Continuous Data Protection: Does Your Business Need It?
The market for data protection tools is constantly growing. Thus, it becomes increasingly hard to choose the solutions that will meet the needs of your business. In this article, we’ll discuss continuous data protection.
What is it? What are the pros and cons of this category of tools? And most importantly, is it enough to protect your data?
What is continuous data protection?
Continuous data protection (CDP) is a backup tool that creates a copy of every single change made in a system. It is often called continuous backup or real-time backup.
It was introduced back in 1989 as an alternative to tape data records of that time. It enabled businesses to reduce the amount of time and storage necessary for backup while increasing the number of recorded data changes.
How real-time backup works
Once introduced to a system, the real-time backup creates its full copy and stores it in the separate assigned storage. After this initial operation, the program monitors the system and records every single change in data.
It’s important to note that CDP never copies the whole system again. Instead, it uses the block-level (also called byte-level) approach to backup. Every change in the system is considered a block. The program makes a copy of this block.
For example, when you type a text in a Word document, CDP creates a copy every time you type in a character or a space, delete, insert a piece of data, or change the text format. As a result, in case of data loss, you can recover it literally from any point in time.
Finally, let’s talk about a critically important aspect of real-time backup performance. Once a change is done, its copy is sent to the target disk. The target disk uses the real-time backup to send a ‘confirmation’ about the receipt of the change. Only after that, this change is recorded on the local disk.
CDP vs. Regular backup tools
Regular backup tools create data copies at certain time points. For example, they can back up on a weekly or daily basis. The information that was added and then deleted between two snapshots will be lost forever.
CDP’s key goal is to eliminate any data loss that might happen between scheduled snapshots of regular backups.
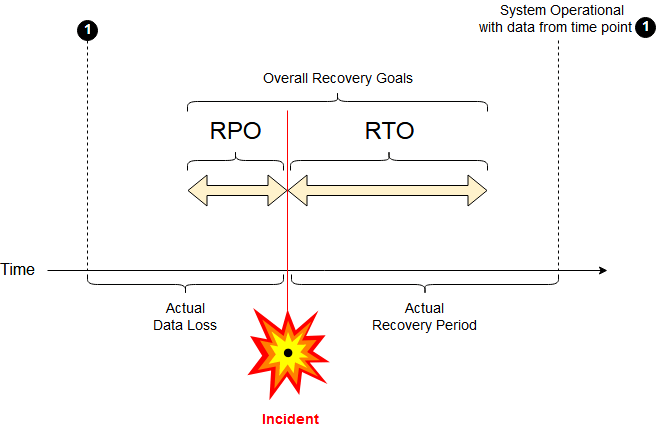
Previously, the difference between CDP and traditional backup tools was also in the level of data copying. The former thus used fewer data storage. Traditional backups would copy the file, while continuous data protection tools only copied the changes in the file.
Modern backup tools used this approach to decrease the amount of data necessary to copy. That’s how incremental backups emerged.
Real-time backup vs. Near continuous data protection solutions
The market has a class of tools that cannot be classified as CDP. However, they are sometimes marketed as CDP. These tools are called near-continuous data protection.
The idea is to make the traditional scheduled backups as frequent as possible. For example, some tools make snapshots every 30 or 15 minutes. This, however, doesn’t enable them to save all the changes that have been made to the data.
Benefits and drawbacks of continuous backup
CDP has both advantages and disadvantages. Let’s study them in detail.
Benefits:
- No data loss. Because every change is recorded, businesses can be sure that every single data entry will be preserved.
- Always up-to-date. Similarly, you can find and recover the last information introduced before the cyber event (e.g. ransomware attack).
- Fast recovery. Since CDP applies a block-level approach, it takes less time to recover.
Drawbacks:
- Slowed performance of the system. Because the system waits each time for the response of the target disk, there can be lags in its performance, especially, if there are many users working simultaneously.
- Speed-dependant. Businesses cannot use just any storage. They need technology (e.g. disk) that enables high-speed performance.
- High cost. Special technology comes at a higher price.
- Data search can be excessively long. In the case of data corruption, searching the exact point-in-time copy before the corruption occurred can take much time as the number of changes can be significant.
Is continuous backup enough to protect your data?
On the surface, CDP looks like a great tool to protect your data from loss, even despite its apparent drawbacks. However, there are several more aspects we suggest you take into account before making a final decision.
Cloud limitations
Many if not most modern businesses have transitioned to the cloud. Environments like Google Workspace or Microsoft Office 365 offer a wide variety of tools, data storage, and file cooperation functionality. We can safely say, that nowadays a large portion of global business-critical data is stored in the cloud.
CDP doesn’t work well with the cloud due to the natural limitations of these environments. Both GW and MSO 365 exchange data with external backup tools via APIs. And both have limitations in the number of APIs per minute. In other words, there’s a reasonable limit on the number of data units a program can exchange with these cloud offices.
Meanwhile, a continuous data protection tool wants to record any data change your users do, which inevitably leads to surpassing API limitations.
That’s why most cloud backup software solutions are incremental and do snapshots on a daily basis.
Data leak
Modern businesses need to be cautious not only about data loss but also about the data leak. Events like corporate espionage, cyber-attacks, and simple human errors can lead to unwanted exposure of your information.
Modern data protection requires tools that will monitor and detect incidents closely related to data leaks:
- Unusual logins as the result of stolen credentials
- Sending personally identifiable information via email
- Incorrect sharing settings that enable unauthorized access to your files
- Unusual data download as part of man-in-the-middle attack
- Application detection and risk assessment.
Ransomware
Ransomware has been on the rise since 2014. Year after year, it hits an increasing number of businesses, non-profits, and even governments. Previously many companies relied on data backup. However, in practice, data recovery can cause downtime.
Usually, CDP recovery is fast, because it recovers only a small portion of a file. However, ransomware tends to encrypt all your files and introduce changes to every single portion of data. Recovery will thus take much longer and can result in financial losses.
Cybersecurity experts suggest using ransomware protection tools that stop ransomware attacks in the very beginning and quickly recover your business-critical data.
Was this helpful?
How Can You Maximize SaaS Security Benefits?
Let's get started with a live demo
Latest blog posts
Why Google Drive Backups Are Important
Google Drive offers customers a unique blend of robust security features to keep their data...
Evaluating the Best Backup Services: What to Look For and Popular O...
If you’re here right now you’ve probably realized how important it is to backup your...
Brewing Trouble: How a Starbucks Ransomware Attack Poured Cold Wate...
Cybercriminals often carry out attacks around holidays as this helps to ensure the most amount...


