Cloud Storage Security From A to Z: Is the Cloud Safe?
In this article, we will go through the list of things cloud storage security depends on. You will get some perspective on the security pitfalls to be ready for and understand how to make full use of the cloud security strengths. In the end, you’ll find out how to secure cloud storage and data on it.
If you are here, you are probably considering moving your business data to the cloud, and you’re concerned about its security. When you ask, “Is the cloud safe for my data?” the real answer will be: it depends. In many ways, the cloud has an advantage over the on-premises solutions: it’s accessible anywhere and anytime, has a top-notch infrastructure, and a good deal of baseline security. And yet, for the cloud to be bulletproof, you need to make it that way.
Cloud Storage: Definition and Types
Cloud storage, at the most basic level, is an outsourced solution for storing and securing your files. When the data goes into the cloud, it gets spread across different servers managed by data centers.
As long as you have an internet connection, you can reach the files stored in the cloud on-demand. That provides companies and individuals with scalability, agility, and flexibility they can’t get using on-premises cloud storage.
The most popular example of this on-demand approach is all solutions with an “as-a-service” ending: Software as a Service (SaaS), Platform as a Service (PaaS), Infrastructure as a Service (IaaS), etc.
You can choose one of the three types of cloud storage depending on your business needs and capabilities: public, private, or hybrid cloud.
Public cloud – it is the cloud computing environment in which computing resources are accessible via the internet and shared between the “tenants.” You can choose the free or freemium model with limited functionality or subscribe to paid plans that provide a broad range of functionality and storage. It’s safe to say that the public cloud is the most popular choice among small-to-medium businesses.
Examples of public cloud providers include Microsoft Azure, Google Cloud, Amazon Web Services (AWS), Oracle Cloud.
Private cloud – it is a cloud environment explicitly dedicated to your organization. All the processes and storage are tailored to your needs and aren’t shared with anyone else. This option is more secure and will suit businesses that operate in strictly regulated fields and plans to store sensitive data in the cloud.
Hybrid cloud – it is, as you see from its name, is a combination of private and public clouds. Such a combination is the best option for companies that have to secure their sensitive or business-critical data on the private cloud while using the public cloud for high-volume workloads.
As you can see, the type of cloud environment you choose to keep your files in has a notable impact on how secure the cloud storage is.
How Secure Is The Cloud?
In many ways, the cloud is much more secure than on-site options. The warehouses with data centers are owned by big respectable corporations, which means high investments in the quality and security of their storage and infrastructure.
Regardless of which one of the types of cloud storage you stick to, they all come with relatively strong baseline protection, including various inbuilt security elements.
To be sure of the security means in place, inspect the cloud vendor first. But generally, popular cloud storage providers like Azure or AWS protect your data using the following practices:
- Encryption. It is a way of encoding information so that only authorized users can read it. If a piece of data gets stolen, it will be impossible to read without an encryption key. Cloud providers like Azure, both at rest (when the data is in the storage) and in transit (when it travels between locations.)
- Physical security. Cloud providers store data on physical carriers like servers that are located in data centers around the world, each having a piece of your data on them. This makes the likelihood of your cloud data getting damaged by a natural disaster like a fire or flood is extremely low. If something happens with one warehouse that con Also, unlike most on-site solutions, these places are guaranteed 24/7 surveillance and armed security guards.
- Event logging and workload audit. Event logs help security analysts understand threats. These logs record network actions. Analysts use this data to build a narrative concerning network events. This helps them predict and prevent security breaches.
- Data Security and data retention policies. Systems use data classification policies to manage and automate how data is stored, retained, archived, and deleted.
- Data access monitoring. The cloud services provide their clients with full visibility and
Major Cloud Storage Security Concerns
Now, you may have a reasonable question: if cloud storages are so secure, why hasn’t the number of data breaches declined? In fact, more than 70% of businesses had their cloud data breached at least once during the past year (source).
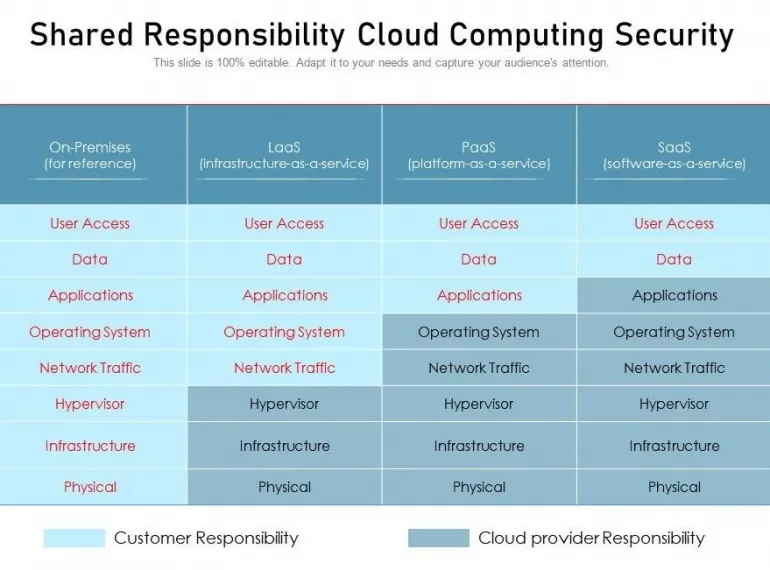
It seems counterintuitive, but there is no contradiction here. The cloud operates on the shared security model, making all of its security strengths only half of the equation. The other half of this equation remains on the tenant, which is you. And that is something most companies tend to overlook.
As you can see, there are some liabilities that will always fall on you regardless of whether you use cloud or on-premises services. These first four areas in red are the most vulnerable ones in your organization that may cause a massive data breach if not taken care of properly.
Here are those areas:
- Identity & Access
- Governance & Policy
- Devices Management
- Education & Awareness
All the threats that can affect your organization in the cloud come from those areas not being taken care of properly.
The biggest threats in the cloud are the same as in on-premises: data breaches, data leaks, and data loss. Here are the most common causes that lead to this outcome:
1. Phishing emails. It is easy to trick mass target public cloud users into clicking on phishing emails by masking them as Google or Microsoft emails. A user may click on the link in a phishing email and provide the scam site with credentials from the real Microsoft 365 or Google Workspace account. Or, by clicking on the malicious link the user can launch a self-deployed virus that will infect their device or the cloud space they have access to.
After obtaining the credentials from your workspace, cybercriminals may use it to infect your data in the cloud with ransomware or any other malware, delete it, or use it to benefit from it in any form.
2. Shadow IT. Shadow IT is unauthorized/unapproved by the IT department’s usage of hardware and software (unapproved third-party applications or devices) that presents risks to your corporate data.
Using third-party applications and extensions to boost productivity is a common practice. To use an app, a user always has to grant access to files and folders on their device or account. This access is the loophole threat actors exploit to get to your data. To do that, they can hack legitimate applications or even create fake apps that can encrypt, copy, or even delete them after obtaining access to files and folders.
3. Absence of Data Loss Prevention (DLP) practices. Users delete data, both intentionally and unintentionally, all the time. In the cloud, the possible damage is potentially higher because any deleted file or folder could be shared with multiple people and even departments. Irreversibly deleting the wrong file can be disastrous for the workflow.
This is why it is necessary to always backup cloud data and protect it with Data Loss Prevention Policies.
4. Weak passwords and turned off multi-factor authentication. Weak authentication practices can easily lead to a brute-force attack and account hijacking. The worst-case scenario is when the hijacked account belongs to Super Admin, which would compromise your whole system and data on it.
4 Practices to Maximize Cloud Storage Security
To make your data in the cloud resilient to threats, you need to fill in security gaps. Simply put, you need to own your part of the responsibility. It doesn’t guarantee your data 100% protection (nothing does), but it will certainly straighten your defenses.
1. Conduct identity and access management
Identity management or, in other words, authentication practices, is a cornerstone of every security system. It includes:
- Strong log-in credentials practices;
- Implementation of two-factor authentification;
In some cases, it can be complemented by biometric authentication and digital device authentication.
Access management is what drastically lowers the chances of data leaks taking place. Just as in on-premises, you need to manage your users and third parties and the access they have to files and folders in the cloud. Assigning or restricting rights to users to make changes in the environment, managing who can and can’t access what, determining high-level and low-level access rights – all these are the tasks for the IT administrator.
2. Manage Shadow IT
More and more third-party applications, extensions, and plugins, as well as unsanctioned devices, happen to be the source of malware, data leaks, and data losses. This is why every app should be thoroughly assessed manually by your security team or automatically by using specially designed apps security software.
Read about how fake apps can undermine your security→
3. Educate your employees
Your employees are the main source of the internal threat, and most of it comes from ignorance in cybersecurity matter. Your employees should know what emails not to open, what links not to click, and what files and access not to share. And it is your obligation to teach them.
The right way to do it is to make cybersecurity training mandatory for everyone. All the newcomers should pass it before taking up their direct duties, and the “old folks” must refresh their knowledge every 6 months.
Spread awareness about key cybersecurity terms.
4. Implement Data Loss Prevention Practices
Data Loss Prevention is a set of tools that protect your data from being deleted or leaked. The foundation of the whole DLP approach is backup, and it is what your data protection should start from. Cloud providers like Microsoft, Amazon, or Google, let alone smaller players, do not back up your data.
Microsoft service agreement is very straightforward about it.
Find out about the Data Loss Prevention practices here
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why a Reliable Backup Plan is Your Best Defense Against Cybersecuri...
…and the Most Boring Way to Protect Your Organization I’ve written about the importance of...
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...