notifying you of the activity. It is then up to you to restore your data.
This approach can lead to long RTO times affecting business-critical tasks. For example, the more data you have encrypted, the more time it will take to restore. Additionally, cloud SaaS providers such as Google and Microsoft are throttling customer’s calls to the backend API for file write operations. What does this mean?
Hitting the throttling threshold
It means the more data you must recover in cloud SaaS environments, the greater the chances of hitting the throttling threshold. When cloud SaaS service providers throttle your connections to the backend API, it directly impacts the speed at which you can restore data, which directly impacts the RTO of disaster recovery. Note the following guidance and explanation of how throttling works in Microsoft Graph (the backend API to Microsoft Office 365/Microsoft 365):
“When a throttling threshold is exceeded, Microsoft Graph limits any further requests from that client for a period of time. When throttling occurs, Microsoft Graph returns the HTTP status code 429 (Too many requests), and the requests fail. A suggested wait time is returned in the response header of the failed request. Throttling behavior can depend on the type and number of requests. For example, if you have a high volume of requests, all requests types are throttled. Threshold limits vary based on the request type. Therefore, you could encounter a scenario where writes are throttled but reads are still permitted.”
SpinOne provides businesses with a proactive, artificial intelligence (AI) powered solution that proactively handles ransomware infection in your cloud SaaS environment. It provides the key capabilities that allow companies to have visibility, control, and protection in cloud SaaS environments to stop ransomware before the damage critically impacts their business.
Related: CISO’s Guide to Cloud Security Transformation
Ransomware protection solution benefits: stop the ransomware attack and keep your SaaS data safe with SpinOne
The beauty of the SpinOne Ransomware Protection module lies in its effectiveness and simplicity. Under the cover of the simple settings in the GUI lies a robust ransomware protection solution is driven by artificial intelligence (AI) and machine learning (ML) technology.
Why SpinOne for Ransomware Protection: Achieving No Downtime
Downtime is an inevitable negative result of any ransomware attack. On average downtime is 16 days, which results in millions of dollars for your business. The main reasons for downtime are:
- Lengthy manual processes
- Huge amounts of damaged data
- API limits of cloud service providers
SpinOpe allows you to reduce downtime from 16 days to 1 hour and cut recovery costs by over 90% per ransomware attack with recovery happening in minutes instead of days or weeks.
Using SpinOne, businesses can proactively defend their cloud SaaS environment using a next-generation tool written to meet the challenges of fighting threats such as ransomware in the cloud. Using the SpinOne approach, businesses can go after ransomware before it encrypts large amounts of data. This capability helps to significantly minimize the threat of data leakage used as leverage by hackers, the risk of paying for a decryption key that may or may not work, or running into the hurdle of throttled API connectivity in the cloud.
Ransomware should undoubtedly be a key topic for CISOs across all businesses and industries as it continues to grow more ominous and effective in holding business-critical data hostage. CISOs and organizations today must meet the threat of ransomware head-on. SpinOne provides the solution necessary to proactively and automatically protect against and recover from a ransomware attack.
Using cybersecurity automation, SpinOne’s Ransomware Protection module carries out the following:
- Performs real-time scans to detect ransomware
- Blocks the network source of the ransomware attack
- Scans to determine which files were affected by ransomware
- Automatically restores files that were encrypted
- Automatically notifies administrators of the ransomware attack and remediation
SpinOne provides continuous real-time Ransomware Protection of your cloud SaaS environment
Ransomware is a type of malicious software, or malware, that prevents you from accessing your computer files, systems, or networks and demands you pay a ransom for their return. Ransomware attacks can cause costly disruptions to operations and the loss of critical information and data.
US Senators roll out bill giving organizations 24 hours to report ransomware attack payments
The leaders of the Senate Homeland Security and Governmental Affairs Committee on September, 28th, 2021 introduced legislation that would give set timelines for cyber incident reporting, including giving certain organizations 24 hours to report if they paid the sum demanded in a ransomware attack.
The Cyber Incident Reporting Act, sponsored by committee Chairman Gary Peters (D-Mich.) and ranking member Rob Portman (R-Ohio), would also require owners and operators of critical infrastructure to report cybersecurity incidents to the Cybersecurity and Infrastructure Security Agency (CISA) within 72 hours.
What are some interesting facts about ransomware?
One of the most interesting facts is that ransomware has become a complex business scheme with labor divided by multiple actors. There are developers who are only responsible for creating ransomware software. They sell access to this ransomware tool to criminals who then spread it among the potential target. The access is subscription-based that’s why it is called RaaS (Ransomware-as-a-Service).
How many ransomware attacks every day?
There are approximately 1.7 million ransomware attacks per day. Most of them aren’t successful, though.
Why ransomware is the biggest threat?
There are several reasons why ransomware can be considered the biggest threat. First, a ransomware attack is easy to carry out and hard to spot. Most attacks now include double or triple extortion, i.e., data theft. Ransomware is very hard to decrypt. It requires months or even years if you do not have a decryption key and most businesses do not have so much time to wait. Finally, the recovery of data from backup can also cause a significant downtime.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...